How to Monitor IoT Device Security in Real Time
Post Summary
Healthcare IoT devices, like ventilators and imaging systems, are essential but often lack modern security. This makes continuous, real-time monitoring critical to prevent disruptions, protect sensitive data, and ensure patient safety. Here's what you need to know:
- Why It Matters: IoT devices handle critical tasks and sensitive information. A single breach can compromise care, cause delays, or violate regulations like HIPAA.
- Key Steps: Start by cataloging all devices, segmenting networks, and centralizing logs. Use tools to detect unusual behavior and prioritize alerts based on device risk.
- Risk Tiers: Devices are classified as high, medium, or low risk depending on their clinical importance, PHI involvement, and vulnerabilities.
- Monitoring Setup: Build a system with passive network visibility, a centralized SIEM platform, and automated response tools.
- Detection Rules: Define baselines for normal behavior and create alerts for deviations, like unapproved outbound connections or lateral movement.
- Integration: Align security with clinical workflows to minimize disruptions while addressing threats efficiently.
Real-time monitoring safeguards patient care by identifying and addressing threats before they escalate. Focus on high-risk devices first and continuously refine your system for evolving threats.
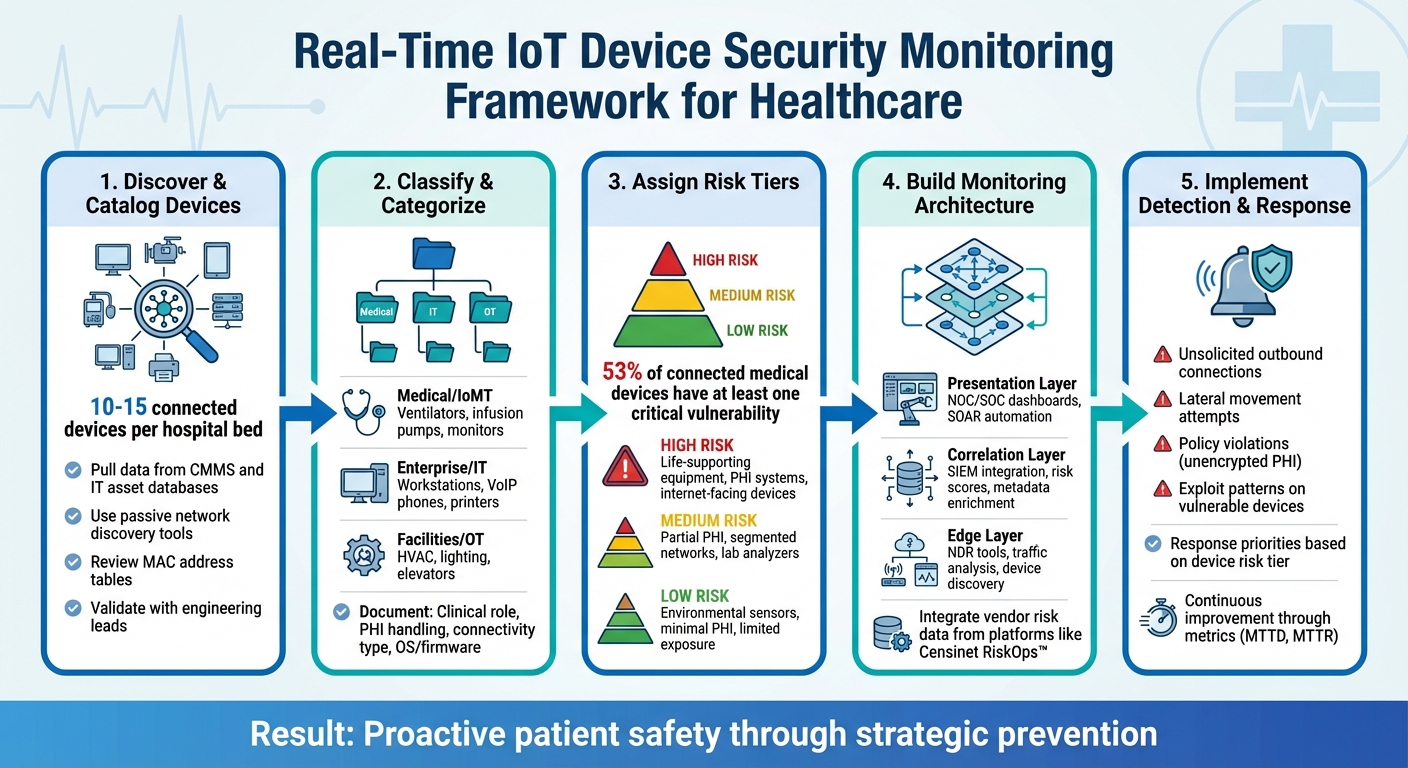
5-Step Framework for Real-Time IoT Device Security Monitoring in Healthcare
Mapping and Classifying IoT Devices in Healthcare
After setting up your inventory and network segmentation, the next step is to map and classify all devices. This process is essential for effective monitoring. Many hospitals underestimate the number of IoT devices they use - on average, there are 10–15 connected devices per hospital bed, including medical equipment, IT systems, and building automation tools. That quickly adds up to thousands of devices, many of which are unmanaged or invisible to traditional IT asset systems [2].
How to Discover and Catalog IoT Devices
Start by pulling data from your existing systems, such as your computerized maintenance management system (CMMS), IT asset database, and biomedical inventory. However, these systems often miss "shadow" devices - equipment connected by staff or vendors without formal approval.
To uncover these hidden devices, use passive network discovery tools on key segments, like clinical, imaging, and automation networks. These tools analyze traffic patterns and protocols (e.g., HL7, DICOM, MQTT) to identify devices without actively probing them, which could disrupt sensitive medical equipment. Additionally, review MAC address tables from switches, routers, and wireless controllers to identify mobile or temporary devices.
Once this data is gathered, validate your findings with engineering and departmental leads. Conduct structured walkthroughs in clinical and specialized areas to reconcile network data with physical equipment. These sessions help confirm device ownership, clinical use, and any vendor-related remote access. To keep your inventory accurate, schedule regular scans - weekly or monthly - and set up automated alerts for newly connected devices.
Creating a Device Classification Schema
Organize devices into categories that align with both security operations and clinical workflows. Start by grouping devices into three broad classes:
- Medical/IoMT: Includes ventilators, infusion pumps, patient monitors, and imaging systems.
- Enterprise/IT: Covers workstations on wheels, VoIP phones, printers, and badge readers.
- Facilities/OT: Encompasses HVAC controllers, smart lighting, elevators, and security cameras [2].
Within each category, document key attributes that impact monitoring, such as the device’s clinical role (e.g., life-supporting or diagnostic), whether it handles PHI (Protected Health Information), its connectivity type (wired, Wi-Fi, Bluetooth, etc.), and its network exposure (on-premises only, internet-facing, or requiring vendor remote access).
Also, track details like the device’s operating system or firmware version, manufacturer support timeline, and the clinical or IT team responsible for it. Use standardized naming conventions - e.g., "Lifepak 20E – ICU Crash Cart" - to make it easier for security and clinical teams to interpret alerts. Integrate this schema into your CMMS and asset management systems, allowing you to filter dashboards by category or owner during incident response.
Assigning Risk Tiers for Monitoring
Once devices are classified, assign them to high, medium, or low risk tiers based on four key factors: clinical importance, PHI involvement, network exposure, and known vulnerabilities.
- High-risk devices: These include life-supporting or life-sustaining equipment (like ventilators and ICU monitors), systems that process or store large amounts of PHI (e.g., imaging archives), and internet-facing devices, especially those running outdated operating systems. A study revealed that 53% of connected medical devices and other IoT devices in hospitals have at least one critical vulnerability, highlighting the importance of this step.
- Medium-risk devices: These handle some PHI or have notable clinical roles but are partially safeguarded by network segmentation or limited external connectivity. Examples include lab analyzers, nurse call systems, and imaging workstations that operate internally.
- Low-risk devices: These pose minimal risk due to limited PHI handling, low clinical impact, and restricted exposure. Examples include environmental sensors or vending machines, which still require basic monitoring to prevent them from being exploited as attack vectors.
To refine these tiers, use external data sources like Censinet RiskOps™, which consolidates vendor and product risk information. Devices linked to higher-risk vendors or products can be flagged for stricter monitoring, such as deeper traffic inspection or tighter network segmentation. For equipment that can’t be patched promptly - like imaging devices or life-support systems - assign higher monitoring priority and implement stricter network controls to mitigate risks.
Regularly review and update risk tiers, especially when new vulnerabilities, FDA safety notices, or manufacturer updates arise. Track metrics like the "percentage of devices classified and risk-tiered" and the "number of unknown devices on the network" to measure progress. Establish a cross-functional IoT governance team with representatives from information security, clinical engineering, IT networking, and facilities management to continually refine classification and monitoring strategies. This approach ensures that your detection and response systems remain effective and up to date.
Designing a Real-Time Security Monitoring Architecture
After classifying and assigning risk tiers to your devices, the next step is creating a system that can monitor them in real time. Healthcare environments often rely on unmanaged IoT and medical devices, many of which run outdated systems. Your monitoring setup needs to account for these challenges while delivering comprehensive visibility. To achieve this, focus on integrating the essential components that ensure uninterrupted monitoring.
Core Components of a Monitoring Architecture
Start by establishing passive network visibility as the backbone of your architecture. Place network taps or SPAN ports at key aggregation points, such as core switches, medical VLANs, and wireless controllers that manage clinical devices. Passive sensors should be deployed at critical points in the network to collect enriched telemetry, which can then be fed into a Security Information and Event Management (SIEM) system. This setup supports automated responses through Security Orchestration, Automation, and Response (SOAR) systems. Avoid active scanning methods, as they can interfere with FDA-regulated equipment or void warranties [2].
The architecture should consist of three primary layers:
- Network Data Capture: Use sensors capable of interpreting healthcare-specific protocols like DICOM (for imaging), HL7 (for lab and clinical data), and vendor-specific telemetry.
- Centralized Management: Implement a SIEM platform to aggregate logs from diverse sources, including firewalls, VPNs, wireless controllers, Electronic Health Record (EHR) systems, and IoT gateways, providing a unified view of activity.
- Response and Workflow Tools: Integrate ticketing systems, SOAR platforms, and change-management tools to automate or guide responses, such as isolating a device, moving it to a restricted VLAN, or generating a patching ticket.
These components should connect via secured APIs and syslog feeds. Network Detection and Response (NDR) tools and asset management platforms can send enriched events to the SIEM, which then adds risk context and forwards incidents to ticketing or SOAR systems. To ensure reliability, design for high availability with redundant collectors, failover mechanisms, and resilient log pipelines. Any lapse in monitoring could leave critical clinical systems exposed.
Integrating Risk and Vendor Data
Relying solely on network and log data won't help you determine which alerts are most critical. Risk context - such as vendor security ratings, known vulnerabilities, and software bill of materials (SBOM) details - provides the missing piece. Solutions like Censinet RiskOps™ play a key role here. Censinet RiskOps draws from a database of over 50,000 vendors, offering secure access to cybersecurity and risk insights [1].
Incorporate vendor risk assessments, product vulnerability data, and third-party risk scores from Censinet RiskOps into your SIEM or asset management platform. For example, if an alert is triggered on a device tied to a high-risk vendor or a product with critical vulnerabilities, the system can automatically escalate its priority. Similarly, if anomalous behavior is detected from a vendor’s IP range or integration interface, the risk score can help your team prioritize the alert. This approach shifts your focus from treating all alerts equally to prioritizing those that pose the highest risk to patient safety and operational continuity.
With this added risk data, your monitoring tools can work together for more effective detection.
Combining Monitoring Layers for Complete Visibility
The true strength of your monitoring architecture lies in layering data sources. At the edge layer, NDR and IoT security tools handle raw traffic analysis, device discovery, behavioral analytics, and initial threat detection. At the correlation layer, your SIEM integrates network events with logs from clinical systems, enriches the data with device metadata, and incorporates risk scores from platforms like Censinet RiskOps. Finally, at the presentation and workflow layer, dashboards provide your Network Operations Center (NOC) and Security Operations Center (SOC) teams with a unified view, while IT Service Management (ITSM) and SOAR tools streamline triage and response.
To prevent overwhelming your analysts, focus on generating prioritized alerts enriched with risk scores, device criticality, and potential patient impact. Lower-level telemetry should still be stored for forensic investigations, but it shouldn't create unnecessary alerts. By linking network anomalies to device metadata, clinical roles, and risk scores, your team can quickly address issues that directly affect patient care. This layered approach ensures your team can act swiftly on critical incidents while maintaining the depth needed to investigate complex situations, keeping healthcare operations secure and efficient.
Implementing Detection and Alerting Rules
With your monitoring system in place, the next step is crafting rules that can identify security incidents before they disrupt patient care. The key is to strike a balance: alerts must be specific enough to catch real threats without overwhelming your team with false positives. Start by defining what "normal" looks like for each type of device, and then create rules to flag meaningful deviations.
Building Baseline Profiles for IoT Devices
Effective detection begins with a deep understanding of normal behavior for each category of device. Automated discovery tools can help you gather essential details for every device, such as the vendor, model, operating system, firmware version, physical location, and clinical purpose. For critical devices - like ventilators, infusion pumps, patient monitors, and imaging systems - it's vital to document the communication protocols they use and their primary endpoints.
Go further by tracking operational data like device uptime, CPU and memory usage, I/O performance, and error rates. These metrics can help you differentiate between normal activity and signs of potential threats, whether it's a cyberattack or a developing hardware issue that might disrupt patient care.
Once you've established these precise baselines, you can create targeted detection rules to monitor key security events.
Defining Security Use Cases for Alerts
With baselines in place, focus on crafting detection rules for the risks that pose the greatest threat to your environment. For example, flag any unsolicited outbound connections when medical devices communicate with unknown external IPs or domains, especially those in unexpected regions or tied to dynamic DNS providers often used in command-and-control operations. To refine this, create allowlists of approved domains and IPs for each device type, and alert on any traffic outside those boundaries.
Be vigilant for lateral movement attempts. If a device starts scanning internal subnets or initiates unusual connections - like SMB, RDP, or SSH - to high-value systems such as EHR databases or domain controllers, that’s a red flag. Policy violations should also trigger alerts, such as unencrypted PHI transmissions where encryption is mandatory, the use of outdated protocols like Telnet or SMBv1, or direct communication between medical device networks and public or guest Wi-Fi networks. For devices with known vulnerabilities, identified through SBOM (Software Bill of Materials) or firmware data, set up rules to detect exploit patterns, such as RDP brute-force attempts targeting older imaging workstations.
The next step is to tie these alerts to operational metrics to better understand their impact on clinical workflows.
Connecting Security Events with Performance Impact
To prioritize alerts effectively, correlate security events with performance data to gauge their impact on clinical operations. For instance, if your SIEM detects unusual behavior, like a device initiating numerous network sessions or exhibiting beaconing activity, compare this with performance metrics from the same device. A CPU spike combined with unusual outbound traffic is far more concerning than either event in isolation. This approach helps you differentiate between harmless anomalies - such as scheduled firmware updates - and active threats that could impair device functionality.
Using pre-established risk tiers, integrate performance data to assess how security events affect clinical workflows. Map each device to its role in patient care - for example, tagging devices as part of ICU, imaging, or pharmacy systems. When an alert involves a device critical to patient outcomes, escalate it with higher priority and provide clear context for both clinical engineering and security teams. Include clinical impact details in your alerts, such as "potential delay in medication delivery" or "imaging services may be disrupted", to help analysts prioritize their response. Tools like Censinet RiskOps™ can streamline this process by combining vendor risk assessments and device vulnerability data, enabling automatic escalation for high-risk devices or products with critical flaws.
sbb-itb-535baee
Operationalizing Continuous Monitoring and Response
Once you've set up a solid monitoring framework and detection rules, the next step is making these processes part of everyday operations. Building the system is just the start - the real challenge lies in weaving it into the daily workflows. Healthcare organizations often deal with tens of thousands of unmanaged IoT and IoMT devices, which far outnumber traditional IT endpoints. Managing these manually is simply not feasible. The key to success is clear accountability, automated processes, and fostering a partnership between security and clinical teams to safeguard patient care without causing disruptions.
Integrating Monitoring into Daily Operations
Start by clearly defining team roles. The Security Operations Center (SOC) should manage 24/7 alert monitoring, handle initial triage, and correlate security events. Clinical engineering or biomedical teams oversee device status, coordinate firmware updates with vendors, and assess whether devices can safely go offline. IT and network teams enforce segmentation policies, manage access controls, and maintain logging systems. When decisions might impact patient safety or disrupt workflows - like isolating a ventilator - clinical leadership steps in to guide the process.
Establish response timelines based on the risk levels of devices. For critical devices like life-support systems, triage alerts almost immediately and have pre-approved containment strategies ready. Medium-risk devices may allow a few hours for triage, aligned with department schedules. Low-risk devices, such as building sensors, can follow standard IT response timelines. Incorporate a daily review of overnight alerts, active incidents, and containment actions to keep teams aligned and informed.
As Terry Grogan, CISO of Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" - highlighting how the right tools can streamline operations and free up staff for proactive security measures.
Responding to IoT Security Alerts
When an alert is triggered, follow a structured validation process. Pull relevant details - such as the device type, manufacturer, firmware version, network placement, and clinical role - from your asset inventory. Determine if the device is actively being used for patient care and its specific function. If the threat is credible, like communication with a known malicious IP or signs of lateral movement, convene a cross-functional team that includes SOC, biomedical/IT staff, and a clinical lead to decide on next steps.
Containment strategies must prioritize patient safety above all else. Options like network isolation, rate-limiting, or implementing strict allow-lists are typically safer than powering down a life-sustaining device. Only shut down a device when a safe clinical alternative is available. For devices that can't be immediately patched or isolated, consider "virtual patching" by blocking specific ports or protocols at the network level. Document all actions and decisions in your ITSM tool to maintain audit trails for HIPAA compliance and future analysis.
After resolving the incident, conduct a detailed review to identify opportunities for improvement.
Improving Monitoring Systems Over Time
Every incident provides a chance to refine your monitoring system. Assess whether detection rules triggered on time and whether alerts provided enough context. Track metrics like mean time to detect (MTTD), mean time to respond (MTTR), false-positive rates, and device downtime to fine-tune your approach. Adjust baselines - such as normal traffic patterns or update behaviors - to reduce false positives over time.
Censinet RiskOps™ can centralize data on third-party risks, device vulnerabilities, and enterprise risks, helping you continuously refine your processes. This platform provides a comprehensive view of vendor risk assessments, device vulnerabilities, and benchmarks against similar healthcare organizations.
As Brian Sterud, CIO of Faith Regional Health, stated, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Use these insights to focus monitoring efforts, improve detection rules, and justify investments in security infrastructure. Over time, this continuous feedback loop strengthens your defenses and ensures your monitoring system evolves to meet new threats.
Conclusion and Key Takeaways
Real-time IoT device security monitoring goes beyond being an IT task - it's a critical component of patient safety. With a solid understanding of your device inventory and risk classifications, real-time monitoring becomes a cornerstone of protecting patient care. Healthcare organizations rely on a wide range of connected devices - infusion pumps, ventilators, imaging systems, lab analyzers, and more. Any security breach in these systems can disrupt essential procedures and put patients at risk. To effectively safeguard these devices, you need a complete inventory, risk-based classifications, multi-layered detection strategies, and response plans that balance security needs with clinical workflows.
To succeed, it's essential to align security measures with patient care priorities. This means integrating IoT security with clinical risk management. Engage key stakeholders like clinical engineering, biomedical teams, and nursing leadership in your governance structure. Response timelines should reflect the impact on patient safety - devices critical to care must be addressed immediately, while lower-risk devices can follow standard IT protocols. Security alerts should also be tied to clinical context, such as which units, patients, or procedures rely on a particular device. This helps prioritize incidents and makes a stronger case for investments when presenting to leadership.
Continuous improvement is non-negotiable as threats, devices, and clinical needs evolve. Metrics like mean time to detect (MTTD), mean time to respond (MTTR), and false-positive rates can help fine-tune detection rules. Post-incident reviews after every alert should be used to update baselines and refine response playbooks. Tools like Censinet RiskOps™ offer centralized oversight by combining third-party risk assessments, device vulnerabilities, and benchmarking data. This governance layer complements technical monitoring and supports proactive risk management across medical devices, patient health information (PHI), clinical applications, and supply chains - making daily monitoring processes more practical and effective.
Start with the basics: build a comprehensive device inventory, classify assets by risk level, and form cross-functional teams for coordinated responses. Focus first on monitoring the highest-risk devices to quickly reduce exposure and build momentum. Healthcare-specific platforms designed for continuous risk management can simplify these efforts, allowing your team to shift from manual processes to more efficient, automated solutions.
Proactive IoT monitoring transforms your approach from reactive problem-solving to strategic prevention. Real-time monitoring enables faster interventions, better patient outcomes, and reduced costs. By embedding security into everyday operations and continuously refining your methods, you create a resilient system that safeguards both patient safety and your organization's integrity.
FAQs
How can hospitals securely monitor and manage large networks of IoT devices in real time?
Hospitals can ensure the secure management of their vast IoT device networks with platforms like Censinet RiskOps™, which are tailored specifically for healthcare settings. These platforms offer tools for real-time monitoring, automated risk assessments, and security analytics, safeguarding sensitive patient data while keeping devices running smoothly.
With features such as centralized dashboards, automated alerts, and ongoing compliance checks, healthcare organizations can maintain clear oversight of thousands of connected devices. These tools not only enhance threat detection but also cut down on manual effort and enable swift responses to potential risks, promoting both security and efficiency in hospital operations.
What are the best practices for categorizing healthcare IoT devices by risk level?
To sort healthcare IoT devices by risk level, start by assessing their importance, potential vulnerabilities, and the impact they could have on patient safety. Devices that manage sensitive patient information or are essential to clinical operations should be placed in higher risk categories.
Implement a risk scoring system to focus on devices that demand the most attention. Ensure continuous monitoring of high-risk devices by utilizing real-time threat intelligence and device behavior analysis. Regularly updating risk tiers based on emerging threats or vulnerabilities is crucial. Routine reviews help maintain a strong security approach, safeguarding both patient safety and data integrity.
How does combining clinical workflows with security measures improve IoT device monitoring?
Integrating clinical workflows with security measures creates a stronger framework for monitoring IoT devices in healthcare. By aligning security protocols with patient care operations, potential threats can be detected and managed in real time - without interrupting essential healthcare activities.
This approach allows healthcare organizations to minimize vulnerabilities, improve response times, and ensure IoT devices remain secure and functional. The result? A system that prioritizes both patient safety and the efficiency of care delivery.


