How to Build a PHI Incident Response Plan
Post Summary
A structured roadmap for detecting, containing, and reporting PHI breaches in compliance with HIPAA.
An Incident Commander—typically a CISO/CIO—supported by security, privacy, legal, clinical, and compliance teams.
Through log monitoring, SIEM alerts, access audits, and intrusion detection tools.
A tool that classifies incidents by patient volume, data exposure, and regulatory impact to guide response actions.
Isolate affected systems, disable compromised accounts, enforce downtime workflows, and preserve forensic evidence.
Notifications to individuals within 60 days, plus OCR and media reporting for breaches affecting 500+ people.
Building a PHI Incident Response Plan is essential for healthcare organizations to protect patient data, comply with HIPAA, and mitigate risks effectively. Here's what you need to know:
A strong response plan not only ensures compliance but also safeguards patient trust and operational continuity.
Building a PHI Incident Response Team
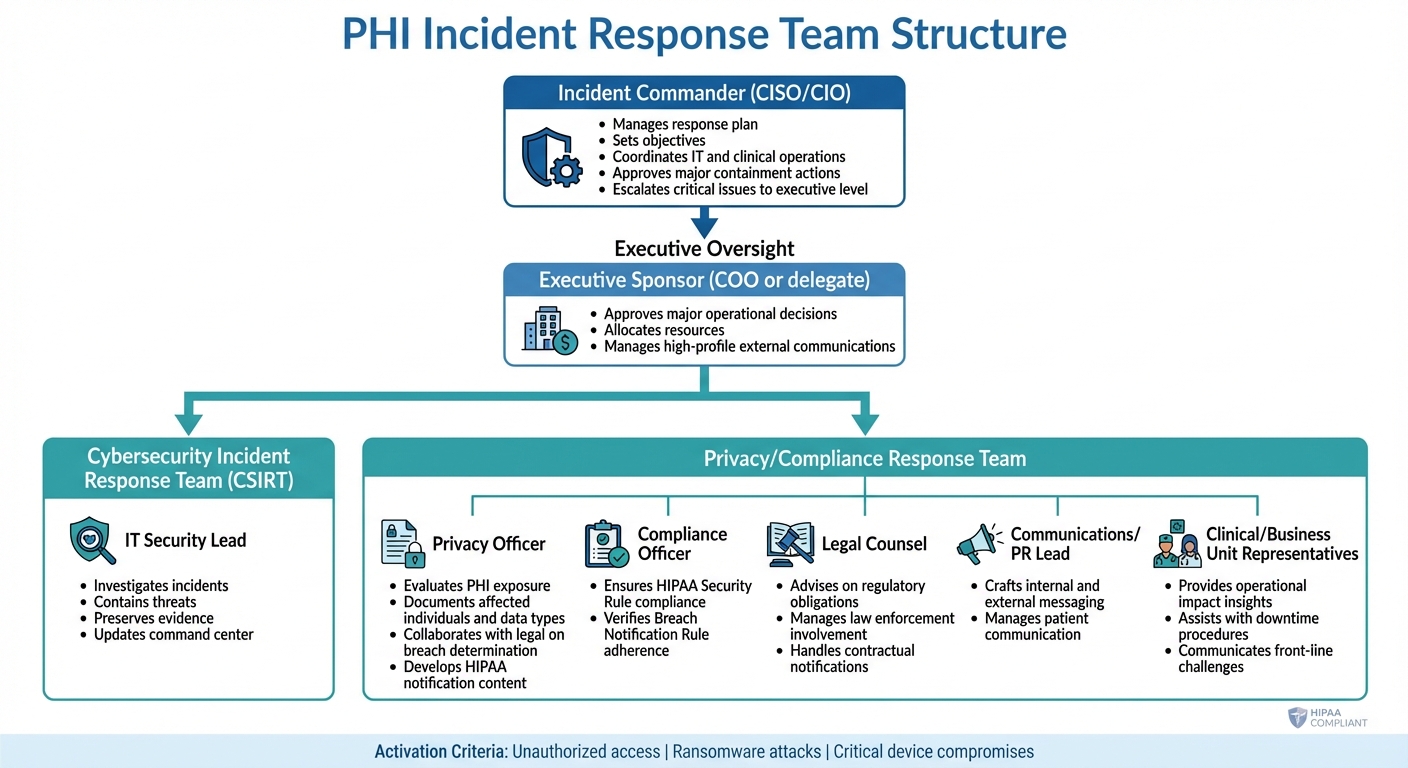
PHI Incident Response Team Structure and Roles
A PHI incident response plan is only as effective as the team carrying it out. Many healthcare organizations already have key components like IT security staff, privacy officers, and legal counsel in place. However, they often lack clear direction on how these roles should collaborate during a breach [7].
Team Roles and Responsibilities
Creating a strong PHI incident response team means bringing together professionals from different disciplines who may not typically work side by side. According to the U.S. Department of Health and Human Services (HHS), it's essential to assign clear roles for handling incidents, decision-making, communication, and documentation, following guidance from NIST SP 800-61 [8]. This structure should include two main groups: a Cybersecurity Incident Response Team (CSIRT) to handle technical containment and forensics, and a Privacy/Compliance Response Team to oversee breach determination and regulatory notifications [8].
At the top of this structure is the Incident Commander, often a senior leader like the CISO or CIO. This individual manages the response plan, sets objectives, coordinates between IT and clinical operations, approves major containment actions, and escalates critical issues to the executive level [4]. The IT Security Lead is responsible for investigating incidents, containing threats, preserving evidence, and keeping the command center updated. Meanwhile, the Privacy Officer evaluates PHI exposure, documents affected individuals and data types, collaborates with legal teams on breach determination, and develops HIPAA notification content [8][9].
Other essential roles include:
Clear activation criteria - such as unauthorized access, ransomware attacks, or critical device compromises - should be established. For significant incidents, an Incident Command Center (virtual or physical) can be convened, with regular updates to ensure all team members stay aligned [4][9].
Once roles are clearly defined, the next challenge is ensuring smooth coordination, which is where tools like Censinet RiskOps™ come into play.
Using Censinet RiskOps™ for Team Coordination

After defining roles and responsibilities, maintaining coordination across diverse stakeholders during an active incident becomes crucial. Censinet RiskOps™ acts as a centralized hub for PHI incident response, offering real-time risk visualization, task management, and secure data sharing within your internal teams and with external partners [1]. Its command center capabilities streamline the process by consolidating assessment findings and routing critical tasks to the appropriate team members for review and approval. Think of it as "air traffic control" for managing incident response [1].
Terry Grogan, CISO at Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Similarly, James Case, VP & CISO at Baptist Health, noted, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
The platform's cloud-based risk exchange further simplifies collaboration by enabling secure sharing of cybersecurity and risk data among team members, healthcare organizations, and third-party vendors. This ensures everyone involved in managing a PHI breach has access to the same up-to-date information during critical moments [1].
Detecting and Classifying PHI Incidents
Once your response team is in place, the next step is knowing when to activate it. Early detection can mean the difference between containing an incident and having it spiral into a crisis affecting thousands of patients. To stay ahead, healthcare organizations need reliable systems to spot unauthorized PHI access before it escalates. Effective detection also lays the groundwork for accurate incident classification.
How to Detect PHI Breaches
Spotting PHI breaches starts with monitoring system logs for unusual activity. Be on the lookout for warning signs like repeated failed login attempts or access to medical records during off-hours [2][5]. These patterns often point to compromised credentials or insider threats, both of which demand immediate attention.
Automated tools like Security Information and Event Management (SIEM) systems can simplify this process by sending real-time alerts when specific thresholds are crossed. Intrusion detection systems also play a key role by analyzing network traffic for suspicious behavior involving electronic PHI - like unexpected data transfers to external servers [2][5]. Additionally, access monitoring tools, such as database activity monitoring (DAM), keep track of who is accessing PHI and when, creating audit trails that help uncover both external breaches and internal misuse. Regular permission audits add another layer of protection [2][3].
The numbers speak for themselves: in 2023, over 540 healthcare organizations reported breaches affecting 112 million individuals. Many of these were identified through log analysis and automated alert systems [9].
Once you detect an anomaly, the next step is to determine its severity.
Building a PHI Incident Severity Matrix
A severity matrix helps your team quickly assess incidents and decide on the right course of action. It considers factors like the number of patients affected, the type of data exposed, and the regulatory impact [2][3]. This structured approach ensures consistent decision-making, even in high-pressure situations, and aligns with the response strategies mentioned earlier.
Here’s a breakdown of four severity levels:
Severity Level
Patient Volume
Data Scope
Regulatory Impact
Example
<100
Limited (names only)
Minimal notification
Isolated unauthorized view
100–1,000
Partial PHI exposure
Internal reporting
Ransomware affecting some records
1,000–10,000
Sensitive data (diagnoses)
State notification required
Widespread access breach
>10,000
Full PHI (SSNs, treatments)
OCR notification within 60 days
Large-scale data exfiltration
The initial assessment should be handled by your IT Director or Cybersecurity Incident Response Team. Using a detailed checklist, they’ll evaluate key factors like how the breach was discovered, available evidence (e.g., logs and timestamps), the systems affected, and the incident’s origin. These insights are crucial for determining the appropriate response level [11].
Containment, Eradication, and Recovery Procedures
Once the severity of an incident is determined, immediate action is critical to limit the exposure of Protected Health Information (PHI) and ensure patient care continues. The process involves three key phases - containment, eradication, and recovery - that work together to mitigate damage, remove threats, and safely restore operations.
HIPAA-Compliant Containment Strategies
As soon as a PHI breach is confirmed, isolate the affected systems without delay. Disconnect compromised devices by making VLAN changes, disabling switch ports, or leveraging Endpoint Detection and Response (EDR) tools. Block malicious IP addresses and domains at the firewall level, disable compromised user accounts, and enforce password resets for impacted areas. If the breach involves APIs or system interfaces, suspend their operations temporarily to stop further data exchange.
While addressing the breach, maintain a balance between security and patient safety. Implement downtime procedures, switch to paper-based workflows, and pause non-essential clinical activities. The HSCC CHIRP template highlights the importance of coordinating with your hospital’s incident command center to ensure clinical operations remain as smooth as possible during containment.
All actions must align with HIPAA safeguards. Limit PHI access to authorized personnel, and log any emergency "break-glass" access for later review. If forensic analysis requires copying PHI, restrict the amount copied, encrypt it, and tightly control access.
Once containment is secured, shift focus to eradicating the threat and restoring affected systems.
Eradication and Post-Breach Recovery
After containment, the next step is to eliminate the root cause of the breach. Reimage or rebuild compromised systems, remove malware using EDR tools alongside manual checks, and apply all missing security patches. Rotate exposed credentials and secrets, and close any misconfigured ports, services, or remote access points exploited by the attacker. Review logs to identify how the breach occurred, confirm vulnerabilities are addressed, and conduct vulnerability scans to validate the fixes.
Recovery involves a careful, step-by-step approach before systems are fully restored. Use trusted, pre-compromise backups that comply with HIPAA encryption and access-control requirements. Test applications in a controlled environment to ensure security patches remain intact and audit logging functions correctly. Coordinate with clinical and operational staff to conduct functional tests, verifying workflows in areas like labs, pharmacies, and imaging departments are back to normal. Systems should only rejoin production networks after these validations, followed by a period of heightened monitoring to catch any lingering issues.
To ensure PHI integrity, compare record counts and key fields, perform database checks, and review audit logs. Work with clinical and health information management teams to sample high-risk datasets and confirm their accuracy. Maintain comprehensive documentation, including incident timelines, logs, forensic reports, lists of affected systems, and details of PHI types involved. Record all containment, eradication, and recovery actions to comply with HIPAA requirements. This documentation not only supports breach notification decisions but also demonstrates adherence to HIPAA standards. Tools like Censinet RiskOps™ can simplify evidence collection and ensure a complete audit trail throughout the incident response process.
sbb-itb-535baee
Communication and Notification Protocols
Once containment and eradication efforts are complete, it’s critical to establish clear notification processes and timelines. Well-defined communication protocols ensure your response team stays coordinated, meet HIPAA’s strict deadlines, and maintain trust with patients and regulators. Without a structured workflow, there’s a risk of missing notification windows, sending mixed messages, or losing coordination across IT, legal, privacy, and executive leadership. These protocols serve as the vital connection between technical containment and stakeholder communication.
Internal Communication and Collaboration
Start by setting up a clear notification hierarchy that identifies key individuals to contact in the event of an incident. Typically, this includes roles like the CISO or IT security lead, Privacy Officer, Compliance, Legal, CIO, CMO, CEO, Communications/Public Relations, and Emergency Management. Establish strict timelines - for example, notifying the Privacy Officer and CISO within one hour of identifying a potential PHI breach and briefing executive leadership within four hours.
Align your communication structure with the Hospital Incident Command System (HICS) to ensure clarity and efficiency. Assign roles such as Incident Commander, Public Information Officer, Liaison Officer, and leads for IT, clinical, and business units. Define who is responsible for approving internal alerts, external statements, and regulatory submissions, and keep a documented approval trail to support defensible decision-making.
Prepare for uninterrupted communication by using redundant channels. Have pre-approved templates ready for email, intranet banners, and mass notifications, and ensure backup methods like secondary email domains, secure messaging apps, or phone trees are in place. This is especially crucial if primary networks or tools are compromised. Standardize situation reports (SITREPs) to include key details like the current impact, affected systems, PHI exposure risks, actions taken, next steps, and guidance for staff on external communication. Regular updates - every four to eight hours during active incidents - help keep leadership and stakeholders informed and aligned.
HIPAA Breach Notification Requirements
Under HIPAA’s Breach Notification Rule, covered entities must notify affected individuals without unreasonable delay and no later than 60 calendar days after discovering a breach of unsecured PHI. Importantly, “discovery” refers to the first day the breach is - or should have been - known, not when an investigation is fully completed. For breaches involving 500 or more individuals in a state or jurisdiction, entities must also notify the HHS Office for Civil Rights (OCR) and local media outlets within the same 60-day period. Breaches affecting fewer than 500 individuals can be logged and reported annually to HHS within 60 days of year-end.
Develop a workflow to determine whether a PHI security incident qualifies as a reportable breach under HIPAA’s four-factor risk assessment. This assessment examines the nature and extent of the PHI involved, who accessed it, whether it was actually acquired or viewed, and the effectiveness of mitigation efforts. Track the discovery date and set up automated reminders to ensure the 60-day regulatory deadline isn’t missed. Use templates for individual notification letters (both postal and electronic), substitute notices (like website or media postings), HHS/OCR submissions, and any state-specific notifications.
Patient-Facing Communication and Media Coordination
When communicating with patients, use straightforward, non-technical language to explain the situation. Outline what happened, what it means for them, and offer practical steps they can take - such as enrolling in credit monitoring, updating passwords, or setting up fraud alerts. Provide a dedicated toll-free number and ensure call-center staff are equipped with consistent, accurate scripts. Align these scripts with written notifications and website FAQs to maintain a unified message. This patient-first approach helps reassure individuals while demonstrating a commitment to protecting their information.
For media relations, designate a single spokesperson to handle inquiries. Prepare holding statements and Q&A documents in advance, ensuring they’ve gone through legal and privacy reviews to streamline response times and avoid speculation.
Leverage secure platforms like Censinet RiskOps™ and Censinet Connect™ to centralize documentation and communication. Censinet RiskOps™ consolidates incident records and communication logs, while Censinet Connect™ enables secure, encrypted messaging for sharing sensitive details - such as PHI exposure or investigation updates - with healthcare organizations, third parties, and legal counsel. These tools ensure confidentiality and maintain an auditable record throughout the notification process.
Testing, Training, and Continuous Improvement
Keeping your PHI incident response plan sharp requires regular testing and updates. Federal guidance from HHS and NIST stresses the importance of exercising, reviewing, and updating incident response capabilities on an ongoing basis to ensure they're effective [8]. Unfortunately, many organizations only uncover weaknesses in their plans during real incidents - when the stakes are at their highest. By setting up a structured program of training, exercises, and continuous improvement, you can ensure your team knows their roles, your procedures hold up under pressure, and your plan adapts to new threats, technologies, and regulatory changes.
Running Tabletop Exercises
Tabletop exercises are discussion-driven sessions where your incident response team walks through a realistic PHI breach scenario. Unlike technical simulations that focus on systems, these exercises emphasize decision-making, coordination, and communication among key stakeholders like IT security, privacy officers, legal teams, compliance staff, clinical leadership, and executives. The primary goal is to test how well your plan's workflows hold up - from detecting and escalating a breach to making containment decisions, meeting HIPAA notification timelines, and managing media inquiries. These sessions often reveal gaps in clarity around roles or outdated processes.
When planning tabletop exercises, set clear objectives. For instance, you might aim to escalate an incident to the Privacy Officer within 30 minutes, activate EHR downtime procedures within 15 minutes, or draft a HIPAA-compliant notification within 24 hours [4]. To make the exercises more dynamic, use timed injects - scenarios that introduce new developments, like discovering additional PHI has been affected, receiving a media inquiry, or learning about a vendor's breach. These injects force participants to think on their feet and make decisions under time constraints, mimicking real-world challenges. Be sure to involve both technical and clinical stakeholders to reflect your actual governance structure, and tailor scenarios to healthcare-specific risks, such as ransomware attacks on EHR systems, exposed patient records from misconfigured cloud storage, or a lost unencrypted laptop.
For larger health systems, aim for at least one multi-department tabletop exercise annually, with additional drills every 6–12 months for high-risk areas like EHR downtime or third-party vendor breaches. Smaller practices can scale these exercises to their size, but maintaining an annual schedule is critical for OCR defensibility and ongoing improvement. After each exercise, hold an immediate debrief (hotwash) to gather initial feedback, followed by a more formal After-Action Review (AAR). The AAR should document successes, failures, and root causes, and lead to a Corrective Action Plan with clear responsibilities and deadlines for updating policies and training materials.
These exercises are the foundation for continuous improvement, a process that can be further enhanced with real-time insights from tools like Censinet dashboards.
Using Censinet Dashboards for Continuous Improvement
Censinet RiskOps™ offers dashboards and benchmarking tools designed to strengthen your PHI incident response program. By consolidating risk assessments across third-party vendors, clinical applications, medical devices, and other PHI-handling systems, the platform helps you identify where incidents are most likely to occur and prioritize your exercises accordingly. For example, you can use vendor risk scores and identified control gaps to craft realistic tabletop scenarios, such as a breach involving a high-risk imaging vendor or a billing service, targeting areas where your response plan is weakest.
Censinet's benchmarking features allow you to compare your risk posture and response maturity with peer healthcare organizations. This can highlight areas needing improvement, such as multi-factor authentication, backup testing, or vendor breach clauses. Aligning remediation tasks - like encrypting legacy databases or improving audit logging - with updates to your PHI incident playbooks ensures that lessons learned from one exercise lead to measurable improvements in future ones. Monitoring key metrics, such as time to detect and contain incidents, training completion rates, and the closure rate of corrective actions, also provides a clear picture of how well your incident response program is performing over time.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health
Conclusion
Having a well-thought-out PHI incident response plan is not just about meeting HIPAA requirements - it's about protecting patients, maintaining trust, and ensuring your organization can continue operating smoothly in the face of security incidents. Both the Security Rule and the Breach Notification Rule emphasize the need for covered entities and business associates to identify, respond to, mitigate, and document incidents involving PHI and ePHI.
An effective response plan brings together preparation, detection, containment, recovery, and ongoing improvement. It requires clear role assignments across key teams, including cybersecurity, privacy, legal, compliance, clinical, and executive leadership. As the HSCC aptly points out, many healthcare organizations already have the necessary components to respond to cybersecurity incidents but lack guidance on how to connect them into a cohesive strategy. A coordinated, documented plan bridges this gap. Regular tabletop exercises, after-action reviews, and corrective action plans help ensure your response capabilities grow alongside emerging threats, new technologies, and evolving regulations. This kind of integration strengthens the coordinated approach discussed earlier.
To take your plan further, tools like Censinet RiskOps™ can help streamline your efforts. By consolidating risk assessments across PHI systems, benchmarking your response maturity, and organizing compliance evidence, Censinet RiskOps™ transforms HIPAA requirements into actionable workflows. It centralizes risk data, tracks incidents, and simplifies prioritization and remediation, making your PHI incident response program more efficient and effective.
Start by assembling your incident response team, defining roles and responsibilities, and creating a severity matrix tailored to your organization's specific needs. Incorporate HIPAA breach notification requirements and timelines into your playbooks, and document all decisions to support compliance and regulatory inquiries. Regular testing and updates to your plan are key, as threats and technologies are constantly evolving. By aligning team roles, detection protocols, and recovery strategies, your organization can confidently protect PHI at every stage of an incident.
FAQs
Who should be part of a PHI incident response team?
A well-rounded PHI incident response team needs specific roles to manage breaches effectively while safeguarding patient confidentiality and safety. Here's a breakdown of the essential team members:
Every role is vital for managing incidents effectively, protecting patient information, and maintaining the organization's credibility.
What is a severity matrix, and how does it help manage PHI incidents?
A severity matrix serves as a practical tool for healthcare organizations to evaluate and prioritize their responses to incidents involving Protected Health Information (PHI). By considering key factors such as the potential impact on patient data and the time sensitivity of the issue, it helps teams determine the appropriate level of response and allocate resources efficiently.
This methodical process ensures that high-priority incidents are managed promptly, while less critical issues are handled in a way that aligns with their severity. Ultimately, it supports the protection of sensitive patient information and helps organizations stay in line with healthcare regulations.
What are the key steps to contain and resolve a PHI breach?
To tackle and resolve a PHI breach effectively, quick and organized action is essential. Here’s how to approach it:
By following these steps, organizations can address breaches effectively, limit harm, and build stronger defenses for the future.
Related Blog Posts
- 5 Steps to Train Incident Response Teams in Healthcare
- How to Build a Data Breach Incident Response Plan
- How HIPAA Impacts Incident Response
- Top 7 Incident Response Templates for Healthcare
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"Who should be part of a PHI incident response team?","acceptedAnswer":{"@type":"Answer","text":"<p>A well-rounded PHI incident response team needs specific roles to manage breaches effectively while safeguarding patient confidentiality and safety. Here's a breakdown of the essential team members:</p> <ul> <li><strong>Incident Manager</strong>: Leads the entire response operation, ensuring swift and coordinated actions.</li> <li><strong>Security Analysts</strong>: Dive into the breach details, investigating its scope and assessing potential damage.</li> <li><strong>Legal and Compliance Experts</strong>: Make sure all actions comply with healthcare laws like HIPAA, avoiding further legal complications.</li> <li><strong>Healthcare IT Specialists</strong>: Focus on fixing technical vulnerabilities and getting systems back up and running.</li> <li><strong>Communication/Public Relations Personnel</strong>: Handle both internal and external communications to maintain transparency and trust.</li> <li><strong>Clinical Representative</strong>: Prioritizes patient safety and ensures that care continues with minimal disruption.</li> </ul> <p>Every role is vital for managing incidents effectively, protecting patient information, and maintaining the organization's credibility.</p>"}},{"@type":"Question","name":"What is a severity matrix, and how does it help manage PHI incidents?","acceptedAnswer":{"@type":"Answer","text":"<p>A severity matrix serves as a practical tool for healthcare organizations to evaluate and prioritize their responses to incidents involving Protected Health Information (PHI). By considering key factors such as the <strong>potential impact on patient data</strong> and the <strong>time sensitivity of the issue</strong>, it helps teams determine the appropriate level of response and allocate resources efficiently.</p> <p>This methodical process ensures that high-priority incidents are managed promptly, while less critical issues are handled in a way that aligns with their severity. Ultimately, it supports the protection of sensitive patient information and helps organizations stay in line with healthcare regulations.</p>"}},{"@type":"Question","name":"What are the key steps to contain and resolve a PHI breach?","acceptedAnswer":{"@type":"Answer","text":"<p>To tackle and resolve a PHI breach effectively, quick and organized action is essential. Here’s how to approach it:</p> <ul> <li><strong>Contain the breach immediately</strong>: Isolate the affected systems to prevent further data exposure or loss. Prompt action here can significantly limit the damage.</li> <li><strong>Conduct a thorough investigation</strong>: Dig into the breach to identify its source, how far it spread, and the extent of its impact. Understanding these details is critical for a proper response.</li> <li><strong>Eliminate the threats</strong>: Remove any malware, revoke unauthorized access, and shore up vulnerabilities in your systems to stop the breach from escalating.</li> <li><strong>Restore operations securely</strong>: Use clean backups to bring systems back online and ensure all security patches and updates are applied.</li> <li><strong>Notify the necessary parties</strong>: Inform individuals impacted by the breach and report it to the appropriate regulatory bodies, following all legal requirements.</li> <li><strong>Reinforce security measures</strong>: Implement stronger safeguards and adopt tools designed to manage risks in healthcare environments, reducing the chances of future incidents.</li> </ul> <p>By following these steps, organizations can address breaches effectively, limit harm, and build stronger defenses for the future.</p>"}}]}
Key Points:
What roles form an effective PHI incident response team?
- Incident Commander oversees strategy and decisions
- IT Security Lead handles technical containment and forensics
- Privacy Officer evaluates PHI exposure and drafts notifications
- Legal/Compliance ensures HIPAA alignment and risk assessment
- Clinical leadership supports safe downtime workflows
- Communications/Public Affairs manages patient and media messaging
How should healthcare organizations detect PHI incidents early?
- SIEM alerts flag unauthorized access and unusual logins
- Intrusion detection identifies suspicious network behavior
- Access monitoring tools track PHI views and downloads
- Periodic permission audits catch privilege misuse
- Log analysis reveals trends behind insider or credential‑based threats
What makes a PHI incident severity matrix effective?
- Clear thresholds for patient volume and data sensitivity
- Defined regulatory triggers, including state and OCR reporting
- Consistent scoring for rapid decision‑making under pressure
- Examples of incidents for each severity level
- Alignment with containment playbooks for predictable execution
What are HIPAA‑aligned containment and recovery actions?
- Immediate isolation of compromised systems, APIs, or devices
- Blocking malicious IPs and disabling user accounts
- EDR‑based malware eradication and system rebuilds
- Restoring from trusted backups, validated for integrity
- Safety‑checked reintegration into clinical workflows
- Enhanced post‑restoration monitoring for lingering threats
What communication workflows help meet HIPAA deadlines?
- One‑hour escalation to Privacy Officer and Security Lead
- Executive briefings within four hours of incident discovery
- Pre‑approved templates for internal alerts and patient letters
- Centralized SITREPs summarizing exposure, actions, next steps
- 60‑day HIPAA breach notifications to individuals, OCR, and media (for 500+)
How does Censinet RiskOps™ support PHI incident response?
- Centralized command center for task routing and approvals
- Secure evidence repository for logs, BAAs, and investigation files
- Automated workflow triggers tied to severity and incident type
- Vendor collaboration channels during third‑party‑related breaches
- Dashboards and benchmarking that guide continuous improvement


