How Quantum Encryption Secures PHI Data
Post Summary
Quantum encryption is reshaping how healthcare protects sensitive patient data, or Protected Health Information (PHI). Current encryption methods like RSA and ECC, while secure against today’s threats, are vulnerable to quantum computing advancements. This could expose decades of archived medical records to future breaches. The solution? Quantum-safe encryption, which includes:
- Post-Quantum Cryptography (PQC): Software-based algorithms resistant to quantum attacks, compatible with existing systems.
- Quantum Key Distribution (QKD): Uses quantum mechanics to detect eavesdropping and secure critical communications.
Healthcare organizations must act now to safeguard PHI, especially long-lived data like genomic records, against "harvest now, decrypt later" threats. Mapping encryption workflows, upgrading systems to PQC, and selectively implementing QKD for high-risk connections are key steps. By prioritizing these measures, healthcare providers can ensure compliance, maintain patient trust, and protect sensitive data for decades to come.
How Quantum Encryption Works
Quantum encryption secures sensitive information through two main methods: Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC). QKD relies on the principles of quantum physics to protect key exchanges, while PQC strengthens existing systems by replacing vulnerable algorithms with new, math-based ones. While QKD requires specialized optical equipment for critical network links, PQC can be implemented via software updates, making it compatible with current hardware like servers, networks, and medical devices. Let’s break down how each method helps safeguard Protected Health Information (PHI).
Quantum Key Distribution (QKD)
QKD leverages quantum mechanics to secure key exchanges, ensuring data remains safe from interception. It uses single photons to encode bits, which are transmitted through fiber-optic cables or free-space links. This method is built on three key quantum principles:
- Superposition: Photons exist in multiple polarization states simultaneously until measured.
- Measurement disturbance: Any attempt to measure or intercept photons disrupts their quantum state, introducing detectable errors.
- No-cloning theorem: It is impossible to create exact copies of unknown quantum states, preventing undetected duplication.
A common QKD protocol, BB84, works as follows: Two parties exchange photons prepared in randomly chosen polarization states. After transmission, they publicly compare the bases used (without revealing the actual data) and discard mismatched bits. A sample of the remaining bits is checked for errors - if the error rate is too high, it indicates possible eavesdropping, and the key is discarded. Once a secure key is established, it’s used with standard symmetric encryption methods like AES-256 to protect PHI over regular networks.
QKD is best suited for high-value, fixed connections, such as those linking hospital data centers, major campuses, or regional health information exchanges. While the infrastructure and costs can be significant, its unparalleled security is ideal for safeguarding critical data.
Post-Quantum Cryptography (PQC)
PQC provides a software-based solution to counter threats from quantum computing. It replaces traditional algorithms like RSA, Diffie-Hellman, and elliptic-curve cryptography with quantum-resistant public-key schemes that can withstand both classical and quantum attacks. Unlike QKD, PQC runs on existing hardware, making it versatile for protecting data in transit (e.g., TLS, VPNs, APIs) and data at rest (e.g., in databases and backups) across healthcare systems.
The National Institute of Standards and Technology (NIST) is leading efforts to standardize PQC algorithms. In 2022, NIST selected several algorithms for quantum-safe encryption:
- CRYSTALS-Kyber for key establishment
- CRYSTALS-Dilithium, Falcon, and SPHINCS+ for digital signatures
Healthcare organizations are encouraged to adopt solutions aligned with these standards when upgrading systems like electronic health records (EHRs), telehealth platforms, medical devices, and cloud services. Many vendors also offer hybrid cryptographic modes, which combine traditional and post-quantum algorithms to ease the transition.
While QKD is ideal for securing high-value connections, PQC offers a scalable, software-based approach to protect PHI across the broader healthcare environment. Both methods play a crucial role in ensuring long-term data confidentiality, especially as quantum computing capabilities continue to advance.
Assessing Quantum Risks in PHI Workflows
Understanding quantum encryption is just the beginning. To ensure long-term protection of Protected Health Information (PHI), it's vital to assess quantum risks within PHI workflows. Start by mapping out the systems that handle PHI to pinpoint vulnerabilities. This involves documenting every system interacting with PHI, noting encryption protocols, and identifying workflows that could face significant risks in the future. A thorough assessment helps uncover which algorithms are susceptible to quantum threats and highlights datasets that adversaries might be storing now, planning to decrypt later. This foundational mapping is key to prioritizing quantum-safe upgrades.
Mapping PHI Workflows and Encryption Practices
The first step is to document every interaction with PHI - creation, storage, processing, and transmission. This includes systems like electronic health record (EHR) platforms, patient portals, telehealth services, imaging systems (e.g., PACS, RIS), lab information systems, revenue cycle tools, data warehouses, backup solutions, medical devices, and home monitoring technologies. Don’t overlook device firmware, communication protocols (e.g., Bluetooth, Wi-Fi, cellular networks), gateways, and data flows that connect to clinical systems.
Next, capture the details of each workflow, including system components, network paths (internal networks, VPNs, internet connections), encryption methods (e.g., TLS versions, VPN protocols, email gateways, database encryption), and third-party access points like cloud providers, SaaS platforms, payers, and health information exchanges. The result should be a visual data-flow map and a detailed "encryption bill of materials". These tools can be managed in governance platforms like Censinet RiskOps™ for ongoing oversight and vendor collaboration. Once workflows are mapped, the focus shifts to identifying encryption elements vulnerable to quantum computing.
Identifying Quantum-Vulnerable Encryption
For every communication channel and data storage location, document the cryptographic algorithms in use. This includes algorithms like RSA-2048, ECC P-256, Diffie-Hellman, and AES-128/256, along with key sizes, protocol versions (e.g., TLS 1.0/1.2/1.3, IPsec/IKE, SSH), and whether public-key or symmetric cryptography is used for key exchange. Additionally, record certificate authorities, certificate lifetimes, and any hardware security modules (HSMs) or trusted platform modules (TPMs) that are aligned with future post-quantum cryptography (PQC) roadmaps.
Algorithms such as RSA, ECC, and Diffie-Hellman are inherently vulnerable to quantum attacks, regardless of key length, as quantum computers running Shor's algorithm can break these encryption methods efficiently. This vulnerability extends to TLS 1.2, IPsec VPNs, SSH, S/MIME email, code signing, PKI certificates, and database encryption relying on RSA or ECC for key management. On the other hand, symmetric algorithms like AES-256 are more resistant - quantum attacks like Grover's algorithm only offer a limited speed advantage. Ensure that key sizes meet quantum-safe standards. Assign each encryption method a "Quantum vulnerability" rating (High, Moderate, Low) to aid in risk assessment and prioritization.
Evaluating Long-Term Confidentiality Requirements
The level of quantum risk PHI faces depends on how long the data needs to stay confidential. For example, routine adult encounter data might only need protection for 7–10 years to meet HIPAA and malpractice requirements. However, genomic data, pediatric records, and reproductive or behavioral health information often remain sensitive for an individual’s entire life - and sometimes even longer, affecting their descendants. Since adversaries could store encrypted data now and decrypt it later as quantum capabilities evolve, workflows handling these long-lived datasets are high-priority for quantum-safe updates.
To manage this, categorize PHI by its expected sensitivity window:
- Short (≤5–10 years): Routine encounter data
- Medium (10–20 years): Standard clinical records
- Long (20–75+ years): Genomic data, pediatric records, research repositories, biobanks, and longitudinal registries
Systems like research repositories, biobanks, genomic labs, longitudinal registries, cloud archives, and off-site backups that store long-lived data should be prioritized for migration to post-quantum encryption. Risk committees can assign specific confidentiality lifetimes to each data class, creating clear technical requirements and timelines. This ensures that systems safeguarding the most sensitive information are upgraded first, minimizing long-term vulnerabilities.
Implementing Quantum-Safe Encryption in Healthcare
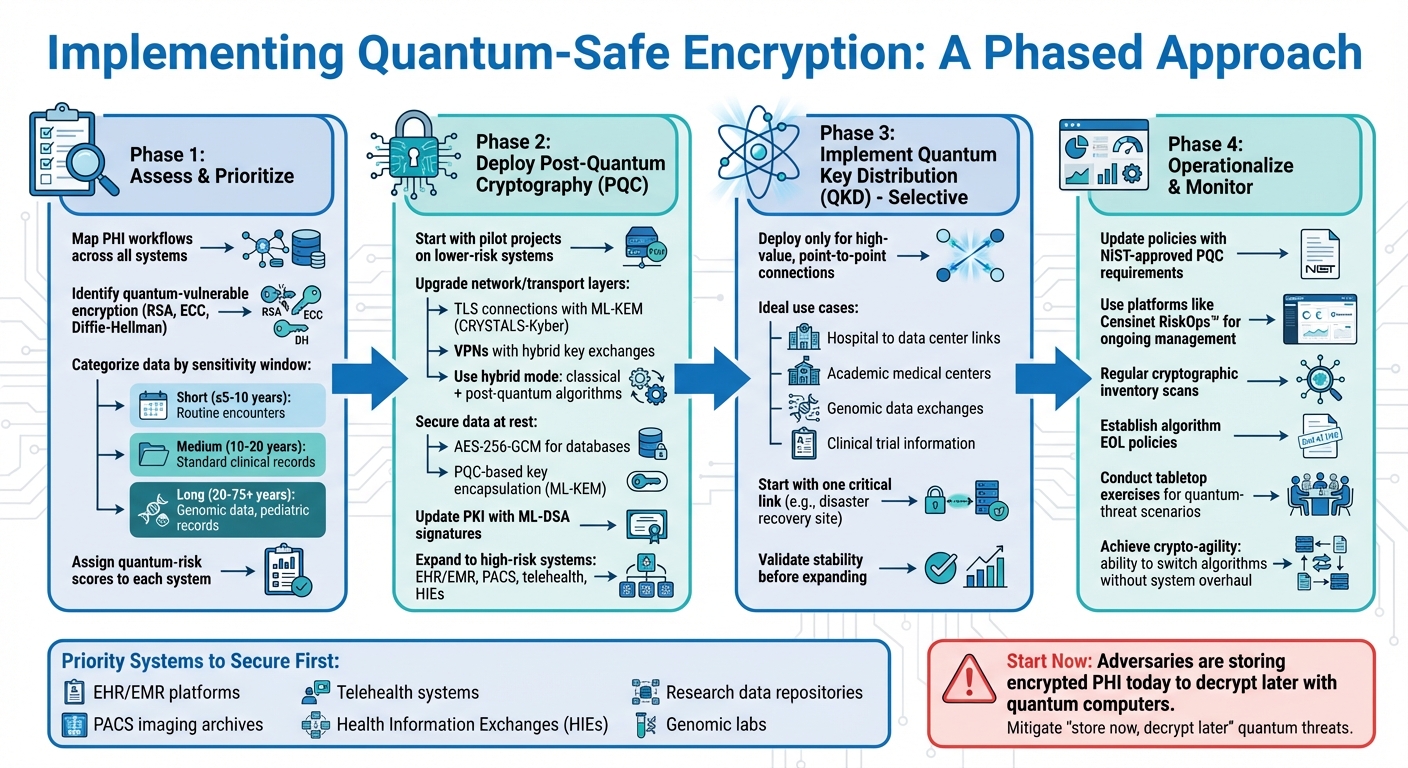
Quantum-Safe Encryption Implementation Roadmap for Healthcare Organizations
Rolling out quantum-safe encryption in healthcare calls for a phased and risk-focused strategy. Start by securing the most critical systems, gradually integrating post-quantum cryptography (PQC) into your current setup. For high-value connections, consider Quantum Key Distribution (QKD) to add an extra layer of protection. This method ensures sensitive patient health information (PHI) remains secure from both current and future quantum threats, all while keeping operations running smoothly. Regular risk assessments will help fine-tune safeguards to address emerging challenges.
Prioritizing High-Risk PHI Systems
To begin, focus on the systems that handle the most sensitive and exposed PHI. These include EHR/EMR platforms, imaging archives (PACS), telehealth systems, health information exchanges (HIEs), and research data repositories. These systems often store highly sensitive information like full medical histories, genomic data, and behavioral health records, which may need confidentiality for decades.
Start by mapping out PHI workflows and tagging systems based on PHI sensitivity, exposure risks, regulatory implications, and long-term confidentiality needs. Build an inventory of applications, identify those using encryption methods like RSA or ECC-based TLS, and assign quantum-risk scores to each system. This creates a clear roadmap for upgrading encryption, beginning with the highest-risk systems. From there, implement PQC and QKD solutions tailored to each system’s requirements.
Adopting Post-Quantum Cryptography
The integration of PQC should first target the network and transport layers to protect PHI in motion. Begin with pilot projects using PQC-enabled TLS connections between internal systems and external partners like vendor APIs and patient portals. A hybrid approach - combining classical algorithms with post-quantum methods like ML-KEM (based on CRYSTALS-Kyber) - provides an extra layer of security in case one algorithm fails. Similarly, upgrade VPNs for both site-to-site and remote access to include PQC or hybrid key exchanges, ensuring secure data flows for telehealth and inter-facility communication.
For data at rest, rely on strong encryption like AES-256-GCM for databases and storage systems containing PHI. While symmetric encryption is generally more resistant to quantum threats, robust key management is still essential. Use PQC-based key encapsulation (ML-KEM) to secure key exchanges for storage and backups. Additionally, update Public Key Infrastructure (PKI) systems to support PQC, incorporating ML-DSA signatures and hybrid certificate chains during the transition phase.
Start with lower-risk PHI systems to pilot PQC, then expand to critical systems. Tools like Censinet RiskOps™ can help identify where vulnerable algorithms like RSA or ECC are in use, prioritize their replacement based on PHI importance, and work with vendors to ensure their systems align with PQC standards. This method not only reduces risk but also demonstrates compliance to regulators and stakeholders while optimizing spending.
Using Quantum Key Distribution in Healthcare
QKD is ideal for high-value, point-to-point connections that demand long-term confidentiality. It’s particularly useful for dark-fiber or metro-area links between large hospitals, academic medical centers, and off-site data centers, especially when exchanging genomic data or clinical trial information. QKD can work alongside existing encryption methods, such as AES-256-based MACsec or IPsec tunnels, to further enhance security.
However, QKD comes with limitations - distance restrictions, specialized equipment needs, high costs, and operational complexity. For most healthcare organizations, PQC will remain the primary tool for securing TLS, VPNs, and key management. QKD should be reserved for a small number of critical, high-bandwidth connections. A practical starting point could be deploying QKD for a single essential link, such as between a hospital and its disaster recovery site. After validating stability and refining response processes, expand selectively based on performance and risk reduction outcomes.
sbb-itb-535baee
Operationalizing Quantum-Safe PHI Protection
After laying the groundwork with initial implementations, the next step is weaving quantum-safe measures seamlessly into daily operations. To effectively protect sensitive data like PHI (Protected Health Information) from quantum threats, organizations must treat these risks as an integral part of their governance and risk management processes. This means updating policies to enforce the use of quantum-resistant cryptography, incorporating quantum risks into third-party assessments, maintaining an up-to-date inventory of cryptographic assets, and keeping a close eye on evolving standards from NIST and the NSA. The ultimate aim? Achieving crypto-agility - essentially, the ability to switch algorithms and cryptographic keys without overhauling entire systems - so your organization stays prepared as quantum risks evolve. Start by revising foundational policies to reflect these quantum-safe priorities.
Updating Policies and Standards for Quantum-Safe Encryption
The first step in embedding quantum-safe practices is revising your organization's core governance documents to address quantum risks directly. Key policies - such as the Information Security Policy, Cryptographic Standards, Data Protection & Privacy Policy (aligned with HIPAA/HITECH), Vendor Risk Management Policy, Medical Device Security Policy, and Business Continuity/Disaster Recovery Plans - should all include clear quantum-safe requirements.
For example, policy updates should mandate the use of NIST-approved post-quantum cryptography (PQC) algorithms for PHI, whether it’s in transit or at rest. Specify timelines for transitioning to these algorithms and explicitly prohibit deploying quantum-vulnerable schemes like RSA, ECC, and Diffie-Hellman for long-term PHI protection unless robust compensating controls and migration strategies are in place.
Clearly define governance roles - such as those of the CISO, privacy officer, and clinical engineering teams - responsible for managing the transition to quantum-safe cryptography. Regular crypto-agility testing should also be required to confirm that algorithms can be updated without causing disruptions. Set deadlines for implementing hybrid classical and PQC solutions, and schedule annual reviews to track progress and refine strategies.
Using Censinet RiskOps™ for Risk Management
Censinet RiskOps™ offers a centralized solution for managing quantum-related risks across third-party vendors and internal PHI systems. With this platform, healthcare organizations can customize questionnaires to assess vendors’ current cryptographic methods, PQC transition plans, and quantum-safe key management capabilities. RiskOps then scores and tracks these risks across the vendor portfolio, providing a clear picture of where quantum vulnerabilities may exist.
Within enterprise workflows, RiskOps helps maintain a detailed inventory of PHI systems, their cryptographic posture, and planned upgrades. Designed specifically for healthcare, the platform aligns quantum-safe controls with HIPAA, HITECH, CMS, and emerging NIST PQC guidelines. It also generates documentation and evidence for audits, board reports, and regulatory reviews.
The platform’s collaborative tools make it easier for teams - spanning security, privacy, procurement, and clinical engineering - to coordinate as they implement quantum-safe controls across clinical applications, medical devices, and cloud services. As Terry Grogan, CISO at Tower Health, remarked:
Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required. [1]
This efficiency is invaluable, especially when dealing with complex transitions like adopting quantum-safe encryption. Once quantum risks are addressed, continuous monitoring ensures these protections remain effective.
Monitoring and Adapting to Quantum Threats
Quantum-safe PHI protection isn’t a one-and-done task - it requires ongoing monitoring and cryptographic lifecycle management. Regularly scan your cryptographic inventory to identify legacy algorithms and weak configurations. Establish clear end-of-life (EOL) policies for outdated algorithms and key sizes, with timelines for phasing out vulnerable schemes and fallback modes.
Stay updated on the latest guidance from NIST, HHS, and the NSA regarding PQC and cybersecurity in healthcare. Reflect these updates in your internal standards and ensure any changes are tested in non-production environments before implementation. Track cryptographic incidents or near-misses to continuously refine your controls.
As NIST finalizes PQC algorithms and new attack methods or optimizations emerge, your organization must be ready to update cryptographic libraries and configurations across systems like VPNs, EHR interfaces, and medical device gateways - without requiring major system overhauls. This level of adaptability demonstrates true crypto-agility.
To prepare for potential disruptions, include quantum-threat scenarios in tabletop exercises and business continuity plans. Pay special attention to ensuring PHI remains secure during and after disruptive events. Regularly review your cryptographic standards to confirm they align with the latest threat landscape, keeping your defenses sharp and up to date.
Conclusion
As we’ve explored the challenges posed by quantum risks and the strategies to address them, one thing is clear: the days of relying solely on current public-key algorithms are numbered. The looming threat of quantum-enabled attacks - especially on stored encrypted PHI - demands immediate attention. Sensitive data like oncology records, genomic information, psychiatric notes, and pediatric files, which require confidentiality for decades, are particularly vulnerable.
The good news? Transitioning to quantum-safe encryption is entirely achievable. Post-quantum cryptography (PQC) can be integrated into existing systems like TLS and VPNs with minimal disruption, much like standard cryptographic updates [2]. By thoroughly mapping PHI workflows and adopting quantum-safe encryption, organizations can safeguard their data for the long haul. A phased approach works best: start with high-risk areas such as EHR repositories, health information exchanges, telehealth platforms, connected medical devices, and long-term image archives, then move to lower-risk internal systems. Tools like Censinet RiskOps™ offer a structured way to inventory cryptographic assets and streamline migration efforts.
FAQs
How does quantum encryption protect PHI more effectively than traditional methods?
Quantum encryption takes data security to a whole new level by leveraging the fascinating principles of quantum mechanics, including superposition and entanglement. These principles create an environment where intercepting or decoding data without being noticed becomes nearly impossible.
Here’s how it works: Unlike traditional encryption methods, quantum encryption ensures that any attempt to tap into the data alters its quantum state. This automatic change serves as an immediate alert to the intended parties, signaling a potential breach. This built-in safeguard makes quantum encryption an incredibly powerful tool against advanced cyber threats, offering a robust way to protect sensitive healthcare information.
How can healthcare organizations adopt quantum-safe encryption?
Healthcare organizations looking to safeguard sensitive data against potential quantum computing threats should start by assessing their current cryptographic systems. This evaluation helps pinpoint vulnerabilities that could be exploited as quantum technology advances. A key step in this process is moving to quantum-resistant algorithms, which are designed to secure critical information like Protected Health Information (PHI).
For a smoother transition, partnering with cybersecurity professionals experienced in healthcare can be invaluable. These experts can assist in aligning with industry regulations while addressing new and evolving risks. Additionally, staying updated on the latest developments in the field and testing solutions through small-scale pilot programs can make the shift to quantum-safe encryption more manageable and effective.
What challenges do organizations face when adopting quantum-safe encryption?
Transitioning to quantum-safe encryption isn't without its hurdles. For starters, organizations must adopt new cryptographic algorithms designed to withstand quantum-based attacks. This often demands extensive research and development, which can be both time-consuming and resource-intensive. On top of that, integrating these advanced algorithms into existing systems is no small feat - it can be technically challenging and may even affect system performance.
Updating older infrastructure adds another layer of complexity. Legacy systems, often deeply embedded in operations, can be expensive and time-consuming to overhaul. Compounding the issue is the absence of standardized protocols for quantum-safe encryption. Without these, ensuring that systems remain consistent and compatible becomes a significant challenge.
To keep up with evolving threats, organizations must also prioritize cryptographic agility. This means having the flexibility to adapt encryption methods quickly as new technologies and risks emerge, ensuring long-term security in a rapidly changing landscape.


