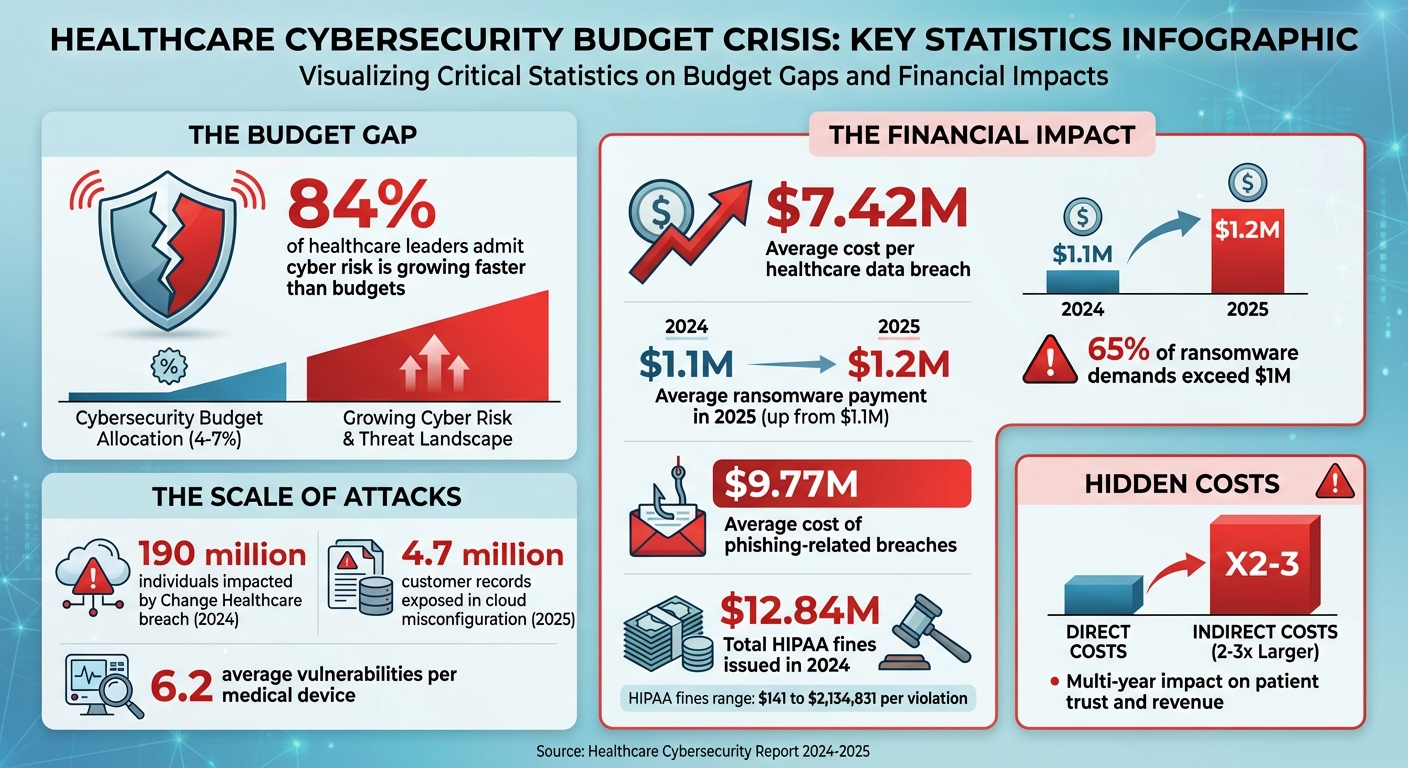
84% of healthcare leaders admit risk is growing faster than budgets. Sound familiar?
Post Summary
Healthcare organizations are facing a dangerous gap: cyber threats are advancing faster than the budgets meant to address them. With 84% of leaders acknowledging this growing risk, the sector is left exposed to escalating attacks like ransomware, phishing, and data breaches. Despite the alarming trends, many providers allocate only 4% to 7% of IT budgets to cybersecurity, while threats grow more sophisticated and costly.
Key Takeaways:
- Rising Costs: Average healthcare data breaches now cost $7.42M per incident, with ransomware demands exceeding $1M in 65% of cases.
- Underfunding Risks: Limited budgets leave critical gaps, especially for smaller facilities, risking patient safety, operational disruptions, and regulatory fines.
- Actionable Steps: Focus on affordable, high-impact measures like multi-factor authentication, phishing training, timely patching, and vendor risk management.
Healthcare leaders must prioritize smarter, cost-effective strategies to safeguard patient data and operational stability without waiting for budget increases.
Healthcare Cybersecurity Costs and Budget Gap Statistics
Why Cyber Risks Are Growing Faster Than Budgets
More Attacks, More Sophisticated Methods
Cybercriminals are stepping up their game, using advanced tools to launch highly targeted attacks. For example, attackers now leverage AI to craft phishing emails that are almost impossible to distinguish from legitimate ones. AI also speeds up reconnaissance, helping hackers find and exploit vulnerabilities with precision [2][4][5].
Consider the ransomware attack on Change Healthcare, owned by UnitedHealth, in 2024. This breach impacted around 190 million individuals, disrupting claims processing and exposing millions of personal health records. The root causes? A lack of multi-factor authentication on a critical system and reliance on outdated technologies [1]. Similarly, during the early months of the COVID-19 pandemic in 2020, Brno University Hospital in the Czech Republic - one of the country’s key COVID-19 testing centers - was hit by ransomware. The attack forced staff to delay surgeries and revert to manual record-keeping as their systems failed [9].
These incidents highlight how attackers are evolving their tactics, creating new challenges for today’s digital infrastructure.
Growing Digital Infrastructure Creates More Vulnerabilities
The rapid expansion of healthcare technologies has opened up new entry points for cybercriminals. Digital tools like electronic health records, Internet of Medical Things (IoMT) devices, cloud platforms, and third-party integrations have significantly increased the attack surface [6].
IoMT devices, including connected pacemakers, infusion pumps, and diagnostic equipment, are particularly vulnerable. Many run outdated software or lack adequate encryption [6][9]. A 2018 study revealed that medical devices had an average of 6.2 vulnerabilities each [3]. Kathy Hughes, CISO at Northwell Health, explains:
IoT (Internet of Things) devices are, in my opinion, computers with operating systems (OS), similar to other types of computers - and those devices are susceptible to the same cyber threats. She added that IoT devices have a small OS and that security is a bolt-on rather than built-in [3].
Cloud adoption adds another layer of risk. In one case from 2025, a major U.S. health insurance provider accidentally exposed 4.7 million customer PHI records over three years due to a misconfigured cloud storage bucket [6]. Third-party vendors also pose significant risks, especially when they have direct access to sensitive data but lack proper vetting [6][8]. On top of that, mergers create additional hurdles, as organizations struggle to integrate different systems while maintaining compliance [7].
Budget and Staffing Limitations
Despite the growing complexity of cyber threats, healthcare organizations often find themselves limited by tight budgets and staffing shortages. A lack of skilled cybersecurity professionals slows down incident response, delays crucial system updates, and leaves organizations more vulnerable to attacks [7][11]. Budget constraints force many healthcare leaders to prioritize day-to-day operations over security, leaving critical gaps [6].
Smaller and rural healthcare providers face even greater challenges. With limited budgets and fewer IT staff, these organizations become prime targets for cyberattacks. The resource gap often results in extended system downtimes, data breaches, risks to patient safety, and significant financial repercussions [6][7][10].
The Real Costs of Underfunded Cybersecurity
Direct Costs: Immediate Financial and Operational Losses
Underfunding cybersecurity programs can lead to immediate and serious financial setbacks for healthcare organizations. One of the clearest examples is ransom payments. By 2025, the average ransom payment had risen to $1.2 million, up from $1.1 million in 2024, with 33% of ransomware victims reporting that their organizations had paid the demanded amount[12]. In 2024, a staggering 65% of ransom demands in the healthcare sector exceeded $1 million.
Regulatory fines also contribute to these financial burdens. In 2024, the U.S. Department of Health and Human Services' Office for Civil Rights issued $12.84 million in fines to healthcare providers for HIPAA violations[6]. These fines ranged from $141 to as much as $2,134,831 per violation[6]. Additionally, phishing-related breaches in healthcare carried an average cost of $9.77 million per incident[6].
Operational disruptions compound these financial losses. Cyberattacks can cripple essential systems, such as electronic health records (EHRs) and patient scheduling platforms. This leads to canceled appointments and even the diversion of ambulances to other facilities. The result? Increased risks of medical errors and, in some cases, higher patient mortality rates during the crisis. These immediate losses are just the beginning, paving the way for far-reaching consequences.
Indirect Costs: Long-Term Business Impacts
While the immediate financial hit from cyber incidents is severe, the long-term effects can be even more damaging. Hidden costs, such as reputational damage and eroded patient trust, often exceed the initial expenses by two to three times. When personal health information is exposed, organizations are forced to spend heavily on advertising and public relations campaigns to restore their image. Cyber insurance premiums also tend to spike after an incident.
Reputation damage doesn't fade quickly. It can take years to rebuild trust, and during that time, patient acquisition and retention often suffer. Prolonged operational downtime further exacerbates revenue losses, stretching the financial impact well beyond the initial attack. Delaying necessary security upgrades to save costs only increases vulnerabilities, creating a cycle of escalating expenses. For smaller facilities, these combined financial and reputational hits can be devastating, sometimes forcing them to shut down entirely.
Direct vs. Indirect Costs Comparison
The table below highlights the financial implications of both direct and indirect costs:
| Cost Type | Description | Example Dollar Amounts |
|---|---|---|
| Direct Costs | Ransom payments, regulatory fines, legal fees, breach response, system recovery | Ransom: $1.2M average; HIPAA fines: $141–$2,134,831; Phishing breach: $9.77M average |
| Indirect Costs | Reputational damage, lost trust, higher insurance premiums, deferred security upgrades, prolonged revenue losses | 2–3× larger than direct costs; Multi-year impact on patient acquisition and retention |
sbb-itb-535baee
How to Manage Cyber Risks Within Budget Constraints
Focus on High-Impact, Low-Cost Security Measures
When resources are limited, it’s essential to prioritize security strategies that offer the most protection for the least cost. For example, multi-factor authentication (MFA) is a simple yet powerful tool to prevent unauthorized access. It’s affordable and significantly reduces the chances of account breaches. Similarly, secure email gateways and phishing awareness training are cost-effective ways to protect against email-based attacks, which are a common entry point for cybercriminals.
Other practical steps include timely patching and regular data backups. These actions help close known vulnerabilities and ensure quick recovery in case of an attack. Implementing basic access controls - restricting employee access to only the systems and data they need - can also reduce risks from insider threats or compromised accounts. These measures are inexpensive but require consistent application.
| Security Measure | Cost | Benefit |
|---|---|---|
| Multi-Factor Authentication (MFA) | Low | Prevents unauthorized access even with stolen credentials |
| Phishing Awareness Training | Low | Reduces user errors, a major cause of breaches |
| Timely Patching | Low | Fixes vulnerabilities before attackers exploit them |
| Secure Email Gateways | Low–Medium | Blocks malicious emails before reaching users |
| Basic Access Controls | Low | Limits data access to reduce exposure |
| Regular Data Backups | Low–Medium | Enables quick recovery without paying ransom |
Once these basics are in place, turn your attention to external risks.
Strengthen Vendor and Third-Party Risk Management
Third-party vendors often pose significant risks, especially in industries like healthcare, where they may handle sensitive data such as protected health information (PHI). Tools like Censinet RiskOps™ can simplify vendor risk management. This platform centralizes vendor security documentation, automates assessment workflows, and continuously monitors vendor security. By streamlining these processes, healthcare organizations can effectively address vendor risks without exceeding budget limits.
Automation tools can further enhance efficiency in managing risks.
Leverage AI and Automation to Save Time
Manual risk assessments take up valuable time and can strain already overworked security teams. AI tools like Censinet AI™ can automate much of this process. For instance, vendors can complete security questionnaires in seconds, while the AI summarizes their responses, reviews documentation, and identifies risks, including fourth-party exposures. The result? Comprehensive risk reports generated in a fraction of the time.
Generative AI is also proving useful for routine cybersecurity tasks like validating evidence or drafting policies. By automating these repetitive jobs, AI allows security teams to focus on more complex challenges. A human-in-the-loop approach ensures accuracy while maintaining the critical thinking needed for strategic decisions.
Use Metrics to Justify Budget Increases
Securing additional cybersecurity funding requires more than hypothetical scenarios - it demands hard data. Track metrics such as incident rates, costs of system downtime, response times for threats, and vendor risk scores. Comparing your organization’s security posture to industry benchmarks can highlight gaps and make a stronger case for investment.
Tools like Censinet RiskOps™ provide real-time dashboards that consolidate risk data, helping you clearly show vulnerabilities and the financial risks of ignoring them. By linking specific security measures to reduced costs or operational benefits, you can build a compelling argument for increased funding. When you demonstrate how targeted investments protect both finances and operations, budget requests are far more likely to succeed. Data-driven proposals resonate because they connect spending to tangible outcomes.
Conclusion
Cyber threats are advancing faster than many healthcare budgets can keep up. Organizations in this sector are grappling with increasingly sophisticated attacks, an expanding digital footprint, and a maze of third-party risks - all while managing slim margins and a shortage of skilled security professionals. Meeting these challenges requires smarter strategies, not just bigger budgets.
The key lies in prioritizing effectively. Start with impactful yet cost-efficient measures, like implementing multi-factor authentication and providing focused employee training. Incorporate AI and automation to handle routine tasks, freeing your team to tackle more complex threats. Use data-driven insights to clearly show leadership how targeted investments can lower risks and safeguard operations.
Platforms tailored for healthcare, such as Censinet RiskOps™, bring everything - risk assessments, vendor management, and compliance tracking - into one streamlined system. Meanwhile, tools like Censinet AI™ can reduce vendor assessment times from weeks to mere seconds. The reality is, cybersecurity can’t wait for budget increases. By adopting smarter approaches, healthcare providers can strengthen their defenses, protect patient safety, and stay ahead of ever-evolving cyber risks - all without overspending.
FAQs
What are the most budget-friendly ways to improve cybersecurity in healthcare?
To strengthen cybersecurity without overspending, focus on a few key strategies: conduct regular risk assessments, enforce strict access controls, and use data encryption to protect sensitive information. These steps ensure that your data is shielded from potential threats.
On top of that, invest in network monitoring, vendor risk management, and automated threat detection tools. These tools help you spot and address vulnerabilities quickly, keeping your systems secure.
Don’t overlook the importance of frequent data backups and having a solid incident response plan in place. These measures can significantly reduce downtime and data loss if a breach occurs. Using a framework like NIST CSF can also help you organize your cybersecurity efforts, ensuring resources are used wisely to protect patient data and maintain compliance.
What steps can healthcare providers take to manage risks from third-party vendors effectively?
Healthcare providers can tackle third-party vendor risks by implementing a well-structured vendor risk management framework. This process should involve detailed security assessments, confirming that vendors meet stringent cybersecurity requirements, and keeping a close eye on their security measures.
Consistent monitoring plays a crucial role in spotting vulnerabilities before they become bigger problems. It's equally important to maintain open communication with vendors to address risks promptly and ensure their practices align with your organization's security objectives. By following these steps, providers can effectively reduce risks without exceeding budget limitations.
Why is the gap between cybersecurity risks and healthcare budgets growing?
The divide is growing as cyber threats become increasingly advanced and frequent, while healthcare budgets often lag behind. Several factors drive this problem, including the high worth of protected health information (PHI), a surge in ransomware attacks, weaknesses in third-party vendors, and the ever-present risk of human error.
Even with higher spending, many healthcare organizations find themselves stretched thin, struggling to allocate enough resources for robust security measures. Tackling this issue means focusing on affordable strategies that address the most pressing risks, ensuring sensitive data stays protected.


