NIST Mapping with Vendor Risk Scoring Models
Post Summary
In healthcare, managing vendor cybersecurity risks is critical to protecting patient data and clinical operations. Vendor risk scoring models evaluate risks by analyzing factors like likelihood, impact, and vendor criticality. Aligning these scores with NIST frameworks ensures consistency, compliance with HIPAA, and stronger defenses against breaches.
Key takeaways:
- Vendor risk scoring models assess risks using NIST's formula: Risk = Likelihood × Impact.
- NIST frameworks (CSF 2.0, SP 800-53, SP 800-161, and RMF) provide structured guidance for vendor risk management.
- Tools like Censinet RiskOps automate vendor assessments, map them to NIST standards, and streamline compliance efforts.
NIST Frameworks for Third-Party and Supply Chain Risk Management

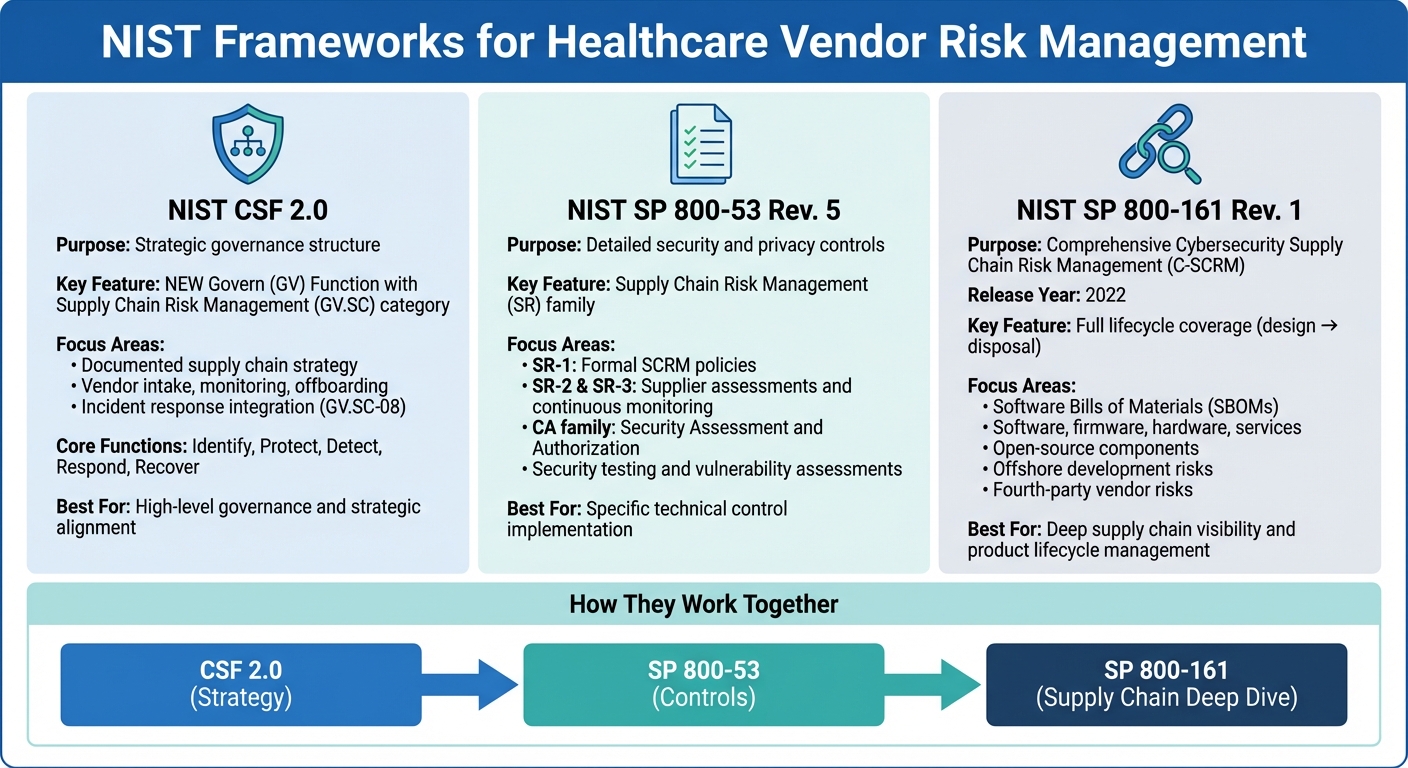
NIST Frameworks for Healthcare Vendor Risk Management: CSF 2.0, SP 800-53, and SP 800-161 Comparison
The National Institute of Standards and Technology (NIST) offers three key frameworks that work in tandem to provide healthcare organizations with detailed guidelines for managing vendor and supply chain cybersecurity. These frameworks include NIST CSF 2.0, which provides a high-level governance structure, NIST SP 800-53 Rev. 5, which lays out specific security and privacy controls, and NIST SP 800-161 Rev. 1, which expands on these controls with specialized guidance for tackling complex supply chain risks, including those from fourth-party vendors and software components. Together, they address risks throughout the vendor lifecycle - from selection to monitoring and contract termination. Below is an overview of how each framework contributes to securing supply chains and managing third-party risks.
NIST Cybersecurity Framework (CSF) 2.0
CSF 2.0 offers both strategic goals and practical guidance for managing vendor risks. A major update in this version is the introduction of the Govern (GV) Function, which includes a specific category for Supply Chain Risk Management (GV.SC). This addition highlights NIST's acknowledgment that managing third-party risks requires more than just technical controls - it demands clear governance structures.
The GV.SC category emphasizes the need for a documented supply chain strategy, covering vendor intake, ongoing monitoring, and offboarding. It also ensures vendors are integrated into incident response and recovery plans (GV.SC‑08), which is critical in healthcare, where vendor-related security breaches could directly affect patient safety.
Beyond governance, CSF 2.0’s core functions - Identify, Protect, Detect, Respond, and Recover - include specific guidance for addressing third-party risks. For instance, the Identify function helps organizations maintain an inventory of vendors with access to sensitive systems and data, while the Protect function focuses on implementing contractual security requirements. Together, these layers help align vendor risk management practices with NIST standards.
NIST SP 800-53 Rev. 5
While CSF 2.0 provides a strategic framework, NIST SP 800-53 Rev. 5 dives into detailed security and privacy controls. Its Supply Chain Risk Management (SR) family outlines specific requirements for vendor oversight. For example, SR‑1 mandates formal supply chain risk management policies, while SR‑2 and SR‑3 focus on supplier assessments, continuous monitoring, and maintaining documented risk management plans throughout the vendor relationship.
The framework also includes the Security Assessment and Authorization (CA) family, which establishes criteria for evaluating third-party systems before granting them access to organizational networks or data. This involves security testing, vulnerability assessments, and formal authorization processes. These controls are especially critical for healthcare organizations that rely on vendor-hosted cloud services or allow vendors to connect directly to clinical systems.
NIST SP 800-161 Rev. 1
Released in 2022, NIST SP 800-161 Rev. 1 serves as the primary guidance for Cybersecurity Supply Chain Risk Management (C-SCRM). It builds on SP 800-53 by linking supply chain risk management practices to both the system development lifecycle and broader enterprise risk processes. This framework addresses risks across the entire lifecycle of products and services - from design and development to acquisition, deployment, operation, and disposal.
What sets SP 800-161 Rev. 1 apart is its focus on evaluating not just a vendor’s current security measures but also how they develop and maintain their products over time. It provides thorough guidance for managing risks tied to software, firmware, hardware, and services, including challenges posed by open-source components and offshore development.
Additionally, its emphasis on Software Bills of Materials (SBOMs) has become particularly relevant for healthcare organizations. SBOMs offer transparency into the components used in clinical applications and medical devices, helping organizations identify and address vulnerabilities more effectively. This level of due diligence ensures that all aspects of the supply chain are accounted for, reducing the risk of unforeseen security issues.
Building NIST-Aligned Vendor Risk Scoring Models
Developing a vendor risk scoring model that aligns with NIST standards involves systematically linking vendor data - like questionnaire responses, security documentation, and external risk signals - to specific NIST controls. This approach creates a clear, defensible process to assess third-party access to sensitive healthcare data, ensuring every step is auditable and tied to established standards.
Mapping Scoring Inputs to NIST Controls
Start by identifying the appropriate NIST frameworks for your vendor relationships. For most healthcare organizations, this means aligning vendor assessments with NIST CSF 2.0 Categories (such as ID.AM for Asset Management or PR.AA for Access Control) and their associated SP 800-53 controls. Each piece of vendor data should map directly to these controls. For example, encryption-related questions can align with SC-8 and SC-28, while incident response queries might tie to controls like IR-1 through IR-10.
When scoring, use a consistent scale - 0 to 5 or 0 to 100 - to evaluate how well a vendor implements each control. Scores should be aggregated by category, and an overall security score should be calculated with direct traceability to NIST controls and supporting evidence. This method helps measure both inherent risk (based on the type of data vendors handle and their system connections) and residual risk (accounting for the vendor's actual security measures and maturity). These mapping techniques provide a structured way to assess how vendors could impact healthcare outcomes.
Criticality Scoring for Healthcare Vendors
Beyond security scoring, you’ll need to assess vendor criticality to understand their potential impact on patient safety, clinical operations, and protected health information (PHI). This involves evaluating three key factors:
- Whether the vendor directly affects patient safety (e.g., EHR systems or medical devices).
- The volume and sensitivity of PHI they access.
- The importance of their services in maintaining care delivery.
Vendors that handle large amounts of PHI or perform critical clinical functions will naturally receive higher criticality scores compared to those managing limited administrative data.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." – Matt Christensen, Sr. Director GRC, Intermountain Health
To refine this process, apply role-based weights to emphasize controls that are most relevant to a vendor's function. For example, clinical application vendors should be weighted more heavily on availability and patient safety measures, while billing vendors might require a stronger focus on data confidentiality and privacy. Combine the criticality score with the NIST-aligned security score using a matrix. Even a vendor with a medium security score might be classified as high risk if they are critical to clinical operations.
Setting Risk Tiers and Thresholds
By combining security and criticality scores, you can categorize vendors into clear risk tiers - typically high, medium, and low. Each tier should correspond to specific NIST-aligned requirements and organizational actions. For instance:
- Low-risk vendors: Require baseline control coverage and assessments every two to three years.
- Medium-risk vendors: Need focused attention on areas like data protection, access control, and incident notification.
- High-risk vendors: Demand comprehensive validation of 800-53 controls, annual reassessments, and continuous monitoring.
Additionally, define control-level thresholds to flag vendors with critical gaps, regardless of their overall score. For example, any vendor lacking essential controls, such as an incident response plan, backup and recovery procedures, or PHI encryption, should automatically be considered high risk. These scenarios might require immediate remediation, additional safeguards like network segmentation, or even contract amendments before granting the vendor access to your systems.
sbb-itb-535baee
Implementing NIST Mapping in Healthcare with Censinet
Censinet RiskOps takes the complexity of NIST frameworks and transforms them into practical, everyday vendor risk workflows specifically tailored for healthcare. By automating the process of mapping vendor questionnaires to NIST controls and consolidating assessments, the platform ensures seamless alignment with standards like CSF 2.0, SP 800-53 Rev. 5, and SP 800-161 Rev. 1. This approach simplifies compliance efforts while helping healthcare organizations manage vendor risks more effectively.
NIST-Aligned Risk Workflows
Censinet structures vendor risk management into customizable workflows that align with NIST's guidance from start to finish. During onboarding, vendors are automatically categorized by their inherent risk level, which is determined by factors like the amount of PHI they handle, their role in clinical operations, and their system integrations. This process ties directly to the Identify and Govern functions of NIST CSF 2.0. For instance, a hospital can configure RiskOps to flag any vendor accessing over 10,000 patient records as "Critical", triggering a full assessment based on NIST 800-53 controls.
High-risk vendors, such as cloud-based EHR systems or medical imaging platforms, undergo comprehensive assessments that focus on detailed control families like Access Control (AC), System and Communications Protection (SC), and Supply Chain Risk Management (SR). Meanwhile, medium- and low-risk vendors follow simplified workflows that concentrate on baseline controls. All assessment data, scores, and remediation updates are centralized in dashboards, providing executives, boards, and regulators with a clear view of NIST-aligned oversight. These structured workflows are further streamlined with RiskOps' advanced automation features.
Leveraging Censinet RiskOps Features

Censinet RiskOps eliminates much of the manual effort involved in NIST-aligned vendor risk management through several key capabilities. Pre-mapped NIST control libraries and questionnaires offer ready-to-use templates aligned with CSF 2.0, 800-53 Rev. 5, and 800-161 Rev. 1, tailored for common healthcare vendors like EHR systems, telehealth providers, cloud hosting platforms, and medical devices. This eliminates the need to manually translate NIST controls into assessment questions.
The platform's automated scoring engine calculates risk scores based on control families and categories, aggregating vendor responses and evidence against NIST standards. Its collaborative risk exchange feature allows healthcare organizations to share and reuse vendor assessment data across a network of over 50,000 vendors, cutting down on duplicate work. Additionally, continuous monitoring dashboards provide ongoing oversight, flagging control gaps and automatically triggering reassessments when thresholds - such as missing incident response plans or lack of PHI encryption - are breached.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health
By embedding NIST requirements into reusable workflows and content, RiskOps empowers healthcare security and compliance teams to scale their vendor risk management efforts across hundreds or even thousands of vendors - without drowning in spreadsheets or endless email chains.
Accelerating Assessments with Censinet AI
Censinet AI builds on the platform's automated scoring features to speed up third-party risk assessments while keeping human oversight intact. Vendors can complete security questionnaires in seconds with AI assistance, which also summarizes vendor evidence and documentation and identifies integration details and fourth-party risks, producing concise risk summary reports.
The platform employs a human-in-the-loop approach, where risk teams maintain control through configurable rules and review processes. This ensures automation supports, rather than replaces, critical decision-making. Advanced routing features direct key findings and high-priority AI-related risks to the appropriate stakeholders, including AI governance committees, for review and approval. With real-time data displayed on an intuitive dashboard, Censinet RiskOps serves as the central hub for managing AI-related policies, risks, and tasks. This ensures that the right teams address the right issues promptly, all while maintaining full alignment with NIST standards.
Conclusion
Integrating vendor risk scoring models with NIST frameworks is reshaping healthcare cybersecurity by creating a standardized way to assess risks. By leveraging frameworks like CSF 2.0, SP 800-53 Rev. 5, and SP 800-161 Rev. 1, healthcare organizations can move away from inconsistent evaluations and adopt reliable, auditable processes. These processes tie vendor risk directly to patient safety outcomes while addressing federal cybersecurity standards and industry-specific priorities, such as protecting PHI, securing medical devices, and ensuring supply chain stability.
Censinet RiskOps turns this framework into action by embedding NIST controls into automated, practical workflows. With a network of over 50,000 vendors and automated scoring aligned with NIST standards, it eliminates redundant assessments. Through centralized dashboards, healthcare organizations can track and report NIST-based risk metrics to executives, boards, and regulators, translating complex technical data into actionable insights that highlight how vendor management strengthens both patient safety and data protection.
The efficiency benefits are undeniable. For example, Tower Health reduced its risk assessment team from five to two full-time employees while increasing the number of assessments completed. Similarly, Baptist Health replaced cumbersome spreadsheet tracking with a collaborative, shared-risk model. These achievements are powered by Censinet RiskOps' automation tools, including Censinet AI, which can fill out vendor questionnaires in seconds, summarize supporting evidence, and escalate critical findings to the right stakeholders, such as AI governance committees.
To build on these advancements, healthcare organizations should take clear next steps: prioritize vendors based on their access to PHI and clinical impact, align assessments with NIST controls, and adopt automated workflows that combine human oversight with scalability. Censinet RiskOps provides the specialized infrastructure needed to implement this strategy, ensuring that vendor risk management aligns with cybersecurity goals while focusing on what matters most - protecting patients and maintaining uninterrupted care.
FAQs
How do vendor risk scoring models work with NIST frameworks in healthcare?
Vendor risk scoring models play a critical role in healthcare by aligning risk assessments with established standards such as the NIST Cybersecurity Framework (CSF) and NIST SP 800-53. This alignment helps organizations implement strong cybersecurity measures, maintain ongoing monitoring efforts, and meet necessary compliance standards.
With these models, healthcare organizations can better prioritize risks, simplify assessment processes, and show alignment with NIST guidelines. This not only strengthens their security measures but also protects sensitive patient data, clinical systems, and supply chain operations.
How does NIST CSF 2.0 support third-party risk management?
The NIST CSF 2.0 offers a clear framework designed to help organizations tackle third-party risks with greater efficiency. It lays out steps for identifying, evaluating, and addressing vulnerabilities linked to vendors, all while aligning with established cybersecurity standards.
By implementing NIST CSF 2.0, businesses can bolster their security defenses, minimize their exposure to potential threats, and improve adherence to industry regulations. This framework is especially beneficial in sectors like healthcare, where protecting sensitive data - like patient records - is a top priority.
How does Censinet RiskOps simplify vendor risk management in line with NIST standards?
Censinet RiskOps simplifies vendor risk management by automating the process of meeting NIST cybersecurity standards. With its AI-powered workflows, the platform keeps a constant eye on vendor risks, evaluating, monitoring, and prioritizing them in real-time. This drastically cuts down on the need for manual work.
For healthcare organizations, Censinet RiskOps offers an efficient way to handle risks tied to patient data, clinical applications, medical devices, and supply chains - all while staying aligned with NIST guidelines. This approach not only strengthens cybersecurity but also helps save time and resources.


