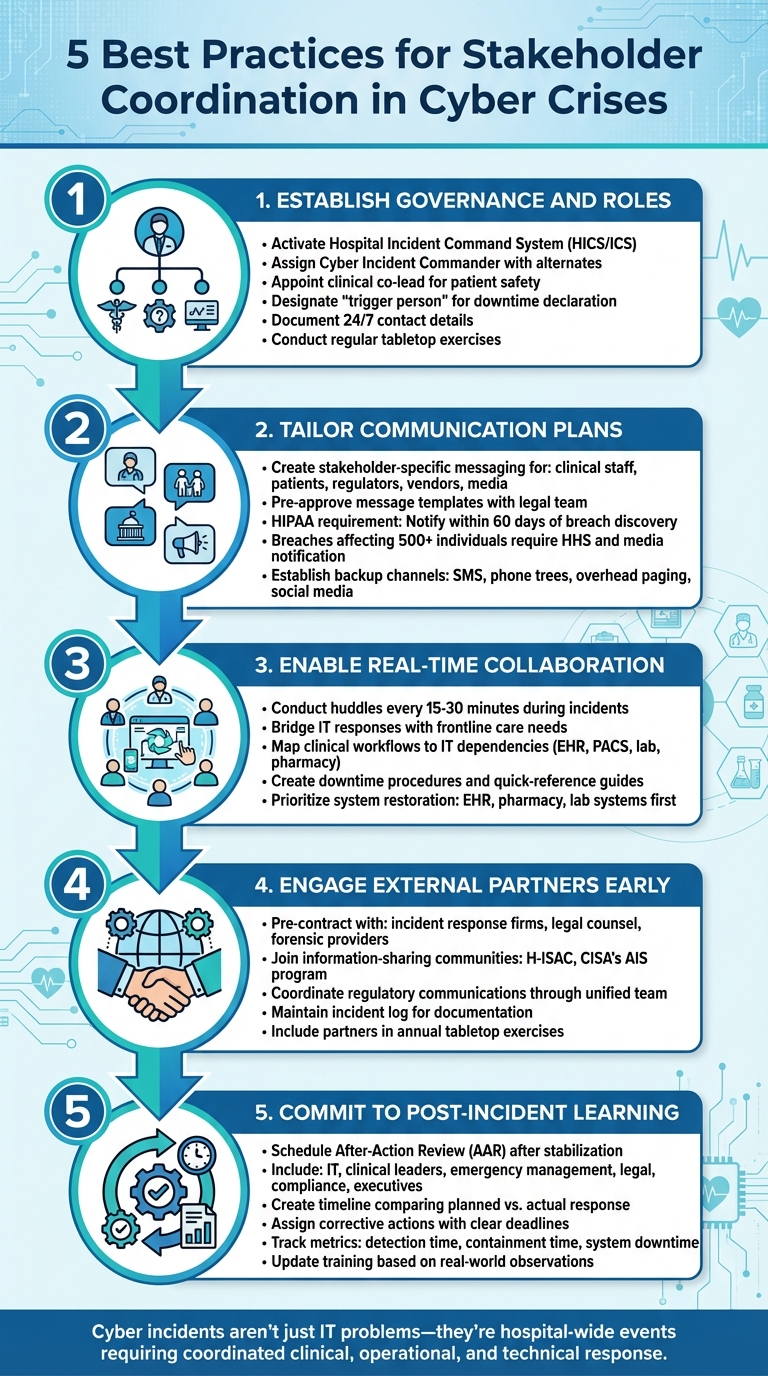
5 Best Practices for Stakeholder Coordination in Cyber Crises
Post Summary
Healthcare cyber crises can disrupt patient care, compromise safety, and create operational chaos. To minimize these risks, organizations must focus on preparation, communication, and collaboration. Here are five key practices to improve coordination during such incidents:
- Establish Governance and Roles: Define leadership, assign clear responsibilities, and document protocols before a crisis occurs.
- Tailor Communication Plans: Create specific messaging for different stakeholders, including staff, patients, regulators, and vendors.
- Enable Real-Time Collaboration: Facilitate seamless coordination between clinical and operational teams during incidents.
- Engage External Partners Early: Build relationships with incident response firms, law enforcement, and regulators in advance.
- Commit to Post-Incident Learning: Conduct after-action reviews to identify gaps and refine plans for future readiness.
5 Best Practices for Healthcare Cyber Crisis Stakeholder Coordination
1. Define Governance Structures and Assign Roles Before a Crisis Occurs
Imagine a ransomware attack striking at 2:00 AM. In such a scenario, having pre-assigned leadership and clearly defined roles isn't just helpful - it’s absolutely critical. According to federal healthcare preparedness guidance, organizations should activate the Hospital Incident Command System (HICS/ICS) for cyber incidents whenever services are disrupted. This approach treats a cyberattack with the same urgency as a mass-casualty event or natural disaster [5]. To prepare effectively, your cyber crisis governance must be formalized, documented, and tested well before any incident occurs.
Start by establishing a formal cyber incident governance charter that integrates seamlessly with your emergency management structure [3][5]. Assign a Cyber Incident Commander - typically a senior leader - and ensure alternates are available for coverage during off-hours [5]. Additionally, appoint a clinical co-lead who can bridge clinical workflows with cybersecurity efforts, ensuring decisions prioritize patient safety [7]. The Agency for Healthcare Research and Quality (AHRQ) even suggests creating a "clinical director of cybersecurity" role to oversee incident planning from a patient-safety perspective [7].
It’s equally important to clarify who has the authority to declare incidents, shut down systems, or activate downtime protocols - and under what circumstances [5]. The Assistant Secretary for Preparedness and Response (ASPR) TRACIE guidance recommends designating a "trigger person" who is empowered to officially declare downtime and communicate the applicable protocol. This step prevents delays and confusion when every second matters [5]. Make sure these responsibilities are documented, including 24/7 contact details and backup personnel for each critical role [3][5].
Don’t overlook external stakeholders. Pre-establish relationships with law enforcement, CISA, cyber insurers, incident response firms, and key vendors [3][5]. Contracting with specialized cyber incident response firms ahead of time ensures they’re ready to step in when needed. To streamline coordination with vendors, tools like Censinet RiskOps™ can centralize third-party risk profiles, vendor contacts, and incident responsibilities.
Testing your governance structure is just as important as creating it. Conduct regular tabletop exercises that involve executives, clinical leaders, IT teams, vendors, and communications staff [4][5]. Use these exercises to refine your governance documents, role descriptions, and contact lists based on what you learn [3][4][5]. Review and update your governance framework at least annually or whenever significant organizational changes occur [3][5]. A governance framework that exists only on paper won’t stand up to the chaos of a real crisis.
2. Create Communication Plans for Each Stakeholder Group
When a cyber crisis unfolds, a one-size-fits-all approach to messaging simply doesn’t work. Effective communication is crucial to complement the governance framework needed for a smooth incident response. Clinical staff require clear instructions to continue delivering care safely, even if the electronic health record (EHR) system is down. Patients need reassurance about the security of their data and uninterrupted access to services. Regulators expect timely, compliant notifications, while vendors rely on detailed technical information to help mitigate the threat. Each stakeholder group has specific needs and communication preferences [3] [5] [6].
To address these diverse requirements, start by identifying all stakeholder groups and assigning a communication lead for each. At a minimum, your plan should include internal clinical staff, non-clinical staff, executive leadership, patients and their families, external vendors, regulators, and the media. For each group, determine who will deliver the messages, which channels will be used, and what type of information is most relevant. For example, clinical teams need operational details, while patients benefit from simple, jargon-free explanations about the incident and how their data is being safeguarded. Regulators, on the other hand, require concise overviews of the breach, including the systems impacted, number of affected records, and immediate safety measures taken [3] [5] [6].
Pre-approved message templates can streamline communication during a crisis. Work with your legal team ahead of time to draft templates for patient notifications, media statements, regulatory updates, and vendor communications. For internal staff, create quick-reference tools like job aids or laminated cards outlining downtime workflows. For patients, develop FAQs for front-desk staff and call center representatives, ensuring the language is straightforward and non-technical. Remember, HIPAA mandates that affected individuals be notified without unreasonable delay - no later than 60 days after a breach is discovered. Breaches impacting 500 or more individuals must also be reported to the Department of Health and Human Services (HHS) and the media [8].
It’s wise to assume that standard communication channels could be disrupted during a cyberattack. Ransomware, for instance, might take down email, EHR systems, and internal messaging platforms. Backup communication methods are a must. Federal guidance from ASPR TRACIE suggests using independent mass notification systems, SMS, phone trees, overhead paging, and clinical "zone captains" to relay critical information when digital systems are compromised [5]. To reach patients and the public, rely on local radio, TV, social media platforms, and ensure your organization's website remains accessible - preferably hosted on a resilient, cloud-based platform. Keep a centralized, up-to-date contact list of clinical, technical, and operational vendors, payers, health information exchanges, and cybersecurity providers, complete with 24/7 contact details and clear escalation paths.
Finally, test your communication plan regularly through tabletop exercises that simulate real-world scenarios. These drills should include challenges like conflicting information, media inquiries, and regulator demands. Use after-action reviews to fine-tune your message templates, contact lists, and backup communication methods. By tailoring your communications, you can help ensure patient safety and maintain care continuity during a cyber crisis.
3. Coordinate Clinical and Operational Teams in Real Time
When a cyberattack strikes, it’s not just an IT issue - it quickly escalates into a crisis that impacts patient safety and disrupts operational continuity. This kind of situation requires seamless collaboration between clinical and operational leaders [5] [7]. Imagine the chaos: electronic health records (EHR) going offline, lab systems freezing, and imaging platforms becoming inaccessible. In these moments, decisions about shutting down systems, implementing downtime workflows, and prioritizing services must involve both technical and clinical expertise.
To tackle this effectively, rely on established governance structures and focus on real-time coordination. Activating your Hospital Incident Command System (HICS/ICS) ensures streamlined decision-making without wasting time revisiting roles already defined. Appointing a clinical cybersecurity liaison can bridge the gap between IT responses and frontline care, ensuring both perspectives are aligned.
Conduct quick huddles every 15–30 minutes to assess system status, patient risks, and operational capacity [3] [5] [7]. These brief meetings help clinical and operational leaders weigh technical containment strategies - like isolating networks or shutting down systems - against the need to maintain care continuity. For example, teams might need to decide whether to switch to manual processes when critical systems are down [3] [5] [7]. Decisions like these require a clear understanding of which clinical workflows rely on specific IT systems. Prioritizing system restoration is key, often starting with EHR core functions, pharmacy, and lab systems, while deferring less critical modules [3] [5] [7].
Preparation is everything. Before a crisis, map out clinical workflows and their IT dependencies - think EHR, PACS, lab analyzers, pharmacy systems, telemetry, and registration [3] [5]. Create detailed downtime procedures for tasks like registration, consent, order entry, documentation, and medication safety. To make these processes accessible, distribute concise quick-reference guides or laminated pocket cards to clinicians and operational staff [5] [7]. Regular tabletop and live downtime drills involving clinical leaders, frontline staff, IT, and operations are invaluable. These exercises build familiarity with roles, communication channels, and decision-making processes, so when an actual incident occurs, teams can respond swiftly and confidently to safeguard patients and maintain operations [4] [5].
Tools like Censinet RiskOps™ can further strengthen preparedness. These healthcare-specific cybersecurity platforms provide real-time insights into digital dependencies and vulnerabilities during a cyber crisis, giving your team a critical edge when it matters most.
sbb-itb-535baee
4. Work with External Partners and Regulators Early
A cyber crisis is the worst time to start forming relationships with external partners. Prepare ahead by pre-contracting with incident response firms, legal counsel, and forensic providers. This ensures you can activate their support immediately if ransomware disrupts your electronic health records (EHR) or compromises patient data[3]. Include key government agencies in your planning to clarify reporting protocols and establish evidence preservation processes. This preparation reduces the risk of rushed decisions during a crisis[5].
Leverage these pre-established relationships by enlisting incident response firms, legal advisors specializing in HIPAA, cyber insurers, and platforms like Censinet RiskOps™[2]. Censinet RiskOps™ is particularly useful for healthcare organizations, helping centralize third-party risk assessments, document security controls for critical vendors, and maintain up-to-date information across your network. This level of visibility allows for quicker decisions, such as disconnecting a compromised integration or notifying vendors promptly.
Participation in sector-specific information-sharing communities, like H-ISAC and CISA's Automated Indicator Sharing (AIS) program, provides access to real-time threat intelligence. These platforms share indicators of compromise and coordinated mitigation strategies during active cyber campaigns. Learning from peers’ experiences - such as tactics and techniques observed during ransomware attacks - can help you address vulnerabilities and strengthen defenses before similar threats impact your organization.
To streamline regulatory communications, coordinate through a unified team that includes legal, compliance, privacy, and executive leadership. This approach ensures consistent, accurate messaging while preserving attorney–client privilege when necessary[6]. Keep all decisions and communications documented in an incident log to prioritize patient safety and demonstrate due diligence to regulators and insurers[5].
Lastly, incorporate external partners into annual tabletop exercises simulating ransomware attacks or protected health information (PHI) breaches. These drills validate your communication channels, decision-making processes, and evidence-handling protocols, ensuring a well-coordinated response when it matters most.
5. Learn from Each Crisis and Update Your Plans
Every cyber incident exposes weaknesses in technology, processes, or coordination. To address these, schedule a structured after-action review (AAR) shortly after stabilizing the situation. Bring together IT, clinical leaders, emergency management, legal, compliance, supply chain, and executive leadership for this review. This collaborative approach ensures you capture both technical failures and the broader operational impacts, such as delayed procedures or confusion caused by switching to paper workflows.
Start by creating a concise timeline that compares what was planned to what actually happened. Highlight successes, pinpoint gaps, and assign corrective actions with clear responsibilities and deadlines. Many U.S. healthcare systems align these reviews with Hospital Incident Command System (HICS) structures, enabling a unified evaluation of clinical operations, business continuity, and cybersecurity. These reviews provide valuable insights that can turn lessons learned into meaningful improvements.
Take action based on the findings. For example, if the AAR reveals staff struggled with paper charting during downtime, update your incident response plan to include clear triggers for manual processes and develop quick-reference guides for each unit. If vendor coordination was an issue, revise business associate agreements to clarify roles, timelines, and communication methods. Platforms like Censinet RiskOps™ can help reassess vendor risks and guide budget priorities for resilience improvements.
Next, refine training and drills based on real-world observations. If a phishing attack led to the breach, update your security awareness training with redacted examples and run targeted simulations for the roles most affected. If clinical teams were unprepared for manual charting, organize hands-on downtime drills that cover tasks like handling consent forms and medication orders. Leadership tabletop exercises should test decision-making under pressure, using real-event timelines to simulate high-stakes conditions.
Finally, track your progress over time. Maintain a corrective action register that links findings to updated policies, with designated owners and deadlines. Compare metrics like detection time, containment time, and system downtime across incidents and drills to ensure your adjustments are working. As Brian Sterud, CIO at Faith Regional Health, explains:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Conclusion
Handling a healthcare cyber crisis effectively requires more than just quick fixes - it demands preparation, strong communication, and a commitment to ongoing improvement. The five best practices discussed here - defining clear roles, customizing communication strategies, ensuring real-time coordination, engaging external partners early, and fostering continuous learning - form a solid foundation for navigating these challenges. Together, they enable faster decisions and minimize disruptions when incidents occur.
Take, for instance, the value of pre-defined governance structures and clear downtime procedures. These tools allow healthcare teams to switch to manual workflows quickly while maintaining seamless communication with stakeholders. An established incident command system ensures staff, patients, vendors, and regulators stay informed through all available channels. After the crisis, structured after-action reviews help refine plans and training, keeping the organization better prepared for the future. This proactive approach safeguards patient safety, reduces disruptions, and accelerates recovery.
Cyber resilience is ultimately about protecting patient care. When electronic health records or medical devices go offline, the risks are real - delayed diagnoses, medication errors, and postponed treatments are just a few examples. That’s why federal guidelines and patient safety experts emphasize integrating cybersecurity with clinical and emergency management. Cyber incidents aren’t just IT problems; they’re hospital-wide events requiring coordinated efforts across clinical, operational, and technical teams.
Preparing for cyber crises is not a one-time task - it’s a continuous process. Start by defining governance structures, documenting communication protocols, and running small tabletop exercises. Focus on impactful steps, like forming a cross-functional cyber incident steering group and aligning with existing emergency management frameworks. Embedding these practices into regular discussions within quality, safety, and governance committees makes them a natural part of daily operations.
Technology can also play a pivotal role in streamlining these efforts. Solutions like Censinet RiskOps™ are designed specifically for healthcare, offering tools to centralize vendor and risk data, simplify assessments, and manage ongoing risks. These platforms provide the support needed to implement these best practices effectively, ensuring healthcare organizations are ready to act swiftly when every second matters.
FAQs
What steps can healthcare organizations take to ensure clear communication during a cybersecurity crisis?
During a cybersecurity crisis, healthcare organizations can improve communication by setting up predefined protocols and utilizing real-time collaboration tools. These measures ensure that everyone involved stays informed and on the same page. Clear and timely updates are key to maintaining open communication, while clearly defining roles and responsibilities helps avoid confusion.
Specialized platforms for cybersecurity and risk management can further simplify coordination, allowing teams to respond more efficiently when it matters most.
How do external partners contribute to managing cyber crises in healthcare?
External partners play a crucial role during healthcare cyber crises by providing specialized skills and resources that organizations might lack internally. They assist in managing response efforts, improving communication, and working towards quicker resolutions to reduce potential risks.
These partners also contribute by sharing threat intelligence, which helps healthcare organizations anticipate and address new cyber threats. Their involvement strengthens cybersecurity defenses, safeguarding both sensitive patient information and vital systems.
Why is it important to review and learn from cyber incidents in healthcare?
Learning from cyber incidents plays a key role in spotting vulnerabilities, improving response strategies, and fortifying defenses against future attacks. By carefully examining failures and successes, healthcare organizations can better safeguard sensitive information, uphold patient trust, and keep operations running smoothly. This ongoing process of evaluation and adjustment is crucial for boosting cybersecurity readiness and resilience.


