FIPA vs. HIPAA: Differences for Healthcare Data Compliance
Post Summary
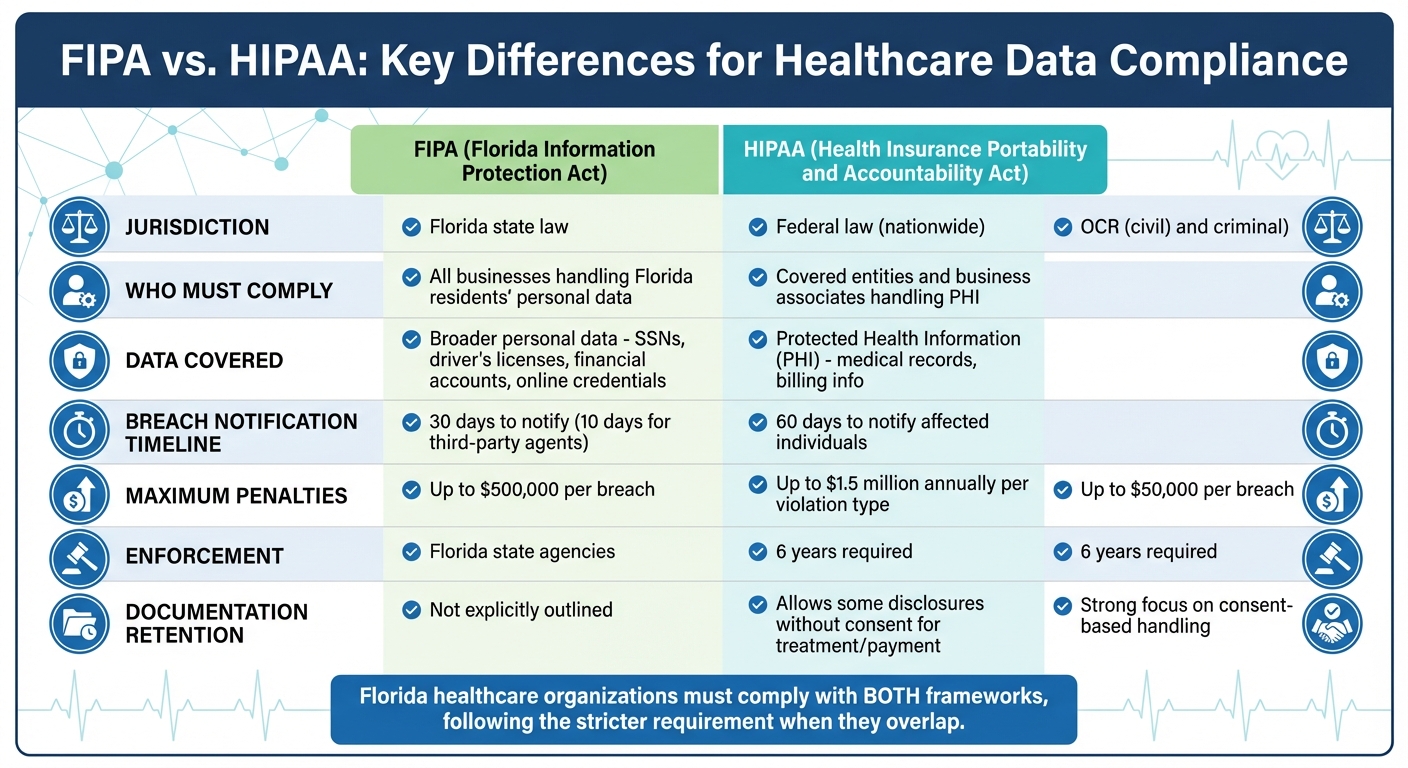
FIPA (Florida Information Protection Act) and HIPAA (Health Insurance Portability and Accountability Act) both aim to protect sensitive data, but they differ in scope, enforcement, and requirements. If you're a healthcare organization in Florida, you need to comply with both, as FIPA adds state-specific rules that go beyond HIPAA's federal standards.
Key Points:
- HIPAA applies nationwide to "covered entities" like healthcare providers and focuses on Protected Health Information (PHI).
- FIPA applies to any business handling Florida residents' personal data, including medical and non-medical information.
- Breach Notification Timelines: HIPAA allows 60 days, while FIPA requires notification within 30 days (and third-party agents must report breaches within 10 days).
- Penalties: HIPAA fines can reach $1.5 million annually per violation type, while FIPA violations can result in fines up to $500,000.
Quick Comparison:
| Feature | HIPAA (Federal) | FIPA (Florida) |
|---|---|---|
| Data Covered | PHI | Broader personal data (e.g., SSNs) |
| Who Must Comply | Covered entities and business associates | All businesses handling Florida residents' data |
| Breach Notification | 60 days | 30 days (10 days for third parties) |
| Max Penalties | $1.5M annually | $500K |
Healthcare organizations in Florida must align with both frameworks, prioritizing the stricter requirement where they overlap. Implementing a robust healthcare third-party risk management strategy can help ensure compliance across both frameworks.
FIPA vs HIPAA Compliance Requirements Comparison Chart
What It Means to Be HIPAA Compliant
sbb-itb-535baee
Main Differences Between FIPA and HIPAA
FIPA and HIPAA differ in their scope and requirements. For healthcare organizations in Florida, where both regulations apply simultaneously, understanding these differences is essential.
Scope and Jurisdiction
HIPAA is a federal law that establishes nationwide standards for protecting health information. It applies to "covered entities" and their business associates who handle Protected Health Information (PHI) on their behalf [3].
FIPA, on the other hand, is a Florida state law with a broader reach [2]. It applies to any business - regardless of industry or location - that collects, stores, or uses the personal information of Florida residents [2]. For example, a healthcare vendor in California processing data for Florida patients must still comply with FIPA, even without a physical presence in Florida.
Jeff Greenberg, Of Counsel at Howell, Buchan & Strong, explains: "FIPA (Florida Information Protection Act of 2014) is specifically a Florida law related to the security of confidential personal information which can extend beyond health information to personal data stored in electronic formats and data breaches" [2].
This creates a layered compliance challenge. A Florida hospital must adhere to HIPAA's federal standards for patient health data while also meeting FIPA's state-level rules for broader personal data categories.
Protected Data Categories
The types of data each law protects further highlight their differences. HIPAA focuses solely on Protected Health Information (PHI), which includes identifiable health information related to a person's medical history, healthcare services, or payment for those services. FIPA, however, covers a wider range of Personal Information, such as Social Security numbers, driver's license numbers, financial account details, and online account credentials [3][2].
For healthcare providers, this means that a breach involving patient billing information or login credentials could trigger FIPA's notification requirements, even if no medical records were compromised. This is particularly critical when managing risks associated with medical devices and other connected clinical technology. For instance, a breach of patient credit card details would fall under FIPA's 30-day notification rule, while a breach involving medical diagnoses would follow HIPAA's 60-day notification window for incidents affecting 500 or more individuals. To simplify compliance, many organizations adopt the shorter 30-day timeline across all data categories [2].
| Feature | HIPAA (Federal) | FIPA (Florida) |
|---|---|---|
| Data Covered | Protected Health Information (PHI) and billing info | Personal Information (SSNs, credit cards, online credentials) |
| Applicability | Covered entities and Business Associates | All businesses handling Florida residents' personal data |
| Max Penalties | $1.5 million per year [2] | $500,000 civil penalty [2] |
| Third-Party Breach Notification | Business Associate must notify entity within 60 days | Third-party agent must notify entity within 10 days [2] |
These differences shape how organizations handle breach notifications and enforcement, especially for those managing compliance with both laws in Florida.
Breach Notification Requirements
Healthcare organizations face the challenge of adhering to HIPAA's notification deadlines while also managing FIPA's stricter timelines in cases of data breaches. Failing to meet these deadlines can lead to hefty penalties. For instance, in January 2017, Presence Health, a Chicago-based health system, agreed to a $475,000 settlement after missing HIPAA's 60-day notification requirement [7]. Understanding these timelines and processes is critical to avoiding such consequences.
Notification Timelines and Processes
HIPAA requires covered entities to notify affected individuals within 60 days of discovering a breach. For breaches involving 500 or more individuals, organizations must also notify the HHS Secretary and prominent media outlets. In cases involving fewer than 500 individuals, reporting to HHS can be deferred until 60 days after the end of the calendar year [7].
By default, any unauthorized use or disclosure of protected health information (PHI) is considered a breach. However, a documented risk assessment can overturn this presumption if it shows a low probability of compromise. Factors like the nature of the PHI, the scope of access, and mitigation efforts are critical in this analysis. Importantly, encrypted data is exempt from notification requirements as long as the encryption key remains secure [7]. This contrasts with FIPA, which imposes a shorter notification window, adding complexity for healthcare organizations operating in Florida.
To stay compliant, healthcare organizations must design breach response plans that meet the most stringent deadlines, whether under HIPAA or FIPA. Staff training on immediate breach reporting is also crucial to minimize risks and avoid penalties [7].
Compliance Requirements and Penalties
Healthcare organizations must navigate distinct compliance rules under HIPAA and FIPA, covering data protection, staff education, and recordkeeping. Understanding these frameworks is critical to avoid hefty fines and maintain patient confidence.
Comparing Compliance Obligations
HIPAA outlines specific administrative, physical, and technical safeguards to secure electronic protected health information (ePHI). These include mandatory security training for all staff, strict data disposal protocols, and procedures for removing health information from electronic devices before reuse. Additionally, organizations are required to keep documentation of policies, procedures, and risk assessments for six years after creation or last use [11].
FIPA, on the other hand, focuses on limiting access to personal health information based on a "need to know" principle [4]. While it mandates protections against unauthorized copying, modification, or disposal [5], FIPA does not demand the same detailed technical measures as HIPAA. Consent is another key difference: FIPA emphasizes consent-based data handling [4], whereas HIPAA allows certain disclosures without consent for purposes like treatment, payment, or healthcare operations [8].
| Compliance Area | HIPAA | FIPA |
|---|---|---|
| Training Requirements | Security training required for all staff [11] | Limits access to "need to know" [4] |
| Data Disposal | Specific controls for device/media disposal [11] | General security requirements [4] |
| Documentation Retention | Must be retained for 6 years [11] | Not explicitly outlined |
| Access Standards | "Minimum necessary" for disclosures [8] | "Need to know" for legitimate purposes [4] |
| Consent Requirements | Allows some disclosures without consent [8] | Strong focus on consent-based handling [4] |
The frameworks not only differ in their compliance measures but also in the financial and operational risks tied to non-compliance.
Penalties for Non-Compliance
The financial penalties for non-compliance vary significantly between HIPAA and FIPA. HIPAA employs a four-tier penalty system based on the level of negligence. Fines for unknowing violations range from $100 to $50,000 per instance, while violations due to reasonable cause range from $1,000 to $50,000 [6]. For intentional violations that are corrected, fines increase to $10,000 to $50,000 per violation, and uncorrected intentional violations can result in penalties of up to $1.5 million annually per violation type [6][8].
"HIPAA violations can result in penalties of up to $1.5 million/year per type of violation - but more importantly, they erode trust, damage your brand, and can break partnerships or contracts." - Tejaswi, Author, Azpirantz [6]
HIPAA enforcement is handled through civil penalties led by the OCR and criminal penalties led by the DOJ [9][10][8]. In contrast, FIPA violations are enforced by Florida state agencies [9][10][8].
How to Ensure Dual Compliance
Healthcare organizations in Florida face the challenge of adhering to both FIPA and HIPAA regulations, with the stricter standard taking precedence when FIPA's requirements surpass those of HIPAA. For instance, FIPA mandates a 30-day breach notification timeline, while third-party agents must notify within 10 days. Additionally, organizations must broaden their data protection measures to include personal data like Social Security numbers, driver's license numbers, and financial account details - not just protected health information (PHI) [1][12]. Furthermore, any offsite patient information must be stored within the United States, its territories, or Canada [13]. These measures are essential to maintaining patient trust and ensuring smooth operations.
"Whenever one law is stricter than the other, entities must ensure that they are complying with the stricter law." - Monica McCormack, Compliancy Group [12]
Using Technology for Compliance
Managing dual compliance manually can lead to missed deadlines and increased risks. Technology platforms offer a solution by automating the monitoring of conflicting breach notification requirements, ensuring adherence to FIPA's tighter timelines.
For example, Censinet RiskOps™ simplifies third-party risk assessments, cybersecurity benchmarking, and compliance management for both FIPA and HIPAA. This platform automates processes like third-party risk management and data discovery, helping organizations identify and protect the broader range of personal information covered under FIPA. With real-time data presented in an easy-to-navigate dashboard, healthcare providers can continuously monitor their compliance status, address critical issues promptly, and ensure timely remediation.
By combining automated tools with robust internal policies, organizations can effectively manage dual compliance requirements.
Best Practices for Healthcare Organizations
To effectively navigate dual compliance, healthcare organizations should adopt the following strategies:
- Conduct Annual Security Risk Assessments: These assessments help identify vulnerabilities in the third-party healthcare ecosystem and implement necessary fixes. They should address HIPAA's administrative, physical, and technical safeguards, as well as FIPA's broader data protection requirements [12].
- Develop a Comprehensive Incident Response Plan: This plan should include reporting procedures for both the Florida Attorney General and the Department of Health and Human Services. If a breach impacts more than 1,000 individuals, it should also outline steps for notifying consumer credit reporting agencies [1][12].
- Update Third-Party Contracts: Ensure contracts reflect FIPA's 10-day notification requirement and that all Business Associate Agreements account for both FIPA and HIPAA frameworks [2].
- Provide Regular Training: Annual training on HIPAA, FIPA, cybersecurity, and secure data disposal reinforces internal policies and helps maintain compliance [12][13].
Florida healthcare providers must also confirm their compliance with offshore storage restrictions during initial license applications and renewals [13].
"Compliance is a less cumbersome burden if it is introduced into your business model early on and assessed often." - Jackie Bain, Attorney [1]
"Having legal oversight of your business operations and a review of your policies and procedures to ensure both FIPA and HIPAA are accounted for can help mitigate future concerns and penalties." - Jeffrey Greenberg, Of Counsel, Howell, Buchan & Strong [2]
The Stakes of Non-Compliance
Violations of FIPA can lead to civil penalties of up to $500,000 per breach, while HIPAA violations can result in fines as high as $1.5 million [2]. Beyond financial repercussions, non-compliance can damage patient trust and harm critical business relationships. By leveraging the right technology and adopting these best practices, healthcare organizations can efficiently meet their dual compliance obligations, safeguard patient data, and maintain operational stability.
Conclusion
FIPA and HIPAA address the protection of sensitive health information from different angles, yet they work together to support quality patient care. While their scopes and specific mandates vary, both frameworks empower individuals with rights like accessing their records, requesting corrections, and understanding how their data is shared.
Healthcare organizations must adhere to the more stringent regulation in any given situation, whether it's stricter breach notification timelines or broader data protection rules. The financial risks of non-compliance are steep - HIPAA violations, for instance, can result in fines of up to $1.5 million per year [15].
"A major goal of the Privacy Rule is to assure that individuals' health information is properly protected while allowing the flow of health information needed to provide and promote high quality health care and to protect the public's health and well being." - U.S. Department of Health and Human Services [14]
Staying compliant often requires leveraging modern compliance tools. Solutions like Censinet RiskOps™ simplify the challenge of managing both frameworks by automating real-time compliance tracking and streamlining risk assessments. When paired with strong policies, regular staff training, and thorough incident response plans, these tools help healthcare organizations meet regulatory demands more effectively, safeguard patient trust, and maintain operational efficiency.
FAQs
When do I have to follow FIPA instead of HIPAA?
In British Columbia's public sector, including health authorities and hospitals, the Freedom of Information and Protection of Privacy Act (FIPA) sets the rules for handling health information. Meanwhile, in the United States, the Health Insurance Portability and Accountability Act (HIPAA) governs how healthcare providers and related entities manage health data.
If you're dealing with health information, make sure to follow FIPA for Canadian public sector organizations and HIPAA for U.S.-based entities. Each law has specific requirements tailored to its region and sector, so understanding the distinction is critical for compliance.
What is considered “personal information” under FIPA in healthcare?
Under FIPA, "personal information" in healthcare includes any identifiable details about a person’s physical or mental health, the healthcare services they’ve received, their payment or eligibility for care, or organ and tissue donations. This applies to both spoken and recorded information.
How should Florida providers handle the 10-day third-party breach notice?
Florida providers are required to notify the Department of Legal Affairs about any breach involving more than 500 records within 30 days of discovery, as mandated by FIPA (Florida Information Protection Act). This timeline is stricter than HIPAA's 60-day reporting requirement. Meeting FIPA's shorter deadline is crucial to avoid penalties and ensure effective breach management.


