Building a Healthcare TPRM Team: Roles, Responsibilities, and Success Metrics
Post Summary
Managing third-party risks in healthcare is no longer optional - it’s a necessity. With over 48 million people impacted by healthcare data breaches in 2022 and financial losses averaging $408 per stolen record, organizations must prioritize Third-Party Risk Management (TPRM). A dedicated TPRM team ensures compliance, protects patient data, and minimizes risks tied to vendors and business associates.
Key Takeaways:
- Why TPRM Matters: Healthcare providers face strict regulations like HIPAA, and 90% of major healthcare data breaches in 2022 were caused by third-party vendors.
- Core Team Roles: TPRM teams include a Program Lead, Cybersecurity Analyst, Compliance Officer, Procurement Specialist, Clinical Leaders, and IT Security Engineers.
- Risk Management Framework: Use a 3 Lines of Defense model - operational teams, TPRM oversight, and internal audits - for accountability.
- Performance Metrics: Measure success with KPIs like vendor assessment speed, breach rates, and risk remediation timelines.
- Tools for Success: Platforms like Censinet RiskOps™ streamline risk assessments, automate monitoring, and enhance collaboration.
By assembling the right team, using advanced tools, and monitoring performance, healthcare organizations can safeguard patient data while meeting regulatory standards.
Managing Third-Party Risk in Large Healthcare Organizations at HIMSS 2022
Core Roles in a Healthcare TPRM Team
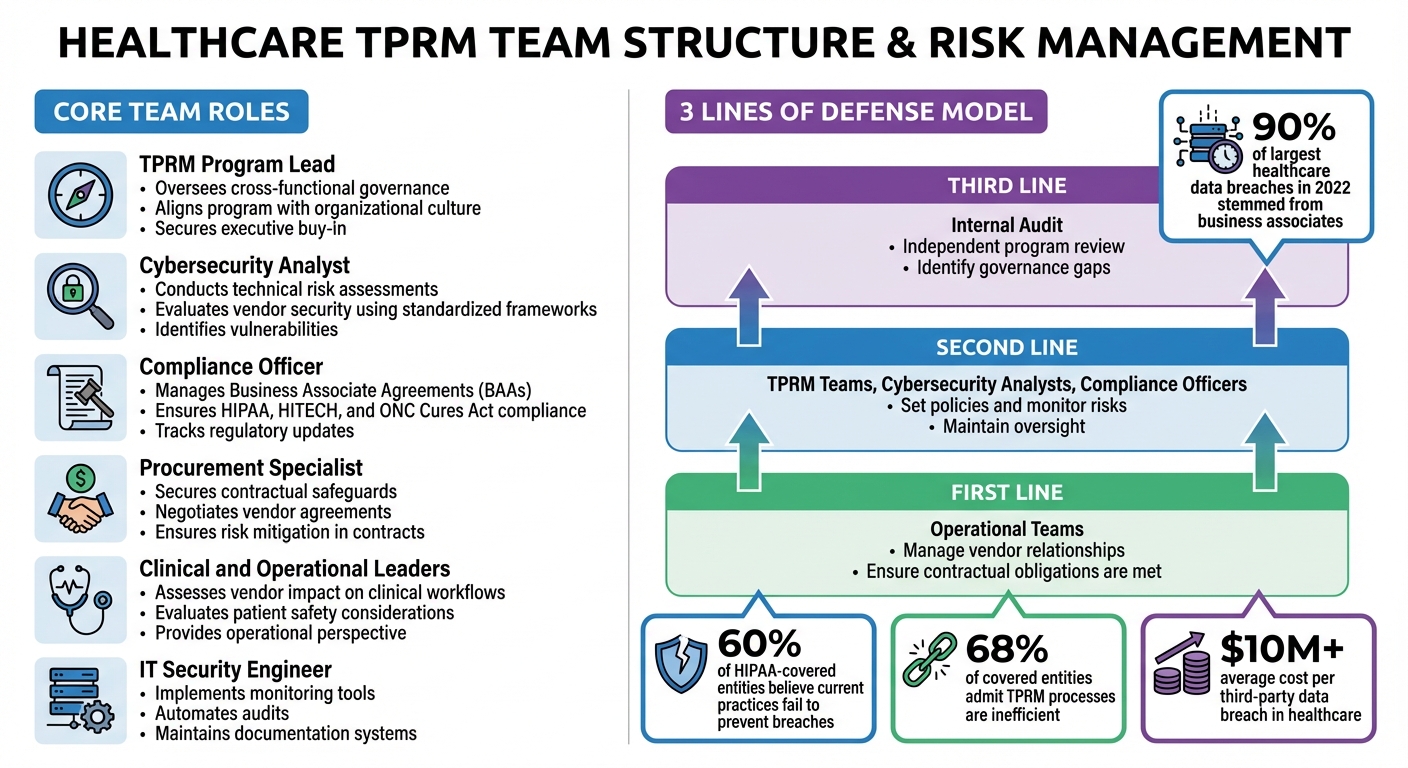
Healthcare TPRM Team Structure: Core Roles and 3 Lines of Defense Model
Required Positions in a TPRM Team
Building an effective Third-Party Risk Management (TPRM) team in healthcare means assembling professionals with complementary expertise. Why is this so critical? Consider this: in just one year, 55% of healthcare organizations experienced a third-party data breach [1]. Even more alarming, 90% of the largest healthcare data breaches in 2022 stemmed from business associates, not the covered entities themselves [1]. And the financial toll? Each third-party data breach in healthcare costs, on average, over $10 million per incident [1].
Here’s a breakdown of the key roles that make up a robust TPRM team:
- TPRM Program Lead: This role is all about leadership. The Program Lead oversees cross-functional governance, aligns the program with the organization’s culture, and ensures buy-in from executives and board members.
- Cybersecurity Analyst: These experts dive into technical risk assessments, evaluating vendor security using standardized frameworks to pinpoint vulnerabilities.
- Compliance Officer: Focused on regulatory adherence, the Compliance Officer manages Business Associate Agreements (BAAs) and ensures third-party practices align with HIPAA, HITECH, and the ONC Cures Act.
- Procurement Specialist: This role secures contractual safeguards during vendor selection and negotiations, ensuring risk mitigation starts at the agreement stage.
- Clinical and Operational Leaders: These individuals bring a critical perspective, assessing how vendor services impact clinical workflows and patient safety - something technical evaluations alone can’t fully capture.
- IT Security Engineer: Responsible for implementing tools to monitor vendor risks, streamline documentation, and automate audits, this role keeps the process efficient and organized.
"Establishing and adopting these more effective and efficient TPRM processes will transition TPRM in healthcare from a superficial check-the-box exercise that exposes organizations to unnecessary risks to more robust, collaborative information protection programs."
- Steve Alder, Editor-in-Chief, The HIPAA Journal [1]
The need for these roles becomes even more apparent when you consider the challenges: 68% of covered entities and 79% of business associates admit their TPRM processes are inefficient, and 60% of HIPAA-covered entities believe their current practices fail to prevent data breaches [1]. Having the right team in place isn’t just helpful - it’s essential. A well-structured team not only identifies risks but also strengthens the organization’s overall defenses.
The 3 Lines of Defense Model
The Three Lines of Defense framework provides a clear structure for managing roles and accountability in TPRM. It works like this:
- First Line: Operational teams manage vendor relationships and ensure vendors meet their contractual obligations.
- Second Line: This includes TPRM teams, Cybersecurity Analysts, and Compliance Officers. They set policies, monitor risks, and maintain oversight.
- Third Line: Internal Audit takes the lead here, independently reviewing the program’s effectiveness and identifying any gaps in governance.
This model prevents risk management from becoming isolated within IT or compliance departments. Instead, it creates a hub-and-spoke system, where a centralized TPRM hub (handling leadership and policy) collaborates with experts in cybersecurity, privacy, and legal. This ensures consistent oversight and comprehensive risk management [2]. By integrating these lines of defense, healthcare organizations can better protect patient data and maintain uninterrupted care delivery.
Responsibilities by Role
What Each Role Does
Every role within a Third-Party Risk Management (TPRM) program plays a key part in the five-stage risk management lifecycle: identify, assess, manage, monitor, and mitigate. This structured approach prevents silos and ensures accountability across the organization [3].
The TPRM Program Lead is responsible for setting the overall strategy, defining risk tolerance levels, managing cross-functional governance, and securing executive sponsorship to allocate necessary resources. They also promote a compliance-driven culture that values open communication, aligning the program with company values, regulatory requirements, and long-term objectives [4].
Cybersecurity Analysts focus on conducting technical vendor assessments, often using frameworks like NIST. Their work involves identifying vulnerabilities, evaluating security controls, and prioritizing risks to address potential issues before they escalate. Compliance Officers handle regulatory oversight, ensuring adherence to standards like HIPAA, HITECH, and the ONC Cures Act. They also manage Business Associate Agreements (BAAs) and track regulatory updates.
Procurement Specialists play a critical role during vendor negotiations by securing strong contractual safeguards. Meanwhile, Clinical and Operational Leaders evaluate how vendor services impact patient safety and clinical workflows - offering insights that go beyond technical evaluations. IT Security Engineers provide additional support by implementing monitoring tools, automating audits, and maintaining streamlined documentation to enhance efficiency.
Clearly defined roles help boost accountability and enable proactive risk management. Executive sponsorship ensures the program has the resources and cultural alignment needed to prioritize risk reduction effectively [4][5]. Advanced tools further enhance these efforts, as explored in the next section.
Tools That Support TPRM Responsibilities
To perform these responsibilities effectively, healthcare TPRM teams rely on advanced tools that integrate all stages of risk management. Censinet RiskOps™ is one such platform, transforming how healthcare organizations handle risks by automating the entire lifecycle. This centralized system allows teams to identify, assess, manage, monitor, and mitigate cyber risks in one unified ecosystem. It bridges Third-Party Risk Management (TPRM) with Enterprise Risk Management (ERM), aligning vendor-specific risks with broader organizational security goals [3].
Censinet AI™ takes risk management a step further by using artificial intelligence to streamline vendor assessments. Cybersecurity Analysts can complete evaluations faster and uncover vulnerabilities that manual processes might miss. The platform’s automation capabilities free up teams to focus on critical risk mitigation. TPRM Leads benefit from enhanced visibility and governance tools, while Compliance Officers gain real-time monitoring features to track regulatory compliance. Additionally, the platform offers pre-built programs based on healthcare cybersecurity best practices, eliminating the need to develop protocols from scratch.
This move toward RiskOps represents a shift away from manual, spreadsheet-driven processes to real-time collaboration and automated workflows. The result is a scalable, efficient program that saves time and resources while improving data security. When assembling your team, prioritize tools that provide automation and are tailored to the healthcare sector. These platforms not only streamline processes but also strengthen the collaborative framework that underpins effective risk management [3].
sbb-itb-535baee
How to Build and Structure Your TPRM Team
Steps to Assemble a TPRM Team
Start by securing executive sponsorship to ensure you have the authority and resources to enforce security measures effectively. Support from senior leadership is essential for holding vendors accountable and, when necessary, terminating relationships with those who fail to meet compliance standards. Without this backing, enforcing security requirements can become a significant challenge.
Next, define a clear maximum risk threshold to filter out high-risk vendors from the start. Using tools like security ratings can help automate this process, speeding up vendor evaluations and reducing manual effort.
Organize vendors based on their risk level. For example, vendors with access to critical clinical systems or protected health information (PHI) should undergo more rigorous assessments. This approach helps allocate resources where they’re needed most. A 2023 study revealed that 61% of organizations experienced a third-party data breach or security incident, marking a nearly 50% increase compared to the previous year [6].
Streamline the vendor intake process by using standardized forms and templates. This reduces communication delays and ensures you’re collecting consistent evidence of compliance across all vendors.
Once these internal processes are established, expand your efforts by collaborating with other departments to bring in specialized expertise.
Working Across Departments
After forming your core TPRM team, its success depends on engaging with multiple departments throughout the vendor lifecycle. Effective third-party risk management (TPRM) requires cross-department collaboration to address risks like operational, compliance, reputation, strategic, and credit risks - areas that general business units might not have the expertise to handle [7].
Procurement teams should align closely with legal experts to create standardized vendor contracts. These agreements should include mandatory security clauses, such as requirements for incident reporting, audit rights, and breach liability. By embedding these terms into contracts from the start, you can set clear expectations for vendors.
IT security teams and compliance officers should shift from annual assessments to continuous monitoring. Around-the-clock tracking of vendor connections and data feeds allows for quicker responses to suspicious activity. Cross-training team members is also critical, as it ensures everyone understands how their role fits into the broader risk management framework.
Healthcare organizations are increasingly joining industry consortiums to share due diligence data and standardize assessment criteria [7]. These collaborations minimize redundant vendor assessments and offer benchmarking insights. Consider participating in such initiatives to gain access to shared vendor risk intelligence while maintaining your organization’s specific security requirements.
How to Measure TPRM Team Performance
Key Performance Indicators (KPIs)
Assessing the performance of your Third-Party Risk Management (TPRM) team hinges on using clear, actionable metrics that align with your organization's goals and regulatory demands. As Ken Reiher, VP of Operations at ComplyAssistant, puts it: "KPIs serve as conduits between organizational ambitions and actual results achieved by vendors" [8].
Metrics related to operational efficiency - like how quickly your team completes vendor assessments or their on-time delivery rates - offer insight into workflow speed. Security and compliance indicators, such as audit success rates and the frequency of security breaches, help gauge adherence to standards like HIPAA and HITRUST. Additionally, service quality metrics, including SLA compliance and the quality of vendor deliverables, along with risk mitigation measures like mean time to remediate (MTTR) and risk remediation rates, highlight how effectively your team addresses identified risks [8].
Regulatory guidelines, such as CMS requirements, provide benchmarks: critical-risk issues must be resolved within 15 days, high-risk issues within 30 days, moderate risks within 90 days, and low-risk items within 365 days [11]. Monitoring discrepancies between vendor self-attestations and threat intelligence data is another key metric for identifying gaps in reporting [10].
To improve oversight, consider moving beyond annual assessments by adopting continuous monitoring. This approach ensures that any vendor whose risk profile exceeds acceptable thresholds is flagged immediately [8][9]. Another strategy is to create an Enterprise Risk Council with representatives from the CISO, procurement, and CFO offices. This council can help align your metrics with both business objectives and compliance requirements [10]. These metrics can then be integrated into dashboards, offering real-time visibility into vendor risks.
Using Dashboards to Track Progress
Dashboards are a powerful tool for turning raw data into actionable insights, offering a centralized view of vendor risks across your third-party ecosystem. Platforms like the Censinet RiskOps™ aggregate data from vulnerability scans, threat intelligence feeds, and assessment results, reducing the need for manual reporting and streamlining oversight [10].
A well-designed dashboard should present metrics for every stage of the vendor lifecycle, using visual tools like progress bars and color-coded alerts to prioritize risks effectively. For example, you can track financial scores during vendor sourcing, measure the mean time to onboard during the intake process, and monitor the number of offboarded vendors who still have data access during termination [10].
Real-time monitoring capabilities are particularly valuable, enabling automated alerts for significant changes in vendor risk profiles or emerging threats [9]. For instance, your dashboard can notify stakeholders immediately if a vendor's risk level surpasses predefined thresholds or if a data breach occurs.
This level of visibility is critical, especially in sectors like healthcare, where the financial stakes are high. In 2021, the average cost of a healthcare data breach reached $9.23 million - the highest across all industries for 11 consecutive years - and modern hospitals often depend on over 1,300 external vendors. With risks this significant, real-time tracking isn't just helpful; it's essential [12].
Conclusion and Next Steps
As outlined above, taking a well-rounded approach - covering everything from defining key roles to tracking performance - is critical for managing third-party risks effectively. Creating a strong Third-Party Risk Management (TPRM) team isn't just a good idea; it's a must. Consider this: 84% of businesses have experienced operational disruptions due to third-party risk oversights, and 33% have faced regulatory actions tied to TPRM failures. The stakes are even higher for healthcare organizations, where business associate breaches skyrocketed by 337% between 2018 and 2024, and the average cost of a healthcare data breach has reached $9.77 million [13][14].
"HIPAA's third-party requirements aren't suggestions. They're federal mandates with enforcement teeth that healthcare organizations can no longer afford to ignore." – Nasir R, Atlassystems [14]
Start by building a thorough vendor inventory. Audits frequently uncover upwards of 200–300 unmanaged business associate relationships [14]. From there, use risk-based tiering to classify vendors based on the sensitivity of the data they handle and their importance to your operations. This step ensures your resources are directed where they matter most, forming the backbone of a focused risk mitigation strategy.
Once you've organized your vendor landscape, integrating technology becomes essential. With vendor ecosystems growing more complex, manual processes just can't keep up. This is where AI-driven platforms like Censinet RiskOps™ come into play. These tools automate risk assessments, review evidence documentation, and facilitate continuous monitoring, turning raw data into actionable insights. Instead of waiting for an annual review, your team can track changes in vendor risk profiles in real time [13][14].
Finally, make sure your legal agreements are airtight. Update your Business Associate Agreements (BAAs) to comply with the 2013 Omnibus Rule, including clauses for subcontractor management and breach notifications. With HIPAA penalties reaching up to $2,134,831 per violation category, having clear contractual terms provides crucial financial protection [14]. Together, these steps create a comprehensive TPRM framework tailored for the unique challenges of the healthcare sector.
FAQs
What roles are essential for a successful healthcare TPRM team?
Creating a strong Third-Party Risk Management (TPRM) team in the healthcare sector starts with defining clear roles that address the unique challenges of managing vendor risks. While the structure may vary depending on the organization's size and priorities, several key positions are typically essential:
- Program Manager: Responsible for overseeing the entire TPRM program. This role ensures that the program aligns with the organization’s goals and complies with regulatory requirements.
- Risk Analyst: Focuses on evaluating vendor risks, keeping a close eye on compliance with security and privacy standards.
- Compliance Officer: Manages adherence to healthcare regulations, such as HIPAA, and handles the preparation and execution of audits.
- Legal Counsel: Reviews contracts and provides guidance on legal risks tied to third-party relationships.
- Security Engineer: Identifies technical vulnerabilities and implements security measures to safeguard sensitive patient data.
Each role contributes to a collaborative effort aimed at protecting patient information, staying compliant with healthcare regulations, and reducing risks tied to third-party vendors. The key to success lies in tailoring your team to meet the specific needs of your organization.
What are the best ways for healthcare organizations to evaluate the performance of their TPRM team?
Healthcare organizations can gauge how well their Third-Party Risk Management (TPRM) team is performing by focusing on measurable outcomes. For instance, they can track the percentage of third-party vendors that have been properly assessed and meet security standards. Progress toward achieving the HPH Cybersecurity Performance Goals is another critical benchmark, as is monitoring the decline in security incidents linked to third-party relationships.
Other useful performance indicators might include cost savings or the return on investment (ROI) tied to effective risk mitigation strategies. Additionally, measuring the average time taken to address and resolve identified risks can highlight the team's operational efficiency. Together, these metrics offer a clear picture of the team's contribution to the organization's cybersecurity efforts.
Why is ongoing monitoring essential for managing third-party risks in healthcare?
In third-party risk management (TPRM), keeping a constant eye on vendors isn't just a nice-to-have - it's a must. For healthcare organizations, this kind of vigilance ensures they can quickly adapt to shifts in a vendor's security posture. Vendor environments are anything but static; they can change overnight due to software updates, staffing adjustments, or newly discovered vulnerabilities. Without consistent monitoring, these changes could leave sensitive patient data exposed or put the organization at risk of violating regulations like HIPAA.
By routinely tracking key risk indicators, security controls, and compliance statuses, healthcare organizations can catch problems early - before they snowball into bigger issues. This approach not only helps in addressing risks proactively but also streamlines decision-making. Access to accurate, real-time data means teams can prioritize fixes, cut down on manual tasks, and improve their overall risk management strategies.
As regulations grow stricter and third-party cyberattacks become more common, staying informed about vendor activities is crucial. Whether it’s spotting a new vulnerability or identifying a lapse in controls, ongoing monitoring ensures risks are addressed promptly, safeguarding both patient data and the organization’s reputation.
Related Blog Posts
- Common Healthcare Third-Party Risk Assessment Questions
- How to Build a TPRM Team That Actually Reduces Healthcare Risk (Step-by-Step Guide)
- How to Build a TPRM Team That Actually Reduces Healthcare Risk (Step-by-Step Guide)
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?


