ISO/IEC Certification for Healthcare IoT Devices
Post Summary
Healthcare IoT devices are transforming patient care but come with risks like cybersecurity threats and privacy concerns. ISO/IEC certification helps ensure these devices meet stringent security, privacy, and quality standards, aligning with U.S. regulations like HIPAA, HITECH, and FDA guidelines. Key standards include:
- ISO/IEC 27001: Information security management.
- ISO/IEC 27701: Privacy information management.
- ISO/IEC 27400/27402: IoT security and privacy controls.
- ISO 13485: Quality management for medical devices.
- IEC 62304: Software lifecycle for medical devices.
- IEC 81001-5-1: Cybersecurity for health IT networks.
Achieving certification involves:
- Governance, scoping, and gap analysis.
- Implementing controls for risks like ransomware or software vulnerabilities.
- Documentation, internal audits, and external certification.
Benefits include stronger security, regulatory compliance, and streamlined vendor management. Challenges include costs, integrating standards into legacy systems, and organizational adjustments. Start with high-risk devices and build a phased approach to certification for long-term success.
Key ISO/IEC Standards for Healthcare IoT Devices
Key ISO/IEC Standards for Healthcare IoT Devices
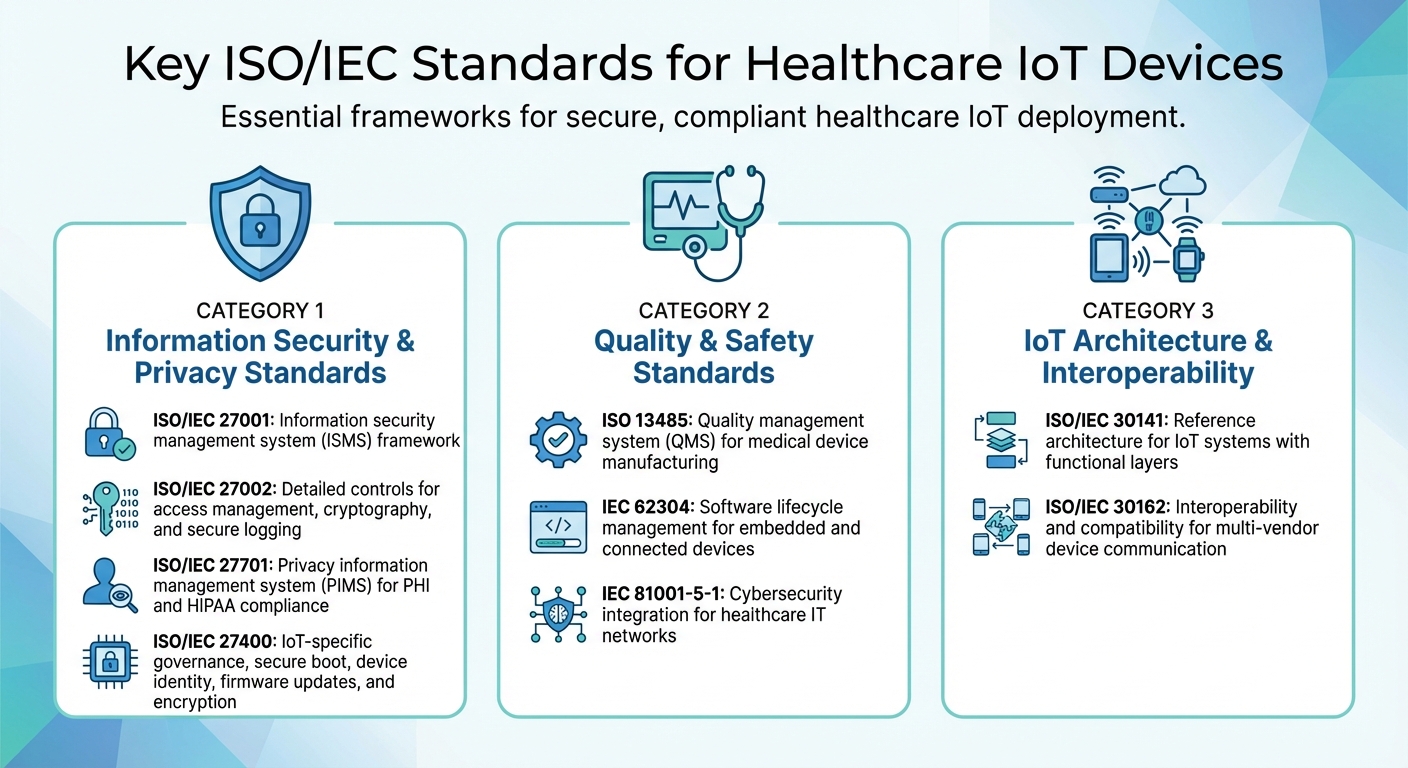
Healthcare IoT devices must comply with a range of standards that address security, privacy, quality, safety, and interoperability. These frameworks form the foundation for producing connected medical devices that meet the rigorous demands of U.S. clinical settings. Each standard tackles specific challenges associated with cybersecurity, privacy, and the seamless integration of IoT in healthcare.
Information Security and Privacy Standards
ISO/IEC 27001 sets the framework for an information security management system (ISMS), while ISO/IEC 27002 provides detailed guidance on controls like access management, cryptography, secure logging, and development processes [6].
Building on these, ISO/IEC 27701 introduces a privacy information management system (PIMS) tailored for managing personal data and protected health information (PHI) [2]. It is particularly useful for healthcare organizations aiming to meet privacy regulations like HIPAA and state-specific laws, as it seamlessly integrates privacy controls with existing security measures.
ISO/IEC 27400 focuses on the unique challenges of IoT ecosystems. It outlines key controls for governance, risk management, and secure lifecycle practices. Specific measures include secure boot processes, device identity protocols, firmware updates, encryption, and guidelines for vulnerability disclosure - all critical for safeguarding connected medical devices [5].
Quality and Safety Standards
ISO 13485 defines the quality management system (QMS) for medical device manufacturing. This standard ensures the consistent design, production, and servicing of safe medical devices, including IoT-enabled equipment. It also links key processes, like design history and risk management, to recognized frameworks [2][3].
For software, IEC 62304 governs the entire lifecycle, from development planning and architecture to validation, verification, and maintenance. This is especially important for embedded software and connected devices, where network connectivity introduces additional clinical risks [2][3].
IEC 81001-5-1 integrates cybersecurity into healthcare IT networks. It ensures that medical devices within clinical environments meet both security and safety requirements. By aligning device-level security with broader clinical network needs, this standard helps healthcare organizations meet U.S. regulatory expectations while maintaining patient safety.
IoT Architecture and Interoperability Standards
ISO/IEC 30141 provides a reference architecture for IoT systems, detailing functional layers, system viewpoints, and trustworthiness factors [7]. Healthcare organizations can use this framework to design IoT ecosystems that span everything from bedside devices and wearables to network and application layers. This structured approach improves trust and interoperability, simplifying certification processes and risk assessments [7].
ISO/IEC 30162 defines interoperability and compatibility requirements for IoT devices and networks. While initially developed for industrial IoT, its principles are highly applicable in healthcare. This standard ensures that devices from multiple vendors can communicate effectively within clinical networks and existing EHR systems, supporting seamless integration of medical and non-medical IoT systems [2].
Steps in the ISO/IEC Certification Process
Getting ISO/IEC certification for healthcare IoT devices is a structured journey, starting with governance and scoping and moving through implementation and audits. Most organizations combine standards like ISO/IEC 27001 for information security, ISO 13485 for medical device quality, and newer IoT-focused standards such as ISO/IEC 27400 and 27402 into a unified framework [2]. This approach ensures that security, privacy, quality, and safety are seamlessly addressed.
Governance, Scoping, and Gap Analysis
The first step is to establish a cross-functional governance team. This team should include representatives from IT security, clinical engineering, quality and regulatory affairs, privacy, procurement, and risk management. They’ll be responsible for setting policies, allocating resources, and making key decisions regarding IoT device risks. Clear accountability within the team is essential to keep the process on track.
Next, define the exact scope of all critical IoT assets. This includes bedside devices, wearables, gateways, on-premises servers, cloud platforms, mobile apps, and vendor-managed services that handle patient data or affect patient safety. A well-defined scope prevents the oversight of critical risks and avoids wasting resources on non-essential areas.
After scoping, perform a gap analysis to compare current practices with ISO/IEC standards. Map existing controls to the requirements of ISO/IEC 27001, ISO 13485, and relevant IoT-specific standards. This analysis will pinpoint missing policies, documentation, and safeguards. Use the findings to create a prioritized remediation plan with clear timelines and responsibilities for closing each gap.
Implementing Controls and Managing Risks
Once gaps are identified, focus on implementing security and privacy controls tailored to the unique risks in healthcare, such as ransomware attacks or software vulnerabilities. Align these measures with U.S. regulations like HIPAA to ensure patient data is protected. Use tools like PKI and device certificates to enable mutual authentication and TLS encryption [8]. For software-enabled devices, follow the IEC 62304 framework, which covers requirements, architecture, risk management, and validation, to simplify compliance [3].
Develop a risk management process to identify threats and vulnerabilities by device type. Assess the likelihood and potential impact of these risks, including their effects on patient safety and exposure of protected health information (PHI). Apply appropriate mitigation strategies, making sure that cybersecurity measures don’t interfere with device performance or patient care.
Documentation, Internal Audit, and Certification
With controls in place, document all processes thoroughly to support internal audits and certification. Maintain key records such as policies, procedures, asset inventories, risk registers, training logs, and audit reports. For medical IoT devices, additional documentation - like design history files and software lifecycle records - will be necessary for both ISO and regulatory compliance.
Schedule internal audits at least once a year or whenever major changes occur, such as new device platforms, significant cloud migrations, or large-scale deployments. Internal auditors should be independent and knowledgeable about ISO/IEC standards, healthcare regulations, and clinical environments. Ensure that any identified issues are resolved before involving an external certification body.
When ready, choose an accredited certification body with expertise in healthcare and IoT. The certification process typically involves two stages: Stage 1 focuses on reviewing your documentation and overall readiness, while Stage 2 evaluates the practical implementation and effectiveness of your controls. Many certification bodies also offer a pre-audit or readiness review to flag potential issues before the formal audit. Certification is followed by ongoing surveillance audits (annually or semi-annually) and full recertification every three years to maintain compliance.
Integrating ISO/IEC Certification into Healthcare Risk Management
Incorporating ISO/IEC certification into healthcare risk management builds on existing controls and aligns with U.S. regulatory frameworks. The objective is to harmonize international standards with domestic requirements like HIPAA, HITECH, the NIST Cybersecurity Framework, and FDA cybersecurity guidance. This creates a unified strategy to tackle both global standards and local regulatory demands.
Alignment with U.S. Regulations and Standards
ISO/IEC 27001 and HIPAA share several overlapping requirements, such as risk assessments, access controls, encryption, audit logging, and incident response plans. However, the primary distinction lies in their approach: ISO/IEC 27001 offers a certifiable management system verified through third-party audits, while HIPAA outlines regulatory mandates without a formal certification process [4][5]. By mapping ISO/IEC 27001 controls to HIPAA's Security Rule, organizations can address both frameworks. For instance, ISO/IEC 27001's access control measures (A.9) align with HIPAA's requirement to limit PHI access to authorized personnel.
ISO/IEC 27400:2022 further supports compliance by offering comprehensive controls from devices to the cloud, complementing HIPAA's requirements [5][9]. Similarly, ISO/IEC 27402:2023 establishes baseline ICT standards for IoT devices, aligning with both HIPAA security measures and FDA guidelines for ensuring safety and effectiveness [4].
FDA cybersecurity guidance for medical devices complements standards like IEC 62304 (software lifecycle) and IEC 81001-5-1 (health software security). These align with ISO/IEC certification principles, ensuring secure product development. Additionally, the NIST Cybersecurity Framework 2.0, endorsed by HHS alongside the Health Industry Cybersecurity Practices (HICP) and Healthcare and Public Health Cyber Performance Goals, emphasizes IoT and medical device security [6]. These frameworks naturally integrate with ISO/IEC 27001’s risk-based approach, offering a cohesive system for managing risks.
Managing Third-Party and Supply Chain Risks
In healthcare, securing vendor networks and supply chains is critical. IoT vendors and supply chain partners often introduce cybersecurity vulnerabilities. To mitigate these risks, healthcare organizations can require vendors to demonstrate their security practices through certifications. Instead of creating custom security questionnaires, organizations can insist that IoT and medical device suppliers maintain ISO/IEC 27001 certification for information security and ISO 13485 for quality management, transferring some compliance responsibilities to vendors.
During vendor evaluations, request current ISO/IEC certifications, recent audit reports, and contractual agreements for ongoing compliance. For vendors lacking formal ISO/IEC certification, ask for documentation showing how their controls align with ISO/IEC 27001 Annex A and ISO/IEC 27402 baseline IoT controls.
Platforms tailored for healthcare risk management simplify this process by enabling secure data exchange between healthcare organizations and vendors. For example, Censinet RiskOps™ connects healthcare delivery organizations with over 50,000 vendors and products, allowing vendors to share security documentation and streamline risk assessments [1].
Matt Christensen, Sr. Director GRC at Intermountain Health, emphasizes: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
Continuous Compliance and Monitoring
Addressing regulatory and vendor risks is just the beginning - continuous compliance is essential. ISO/IEC certification is not a one-and-done effort; it requires ongoing monitoring and periodic recertification. Conduct internal audits annually for your IoT scope and prepare for surveillance audits by certification bodies, which typically occur annually or biennially between full recertifications [2]. These audits ensure that controls remain effective as your IoT environment evolves.
Maintain a proactive approach by performing regular vulnerability scans, applying patches, and monitoring threats. When new vulnerabilities arise, assess their impact and document your findings. This demonstrates diligence while maintaining compliance with ISO/IEC standards and U.S. regulations.
When deploying new devices or services, review the scope of your certification. Updates to risk assessments, control measures, and certification scope may be necessary. AI-powered platforms can simplify this process by offering real-time risk dashboards and automated workflows that adapt to changes in resources, workforce, and budgets [1].
Brian Sterud, CIO at Faith Regional Health, notes: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
In the event of an IoT-related cybersecurity incident, ISO/IEC certification can be a powerful tool to demonstrate due care. Comprehensive risk assessments, implemented controls, and detailed audit trails provide evidence that reasonable steps were taken to safeguard patient data and device security - critical factors during regulatory reviews or legal proceedings.
sbb-itb-535baee
Benefits and Challenges of ISO/IEC Certification
Benefits for Healthcare Organizations
Achieving ISO/IEC certification brings several advantages, especially for healthcare organizations managing IoT devices. One of the most critical benefits is a stronger cybersecurity framework. Standards like ISO/IEC 27400:2022 address both cyber and physical security aspects, creating a well-rounded defense for IoT devices in healthcare settings[5][9]. This, in turn, enhances patient safety, as certified devices are subjected to stringent risk management and traceability requirements under IEC 62304 and ISO 13485. These standards also support FDA submissions and ensure continuous safety monitoring[3].
Certification also simplifies regulatory compliance. For instance, organizations following ISO 13485 often report fewer nonconformities and smoother outcomes during FDA reviews or when meeting EU MDR requirements[2][3]. The detailed risk management files, design histories, and security testing records mandated by these standards streamline regulatory submissions and demonstrate thorough preparation during audits. Similarly, compliance with ISO 30141 provides a standardized IoT architecture, ensuring better interoperability and reliability across diverse devices, which is especially vital in the complex environment of hospitals[7].
Another advantage lies in procurement and vendor management. By prioritizing ISO/IEC-certified devices, healthcare organizations can eliminate the need for custom security questionnaires for every vendor. Instead, they can rely on third-party certifications as a baseline, reducing the workload for internal teams while maintaining consistent security standards across the supply chain. However, these benefits must be balanced against the time, resources, and organizational adjustments required to achieve certification.
Cost, Effort, and Common Challenges
Despite its advantages, ISO/IEC certification comes with challenges, starting with the financial and operational commitments it demands. Costs vary depending on the size and scope of the organization, but they typically include fees for initial and recurring audits. Certification bodies charge for services like gap analyses, Stage 1 and Stage 2 audits, and ongoing surveillance visits[2]. Beyond these direct costs, organizations must also account for indirect expenses, such as staff time, updates to documentation systems, and implementing required controls. Budgeting for these expenses over a 3–5 year period is essential.
Operationally, integrating ISO/IEC standards into healthcare settings can be complex. Legacy medical devices often lack the modern security features required by these standards. Upgrading or replacing these older systems can be difficult due to clinical dependencies and budget constraints. Additionally, fragmented networks across multiple vendors further complicate integration, as devices may operate under different security protocols and frameworks.
Cultural and organizational resistance can also hinder certification efforts. For example, incorporating software lifecycle controls from IEC 62304 into agile development workflows requires a level of process discipline that some teams may find difficult. Teams accustomed to rapid iteration may push back against the extensive documentation and traceability requirements that certification entails[3].
Roadmaps for Certification and Continuous Improvement
To maximize the benefits of certification and address its challenges, healthcare organizations should take a phased, strategic approach. Start by focusing on high-risk IoT devices - those that handle sensitive patient data or perform critical clinical functions should be prioritized. Begin with ISO/IEC 27001 to establish a solid foundation for information security management, then expand into device-specific standards like IEC 81001-5-1 for health software security or ISO 13485 for quality management as the program evolves.
Integrating certification tasks into existing workflows is key. Maintain unified documentation for design history and risk management, and continuously benchmark against industry standards to address emerging gaps quickly. This approach minimizes redundant efforts and ensures consistency across various regulatory requirements[3]. Additionally, organizations should regularly assess their cybersecurity maturity to pinpoint weaknesses and secure necessary resources. When introducing new devices or expanding IoT capabilities, proactively update risk assessments and certification documentation. This way, gaps can be addressed before they are flagged during audits.
Conclusion
ISO/IEC certification has become an essential step for healthcare organizations managing connected medical devices. These standards provide a structured approach to tackling the unique security, privacy, and safety challenges posed by IoT devices in clinical settings. By implementing frameworks like ISO/IEC 27400[5] for IoT governance and ISO/IEC 27402:2023[4] for baseline security and privacy controls throughout a device's lifecycle, healthcare providers can strengthen their defenses against cyber threats while safeguarding patient data.
But it’s not just about cybersecurity. Certification also plays a vital role in improving clinical care. Standards such as ISO 13485 and IEC 62304 incorporate strict risk management, traceability, and lifecycle controls into device development and deployment. The result? Fewer device failures, more consistent performance, and better outcomes for patients. By aligning these efforts with U.S. regulations - like the HIPAA Security Rule, HITECH Act, NIST CSF 2.0, and HPH Cyber Performance Goals - organizations can streamline compliance while avoiding redundant work[6].
Interoperability offers another key advantage. Standards like ISO/IEC 30141 provide a reference architecture that promotes trust and compatibility across devices from different vendors. This makes integration easier and helps create a more cohesive and secure ecosystem[7].
For healthcare organizations and IoT vendors beginning their certification journey, the roadmap is clear. Start with high-risk devices, establish a foundation using ISO/IEC 27001, and gradually adopt device-specific standards as your program evolves. Incorporate certification tasks into your existing workflows, keep documentation centralized, and regularly evaluate your cybersecurity readiness. Tools like Censinet RiskOps™ can simplify third-party risk assessments and help ensure vendor compliance across your supply chain.
Although certification demands both financial and operational investment, the benefits are undeniable. Organizations that adopt ISO/IEC standards position themselves for greater resilience, smoother regulatory reviews, and stronger stakeholder trust. As connected care continues to grow in the U.S., certification is about more than just meeting today’s demands - it’s about building a secure foundation for future advancements while prioritizing patient safety.
FAQs
What are the key benefits of obtaining ISO/IEC certification for healthcare IoT devices?
ISO/IEC certification plays a crucial role in the world of healthcare IoT devices, ensuring they meet internationally recognized standards. This certification bolsters safety, security, and reliability, which are essential in minimizing risks and safeguarding sensitive patient information.
On top of that, it streamlines regulatory approval processes, fosters trust among healthcare providers and patients, and strengthens cybersecurity protocols. Tools like Censinet RiskOps™ can provide additional support, helping healthcare organizations effectively manage risks and ensure their devices align with these vital standards.
How does ISO/IEC certification support compliance with U.S. healthcare regulations like HIPAA?
ISO/IEC certification offers healthcare organizations a structured approach to align with U.S. healthcare regulations like HIPAA. It provides a standardized framework to manage cybersecurity risks and safeguard sensitive data, ensuring patient information and PHI are protected in line with HIPAA's stringent data security requirements.
When healthcare providers implement ISO/IEC standards, they show a strong dedication to security best practices. This not only helps meet compliance demands but also strengthens trust among patients and business partners.
What obstacles might healthcare organizations encounter during the ISO/IEC certification process?
Healthcare organizations encounter a variety of hurdles when pursuing ISO/IEC certification. Among the most common are the complex regulatory requirements they must navigate, ensuring that every piece of documentation is both complete and accurate, and aligning their internal processes to meet the precise standards set by ISO/IEC.
On top of that, limited resources - whether it's time, budget, or staff expertise - can make it tough to give the certification process the attention it demands. Tackling these challenges head-on can help simplify the journey and improve the chances of achieving compliance successfully.


