How Compliance Drives Healthcare IT Vulnerability Scans
Post Summary
Healthcare IT systems are under constant threat, and compliance regulations like HIPAA mandate regular vulnerability scans to protect sensitive patient data (ePHI). These scans are essential for identifying risks, but when treated as mere compliance tasks, they can fall short of addressing critical security gaps. Here's what you need to know:
- HIPAA Requirements: Regular scans and risk assessments are required to safeguard ePHI as part of the Security Rule. This includes both internal and external systems.
- Challenges: Compliance-only scanning often leads to infrequent scans, limited scope, and overwhelming findings without prioritization, leaving healthcare systems vulnerable.
- Best Practices: Shift from a reactive, compliance-focused approach to a risk-based strategy. This includes:
- Frequent scans for critical systems (e.g., EHRs, cloud platforms).
- Prioritizing vulnerabilities based on clinical impact and patient safety.
- Integrating scans into IT workflows for continuous risk management.
- Vendor and Device Considerations: Medical devices and vendor-managed systems require tailored strategies, including network segmentation and clear contract terms for vulnerability management.
Key takeaway: Compliance is the baseline, not the goal. A risk-based approach ensures healthcare organizations stay ahead of evolving threats while maintaining regulatory alignment.
Compliance Requirements That Drive Healthcare Vulnerability Scanning
HIPAA and HHS Requirements for Vulnerability Assessments
The HIPAA Security Rule lays out the legal framework for vulnerability scanning in U.S. healthcare. Specifically, §164.308(a)(1)(ii)(A) requires covered entities and business associates to assess potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information (ePHI). This isn’t a one-and-done process - ongoing risk analysis and periodic technical evaluations are necessary to ensure security measures remain effective as systems and threats evolve.
Healthcare organizations are expected to perform regular scans of networks, applications, and databases that handle ePHI. The Security Rule’s focus on technical safeguards emphasizes identifying system weaknesses that could jeopardize ePHI. Each identified vulnerability must be documented, along with risk ratings and steps for remediation, to show a commitment to continuous risk management.
While the Department of Health and Human Services (HHS) doesn’t specify exact scanning frequencies, guidance suggests conducting a comprehensive annual risk assessment. Additionally, high-risk systems often require more frequent evaluations. Out-of-cycle scans are also common after significant changes, such as electronic health record (EHR) upgrades, cloud deployments, network overhauls, acquisitions, or major security incidents that alter the threat landscape.
These regulations not only shape scanning practices but also expand the range of systems that must be assessed.
Expanded Scope of Compliance-Driven Scans
Regulatory requirements push organizations to cast a wide net when it comes to vulnerability scanning. HHS guidance mandates that risk analysis must cover every location and system where ePHI is stored or transmitted. This includes not only traditional IT infrastructure like servers and workstations but also platforms such as EHR systems, picture archiving and communication systems (PACS), medical devices, mobile devices, cloud environments, third-party solutions, and APIs connecting clinical applications. With the rise of cloud-based healthcare systems, which are frequent targets for ransomware and data breaches, vulnerability scanning for cloud-hosted systems has become a critical focus.
However, challenges arise with certain devices, such as regulated medical equipment and older clinical systems, which may not tolerate aggressive scanning. In these cases, HIPAA and HHS require organizations to identify risks and implement alternative safeguards. This might involve documenting system limitations, vendor constraints, and potential impacts on patient safety. Instead of invasive scans, organizations often use compensating controls like network segmentation, strict access controls, enhanced logging, and managed patching schedules. Vendor guidance, FDA advisories, and contractual terms often help define acceptable testing methods while ensuring risks are managed in line with HIPAA's "reasonable and appropriate" standard.
Documentation and Audit Requirements
To meet compliance expectations, healthcare organizations must thoroughly document their vulnerability management activities. OCR auditors look for detailed risk analyses that include vulnerability scanning as a core element of the security program. Documentation should cover scan reports with specifics like scope, tools used, dates, results, and methodologies (e.g., authenticated versus unauthenticated scans). Each finding should be assigned a risk rating, and a Plan of Action and Milestones (POA&M) should outline remediation steps, assign responsibilities, and set deadlines.
Periodic reviews are essential and should include leadership approvals, re-scans to confirm remediation efforts, and clearly defined policies for scan frequency and scope. These practices demonstrate that vulnerability management is an ongoing process, deeply integrated into the HIPAA Security Rule’s risk management framework. Organizations must also retain key records - such as scan reports, remediation logs, tool configurations, and evidence of compensating controls - so they’re readily available for OCR or other regulatory audits. By aligning these artifacts with HIPAA’s Administrative, Technical, and Physical Safeguards, organizations can show they have a structured, risk-based security program that satisfies compliance requirements.
Problems with Compliance-Only Vulnerability Scanning
Issues with Infrequent Scans and Limited Scope
Relying on vulnerability scans as a once-a-year task creates serious risks. Annual or even quarterly scans simply can’t keep up with the fast pace of IT changes, like new cloud workloads or updates to electronic health record (EHR) systems [1][5]. According to the ClearDATA 2024 Healthcare Threat Report, healthcare cloud workloads are prime targets for ransomware attacks and API exploits. Unpatched systems can be compromised in just days or weeks [5].
Another problem is the narrow focus of these scans. Limiting them to a handful of production servers while ignoring shadow IT, legacy clinical systems, third-party apps, or biomedical device networks leaves huge parts of the attack surface unchecked [1][7]. This approach not only clashes with HIPAA’s requirement for an ongoing, comprehensive risk analysis [1][2], but also creates a dangerous illusion of security. Passing an audit might look good on paper, but it can hide critical vulnerabilities. What’s worse, these limited scans often produce a flood of findings that lack context, making it hard to identify the real threats.
Overwhelming Findings Without Proper Prioritization
Compliance scans often churn out thousands of vulnerability findings, but they rarely provide the context needed to prioritize them effectively [7]. These reports typically use generic severity ratings, ignoring whether a system contains sensitive electronic protected health information (ePHI), supports critical clinical functions, or is exposed online. Without this context, IT teams - already stretched thin - can become overwhelmed by the sheer volume of alerts [1][7]. This alert fatigue often leads to teams addressing the easiest fixes or arbitrarily chosen items, rather than focusing on vulnerabilities that pose the most significant risks to patient data and clinical operations [1]. The absence of prioritization makes it even harder to move beyond a reactive approach to remediation.
Reactive Remediation vs. Continuous Risk Management
Compliance-driven programs tend to fall into a repetitive cycle: scan, fix, and forget until the next audit deadline. This reactive pattern leaves vulnerabilities lingering between scans. Censinet puts it bluntly: "Stop Chasing Questionnaires. Start Managing Risk." [6] When vulnerability management is treated as a periodic task rather than an ongoing process, it fails to integrate into daily IT operations.
Regulators, however, expect more than just occasional scans - they demand continuous risk management [1][2]. In fact, the Office for Civil Rights (OCR) often cites healthcare organizations for neglecting thorough risk analyses and failing to implement effective risk management, even when annual scans have been completed [1][2]. The message is clear: proving that a scan was performed once a year isn’t enough. Regulators want to see evidence of continuous, risk-based decision-making and active remediation tracking. Without this, organizations remain vulnerable to breaches and penalties between compliance cycles.
Building a Risk-Based Vulnerability Management Program
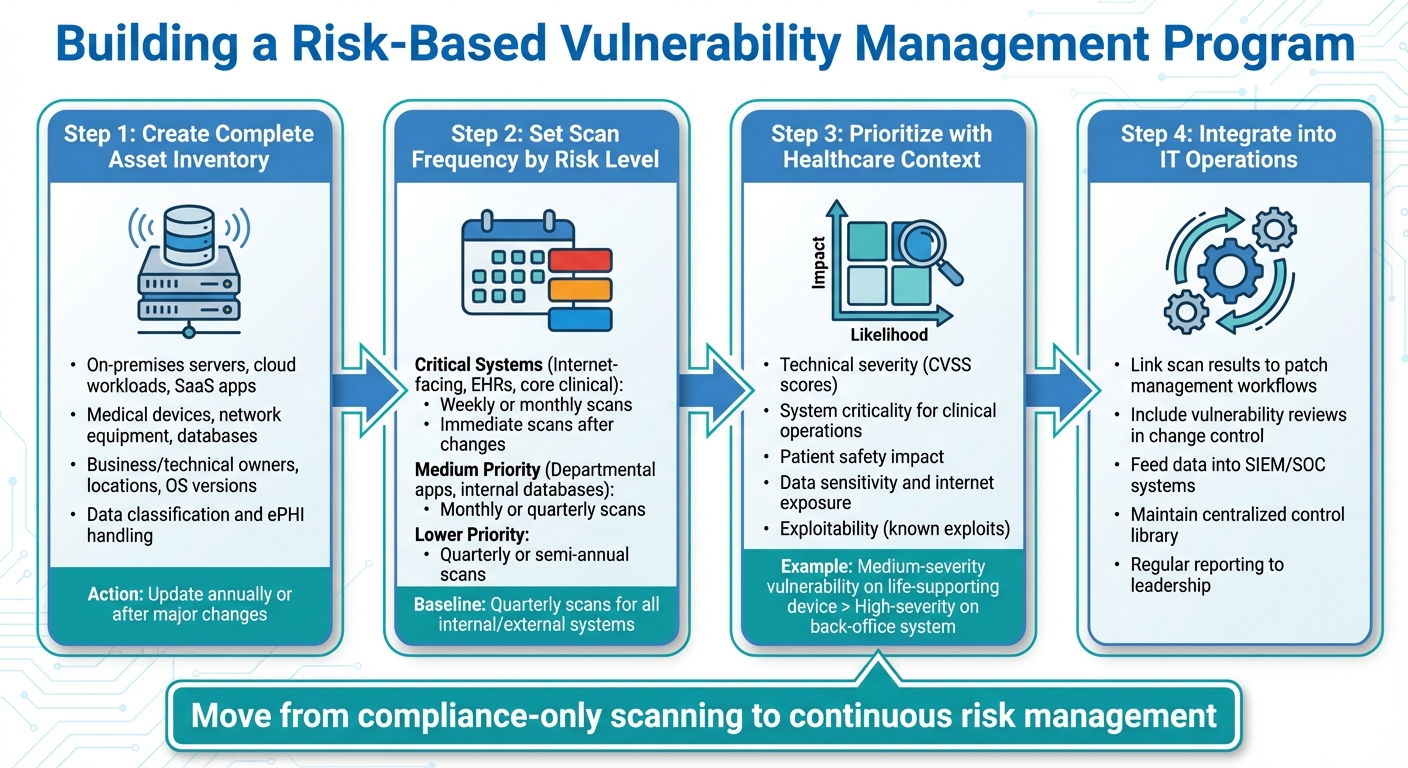
Building a Risk-Based Healthcare Vulnerability Management Program: 4 Key Steps
Creating a Complete Asset Inventory and Risk Analysis
Start by compiling a thorough inventory of all systems handling ePHI. This includes on-premises servers, cloud workloads, SaaS applications, and third-party hosted systems [1]. Your inventory should cover servers, endpoints, medical devices, network equipment, databases, user accounts, and integrations. Be sure to document details like business and technical owners, locations, operating systems, software versions, network segments, internet exposure, and data classification [1][8].
Next, map out how critical data flows between these systems. This helps you understand where ePHI is concentrated and how it moves [1]. For each asset, evaluate both the likelihood and impact of a potential compromise. Consider factors such as disruption to patient care, the sensitivity and volume of PHI, regulatory implications, and downtime tolerance. Record these risks in a register, assign accountable owners, and set remediation timelines. To stay accurate, update this inventory and risk analysis annually or after any major changes [1].
Setting Scan Frequency and Scope
Start with quarterly scans for both internal and external systems [3][4]. Then, categorize your assets by their criticality. Systems that are internet-facing, EHRs, core clinical systems, and high-value ePHI repositories should be scanned weekly or monthly, and immediately after major changes [1][3]. For these critical systems, include authenticated scans, configuration checks, and web application tests [1][3].
Medium-priority assets, like departmental applications and internal databases, should undergo monthly or quarterly scans with authenticated checks and network segmentation validation [1]. Lower-priority systems can be scanned quarterly or semi-annually, as long as changes are closely monitored [1]. For sensitive clinical networks where active scans could disrupt devices, use agent-based or credentialed scans, along with passive discovery tools [1]. Document your scan schedules and scope in your policies and risk analysis to ensure they align with both compliance and risk management goals [1][2].
Prioritizing Remediation with Healthcare Context
In healthcare, generic severity ratings don’t always tell the full story. To prioritize remediation effectively, combine technical severity (like CVSS scores), exploitability (including known exploits), system criticality for clinical operations, and the potential impact on patient safety. For example, a medium-severity vulnerability on a life-supporting medical device might take precedence over a higher-severity issue on a back-office system due to its direct effect on patient care [1][7].
Also, factor in data sensitivity, internet exposure, and any compensating controls, like strong network segmentation or monitoring [1][7]. Use risk scores from your formal analysis to align vulnerability tickets with their business impact and set appropriate service-level agreements. Document any accepted risks with leadership approval, including justifications tied to clinical and operational realities [1]. By integrating these priorities into daily IT workflows, you can maintain continuous protection.
Integrating Vulnerability Scanning into IT Operations
To make these strategies work, embed vulnerability management into your IT processes. For example, link scan results directly to patch management workflows so that critical vulnerabilities on key assets automatically generate prioritized change tickets with clear deadlines [1][5]. Make vulnerability reviews a standard part of your change control process, ensuring that major system changes or new deployments are accompanied by pre- or post-deployment scans [1].
Feed vulnerability data into SIEM/SOC systems to quickly correlate threats with alerts, unusual traffic, or other suspicious activity. This integration accelerates threat detection and response [1]. Maintain a centralized control library that tracks control owners, testing procedures, supporting evidence, and remediation progress. Regularly report risk metrics to leadership and governance teams to ensure accountability and validate investments [1][2].
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [6]
Platforms like Censinet RiskOps are specifically designed for healthcare, moving organizations from manual, questionnaire-based compliance to continuous risk management [6]. For instance, Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps enabled them to reallocate 3 FTEs, allowing the team to conduct significantly more risk assessments with just 2 FTEs [6]. This kind of efficiency is essential when transitioning from basic compliance scanning to a more comprehensive, risk-based approach.
sbb-itb-535baee
Managing Vendor and Medical Device Vulnerabilities
Working with Vendor and Device Limitations
Managing medical devices and vendor-managed systems comes with unique challenges that standard IT scanning methods simply can't handle. Medical devices often rely on FDA-regulated software, legacy systems, and proprietary protocols, which limit the ability to perform active scans or apply direct patches without jeopardizing certifications or disrupting clinical operations. Healthcare delivery organizations (HDOs) frequently lack administrative control over these devices, can't dictate patch schedules, and must carefully plan maintenance windows to avoid interfering with patient care. These factors significantly slow down the remediation process.
Adding to the complexity, many medical devices, like MRIs or infusion pumps, have a lifespan of a decade or more. This means devices purchased today could still be in use long after their operating systems are no longer supported. Studies of device inventories in U.S. hospitals often reveal that a significant percentage of devices run on outdated platforms. For critical devices - those that are always on, connected to patients, or vital for life support - even short interruptions for scanning or patching are unacceptable. As a result, HDOs often turn to alternative strategies like network segmentation, strict access controls, and enhanced monitoring instead of direct fixes. These challenges make it essential for organizations to negotiate proactive agreements with vendors to address vulnerabilities effectively.
Adding Vulnerability Requirements to Vendor Contracts
To tackle these limitations, it's crucial to include clear vulnerability management requirements in vendor contracts and business associate agreements (BAAs). For example, contracts should mandate regular vulnerability scans, sharing of high-level results, and timely remediation of critical issues - such as fixing critical vulnerabilities within 30 days and high-severity ones within 90 days. Additionally, breach and vulnerability notification timelines should align with HIPAA standards, requiring initial notice within 24–72 hours and detailed follow-ups that outline the root cause and impact of the issue.
Contracts should also include provisions like a right-to-audit clause, obligations for vendors to extend security requirements to their subcontractors, and rules for securely returning or destroying data when the contract ends. When acquiring new devices, involving teams from procurement, legal, and clinical engineering early in the process ensures that cybersecurity and vulnerability management expectations are baked into purchasing decisions. This approach sets clear security standards before the devices are put into use.
Using Censinet for Streamlined Risk Management

Given the complexity of managing vulnerabilities across numerous vendors and devices, manual processes are no longer practical. This is where Censinet RiskOps™ steps in. The platform centralizes vendor security questionnaires, BAAs, and vulnerability disclosures, making risk management far more efficient for healthcare organizations. It also connects healthcare delivery organizations with over 50,000 vendors and products through a collaborative risk network, simplifying the sharing of cybersecurity and risk data. By eliminating the need for cumbersome spreadsheet-based workflows, Censinet accelerates risk assessments and improves overall efficiency.
Terry Grogan, CISO at Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [6]
James Case, VP & CISO at Baptist Health, echoed this sentiment: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [6]
Maintaining and Documenting a Compliance-Aligned Vulnerability Program
Setting Up Governance and Accountability
To run an effective vulnerability program, it’s essential to establish clear governance and meaningful metrics. A cross-functional governance committee, led by the CISO and including representatives from IT, compliance, clinical leadership, biomedical engineering, legal, and vendor management, should oversee the program. Each member brings a unique perspective: IT and security teams handle scanning and remediation, compliance ensures alignment with HIPAA Security Rule safeguards, and clinical leaders prioritize vulnerabilities based on their potential impact on patient care while coordinating maintenance windows for clinical systems.
Responsibilities should be clearly defined and documented using tools like a RACI matrix. For example, security engineering teams might manage scans, system owners oversee remediation, and compliance ensures all documentation aligns with HIPAA requirements. These roles should be integrated into job descriptions, performance goals, and a formal risk register or Plan of Action and Milestones (POA&M), which tracks task owners and deadlines.
Tracking Metrics and Reporting
Metrics are key to driving improvement. Track scan coverage and remediation timelines, focusing on addressing critical vulnerabilities within 15–30 days and high-severity issues within 60 days. Use a POA&M or risk register to monitor overdue tasks and ensure accountability.
To gain executive buy-in, align these metrics with broader clinical and operational goals. For instance, showing how reducing unplanned downtime for systems like EHR or imaging improves patient care can highlight the program's value. Similarly, tracking fewer emergency patching events can demonstrate operational efficiency. Benchmarking against industry standards also offers a way to measure program maturity and advocate for necessary resources.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
– Brian Sterud, CIO, Faith Regional Health
Strong metrics not only improve program effectiveness but also lay the groundwork for maintaining audit-ready documentation.
Preparing Audit-Ready Documentation
Keeping well-organized records is essential for demonstrating a consistent, risk-based approach. This includes scan reports, penetration test results, and evidence of remediation, such as ticket screenshots, change records, configuration baselines, and patch logs. Each vulnerability should be documented with a risk rating (considering likelihood and impact), a clear treatment decision (e.g., remediate, mitigate, accept, or transfer), an assigned owner, a due date, and proof of resolution or formal risk acceptance.
Data from the HHS OCR reveals that failures in risk analysis and risk management are among the most common deficiencies cited in settlements and corrective action plans. To avoid such pitfalls, maintain a compliance calendar that schedules regular risk assessments, vulnerability scans, policy reviews, vendor reassessments, and training sessions. Tools like Censinet RiskOps can simplify this process by consolidating cybersecurity and risk data from vendors, medical devices, and enterprise systems into a single, centralized platform - eliminating the need for manual spreadsheets and ensuring a streamlined approach to documentation.
Conclusion: Using Compliance to Strengthen Healthcare IT Security
HIPAA and HHS requirements emphasize ongoing risk analysis, regular vulnerability assessments, and thorough documentation - key elements that form the backbone of continuous risk management. Under the HIPAA Security Rule, organizations are required to perform an "accurate and thorough assessment" of risks to electronic protected health information (ePHI) [2][5]. By treating these mandates as a starting point, healthcare organizations can evolve beyond routine compliance, creating a dynamic, risk-based program that prioritizes remediation based on clinical impact and patient safety.
To achieve this, healthcare organizations should exceed the standard quarterly scanning frequency, expand their coverage to include cloud environments and medical devices, and adopt risk-based prioritization. This approach transforms compliance activities into tools for ongoing risk reduction, allowing teams to focus on high-risk areas and connect each vulnerability to a documented risk and its responsible business owner.
Integrating vulnerability scanning into daily IT workflows ensures that remediation efforts enhance security without interfering with patient care. Tracking metrics like the average time to fix critical vulnerabilities, scan coverage, and patterns in recurring issues provides clear, audit-ready evidence of continuous improvement. This integration lays the groundwork for solutions that automate and consolidate risk management processes.
Advanced platforms, such as Censinet RiskOps, simplify this transformation by centralizing cybersecurity and risk data from vendors, medical devices, and enterprise systems into one unified solution. By eliminating reliance on manual spreadsheets, these tools enable healthcare organizations to manage risk consistently across all compliance-related areas. This consolidation supports a comprehensive, risk-based strategy, aligning with the principles outlined above. When HIPAA's requirements are treated as the foundation of a year-round vulnerability management program, IT teams can not only meet audit standards but also significantly enhance their overall security posture.
FAQs
What are the benefits of using a risk-based approach over compliance-only scans for managing healthcare IT vulnerabilities?
A risk-based approach to managing healthcare IT vulnerabilities prioritizes identifying and addressing the most pressing threats by evaluating their potential impact and likelihood of occurrence. This strategy ensures resources are used wisely, focusing on vulnerabilities that could significantly compromise patient data, clinical systems, or overall operations.
Unlike compliance-only scans that are designed to meet regulatory requirements, a risk-based method dives deeper into your organization's security landscape. By aligning vulnerability management with actual risks, healthcare organizations can actively minimize threats, improve patient safety, and uphold trust in their IT systems.
What are the key challenges of implementing vulnerability scans in healthcare IT systems?
Healthcare IT faces distinct hurdles when implementing vulnerability scans. One of the biggest concerns is navigating strict regulations like HIPAA while safeguarding sensitive patient information. On top of that, healthcare IT systems are incredibly intricate, with a mix of diverse technologies, medical devices, and applications. This complexity demands scanning methods that are specifically tailored to each environment.
Another major challenge is maintaining continuous monitoring without interfering with critical clinical operations. Any disruption could directly affect patient care, making this a delicate balancing act. Limited resources - whether it's staffing or technology - can also make it tough to establish and sustain effective scanning practices. And let’s not forget the constant need to adapt to fast-changing cyber threats, all while managing privacy concerns and ensuring smooth day-to-day operations.
How can healthcare organizations address vulnerabilities in medical devices and vendor-managed systems?
Healthcare organizations face unique challenges when it comes to securing medical devices and vendor-managed systems. One effective way to tackle these issues is by embracing continuous risk management practices. Tools like Censinet RiskOps™ make this process more efficient by automating vulnerability assessments, providing real-time risk monitoring, and simplifying compliance tasks. This reduces the need for manual effort while strengthening overall security.
Working closely with vendors is another key element. By fostering shared risk management efforts and comparing practices against industry benchmarks, organizations can quickly identify and address vulnerabilities. This proactive strategy not only protects patient data, medical devices, and critical systems but also ensures compliance with healthcare regulations.


