Cross-Border Data Transfers: Compliance Checklist
Post Summary
Managing cross-border data transfers in healthcare is complex but essential. Sensitive health data often moves between countries for care, billing, research, and more. However, strict U.S. and international laws, like HIPAA, GDPR, and China's PIPL, impose tough compliance rules. The new U.S. Department of Justice (DOJ) restrictions, effective April 2025, add another layer, limiting transfers of bulk health and genomic data to certain countries.
Key Steps for Compliance:
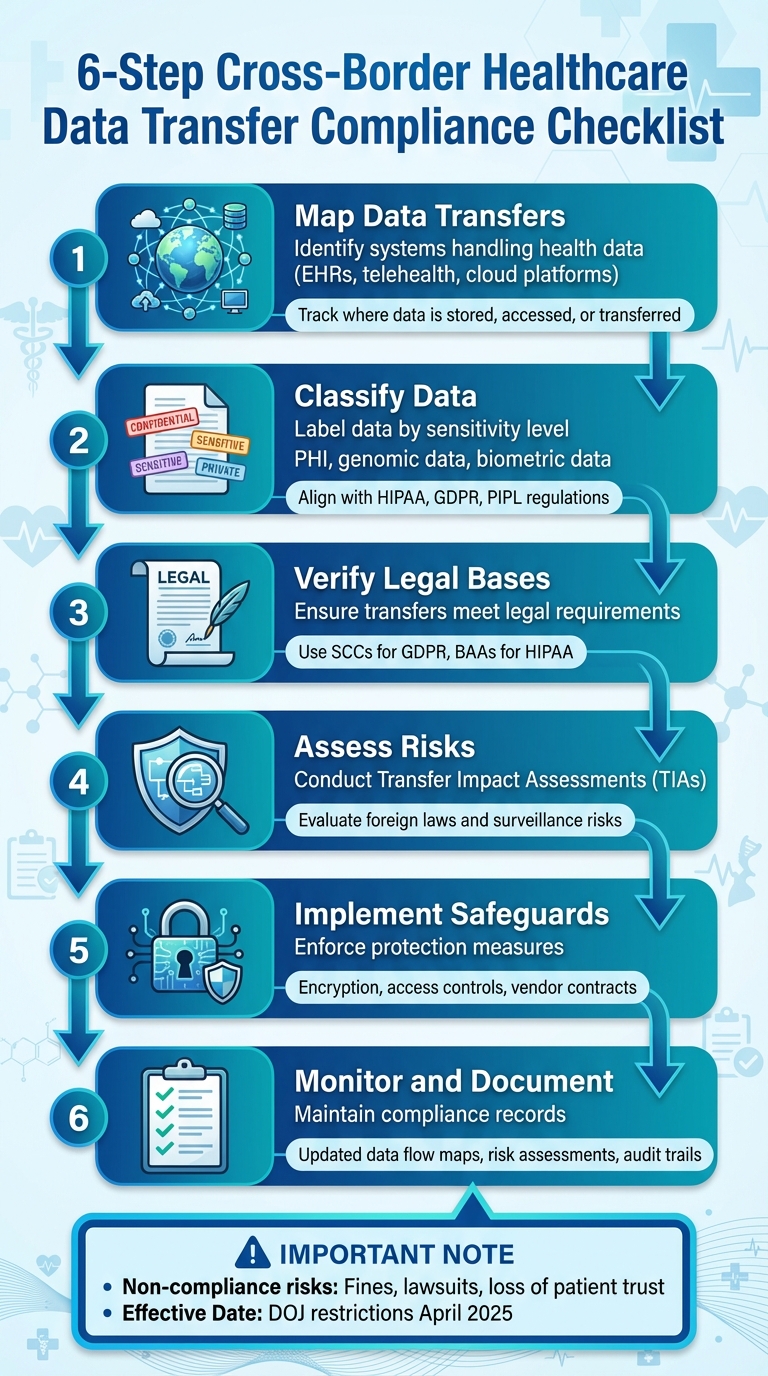
- Map Data Transfers: Identify systems handling health data (e.g., EHRs, telehealth platforms) and track where data is stored, accessed, or transferred.
- Classify Data: Label data by sensitivity (e.g., PHI, genomic data) and align with regulations like HIPAA or GDPR.
- Verify Legal Bases: Ensure transfers meet legal requirements, using tools like Standard Contractual Clauses (SCCs) for GDPR or BAAs for HIPAA.
- Assess Risks: Conduct Transfer Impact Assessments (TIAs) to evaluate risks tied to foreign laws and surveillance.
- Implement Safeguards: Enforce encryption, access controls, and strict vendor contracts to protect data.
- Monitor and Document: Maintain updated data flow maps, risk assessments, and compliance records.
Non-compliance risks are high, including fines, lawsuits, and loss of trust. Tools like Censinet RiskOps™ can simplify vendor management and compliance tracking. Staying ahead of evolving laws is critical for protecting patient data and avoiding penalties.
6-Step Cross-Border Healthcare Data Transfer Compliance Checklist
Map and Classify Your Data Transfers
Understanding how data moves, where it goes, and who accesses it is the cornerstone of any cross-border compliance program. Without this knowledge, it’s impossible to apply the correct legal safeguards or identify prohibited transfers before they occur.
Identify Systems and Data Types
Start by creating a complete inventory of systems across your organization. Use IT asset management tools and configuration databases to gather data, and verify it with teams like clinical, research, billing, and security to uncover shadow IT or departmental tools that might not be on the official list. Pay special attention to systems that store or process protected health information (PHI), such as:
- Electronic health records (EHRs)
- Patient portals
- Telehealth platforms
- Cloud-based imaging and lab systems
- Revenue cycle and billing platforms
- Population health and analytics tools
- Patient engagement and mobile apps
- Research data repositories
- Identity and access management systems that interact with third-party services
Don’t forget about less obvious systems. Collaboration tools used for case reviews, medical device gateways that send data to vendor clouds, outsourced coding and revenue cycle management (RCM) platforms, offsite backup systems, and vendor support tools with remote access to production systems are all potential sources of cross-border data flows. For each system, document whether hosting, backup, support, analytics, or development activities occur outside the U.S., and note if foreign-based staff or contractors have remote access.
Once your systems are cataloged, classify the data types each one handles according to relevant legal frameworks. For example:
- Under HIPAA, flag all PHI and electronic PHI (ePHI), including identifiers, clinical notes, test results, and billing records.
- Under GDPR, identify personal data and special category data, such as health, genetic, or biometric information.
- Under China’s PIPL, classify sensitive personal information like health and biometric data.
- For the U.S. DOJ rule, highlight “U.S. sensitive personal data,” which includes health, biometric, genomic, and geolocation data - even if encrypted or de-identified - when transferred to certain countries of concern.
Also, tag records with attributes like children’s data, reproductive health data, mental health and substance use data, genomic datasets, and government-related health data (such as for federal employees or TRICARE beneficiaries). These categories often require stricter restrictions or risk assessments. With this classification complete, diagram the flows to capture all access points and transfers.
Map Data Flows and Access Points
Using your system inventory, visually map how data moves across borders. Start with a reference system, such as an EHR, and use diagrams and logs to track data flows. For each flow, document:
- Origin system and location (e.g., on-premises in Texas)
- Data types involved (PHI, imaging, genomic data)
- Transfer method and protocol (APIs, SFTP, VPN, web portals)
- Intermediate processors (health information exchanges, cloud services)
- Storage locations and regions
- Destination entities and jurisdictions, including sub-processors
Pay special attention to remote access scenarios, such as offshore support engineers accessing U.S.-hosted systems, external clinicians logging in from other countries, or third-party analysts pulling data from U.S. environments. Regulators in the EU, UK, and China - and under the DOJ rule - often consider these scenarios as transfers, even when the data remains stored in the U.S.
Use standardized data flow diagrams organized by system or use case, and maintain these maps in a central governance, risk, and compliance (GRC) platform. This allows updates to vendors or hosting locations to automatically reflect in your transfer maps. Tools like Censinet RiskOps™ (https://censinet.com) can help healthcare organizations centralize and continuously update these maps. Periodically validate your flows using packet captures or cloud provider logs to catch any unintentional transfers or region changes.
Classify Use Cases and Sensitivity Levels
Once data flows are mapped, organize transfers by their purpose to align safeguards with data sensitivity. Create a consistent taxonomy of use cases, such as:
- Direct patient care (treatment, telehealth)
- Payment and operations (billing, RCM, quality reporting)
- Research and clinical trials
- AI and machine learning (ML) for analytics
- Population and public health reporting
- Vendor maintenance and support
- Education and training
- Marketing or patient engagement
Assign a primary purpose to each transfer, along with any secondary purposes - for instance, clinical data sent to a cloud-based AI tool for both decision support and model training. This is important because different regulations impose varying rules based on purpose. For example, GDPR may allow treatment-related transfers but require additional safeguards for research or marketing. PIPL enforces stricter rules for profiling and automated decision-making. The DOJ rule permits some regulatory or safety-related transfers but prohibits others, such as bulk genomic data transfers to specific countries.
To manage risks, implement a tiered sensitivity model to label data by risk level:
- Level 1: Public or de-identified data with minimal re-identification risk
- Level 2: Internal data without direct patient identifiers
- Level 3: Individual-level PHI or health data
- Level 4: High-risk or special category data (e.g., genetic data, children’s data, reproductive health data)
- Level 5: Mission-critical or legally restricted datasets
Calibrate these levels using legal definitions. For example, HIPAA PHI should be at least Level 3, while GDPR special category data and PIPL sensitive information should be Level 4 or higher. Data classified as “U.S. sensitive personal data” under DOJ rules - such as bulk health or genomic data - should default to Level 4 or 5, especially if it involves countries of concern. Use quantitative thresholds where possible, such as datasets containing 10,000 or more U.S. individuals in a 12-month period, to determine whether data qualifies as “bulk.”
Integrate these sensitivity labels into workflows like EHR exports, ETL pipelines, and vendor intake processes. This ensures that high-risk data (Levels 4 and 5) cannot move across borders without proper safeguards or additional review, minimizing compliance risks.
Establish Legal and Regulatory Compliance
Once you’ve mapped out data flows and classified their sensitivity, the next step is ensuring compliance with legal and regulatory requirements. Healthcare organizations must navigate a complex web of laws, including HIPAA/HITECH in the U.S., GDPR/UK GDPR in Europe and the UK, PIPEDA in Canada, and China’s PIPL. Each framework comes with its own set of rules, and a single data transfer often needs to meet multiple standards simultaneously.
Determine Applicable Laws and Regulators
Start by mapping where your data originates, where it’s going, and who has access to it. For each location, identify the relevant privacy laws. For example:
- HIPAA applies to Protected Health Information (PHI) within the U.S.
- GDPR/UK GDPR governs personal data of individuals in the EU and UK.
- PIPEDA applies to Canadian data.
- PIPL covers data originating in China.
Additionally, consider the U.S. Department of Justice’s "bulk sensitive personal data" rule (28 C.F.R. Part 202), effective April 8, 2025. This rule restricts certain data transfers and access involving "countries of concern" (e.g., China, Russia, Iran, North Korea, Cuba, and Venezuela). Even if the data is de-identified, pseudonymized, or encrypted, the rule may still apply when dealing with large-scale datasets or access by individuals linked to these countries.
Next, identify the regulators overseeing each transfer. For instance:
- In the U.S., agencies like HHS/OCR and the FTC may have jurisdiction.
- Transfers involving EU or UK data fall under their respective data protection authorities.
- In Canada, the Office of the Privacy Commissioner enforces PIPEDA.
- For China’s PIPL, the Cyberspace Administration of China (CAC) oversees compliance.
To streamline this process, create a jurisdiction and regulator matrix tied to your systems and vendors. Tools like Censinet RiskOps™ can centralize this mapping and help keep it updated as vendors or hosting locations change.
Verify Legal Bases and Transfer Mechanisms
Refer to your data flow maps to ensure that every transfer aligns with the legal requirements of the applicable frameworks. Let’s break this down:
- HIPAA: Confirm that the data qualifies as PHI and that the transfer is for a permitted purpose, such as treatment, payment, operations, public health, or research. Offshore vendors or affiliates handling PHI must have a Business Associate Agreement (BAA) that includes privacy and security provisions. Ensure this agreement extends to subcontractors as well.
- GDPR: Determine a legal basis for processing (e.g., contract performance, compliance with a legal obligation, or public health interest). Use valid transfer mechanisms like Standard Contractual Clauses (SCCs), adequacy decisions (e.g., the EU-U.S. Data Privacy Framework), or Binding Corporate Rules (BCRs). If relying on SCCs, conduct a Transfer Impact Assessment (TIA) to evaluate the recipient country’s surveillance laws and whether additional safeguards are needed.
- PIPEDA: Ensure the transfer serves a lawful purpose, obtain meaningful consent if required, and implement contractual protections. Be transparent about any foreign processing of data.
- PIPL: Verify that the transfer has a statutory basis and an approved export mechanism, such as passing a CAC security assessment, using standard contracts, or obtaining certification. This is particularly important for critical or high-volume data.
Keep detailed records linking each system or vendor to the data categories involved (e.g., PHI, biometric data), the legal basis, and the transfer mechanism. For example: “EU patient imaging data → U.S. cloud: GDPR Article 6(1)(f) and Article 9(2)(h); SCCs with supplemental measures.”
For transfers subject to the DOJ rule, implement the required security controls, such as strong encryption, access monitoring, and recordkeeping. Update contracts to include due diligence, audit, and reporting requirements. These measures should complement HIPAA’s privacy and security rules, but where DOJ or CISA restrictions are stricter, adjust your BAAs and vendor management processes accordingly.
| Framework / Rule | Governs Cross-Border Health Data | Key Transfer Mechanisms / Requirements |
|---|---|---|
| HIPAA/HITECH (U.S.) | PHI handled by covered entities and business associates | BAAs, Privacy & Security Rules, appropriate safeguards |
| DOJ Rule (28 C.F.R. Part 202) | Bulk sensitive personal data (e.g., health, genomic, biometric) and transfers involving countries of concern | Enhanced security controls, due diligence, and reporting requirements |
| GDPR / UK GDPR | Personal data of EU/UK subjects, including health data, transferred to third countries | Adequacy decisions, SCCs, Binding Corporate Rules |
Conduct Risk and Impact Assessments
After verifying legal bases, assess the risks associated with each transfer. Regulators increasingly expect organizations to evaluate foreign surveillance laws, government access risks, and the effectiveness of technical and organizational measures.
Under GDPR, a Data Protection Impact Assessment (DPIA) is mandatory when processing - particularly cross-border transfers - poses a high risk to individuals’ rights. This might include large-scale processing of sensitive data, systematic monitoring, or combining datasets in ways that could significantly impact patients. In the U.S. and Canada, similar requirements may arise from research ethics frameworks or institutional policies, especially for large research registries. For China’s PIPL, high-volume or critical data exports often require security assessments with a similar focus.
A Transfer Impact Assessment (TIA) should include:
- A description of the transfer: data categories (e.g., PHI, genomic data), data subjects (patients, clinical trial participants), purposes (e.g., care coordination, research), recipients (e.g., cloud providers, analytics vendors), and frequency.
- An analysis of the recipient country’s laws and practices regarding government access and surveillance, along with available redress mechanisms.
- Documentation of residual risks and compensating controls to ensure compliance.
Implement Safeguards and Governance Controls
Once legal and risk assessments are complete, the next step is to put compliance into action. This involves weaving data protection measures into contracts, technical systems, and everyday procedures. The aim? To create a robust framework that safeguards patient data while meeting the overlapping requirements of regulations like HIPAA, GDPR, PIPEDA, China's PIPL, and the new U.S. Department of Justice (DOJ) rule limiting bulk sensitive data transfers to certain countries.
Contractual Safeguards with Vendors and Partners
Every vendor or partner handling sensitive health data - whether it's PHI, genomic data, or biometric identifiers - must sign contracts that clearly outline their data protection responsibilities. Start by creating a global data protection addendum (DPA) template that can be attached to contracts involving cross-border data transfers. For contracts involving PHI, this addendum should include HIPAA Business Associate Agreement (BAA) terms, addressing key areas like permitted data uses, minimum necessary standards, breach reporting timelines, and audit rights for the HHS Office for Civil Rights.
For data transfers covered by the DOJ rule (effective April 8, 2025), the contracts need to go further. They must prohibit access by or transfers to "covered persons" in countries of concern - such as China, Russia, Iran, and others - unless exceptions apply and the transfer meets CISA's security standards. Vendors should provide assurances about data origin, ownership, and downstream access, particularly for bulk data thresholds like health data on 10,000 or more U.S. individuals or genomic data on 1,000 or more people within a year. For EU and UK transfers, include updated Standard Contractual Clauses (SCCs) and GDPR Article 28 terms, covering onward transfer restrictions and data subject rights.
Contracts should also specify security requirements tied to recognized frameworks. For example, require vendors to follow NIST-based controls like those in the NIST Cybersecurity Framework or NIST SP 800-53. Where the DOJ rule applies, include CISA-mandated security measures such as strong encryption, access controls, monitoring, and network segmentation. Breach reporting obligations should be clearly defined, with short timelines (24 to 72 hours), detailed content expectations, and a commitment to regulatory cooperation. To ensure compliance, grant your organization audit rights, such as reviewing security documentation, obtaining certifications like SOC 2 or HITRUST, and conducting audits.
Onward transfer restrictions are critical. Vendors must not engage sub-processors or affiliates outside approved jurisdictions without explicit consent and must extend equivalent contractual safeguards to all downstream parties. This is particularly important for GDPR's SCCs and the DOJ rule, which treat onward transfers as separate transactions. Contracts should also address data localization, retention, and deletion, specifying where data can be stored, how long it can be retained, and procedures for verified destruction.
A platform like Censinet RiskOps™ can simplify this process. It centralizes vendor security questionnaires, BAAs, DPAs, and compliance evidence, scores vendor risks, tracks remediation efforts, and maintains audit-ready documentation. This ensures consistent enforcement and readiness for regulatory reviews.
With contracts in place, the next step is enforcing these standards through technical measures.
Technical Security Measures
While contracts set the rules, technical controls ensure they're followed. Healthcare organizations must implement layered security measures to protect cross-border data flows, aligning with HIPAA, NIST standards, and the DOJ and CISA requirements.
Encryption is non-negotiable. Use TLS 1.2+ for data in transit and AES-256 for data at rest. Policies should prevent sharing encryption keys or KMS administration with "covered persons" in restricted countries.
Access control is equally essential. Apply role-based (RBAC) or attribute-based (ABAC) access methods to enforce least privilege. Require multi-factor authentication (MFA) for remote and privileged access, and restrict administrator access from high-risk jurisdictions. These measures align with HIPAA’s technical safeguards and CISA's requirements. Combine access controls with network segmentation and zero-trust principles to isolate sensitive databases - especially those containing bulk genomic or health data - from systems accessible to restricted entities.
Where feasible, use pseudonymization and de-identification to reduce exposure. Replace direct identifiers with tokens and store re-identification keys separately. This approach lowers the sensitivity of shared datasets, though some bulk de-identified data may still be considered sensitive under the DOJ rule, depending on context and volume.
Enable security monitoring and logging to detect suspicious activity. Use centralized log aggregation (SIEM), intrusion detection/prevention systems (IDS/IPS), and anomaly detection to flag large data exports, foreign IP access, or unusual privilege escalations. Retain logs long enough to support forensic investigations or regulatory inquiries.
Document these technical safeguards in an enterprise security standard, mapping each control to HIPAA requirements, NIST standards, and DOJ/CISA mandates. This documentation will be invaluable during audits or when onboarding new vendors.
With technical and contractual safeguards in place, governance ensures they remain effective over time.
Governance and Documentation
Safeguards only work when someone is accountable for them. Use data flow maps and risk assessments to build governance policies. Start by forming a cross-border data steering committee or working group that reports to executive leadership. Key members should include:
- A Chief Privacy Officer to oversee privacy laws and transfer mechanisms.
- A Chief Information Security Officer (CISO) to enforce technical controls and approve architectures involving cross-border access.
- Legal and compliance leads for contract management and regulatory interactions.
- Data owners (e.g., clinical, research, revenue teams) responsible for managing their data domains.
- A third-party risk management team to evaluate vendors, execute agreements, and monitor compliance.
This group should establish a formal Cross-Border Data Transfer Policy, outlining what data can leave the U.S., under what conditions, and with what approvals. They should also monitor dashboards tracking vendor risks, data transfer trends, and regulatory changes, ensuring that training reaches teams initiating data-sharing activities.
Maintain a centralized repository with data inventories, flow maps, and documented controls. Include details on systems, data types (PHI, genomic, biometric), destinations, and transfer mechanisms (SCCs, BAAs, exemptions). Store records of Data Protection Impact Assessments (DPIAs), executed contracts, vendor security questionnaires, certifications, and evidence of safeguards. Keep training logs to demonstrate staff awareness of policies and procedures. Finally, document incidents and breaches, including root causes, remediation steps, and regulatory notifications.
Review and update this documentation annually or whenever significant changes occur, such as new vendors, data flows, or regulations. The DOJ has provided a 90-day grace period (ending July 8, 2025) for organizations to demonstrate good-faith compliance efforts. By documenting these efforts now, healthcare entities will be better prepared for regulatory scrutiny.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health
Platforms like Censinet RiskOps™ can streamline governance tasks by automating workflows, managing vendor risks, and providing a centralized view of compliance efforts.
sbb-itb-535baee
Regional Compliance Requirements
When it comes to cross-border data compliance, regional regulations add another layer of complexity to the already intricate legal and governance frameworks. Unlike the United States' HIPAA and the DOJ's bulk sensitive data restrictions, there’s no universal standard governing international health data transfers. Instead, healthcare organizations must navigate region-specific rules. Some of the most challenging frameworks come from the European Union and United Kingdom (GDPR/UK GDPR), Canada (PIPEDA and provincial laws like Quebec Law 25), and China (PIPL and related health regulations). Each region enforces distinct legal and technical requirements for handling sensitive health data.
European Union and United Kingdom
Transferring patient data from the EU or UK to countries outside their respective zones requires a valid legal mechanism. Start by confirming if the destination country has an adequacy decision from the EU Commission or UK government. For U.S. transfers, the EU–US Data Privacy Framework and UK–US Data Bridge enable certified organizations to receive data, so check whether your vendors are certified for your services.
If no adequacy decision exists, you’ll need to use Standard Contractual Clauses (SCCs) for EU data or the International Data Transfer Agreement (IDTA) or UK Addendum for UK data. These contracts must be signed with each vendor handling EU or UK data. Additionally, you’re required to conduct a Transfer Impact Assessment (TIA) to evaluate the legal risks in the destination country and document any extra safeguards, such as encryption or access controls, you’ve implemented. This requirement stems from the Schrems II ruling, which invalidated the EU–US Privacy Shield and prompted many organizations to update their SCC arrangements.
Health data is classified as special category data under GDPR Article 9, meaning you need both a lawful basis (Article 6) and a specific condition for handling sensitive information. For high-risk cross-border projects - like international clinical trials or AI development using EU or UK patient data - you must also complete a Data Protection Impact Assessment (DPIA). Update your Records of Processing Activities (RoPAs) to document these transfers, and ensure data subject rights (such as access, deletion, or objection) are enforceable across borders. Clear mechanisms for complaints and redress should also be in place.
These measures align with U.S. standards and set the stage for compliance with Canadian and Chinese regulations.
Canada
Under PIPEDA, Canada allows cross-border transfers if you use contracts or safeguards that ensure equivalent protection and maintain accountability for data shared with third parties. To comply, determine whether your activities fall under federal PIPEDA or stricter provincial laws like those in Quebec, British Columbia, or Alberta. Notify data subjects about potential access by foreign authorities and ensure your contracts with processors and sub-processors meet PIPEDA’s accountability standards.
Quebec’s Law 25 introduces even stricter requirements. Before transferring data outside Quebec, you must conduct a Privacy Impact Assessment (PIA) to evaluate the sensitivity of the data, the purpose of the transfer, the safeguards in place, and the legal landscape of the destination. Transfers are only permitted if the assessment concludes the data will receive adequate protection. Contracts must include terms addressing security, use limitations, incident reporting, and data subject rights. Violations can result in steep penalties: administrative fines up to CAD $10 million or 2% of global turnover, and penal fines up to CAD $25 million or 4% of global turnover, whichever is higher.
Operationally, update privacy notices, patient intake forms, and patient portals to disclose where data may be stored or accessed, the types of data being transferred (e.g., lab results, imaging, genetic data), and the purposes (e.g., telehealth, clinical research). Use clear, layered notices and provide options for withdrawing consent when applicable. Train staff in registration, research, and telehealth to answer patient questions about cross-border data use. Maintain a confidentiality incident register and ensure cross-border transfers are integrated into your incident response and breach notification plans.
Since Canadian compliance varies by province, the complexity increases further when dealing with non-Western frameworks, like those in China.
China
China’s Personal Information Protection Law (PIPL) treats health data as sensitive personal information, requiring explicit consent for processing and transfer. You must disclose the foreign recipients and the purpose of the transfer. Before exporting data, determine if your organization qualifies as a Critical Information Infrastructure Operator (CIIO) or processes data on over 1 million individuals - either of which would trigger a government-led security assessment by the CAC.
Cross-border transfers under PIPL must comply with one of three mechanisms: (1) passing a CAC security assessment, particularly for CIIOs or large-scale processors; (2) signing standard contracts with foreign recipients and filing them with regulators; or (3) obtaining certification from approved bodies. Additionally, certain health-sector regulations require data localization, meaning primary storage must remain in China, and only the minimum necessary data can be exported for specific purposes like research. Exported copies must be tightly controlled, logged, and accessible to authorities.
PIPL’s extraterritorial scope means that even organizations without a physical presence in China must comply if they handle data about Chinese residents. Ensure Chinese-language notices and consents are in place, explicitly addressing cross-border transfers, and inform data subjects about potential risks. Prepare personal information protection impact assessments (PIPIAs) to document the necessity, proportionality, and safeguards for these transfers.
For transfers involving data from multiple jurisdictions - such as EU/UK, Canadian, or Chinese data - ensure that DOJ restrictions are reconciled with GDPR, PIPEDA, and PIPL obligations. This may require adjusting how you structure cloud services, analytics, or research collaborations with partners in regions of concern.
Simplifying Compliance
Given the complexity of these regional requirements, tracking and managing cross-border data transfers is no small task. Tools like Censinet RiskOps™ (https://censinet.com) can centralize third-party risk assessments, transfer inventories, contract reviews, and security benchmarks across regions. These platforms offer standardized questionnaires tailored by jurisdiction, automated alerts for high-risk data types (e.g., PHI, genetic data), and collaborative tools for addressing compliance gaps across your organization and third-party vendors.
Conclusion
Managing cross-border data transfers requires complete transparency and robust oversight. Using detailed data maps allows organizations to pinpoint transfers to high-risk countries, identify flows that might be categorized as "bulk" sensitive personal data under DOJ's 28 C.F.R. Part 202, and implement encryption, access controls, and contractual restrictions to mitigate risks effectively [1][2].
Each data transfer should comply with established legal and technical standards. For instance, a U.S. hospital working with an EU-based teleradiology provider must address HIPAA and GDPR requirements (using SCCs and transfer impact assessments), as well as DOJ regulations when applicable [1][2]. Similarly, contracts involving U.S.-based cloud providers with offshore support teams should incorporate DOJ-recommended language or equivalent measures to prevent unauthorized downstream transfers and ensure proper controls for restricted transactions [1][5].
To achieve compliance, organizations need layered safeguards, including updated BAAs, robust encryption, role-based access controls, and stringent contractual terms [1][2][3]. Relying on manual tools like spreadsheets becomes impractical when managing numerous vendors and data flows. Platforms such as Censinet RiskOps™ (https://censinet.com) streamline this process by centralizing questionnaires, evidence, and remediation workflows. These tools help U.S. health systems identify cross-border risks, prioritize high-risk relationships (like bulk data analytics or genomics), and document safeguards to satisfy auditors and regulators [1][3].
In addition to implementing safeguards, maintaining continuous oversight is critical. Cross-border health data regulations are constantly evolving. For example, DOJ's 2025 Final Rule under 28 C.F.R. Part 202 and CISA’s security requirements impose national security restrictions on bulk sensitive personal data transfers, even when the data is de-identified or encrypted [1][3]. Staying compliant means regularly monitoring regulatory updates, revising risk criteria, and auditing cross-border data configurations [1][4]. Leadership must designate executive responsibility - whether it's the CISO, Chief Privacy Officer, or CIO - for managing cross-border risks. This includes allocating budgets for data mapping, contract updates, and technical controls, as well as embedding cross-border considerations into broader enterprise risk and third-party governance frameworks [1][3].
FAQs
What are the main challenges healthcare organizations face with cross-border data transfers?
Healthcare organizations face a host of obstacles when it comes to managing cross-border data transfers. These challenges often stem from the need to comply with intricate international regulations, protect patient privacy, and maintain data security across multiple jurisdictions. To meet these demands, organizations must adopt strong legal measures, like data transfer agreements, and remain vigilant in tracking compliance with ever-changing laws.
The shifting landscape of global regulations adds another layer of complexity, making it tough for organizations to stay current and ensure consistent adherence. Tackling these issues is crucial - not just to safeguard sensitive patient information, but also to uphold trust in healthcare systems.
What impact do the new U.S. DOJ restrictions have on transferring health data to certain countries?
The U.S. Department of Justice (DOJ) has introduced tighter rules governing the transfer of health data to certain countries. These new restrictions demand adherence to stricter legal and security protocols, particularly when dealing with nations deemed high-risk or not aligned with U.S. regulations.
For healthcare organizations, this means cross-border data transfers could encounter delays or heightened scrutiny. To navigate these changes, it's crucial to review and adjust processes to meet the updated standards. Ensuring compliance not only helps avoid disruptions but also safeguards patient data and other sensitive information.
How can organizations comply with GDPR and PIPL requirements for cross-border data transfers?
To align with GDPR and PIPL requirements for cross-border data transfers, organizations should focus on several essential steps:
- Map your data: Identify where personal information is stored and how it moves across borders.
- Establish a legal foundation: Use mechanisms like Standard Contractual Clauses (SCCs) or Binding Corporate Rules (BCRs) to ensure compliance.
- Assess third-party safeguards: Confirm that any external data recipients have proper protections in place.
- Secure explicit consent: When necessary, obtain clear and informed consent from individuals.
- Strengthen security protocols: Use robust measures to protect data during transfers.
It's equally important to keep detailed records of these efforts and routinely evaluate your processes to stay up-to-date with changing regulations.


