HITRUST vs. NIST: Cloud Security Frameworks Compared
Post Summary
HITRUST integrates multiple standards and offers certification, while NIST provides flexible, widely adopted security controls and best practices.
Both frameworks are used, but HITRUST certification is often preferred for demonstrating HIPAA compliance, while NIST is valued for its adaptability.
HITRUST offers comprehensive coverage, mapped controls, and a certifiable framework tailored for healthcare.
NIST provides granular, flexible controls, is government-backed, and is recognized across industries.
Both frameworks guide organizations in securing cloud environments through risk management, data protection, and compliance requirements.
The best choice depends on your goals: HITRUST for certification and healthcare alignment; NIST for flexibility and broad adoption.
When it comes to securing Protected Health Information (PHI) in the cloud, U.S. healthcare organizations often turn to HITRUST CSF and NIST frameworks. Both frameworks help manage security risks but differ in approach and scope:
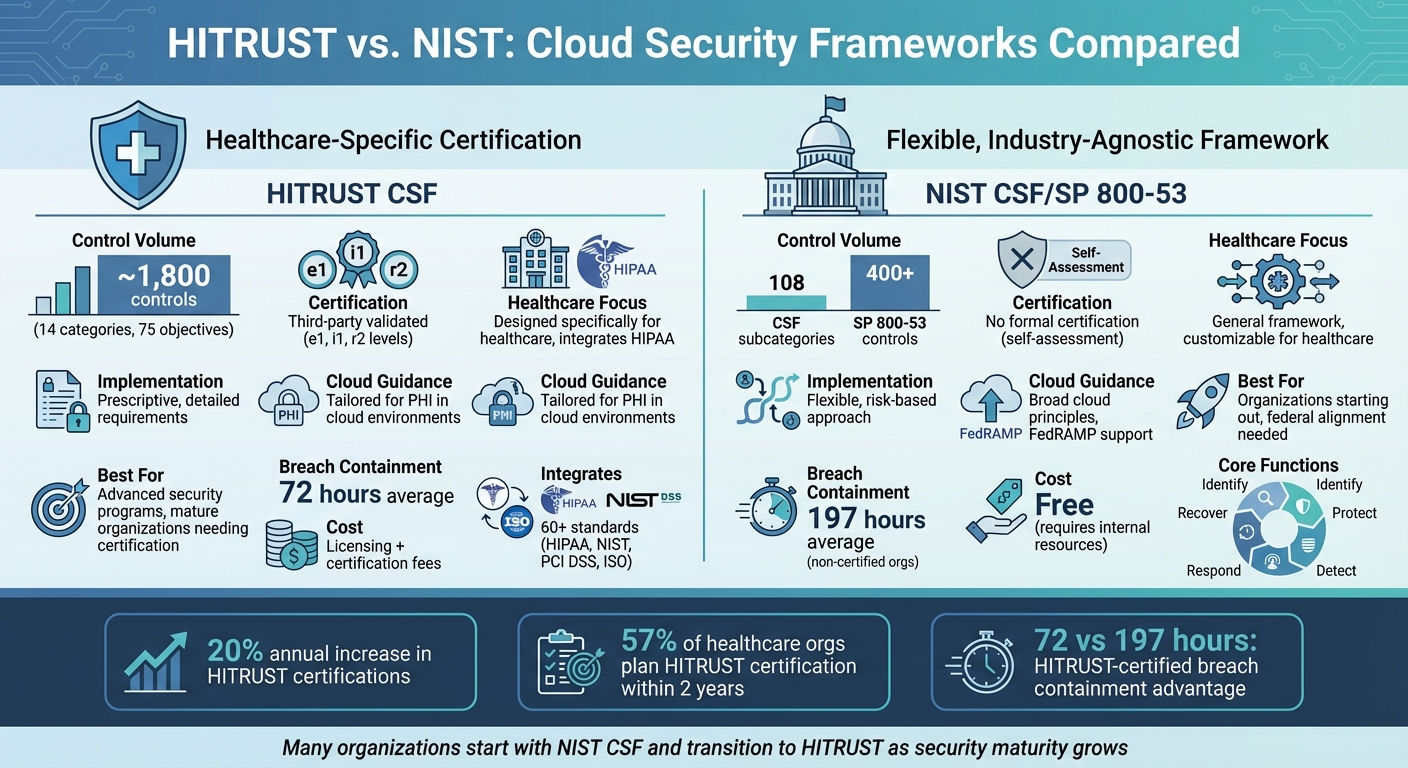
- HITRUST CSF: A detailed, certifiable framework tailored for healthcare, integrating over 60 standards (e.g., HIPAA, NIST, PCI DSS). It offers ~1,800 controls and certification options (e1, i1, r2) for structured compliance.
- NIST Frameworks: Includes the flexible NIST Cybersecurity Framework (CSF) with five core functions (Identify, Protect, Detect, Respond, Recover) and NIST SP 800-53, which catalogs 400+ customizable controls. These are widely used across industries, including healthcare.
Key Takeaways:
- HITRUST is ideal for advanced security programs needing certification and healthcare-specific controls.
- NIST is better suited for organizations starting out or those requiring a broader, industry-agnostic approach.
- HITRUST-certified organizations can contain breaches in 72 hours compared to 197 hours for others.
- Cost and resources: NIST is free but requires internal effort, while HITRUST involves licensing and certification costs.
Quick Comparison:
| Dimension | HITRUST CSF | NIST CSF / SP 800-53 |
|---|---|---|
| Control Volume | ~1,800 controls | CSF: 108 subcategories; SP 800-53: 400+ controls |
| Certification | Third-party certification available | No formal certification |
| Healthcare Focus | Designed for healthcare | General framework, customizable for healthcare |
| Implementation | Prescriptive, detailed controls | Flexible, risk-based approach |
| Cloud Guidance | Tailored for PHI in cloud setups | Broad cloud principles |
Choosing the right framework depends on your organization's size, security maturity, and compliance needs. Small or early-stage organizations often start with NIST, while larger, mature programs may benefit from HITRUST certification. Tools like Censinet RiskOps™ can simplify implementation by mapping controls across both frameworks.
HITRUST vs NIST Cloud Security Frameworks Comparison for Healthcare
What is HITRUST CSF for Cloud Security?

HITRUST's Origins and Purpose
The HITRUST Common Security Framework (CSF) was created to simplify the complex landscape of healthcare security compliance. Instead of requiring organizations to juggle multiple standards like HIPAA, NIST, PCI DSS, and ISO, HITRUST brings these frameworks together into a single, unified system. This consolidation includes over 60 different standards and regulations, offering a streamlined approach to securing cloud-hosted Protected Health Information (PHI) [1].
HITRUST CSF provides clear, actionable guidelines with detailed implementation requirements. These are organized into 14 control categories, 75 control objectives, and roughly 1,800 individual controls. It integrates healthcare-specific regulations like HIPAA with baseline controls from frameworks such as NIST 800-53. Additionally, it incorporates threat intelligence and best practices tailored to healthcare workflows, including those in cloud environments [1][2].
Cloud-Specific Risk Management with HITRUST
HITRUST CSF is particularly effective in addressing the unique challenges of managing PHI in the cloud. It aligns its controls with the shared responsibility models of cloud providers, ensuring that critical areas like access management, encryption, configuration management, logging, monitoring, business continuity, and incident response are adequately covered [1][2][3]. For organizations using major cloud platforms, HITRUST helps clearly define which security responsibilities lie with the cloud provider and which belong to the organization.
The framework also tackles technical risks specific to cloud environments. It includes controls for API security, identity and access management (IAM), data residency, and continuous monitoring across multi-cloud setups [1][2]. By promoting ongoing risk management and regular compliance checks, HITRUST ensures that cloud-hosted PHI remains secure in an ever-evolving threat landscape.
HITRUST Certification and Assurance Model
HITRUST offers three levels of certification: e1 (self-assessment), i1 (interim validated assessment), and r2 (comprehensive validated assessment). Among these, the r2 certification is the most thorough, requiring third-party assessors to verify an organization’s implementation of HITRUST controls across all domains. This rigorous process has tangible benefits - HITRUST-certified organizations have reduced the average time to identify and contain a breach to 72 hours, compared to 197 hours for non-certified organizations [2].
The framework’s adoption is growing steadily, with certifications increasing by 20% annually. In fact, 57% of surveyed healthcare organizations plan to pursue HITRUST certification within the next two years, solidifying its role as a trusted security standard in U.S. healthcare [2].
For healthcare organizations managing intricate cloud ecosystems with multiple vendors, tools like Censinet RiskOps™ can simplify HITRUST compliance. These platforms streamline tasks such as vendor assessments, tracking control gaps, and preparing documentation for certification. By automating HITRUST control assessments for clinical applications, devices, and cloud-hosted PHI, organizations can significantly reduce manual effort.
Next, we’ll explore how HITRUST’s approach compares to NIST frameworks.
What are NIST Frameworks for Cloud Security?

The National Institute of Standards and Technology (NIST) provides two key frameworks to guide cloud security in the U.S. healthcare sector: the NIST Cybersecurity Framework (CSF) and NIST Special Publication 800-53 (SP 800-53). The NIST CSF offers a high-level, results-oriented approach to managing cybersecurity risks, while SP 800-53 provides a detailed catalog of security and privacy controls. Together, these frameworks help healthcare organizations build cloud security programs that align with federal standards and support HIPAA compliance. Although the NIST CSF was originally designed for critical infrastructure, its principles are now applied across industries, including healthcare. Below, we break down the core principles and controls of each framework.
NIST CSF: Core Functions and Outcome-Based Approach
The NIST Cybersecurity Framework outlines five core functions - Identify, Protect, Detect, Respond, and Recover - to help organizations assess and improve their cloud security strategies [1]. With around 108 subcategories tied to specific security activities, the framework provides clear guidance without dictating exact implementation methods. In healthcare cloud environments, these functions translate into actionable steps:
- Identify: Cataloging assets and protected health information (PHI) across on-premises systems, cloud platforms, and SaaS applications.
- Protect: Using access controls, encryption, secure configurations, and development practices to safeguard cloud-hosted electronic health records (EHRs) and clinical applications.
- Detect: Setting up logging, monitoring, and threat detection for cloud-native services and APIs.
- Respond: Creating incident response playbooks and assigning roles to handle issues like misconfigurations or compromised accounts.
- Recover: Establishing backup plans, disaster recovery strategies, and resilience measures to ensure clinical operations and patient safety during cloud service outages.
NIST SP 800-53: Catalog of Security Controls
NIST SP 800-53 takes a more detailed approach, offering over 400 specific security and privacy controls grouped into control families [2]. The latest revision (Revision 5) introduces privacy controls and addresses supply chain risks, which are critical for healthcare organizations relying on multi-vendor ecosystems. This framework is closely tied to federal programs like FedRAMP, which uses SP 800-53 baselines to authorize cloud service providers for federal use. As healthcare organizations increasingly adopt FedRAMP-authorized cloud services, they benefit from the robust controls these platforms are built on. While originally intended for federal agencies, SP 800-53 has become widely used in healthcare because its granular controls complement the broader structure of the NIST CSF.
NIST Frameworks in Healthcare Cloud Use Cases
Healthcare organizations frequently use NIST frameworks to manage cloud security. Since the HIPAA Security Rule does not specify technical controls, mapping NIST CSF functions and SP 800-53 controls offers a way to demonstrate appropriate safeguards for PHI stored and processed in the cloud [1][2]. These frameworks also provide a standardized method for conducting cloud risk assessments, especially when evaluating third-party vendors. By requiring vendors to align their controls with NIST CSF and SP 800-53, healthcare providers gain better insight into the security measures protecting their data.
Platforms like Censinet RiskOps™ assist healthcare organizations in applying these frameworks across their cloud environments. This tool simplifies the process of mapping vendor controls to NIST CSF and SP 800-53, making it easier to evaluate cloud-hosted clinical applications, devices, and services. Next, we’ll explore how these frameworks compare side by side.
HITRUST vs. NIST: Side-By-Side Comparison
Comparison Table: Key Differences
HITRUST CSF and NIST frameworks take distinct paths when it comes to cloud security. HITRUST CSF is a prescriptive framework tailored to the healthcare sector, with approximately 1,800 controls spread across 14 categories, 75 objectives, and 19 domains [1]. On the other hand, NIST CSF offers a more flexible, outcome-driven approach, featuring 5 core functions and about 108 subcategories, while NIST SP 800-53 provides over 400 detailed controls that can be customized to fit an organization’s specific needs [1][2]. The table below breaks down the key differences between these frameworks, particularly for healthcare cloud environments:
| Dimension | HITRUST CSF | NIST CSF / NIST SP 800-53 |
|---|---|---|
| Control Volume | ~1,800 controls across 14 categories | NIST CSF: 108 subcategories; SP 800-53: 400+ controls |
| Certification Model | Third-party validated certification | Self-assessment or optional third-party validation (no formal certification) |
| Healthcare Focus | Specifically designed for healthcare; integrates HIPAA requirements | General framework usable across industries; requires mapping for healthcare-specific needs |
| Implementation Approach | Prescriptive controls with detailed requirements | Flexible, risk-based approach allowing organizations to select relevant controls |
| Cloud-Specific Guidance | Includes tailored controls for healthcare PHI in cloud environments | Broad cloud principles; SP 800-53 supports FedRAMP for federal cloud services |
| Regulatory Alignment | Directly maps to HIPAA with healthcare-specific safeguards | Facilitates HIPAA compliance through control mapping; widely applied in federal healthcare settings |
This table provides a clear snapshot of how these frameworks differ in their approach to cloud security within the healthcare sector.
Frameworks and Cloud Security Maturity
NIST CSF is ideal for organizations just beginning their cloud security journey, offering a straightforward roadmap through its five core functions: Identify, Protect, Detect, Respond, and Recover. These functions provide a foundation without overwhelming teams with excessive detail, making it easier for healthcare organizations to start small and scale their efforts over time.
HITRUST CSF, on the other hand, is better suited for organizations at more advanced stages of cloud security. Its structured certification process not only provides a way to measure progress but also ensures continuous improvement. This makes HITRUST a strong choice for organizations that need to demonstrate compliance and maturity in their security practices.
How Each Framework Affects Cloud Security
HITRUST’s prescriptive nature establishes clear benchmarks for configurations, monitoring, and incident response. This consistency is especially valuable for standardizing security practices across multi-cloud setups and vendor ecosystems. Meanwhile, NIST’s adaptable framework allows healthcare organizations to tailor controls to their specific risk profiles, ensuring that critical risks are prioritized effectively.
Both frameworks support regulatory compliance, but their focus differs. HITRUST directly addresses healthcare regulations like HIPAA, while NIST provides a broader foundation that aligns with federal standards, making it versatile for various industries [2][3].
sbb-itb-535baee
How to Choose the Right Framework for Your Healthcare Organization
Factors to Consider When Selecting a Framework
The decision to choose a framework for your healthcare organization should start with understanding regulatory and customer requirements. If you need to prove compliance to business associates, payers, or federal programs, HITRUST’s third-party certification is a solid choice. It offers the external assurance that many partners now expect [2]. On the other hand, if your focus is on building a strong internal security program without the immediate need for certification, NIST frameworks provide a practical and cost-effective option. These frameworks are publicly available for free and are widely accepted across industries [1].
Your organization’s size and cloud footprint also play a crucial role. Smaller organizations or those just beginning their cloud journey may find NIST CSF’s 108 controls manageable, offering structure without overwhelming limited resources [1]. Larger healthcare systems, especially those dealing with complex multi-cloud setups and significant volumes of protected health information, often require HITRUST’s detailed 1,800 controls to maintain consistency across vendors and internal systems [1]. Additionally, your current security maturity level matters - NIST is ideal for building foundational capabilities, while HITRUST is better suited for organizations ready to demonstrate advanced security maturity through formal validation [1][2].
Lastly, consider cost and resource demands. NIST frameworks don’t require licensing fees, but tailoring controls to fit your risk profile will require staff time and effort. HITRUST, on the other hand, involves licensing costs and more rigorous preparation. However, the investment in HITRUST certification can pay off - studies show it reduces breach containment time to an average of 72 hours compared to 197 hours for non-certified organizations [2].
By weighing these factors, you can make a strategic choice about which framework aligns best with your organization’s needs.
Strategies for Framework Adoption
Many healthcare organizations start with NIST CSF, using its five core functions - Identify, Protect, Detect, Respond, and Recover - as a foundation for organizing policies, controls, and metrics [1]. As regulatory or customer demands grow, they often transition to HITRUST, leveraging their existing NIST-based work as a stepping stone. Since HITRUST integrates multiple frameworks, including NIST, much of the groundwork already aligns [1][2].
For organizations already using HITRUST, there’s an added advantage: you can validate NIST alignment simultaneously. HITRUST’s comprehensive controls already encompass NIST requirements, so it’s a matter of mapping and documenting the overlap [1]. Some organizations take a phased approach, starting with NIST CSF and moving toward full HITRUST certification over two to three years for critical systems [2].
Once you’ve decided on a framework strategy, the right tools can make implementation smoother and more efficient.
Using Censinet RiskOps™ to Support Framework Implementation
Censinet RiskOps™ simplifies the process of implementing frameworks by offering a centralized platform for risk assessments. It enables healthcare organizations to evaluate both cloud vendors and internal services against HITRUST and NIST control sets within a single workflow [2]. By collecting evidence once and mapping it across frameworks, the platform minimizes redundancy and improves visibility [2].
This platform acts as a central repository for controls, assessments, and remediation efforts. It tracks the status of HITRUST and NIST controls across cloud environments and vendors over time. Key evidence - such as policies, penetration test results, configuration reports, and audit logs - can be linked directly to specific controls, streamlining preparation for HITRUST validations or NIST reviews [2].
RiskOps™ dashboards provide a clear view of where protected health information, clinical applications, and medical devices might be exposed in the cloud. They also highlight which controls align with HITRUST or NIST and identify vendors with the highest residual risks. By aggregating assessment results and risk scores, the platform helps healthcare leaders visualize security trends, prioritize fixes, and demonstrate progress to boards, regulators, and key partners - all while aligning with both frameworks [2].
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health
Conclusion
Healthcare organizations can rely on both HITRUST and NIST frameworks to strengthen cloud security. NIST CSF and NIST SP 800-53 provide flexible baseline structures that many use to shape their security programs, particularly when addressing federal regulations or broader risk management needs. On the other hand, HITRUST CSF offers a more detailed, certifiable framework with around 1,800 controls specifically tailored to healthcare. This makes it a go-to standard for demonstrating advanced security practices to business associates, payers, and regulators.
Many organizations begin with NIST’s 108 subcategories to establish a solid security foundation and later transition to HITRUST as their security programs mature and external assurance needs expand. The benefits of HITRUST certification are clear - certified organizations have been shown to contain breaches within 72 hours, compared to 197 hours for those without certification [2]. As cloud environments grow increasingly complex, achieving higher levels of security maturity becomes even more critical.
To address these challenges, tools that simplify compliance across frameworks are essential. Censinet RiskOps™ is one such solution, designed to manage both HITRUST and NIST requirements efficiently in cloud environments. This platform centralizes risk assessments for third parties and enterprises, maps vendor controls to both frameworks, and tracks progress over time. It covers areas like protected health information, clinical applications, medical devices, and supply chain risks. By standardizing questionnaires, consolidating risk scoring, and providing dashboards that visualize security trends, RiskOps™ helps healthcare leaders demonstrate progress to boards, regulators, and partners - all without duplicating efforts.
Choosing the right framework strategy depends on your organization’s risk profile, compliance requirements, and business goals. Whether you prioritize NIST’s flexibility, HITRUST’s comprehensive framework, or a combination of both, the end goal should always be measurable improvements in cloud security maturity.
FAQs
How do HITRUST CSF and NIST frameworks differ in addressing cloud security for healthcare organizations?
HITRUST CSF is a framework specifically designed for the healthcare industry, offering a certifiable method to manage risks and ensure compliance. Its primary focus is on safeguarding healthcare data, Protected Health Information (PHI), and clinical systems. What sets HITRUST apart is its integration of multiple standards, like NIST, while providing more detailed, healthcare-focused guidance.
On the other hand, NIST, especially its Cybersecurity Framework (CSF), takes a broader, industry-neutral approach to managing cybersecurity risks. It revolves around five core functions: identify, protect, detect, respond, and recover. While comprehensive, NIST is less tailored to the unique needs of healthcare than HITRUST.
For healthcare organizations, HITRUST often proves more practical for addressing specific compliance requirements in the industry. Meanwhile, NIST serves as a solid, flexible foundation for developing a risk-based security strategy that can be applied across various sectors.
Why would a healthcare organization choose HITRUST instead of NIST for cloud security compliance?
Healthcare organizations often choose HITRUST because it provides a specialized framework specifically designed for the healthcare industry. By combining multiple standards into one certifiable program, HITRUST simplifies the compliance process, helping organizations manage risks and meet regulatory demands more effectively.
What sets HITRUST apart is its focus on the unique challenges of healthcare. It addresses risks tied to patient data, clinical systems, and other vital areas, making it a practical solution for safeguarding sensitive information. This targeted approach not only enhances security but also helps organizations save both time and resources.
How does HITRUST certification improve breach containment compared to relying on NIST alone?
HITRUST certification strengthens an organization's ability to handle breaches by offering clear security controls and a well-defined certification process. This helps teams respond to incidents faster and with greater efficiency. While NIST provides a flexible framework for managing cybersecurity, HITRUST takes it a step further by incorporating healthcare-specific requirements, making it easier to implement the necessary protections.
By blending detailed guidance with a structured certification process, healthcare organizations can better address risks, contain breaches more effectively, and reduce the time it takes to respond. This approach helps safeguard patient data and ensures smoother operations during incidents.
Related Blog Posts
Key Points:
What is the main difference between HITRUST and NIST frameworks?
- HITRUST: Integrates multiple standards (including HIPAA, ISO, NIST, and PCI), providing a certifiable framework with mapped controls specifically tailored for healthcare and cloud environments.
- NIST: Offers modular, flexible security controls (notably through NIST SP 800-53 and NIST CSF), serving as a widely recognized, government-backed set of best practices for information security across industries.
Which framework is more widely used in healthcare?
- HITRUST: Frequently chosen by healthcare organizations needing formal certification to demonstrate HIPAA compliance and third-party assurance.
- NIST: Broadly implemented for its adaptability and foundational best practices, often serving as the baseline for risk management programs in healthcare.
What are the strengths of the HITRUST framework?
- Comprehensive Coverage: Maps to multiple regulatory requirements and standards, reducing redundancy and audit fatigue.
- Certifiable: Provides a recognized certification that can streamline vendor risk assessments and demonstrate compliance to partners.
- Tailored for Healthcare: Specifically designed to address the complex regulatory landscape of healthcare data protection.
What are the strengths of the NIST framework?
- Flexibility: Allows organizations to tailor controls to their specific risk profiles and operational needs.
- Widely Recognized: Backed by the U.S. government and used as the foundation for many public and private sector security programs.
- Detailed Guidance: Offers granular, step-by-step controls for a wide range of security scenarios, including cloud environments.
How do HITRUST and NIST support cloud security?
- HITRUST: Provides mapped controls and requirements specific to cloud service providers and users, ensuring consistent application of data protection safeguards in cloud environments.
- NIST: Offers in-depth guidance on cloud security (e.g., NIST SP 800-53, NIST SP 800-171), supporting risk assessment, cloud-specific controls, and continuous monitoring.
Which framework should my organization choose?
- HITRUST: Choose if you require certification, want streamlined vendor assessments, or need specific healthcare compliance.
- NIST: Choose if you value flexibility, want a customizable framework, or need foundational controls for various data environments.
- Combination: Many organizations leverage both, using NIST as a baseline and HITRUST for certification and assurance.


