HIPAA Access Control Requirements Explained
Post Summary
Access control is a key part of HIPAA's Security Rule, ensuring that only authorized individuals or systems can access electronic protected health information (ePHI). This rule applies to healthcare providers, health plans, and their business associates. Here's a quick breakdown of the core requirements:
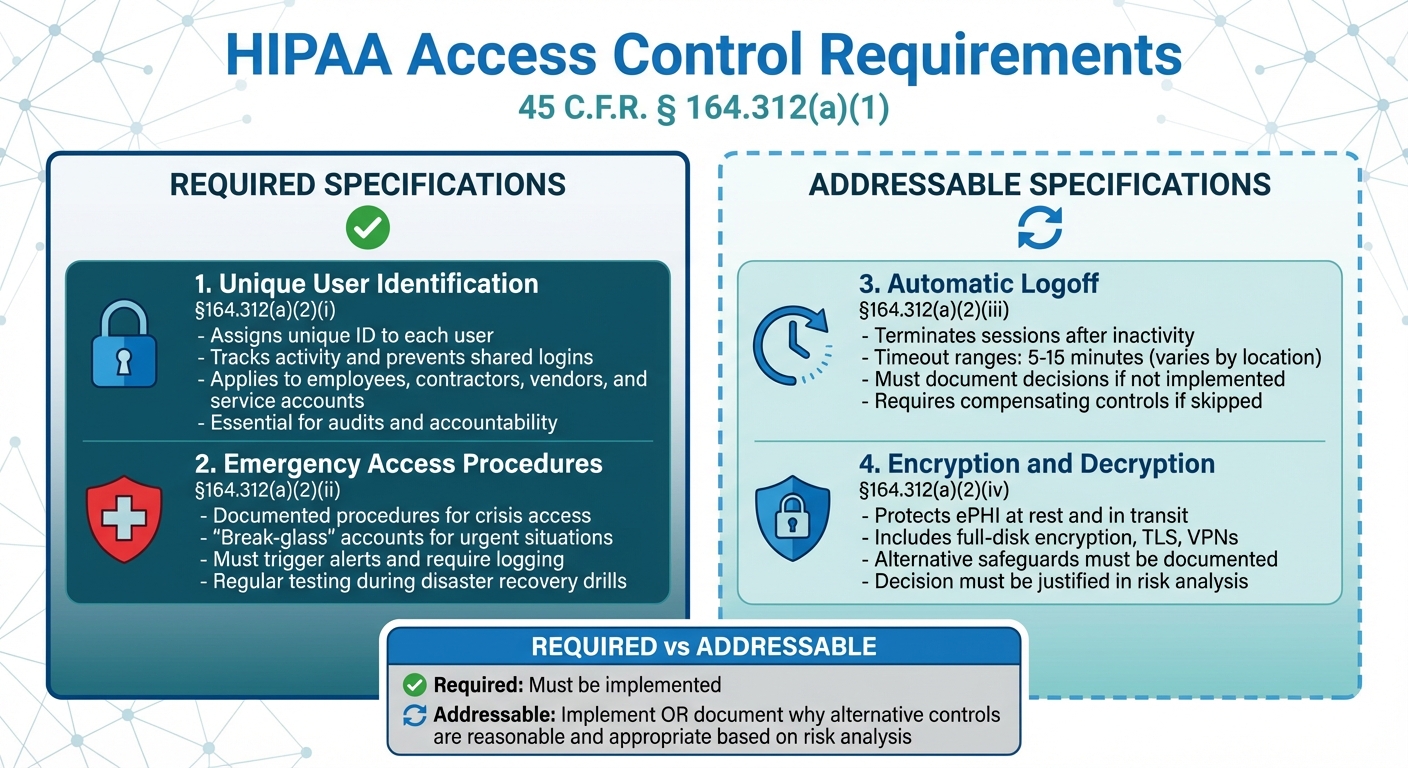
- Unique User Identification (Required): Assigns a unique ID to each user to track activity and prevent shared logins.
- Emergency Access Procedures (Required): Ensures secure access to ePHI during crises like system outages.
- Automatic Logoff (Addressable): Logs users out after inactivity to reduce risks.
- Encryption and Decryption (Addressable): Protects ePHI by making intercepted data unreadable.
Organizations must conduct regular risk analyses, define access needs, and document their decisions, especially for addressable measures. By implementing these safeguards, healthcare entities can protect patient data, meet compliance standards, and reduce risks of breaches or penalties.
HIPAA Access Control Requirements: Required vs Addressable Specifications
HIPAA Access Control Requirements Under the Security Rule
HIPAA Access Control (45 C.F.R. § 164.312(a)(1)) sets technical policies to ensure that only authorized users or programs can access electronic protected health information (ePHI). It includes two mandatory measures - Unique User Identification and Emergency Access Procedures - along with two addressable specifications: Automatic Logoff and Encryption/Decryption. If an organization decides not to implement the addressable measures, it must document its reasoning.
When drafting the Security Rule, the U.S. Department of Health and Human Services opted to remove strict requirements for "role-based" or "context-based" access. This gives organizations the freedom to adopt any access control methods that meet the standard, without requiring specific tools like a particular encryption product or multi-factor authentication system. Instead, entities are expected to choose measures that align with their size, complexity, technical capacity, and the risks identified in their risk analysis.
Each requirement plays a role in protecting ePHI. Let’s break them down.
Unique User Identification
Under §164.312(a)(2)(i), each individual who accesses systems containing ePHI must have their own unique user ID. This ensures activity can be traced back to a specific person, promoting accountability and preventing shared logins. For example, organizations often use centralized tools like Active Directory to create unique, non-recycled identifiers for employees, contractors, and vendors. Shared accounts like "nurse1" or "frontdesk" are not allowed.
This requirement also applies to software processes and service accounts - every interface or application accessing ePHI must be uniquely identifiable. Logs should capture detailed information, including user ID, date and time, device details, and actions taken. These records are essential for audits and compliance checks, and failures in this area have been a frequent target of enforcement actions by the Office for Civil Rights (OCR).
Emergency Access Procedures
Under §164.312(a)(2)(ii), organizations must have documented procedures for accessing ePHI during emergencies, such as natural disasters, system outages, or mass casualty events. These procedures often include "break-glass" accounts or workflows that grant temporary, elevated access in urgent, clinically justified cases. For instance, during a life-threatening situation, a clinician might use a break-glass mechanism to access restricted psychiatric records.
Such actions must trigger alerts, be logged, and require documentation to maintain accountability. Clear guidelines should dictate when break-glass measures are permissible, and strong authentication (like multi-factor authentication with time-limited access) should still apply. To ensure their effectiveness, these procedures should be tested regularly, often during disaster recovery or business continuity drills.
Automatic Logoff and Session Management
Automatic Logoff, an addressable measure under §164.312(a)(2)(iii), requires systems to automatically lock or terminate sessions after a period of inactivity. For example, screen lock timeouts might range from five to fifteen minutes in secure areas, with shorter intervals in public or shared spaces. Application-level timeouts within systems like EHRs or billing platforms provide additional protection.
Sensitive actions, such as exporting ePHI or processing prescriptions, often require re-authentication for added security. Organizations can adjust timeout settings based on their risk analysis and workflows, as long as they document their decisions and implement compensating controls like proximity badge systems or privacy screens. For remote sessions, shorter timeouts and device encryption are typically necessary due to higher exposure risks.
Authentication and Encryption
Strong authentication and encryption methods are key to safeguarding ePHI. Under the Person or Entity Authentication requirement, organizations must verify the identity of users or systems accessing ePHI. This is often achieved through strong passwords and multi-factor authentication (MFA), which combines elements like:
- Something you know (password)
- Something you have (a token, smartphone app, or smart card)
- Something you are (biometric data)
For example, MFA is commonly required for remote access, administrative accounts, cloud-based EHR systems, and vendor access. Internal workstations are typically secured with strong passwords and session management controls.
Encryption and Decryption, outlined as an addressable measure under §164.312(a)(2)(iv), involves protecting ePHI both at rest and in transit. This might include full-disk encryption on laptops, database encryption on servers, or securing data in transit using TLS for web applications, encrypted email, or VPNs. If encryption isn’t implemented, organizations must document their decision and adopt alternative safeguards. The Transmission Security standard further emphasizes the need for encryption and integrity controls to ensure ePHI remains secure and unaltered during transmission.
How to Design HIPAA-Compliant Access Control Systems
Creating a HIPAA-compliant access control system starts with defining clear access parameters: who can access what electronic protected health information (ePHI), when, where, and why. These parameters must then be enforced through technical controls and well-documented policies. Whether you choose role-based, user-based, or attribute-based access controls, the goal remains the same - restricting ePHI access to authorized individuals only.
A well-designed system should address key areas such as user onboarding and offboarding (joiners, movers, leavers), access for third-party vendors and business associates, device and location-specific considerations (on-premises, cloud, mobile, remote access), and audit logging tied to unique user IDs. Additionally, the design must align with HIPAA's Information Access Management requirements (Administrative Safeguards, 45 C.F.R. §164.308(a)(4)) and the technical safeguards (45 C.F.R. §164.312).
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
By following these principles, organizations can establish clear roles, ensure secure vendor interactions, and maintain dynamic lifecycle management - all while meeting HIPAA’s strict access control mandates.
Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) assigns permissions based on job roles and responsibilities, streamlining access management. Instead of handling individual permissions for each user, RBAC groups users by their roles, making administration more efficient.
To implement RBAC, start by creating a detailed inventory of workforce roles that interact with ePHI. For example, roles might include registered nurses, physicians, schedulers, billing staff, and IT administrators. Each role should be mapped to specific ePHI needs. For instance, a billing clerk may only require access to demographic and claims data, while a nurse needs clinical records for assigned patients but not billing information.
Once roles are defined, establish standard access profiles within systems like EHR, practice management, and billing platforms. These profiles should grant the minimum permissions necessary for each role. Centralized tools like identity and access management (IAM) or single sign-on (SSO) systems can simplify provisioning. Any non-standard access must be justified, approved, time-limited, and logged. Regular reviews should compare actual permissions to role profiles to prevent "permission creep" and maintain compliance with HIPAA’s Information Access Management and Access Control standards.
Managing User Access Throughout the Employee Lifecycle
Effective access control evolves with an employee’s lifecycle, from onboarding to departure. During onboarding, require documented management approval for new users. Each account should be tied to a unique user ID, with access assigned based on predefined role profiles. Access requests must be linked to manager authorization.
For role changes, implement workflows triggered by HR updates. These workflows should immediately adjust access - removing permissions tied to the old role and adding those needed for the new position. Use change tickets and audit logs to maintain full traceability.
When employees leave, terminate all access promptly. This includes securing or transferring shared mailboxes or service accounts they managed. Regularly reconciling HR records with active accounts in critical systems can help identify orphaned accounts and ensure compliance with HIPAA’s technical safeguards around access control and unique user identification.
Controlling Third-Party Vendor Access
Vendors and business associates bring unique challenges to access control. Start by classifying vendors as business associates and enforce Business Associate Agreements (BAAs) that outline permitted uses, security roles, and breach notification requirements.
Apply the principle of least privilege to vendor accounts, ensuring they are time-limited, protected by multi-factor authentication (MFA), and restricted to only the applications or environments they need. All vendor activity should be logged and monitored. For high-risk vendors, such as those providing remote support for EHRs or medical devices, implement heightened monitoring and conduct periodic access reviews.
For organizations managing multiple vendor relationships, tools like Censinet RiskOps™ can streamline vendor risk assessments, centralize business associate documentation, and provide continuous monitoring of vendor security. This proactive approach shifts organizations from reactive compliance - scrambling to complete questionnaires - to a continuous risk management model, ensuring both security and compliance across the third-party ecosystem.
Technical Controls and Audit Requirements
Once you've designed your access control framework, the next step is implementing technical tools to enforce the rules and track system activity. HIPAA's Technical Safeguards (45 CFR §164.312) outline the need for controls over access, auditing, integrity, authentication, and transmission security. These tools build upon your access control strategies to ensure compliance is maintained consistently.
HIPAA doesn't dictate specific technologies or tools, giving you the freedom to choose solutions that align with your organization's risk analysis. This flexibility allows you to adapt authentication methods, logging systems, and data segmentation strategies to suit your workflows, as long as they meet HIPAA standards and are well-documented. These technical measures ensure every access event is both traceable and verifiable.
Authentication and Identity Verification Methods
The Person or Entity Authentication standard (§164.312(d)) requires organizations to verify that anyone accessing ePHI is who they claim to be. This starts with assigning unique user IDs - shared logins are not allowed - and selecting authentication methods that balance security with operational efficiency.
Strong passwords, enforced through policy, should be paired with multi-factor authentication (MFA) to reduce the risk of credential theft. MFA adds an extra layer of security by combining a password with something like a one-time code, push notification, or hardware token. It's especially critical for remote access, VPNs, and privileged accounts. In fact, credential compromise contributed to over 700 major healthcare data breaches reported to HHS in 2023 [1].
Single sign-on (SSO) systems are another option to streamline workflows, allowing users to log in once and access multiple systems, such as electronic health records (EHR) or picture archiving and communication systems (PACS). However, SSO must be carefully configured to avoid security gaps. Pairing SSO with MFA and implementing strict role management can address these risks.
Risk analysis should guide your choice of authentication methods. For high-risk scenarios, combine MFA with efficient sign-on options. On clinical workstations, quick reauthentication methods can be used after the initial MFA login. Document your MFA requirements, including when additional authentication is triggered (e.g., accessing sensitive records), and outline how exceptions like emergency access or system downtimes are handled.
Audit Logs and Access Monitoring
The Audit Controls standard (§164.312(b)) mandates that organizations record and examine system activity involving ePHI. Simply enabling logging isn’t enough - you must actively review and analyze these logs to detect unauthorized access and support investigations.
Audit logs should capture key details, including the user ID, date and time, event type (e.g., logon, logoff, record access), patient or record identifiers, source IP/device, system involved, and event outcome. To ensure integrity, logs should be protected from tampering using measures like write-once storage, restricted admin access, and regular backups.
Develop a formal log review process that specifies what data is collected, retention periods, criteria for suspicious activity, and who is responsible for reviewing logs. Automated alerts can flag potential issues, such as repeated failed login attempts, unusually high record access volumes, off-hours activity, or access to particularly sensitive records. Proactive audits - whether through random sampling or focused reviews of high-risk roles - can further bolster security. The Office for Civil Rights (OCR) has frequently flagged issues like shared logins, missing unique IDs, and inadequate log reviews as compliance failures. Using centralized log management or security information and event management (SIEM) tools can improve detection by correlating events across systems and providing compliance dashboards. Effective logging also supports data segmentation and least privilege principles.
Data Segmentation and Least Privilege Principles
Data segmentation involves organizing ePHI into distinct categories to control access based on user roles, data sensitivity, or legal requirements. This approach reduces the risk of unauthorized access and limits damage in the event of a breach.
Segment ePHI by grouping data according to sensitivity and restricting access based on roles. Use tools like separate schemas, VLANs, and firewalls to enforce these boundaries. At the application level, configure your EHR to limit access to highly sensitive information - such as substance use records, psychotherapy notes, or reproductive health data - to specific clinical roles.
The principle of least privilege ensures that users, devices, or applications only have the access needed to perform their duties. Implement this by granting permissions based on standardized roles rather than ad hoc decisions. Regularly review permissions to prevent "permission creep", and align active accounts with HR records to identify orphaned accounts. For third-party vendors and business associates, apply least privilege through time-limited accounts, MFA, and enhanced monitoring, especially when they require remote access to systems like EHRs or connected medical devices.
sbb-itb-535baee
Implementing and Maintaining HIPAA Access Control Compliance
Staying compliant with HIPAA access controls is an ongoing process that requires regular risk analysis, detailed documentation, and consistent updates. The Security Rule outlines administrative, physical, and technical safeguards that work together to protect electronic protected health information (ePHI). Your access control program should be grounded in a thorough risk analysis that identifies where ePHI is stored, who needs access, and what potential threats exist. This analysis informs key decisions, such as assigning unique user IDs, setting automatic logoff protocols, enabling encryption, and establishing emergency access procedures. It's crucial to revisit this analysis whenever there are changes to systems, workflows, or regulations. Below, we’ll explore practical steps to implement, review, and manage these controls effectively.
Risk Assessments and Access Control Policies
A strong foundation starts with a comprehensive risk analysis, as required by 45 CFR §164.308(a)(1). This involves cataloging all systems that store or process ePHI and identifying potential threats, such as stolen credentials, unauthorized access by insiders, or excessive permissions granted to third-party vendors. Evaluate your existing controls - things like multi-factor authentication, role-based access, and audit logging - and categorize risks by their likelihood and potential impact. Use this information to prioritize areas where improvements are most needed.
From this analysis, develop written access control policies that clearly define who can access ePHI, what information they are allowed to view, how access is granted or revoked, and under what conditions emergency or elevated access can occur. These policies must adhere to the "minimum necessary" standard, ensuring that users only access the data essential for their roles.
Key areas to address in your policies include:
- Password and authentication requirements
- Session timeout settings
- Emergency access procedures
- Encryption protocols
Once policies are established, align user roles with system permissions and configure role-based access controls in your electronic health record (EHR) system and related applications to enforce these rules automatically. Document everything - from policy details to role-permission mappings - and secure leadership approval. Training is equally important. New employees should complete training before gaining access to ePHI, with annual refreshers and updates when systems or policies change. Effective training should not just explain rules but also highlight their importance by connecting misuse to real-life breach examples and HIPAA penalties. Pair this with a sanctions policy that outlines consequences for violations, and use audit logs to monitor compliance and enforce accountability.
Regular Access Reviews and Continuous Monitoring
Policies alone aren’t enough - regular reviews are essential to maintain compliance. Conduct quarterly reviews of systems containing ePHI, with more frequent checks for high-risk applications or privileged accounts. Extract user and role data from critical systems like EHRs, billing platforms, and imaging tools, then compare this information against HR rosters and role definitions. This helps identify users who no longer need access, have left the organization, or hold permissions beyond what’s necessary. Managers should verify that access aligns with current roles, and IT or security teams should adjust permissions accordingly, documenting all changes.
Continuous monitoring is another critical component. Use audit logs, automated alerts, and periodic manual reviews to detect unusual or unauthorized access in near real-time. Systems managing ePHI should log key events, such as attempts to access large volumes of records, VIP patient lookups, off-hours activity, or logins from unexpected locations. Centralized log collection tools like SIEM platforms can help correlate and analyze this data, triggering alerts for suspicious behavior. Regularly review and fine-tune these alerts to minimize false positives, and document procedures for log reviews, frequency, and escalation steps. This approach supports the Audit Controls standard (§164.312(b)) and demonstrates compliance with HIPAA requirements.
Using Censinet for Access Control Risk Management
Healthcare organizations can simplify access control compliance by using Censinet RiskOps™, a specialized platform designed for healthcare cybersecurity and risk management. This platform centralizes risk assessments for both internal systems and external vendors that handle ePHI, making it easier to identify and prioritize access-related risks across clinical applications, medical devices, and supply chain partners. By standardizing questionnaires and evidence collection, Censinet enables organizations to evaluate whether vendors have implemented proper controls, such as authentication protocols, role-based access, encryption, and monitoring.
Censinet RiskOps™ also supports continuous monitoring and provides benchmarking tools to measure progress against industry standards, helping organizations improve their cybersecurity programs and secure necessary resources. Industry experts have noted that Censinet streamlines the risk assessment process and improves resource allocation. By consolidating risk data, automating workflows, and offering visibility into vendor practices, the platform helps healthcare organizations stay audit-ready and maintain ongoing HIPAA compliance.
Conclusion
HIPAA access control isn't just a recommendation - it's a mandatory safeguard outlined in 45 CFR §164.312 for any covered entity or business associate managing electronic protected health information (ePHI). These requirements form the backbone of compliant access control systems. Achieving compliance demands a well-coordinated strategy that incorporates role-based access control (RBAC), the principle of least privilege, user lifecycle management, and vendor oversight, all underpinned by clear policies and continuous monitoring.
Effective access controls play a critical role in protecting patients from common threats like compromised credentials, insider misuse, and overly broad permissions. When access is tightly restricted, properly authenticated, and thoroughly logged, organizations can significantly reduce their risk of civil penalties, corrective action plans, and damage to their reputation. Patients, in turn, enjoy fewer breaches of privacy and greater confidence in their healthcare providers.
Given the round-the-clock nature of U.S. healthcare and its diverse care environments, access controls must strike a balance between security and the real-time demands of clinical care. Emergency protocols ensure that ePHI remains accessible during critical situations while preserving necessary audit trails. When designed thoughtfully, access controls enhance care delivery without disrupting workflows.
As highlighted in this guide, maintaining access control is an ongoing process. Regular risk analyses, routine access reviews, continuous log monitoring, and consistent training help organizations stay ahead of evolving threats and regulatory changes. Managing access risks across internal systems and third-party vendors demands unified governance. Tools like Censinet RiskOps™ streamline this process, enabling healthcare organizations to centralize risk assessments, benchmark cybersecurity practices, and manage risks tied to PHI, clinical applications, and medical devices more efficiently. These tools simplify identifying and addressing access risks within vendor ecosystems.
HIPAA’s risk-based framework offers flexibility, making compliance achievable for organizations of all sizes. By grounding your program in a detailed risk analysis, adopting practical safeguards like RBAC and encryption, and maintaining diligent oversight, you can protect patient data, uphold trust, and support the secure evolution of healthcare in the digital age. This conclusion reinforces the importance of the access control best practices discussed throughout this guide.
FAQs
What is the difference between required and addressable access controls under HIPAA?
Under HIPAA, required access controls are non-optional measures that every healthcare organization must put in place to protect patient information. These include essential safeguards like assigning unique user IDs, setting up emergency access procedures, and encrypting sensitive data.
In contrast, addressable access controls offer some flexibility. Organizations need to assess whether implementing these measures makes sense for their specific setup. If they determine the controls are practical, they should adopt them. If not, they must document their reasoning and outline an alternative approach.
The key difference lies in their rigidity: required controls are mandatory, while addressable controls allow organizations to adapt based on their unique circumstances and risk evaluations.
What steps can healthcare organizations take to comply with HIPAA's unique user identification requirement?
To meet HIPAA's requirement for unique user identification, healthcare organizations must assign individual user IDs to every person accessing protected health information (PHI). This approach ensures that each user can be distinctly identified and held accountable for their actions.
In addition, organizations need to enforce strict access controls to ensure that only authorized personnel can access PHI. Regularly conducting login activity audits is equally important. These audits help confirm proper usage and identify any instances of unauthorized access. Together, these practices safeguard sensitive patient information and align with HIPAA's security and privacy standards.
Why is it necessary to document decisions when choosing not to implement certain HIPAA access control measures?
Documenting decisions about not implementing certain HIPAA access control measures is crucial for maintaining clarity and responsibility. This process creates a detailed record that explains why specific measures were not adopted - whether due to cost, practicality, or other legitimate factors. Such documentation can highlight the organization’s careful approach to compliance and provide valuable context during audits.
Moreover, keeping these records allows organizations to reevaluate their choices as circumstances change. As technology advances, risks shift, or operational needs grow, these records serve as a foundation for revisiting past decisions. It’s a smart way to reduce risks and stay aligned with HIPAA requirements over time.


