Real-Time IoT Monitoring: Key Protocols Explained
Post Summary
Hospitals today manage thousands of connected devices, from infusion pumps to vital-sign monitors. These devices improve patient care but also introduce cybersecurity risks. For example, in 2025, over 1 million medical IoT devices were found exposed online, with vulnerabilities averaging 6.2 per device. Real-time monitoring is critical to detect anomalies, secure data, and ensure device functionality.
Here’s how key protocols play a role:
- MQTT: Lightweight, efficient for continuous data flow in clinical settings.
- CoAP/6LoWPAN: Ideal for low-power sensors transmitting vital signs.
- AMQP: Reliable messaging for integrating IoT platforms with hospital systems.
- HTTP/REST, WebSocket, gRPC: Used for data transfer and streaming to central systems.
- Security Layers: TLS/DTLS encryption, mutual authentication, and AI-based intrusion detection ensure compliance with HIPAA and FDA standards.
Real-time IoT monitoring is not just about data flow - it's about securing patient safety, meeting regulatory requirements, and integrating monitoring data into broader risk management systems.
Core Protocols for Real-Time IoT Monitoring in Healthcare
Healthcare systems rely on a mix of communication protocols to manage data from thousands of devices, ensuring telemetry, alerts, and security events reach central monitoring systems efficiently. Lightweight protocols like CoAP and 6LoWPAN handle communication for constrained sensors, while gateways translate this data into MQTT, AMQP, HTTP/REST, WebSocket, or gRPC formats for integration with clinical and security platforms. Each protocol is chosen based on its ability to balance latency, bandwidth, reliability, and device capabilities - key factors for both operational efficiency and cybersecurity. Let’s break down how these protocols work together to create a real-time monitoring framework.
Message Queuing and Publish-Subscribe Protocols
MQTT (Message Queuing Telemetry Transport) is a cornerstone for continuous data flow from devices like patient monitors, infusion pumps, and smart beds. Its publish–subscribe model uses persistent TCP connections with minimal overhead, allowing adjustable quality-of-service (QoS) levels to match clinical needs. For example, critical alarms might require guaranteed delivery (exactly-once QoS), while routine vitals could use a faster, best-effort approach. Topic hierarchies (e.g., hospital/floor3/room305/monitor/heartrate) simplify data routing and access control, while retained messages ensure new subscribers instantly receive the latest device state.
MQTT-SN, a variant of MQTT tailored for sensor networks, operates over UDP and supports non-TCP transports like 6LoWPAN. This reduces overhead further, making it ideal for low-power, battery-operated devices. Gateways typically handle encryption and convert MQTT-SN messages into standard MQTT for broader system compatibility. Meanwhile, AMQP provides reliable, transactional messaging with advanced routing, ensuring seamless integration between IoT platforms, electronic health records (EHRs), and analytics tools.
Security is integral to these protocols. Mutual authentication via client certificates or token-based methods is standard, with traffic encrypted using TLS (or DTLS for MQTT-SN). Brokers should log connection attempts, topic subscriptions, and publishing activities in real time, feeding this data into SIEM systems or IoT security platforms. Enforcing access control on topics and queues limits devices to authorized communication channels, reducing the impact of potential breaches. Additionally, monitoring for unusual topics, unexpected devices, or abnormal message rates can help detect early signs of cyber threats, such as lateral movement or command-and-control activity.
Protocols for Constrained Devices
CoAP (Constrained Application Protocol) is a lightweight, REST-like protocol designed for devices with limited resources. Operating over UDP, it supports simple request/response and observe patterns with minimal overhead. It’s particularly effective for medical sensors that periodically transmit vitals or device status. Paired with 6LoWPAN, which enables IPv6 communication over low-power networks, these protocols extend battery life for wearable or implanted devices while maintaining real-time telemetry for clinical and security purposes.
However, because CoAP uses UDP, additional measures are needed to ensure message reliability and proper sequencing when necessary. Security is typically handled via DTLS, though this can strain very constrained devices. Techniques like session resumption and pre-shared keys help reduce this burden. Since these devices often lack the resources for full-featured security, threat detection relies on network behavior analysis at gateways or dedicated security platforms. These systems monitor for anomalies like unexpected destinations, unusual message frequencies, or malformed packets. Strong network segmentation and continuous monitoring further mitigate risks associated with limited on-device security.
Transport and Web Communication Protocols
Transport protocols act as a bridge, connecting device-level data to web-based applications and centralized monitoring systems. HTTP/REST remains a popular option due to its simplicity and compatibility with web services and clinical applications. However, its stateless design and header overhead can make it less suitable for high-frequency telemetry. WebSocket, on the other hand, provides a long-lived, full-duplex TCP connection, enabling continuous streaming of data like vitals, alerts, or security events without the need to repeatedly establish connections. For scenarios requiring high throughput and low latency, gRPC offers an excellent alternative. Built on HTTP/2 and using binary Protobuf encoding, gRPC supports efficient remote procedure calls and streaming, making it ideal for real-time processing.
To ensure secure communication, all three protocols must enforce strict authentication, implement origin checks, and use TLS encryption to comply with HIPAA requirements for protecting health information. Monitoring metrics such as connection attempts, authentication failures, session durations, and unusual data patterns can reveal potential security issues. For instance, if a bedside monitor suddenly sends data to an unexpected endpoint, it could indicate a misconfiguration or a security breach. Centralized monitoring tools that incorporate machine learning and behavioral baselining can help prioritize genuine threats, reducing alert fatigue for busy healthcare security teams.
Security Protocols for Real-Time Threat Detection
Detecting threats in real time within healthcare IoT networks requires robust, multi-layered security protocols built on the principles of Zero Trust. This means every device is treated as untrusted until proven otherwise, with continuous verification of its identity and behavior [8][10]. These protocols, which leverage established communication standards, are designed to quickly identify and neutralize potential risks. By default, every connected medical device must undergo ongoing authentication and authorization.
Secure Communication Channels
To ensure data remains protected, healthcare IoT systems rely on Transport Layer Security (TLS) for TCP connections and Datagram Transport Layer Security (DTLS) for UDP. TLS is commonly used for securing communications between gateways and cloud services, as well as backend systems like electronic health records (EHRs). Meanwhile, DTLS is tailored for real-time sensor data from devices with limited resources, often using lightweight protocols like CoAP over UDP.
Mutual authentication plays a key role here, preventing unauthorized access to the network. For large-scale deployments of medical devices, automated processes for provisioning, certificate rotation, and revocation are critical. These measures ensure strong security without overwhelming IT teams with manual tasks.
Intrusion Detection and Adaptive Security Frameworks
AI-powered Intrusion Detection Systems (IDS) are vital for spotting unusual device behavior. These systems learn the typical activity patterns of devices and flag anomalies, enabling them to detect most IoT-related attacks [10]. Another important measure is network segmentation, which involves isolating medical devices on dedicated VLANs. This limits the scope of potential breaches and allows for passive monitoring at key network points, making it easier to detect irregular traffic patterns early [10].
Adaptive security frameworks go a step further by combining threat intelligence, AI-driven analytics, and automated updates. Unlike static, signature-based defenses, these frameworks evolve dynamically to counter emerging threats. Fine-tuning IDS models to align with specific device behaviors minimizes false positives while ensuring real threats are addressed quickly. Detailed audit trails further enhance these defenses, enabling continuous improvement over time.
Explainability and Auditability in Security Protocols
Clear and tamper-proof logging systems are essential for compliance and forensic investigations. Healthcare organizations should implement time-synchronized logs across IoT gateways, platforms, and clinical applications. This allows for accurate reconstructions of events during incident investigations. Standardized log formats make it easier to correlate events across different systems and integrate with tools like Security Information and Event Management (SIEM) platforms.
Emerging technologies, such as hash-chained or blockchain-backed logs, add an extra layer of tamper resistance while meeting HIPAA audit requirements [10]. When an AI-driven IDS flags a potential threat, it's crucial to have explainability mechanisms in place. These mechanisms should clearly document the behavioral deviations or policy violations that triggered the alert. This transparency helps build trust in automated systems and supports a thorough and effective incident response process.
Comparing Real-Time IoT Monitoring Protocols
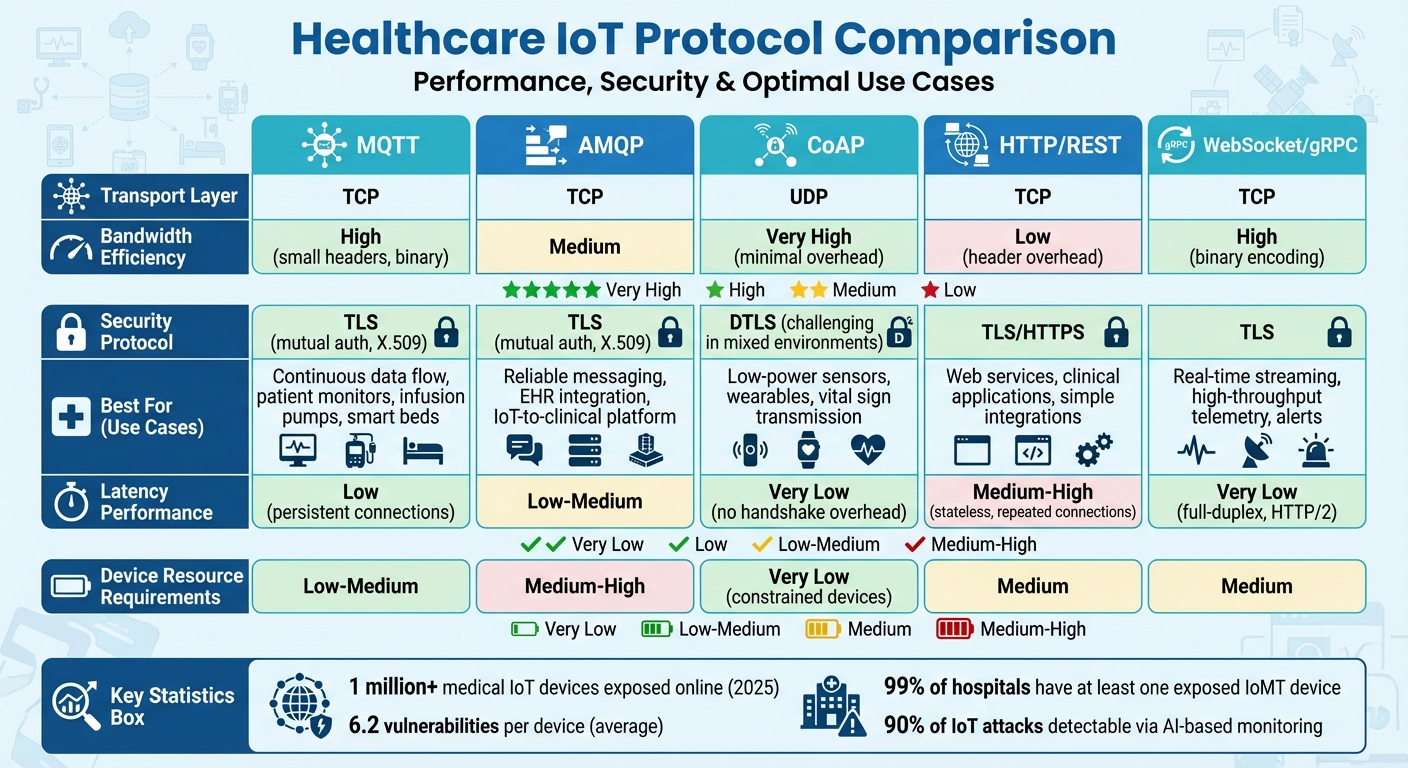
Healthcare IoT Protocol Comparison: Performance, Security, and Use Cases
Healthcare organizations face the challenge of selecting protocols that strike the right balance between efficiency, security, and reliability. MQTT and CoAP stand out for their bandwidth efficiency, thanks to their smaller headers and binary framing compared to HTTP [5]. This makes them especially suitable for wearables and bedside sensors that transmit vital signs every 1–5 seconds. Understanding these protocol differences is crucial when evaluating their performance, security measures, and limitations.
Performance in Low-Latency Environments
In hospital settings with high-speed networks and numerous devices running simultaneously, the choice of protocol can significantly impact clinical workflows [2][3]. MQTT and AMQP perform exceptionally well in publish-subscribe setups, where multiple systems need access to the same streams of vital-sign data. Unlike HTTP polling, these protocols eliminate redundant transmissions, which is critical for ICU monitors, infusion pumps, and operating room equipment. Their lightweight design ensures low latency and reliable jitter control - key factors for patient safety.
MQTT’s ability to maintain persistent sessions is ideal for managing thousands of devices across hospital networks. Meanwhile, CoAP, operating over UDP, further minimizes handshake overhead, though it introduces added complexity in ensuring reliability [5]. To ensure optimal performance, hospitals should benchmark end-to-end latency under peak device loads, simulating real-world conditions [2][3].
Security Features and Observability
Speed alone isn’t enough - security and observability are equally important. TLS over TCP secures protocols like MQTT, AMQP, HTTP/1.1, and HTTP/2, offering encryption, server authentication using X.509 certificates, and message integrity [5][7]. CoAP, on the other hand, relies on DTLS for security. However, deploying DTLS in mixed-vendor environments can be challenging, particularly when managing keys and certificates on resource-constrained devices [5].
Healthcare organizations align protocol security with HIPAA and FDA requirements by enforcing strong cipher suites and certificate-based mutual authentication, often integrated with enterprise IAM and PKI systems [5][7]. At the integration level, FHIR over HTTPS has become the go-to standard for transferring clinical data between IoT platforms, EHRs, and analytics tools. This approach leverages mature security frameworks and observability tools, ensuring compliance and seamless data exchange [4][7].
Limitations and Research Gaps
Despite advancements, vulnerabilities in IoMT devices remain a pressing issue. A 2025 security assessment revealed alarming statistics: 6.2 vulnerabilities per device on average and 99% of hospitals with at least one exposed IoMT device on their networks [9]. Protocol-level security measures alone are insufficient without robust identity management, network segmentation, and continuous monitoring.
Legacy devices, which often lack support for modern security features, create significant blind spots in hospital monitoring systems. Additionally, there’s a growing need to integrate protocol-level monitoring data into healthcare cyber risk management workflows. While AI-based monitoring can identify up to 90% of IoT attacks by analyzing normal device behavior [10], turning these detections into actionable insights for security teams remains a work in progress. This area continues to demand research, particularly in improving explainability and auditing for healthcare cybersecurity.
sbb-itb-535baee
How This Affects Healthcare Cyber Risk Management
Real-Time Monitoring and Risk Posture
Real-time telemetry is revolutionizing cyber risk management in healthcare by offering immediate insights into device inventories, vulnerabilities, and unusual activity. This capability significantly cuts down detection and response times, which are crucial for maintaining resilience [2][3]. Metrics like mean time to detect (MTTD) and mean time to respond (MTTR) benefit directly, helping organizations respond more effectively to threats.
Hospitals are leveraging advanced monitoring systems to focus on devices based on their role in handling PHI, their importance to patient care, and their exposure to risks [2][5]. Research and vendor reports consistently show that facilities with well-established, continuous monitoring experience fewer ransomware incidents and recover faster when disruptions occur. This directly enhances patient safety by minimizing downtime for critical systems [2][3].
Monitoring at the protocol level also aligns with HIPAA Security Rule requirements, such as ongoing risk analysis, audit controls, and the safeguarding of ePHI. These systems generate detailed logs tracking device activity and PHI data flows, ensuring compliance [5][7]. For FDA-regulated medical devices, continuous telemetry provides documented evidence of vulnerability management, patching, and incident responses, adhering to both premarket and postmarket cybersecurity guidelines [7]. Monitoring platforms can also produce automated reports for audits and assessments, linking identified issues to regulatory controls. This simplifies preparations for OCR investigations, accreditation reviews, and third-party risk evaluations, creating a clearer path for integrating monitoring data into centralized risk management systems [2][7].
Integrating Monitoring Data into Risk Platforms
The true power of IoT monitoring is unlocked when its data feeds into centralized platforms that can analyze and act on the information. Censinet RiskOps™ is an example of such a system, specifically designed to lower cybersecurity risks in healthcare. This cloud-based platform facilitates secure sharing of risk data across a network of healthcare providers and over 50,000 vendors and products [1].
By combining IoT monitoring data with vendor assessments and control maturity, platforms like Censinet RiskOps™ generate dynamic risk scores. These scores guide security teams in prioritizing remediation efforts based on the criticality of devices, their vulnerabilities, and their clinical importance. This approach moves beyond static assessments to address the most urgent threats to patient safety and data security [2].
Terry Grogan, CISO at Tower Health, highlighted the platform's efficiency: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
The platform also enables organizations to benchmark their cybersecurity efforts against peers, helping them improve their IoT-related risk management. This collaborative approach is especially valuable for healthcare organizations that often struggle with incomplete device inventories or limited cybersecurity expertise. By tapping into a shared risk network, security teams gain access to collective insights on device vulnerabilities, vendor security practices, and effective mitigation strategies [2][3].
Future Trends in Healthcare IoT Security
As risk data integration grows, new trends are shaping the future of healthcare IoT security. One significant development is the increasing collaboration between clinical engineering and cybersecurity teams. By sharing telemetry and configuration data, these groups are improving how IoMT assets are triaged and secured during incidents [2][6][7]. Additionally, AI-driven solutions are playing a larger role, analyzing real-time data to identify vulnerabilities, detect intrusions, and enhance incident response for medical devices and other connected assets [1].
Regulatory requirements, including those from the FDA and HIPAA/HITECH, now mandate real-time monitoring, logging, and rapid updates for networked medical devices [5][7]. As AI and machine learning tools advance, there's a growing focus on explainability and audit trails - ensuring that alerts and deviations are well-documented for compliance, forensic investigations, and maintaining clinical safety [2][4][5].
Looking ahead, the adoption of zero-trust architectures, lightweight encryption for resource-constrained devices, and protocol-aware security controls is expected to define healthcare IoT security over the next three to five years. Organizations that incorporate these advancements into their risk management strategies will be better equipped to protect patient safety while ensuring the operational efficiency modern healthcare demands. These emerging capabilities underscore the importance of real-time monitoring as a cornerstone of cyber resilience, safeguarding clinical operations in an increasingly connected world.
Conclusion
In U.S. healthcare, real-time IoT monitoring protocols have become essential for ensuring both patient safety and cybersecurity. Whether using MQTT for lightweight data transmission, AMQP for reliable message queuing, or HTTP/2 for streaming, the choice of protocol has a direct impact on how timely and dependable the data is for clinicians, as well as how effectively security teams can identify and respond to threats. As remote monitoring becomes more prevalent, the stakes for managing these risks have grown exponentially.
To protect sensitive patient information and meet regulatory standards, security must be woven into every layer of IoT systems. This includes encryption, authentication, and certificate management - all critical for safeguarding Protected Health Information (PHI) and ensuring compliance with legal frameworks [5][7]. Real-time monitoring also plays a key role in generating audit trails and alerting teams to anomalies, enabling faster responses to potential incidents.
No single protocol works for every situation. Lightweight options are ideal for devices with limited resources but may require additional infrastructure, while more robust protocols offer advanced features at a higher resource cost. Challenges remain, such as optimizing quality of service for critical telemetry in hospital settings and creating explainable, protocol-aware intrusion detection systems tailored to medical workflows [2][5]. Addressing these complexities requires careful, collaborative planning across departments.
Healthcare leaders - including CIOs, CISOs, and clinical engineering teams - must approach IoT protocol decisions as a shared responsibility that balances security and operational needs. High-priority use cases, like ICU monitoring, infusion therapy, and imaging, are excellent starting points, as real-time data in these areas directly improves patient safety and incident response. Equally important is planning for the long-term management of IoT systems, including updates, certificate renewals, and device decommissioning, to avoid being locked into outdated and insecure technologies [7].
Looking ahead, advancements such as Zero Trust architectures, lightweight encryption for constrained devices, and AI-driven anomaly detection are set to redefine healthcare IoT security [8][9][10]. Organizations that integrate monitoring data into centralized risk platforms - enabling dynamic risk scoring, vendor assessments, and peer comparisons - will be better equipped to safeguard patients while maintaining operational efficiency. Tools like Censinet RiskOps™ highlight how monitoring data can be transformed into actionable insights, aligning with the risk management principles outlined earlier.
Ultimately, real-time monitoring protocols serve as the backbone that connects device security, clinical operations, and regulatory compliance into a cohesive and effective defense strategy.
FAQs
What are the key differences between MQTT and CoAP for real-time IoT data in healthcare?
When it comes to managing real-time IoT data in healthcare, MQTT and CoAP each bring unique strengths to the table, depending on the specific needs of the application.
MQTT operates as a lightweight, publish-subscribe protocol. Its design thrives in environments with low bandwidth and high latency, ensuring quick and dependable data transfer. This makes it a great fit for use cases where real-time responsiveness is critical, such as tracking vital patient data in intensive care units or large-scale monitoring systems.
CoAP, in contrast, follows a RESTful approach and is specifically designed for constrained devices. It supports features like asynchronous communication and multicast, which are perfect for low-power devices. Think of applications like wearable health trackers or compact medical sensors operating in resource-limited settings - this is where CoAP shines.
In summary, while MQTT is ideal for large-scale, real-time healthcare applications, CoAP is better suited for energy-efficient setups with constrained devices. Each has its place in advancing IoT-driven healthcare solutions.
What are the key security practices for safeguarding medical IoT devices?
To safeguard medical IoT devices, adopting effective security measures is a must. Start with strong access controls, which ensure that only authorized individuals can interact with the devices. Combine this with encryption to protect sensitive data both during transmission and while stored. Regularly updating firmware is another critical step - it helps fix vulnerabilities and keeps devices secure.
Another key strategy is network segmentation. By isolating IoT devices from other systems, you can minimize the chances of an attack spreading across the network. On top of that, continuous monitoring and active vulnerability management are essential. These practices help identify potential threats early, protecting both patient safety and the confidentiality of sensitive information.
How does real-time IoT monitoring enhance cybersecurity in healthcare?
Real-time IoT monitoring plays a crucial role in bolstering healthcare cybersecurity. By keeping a constant watch on device and network activity, it enables the swift identification and response to potential threats. This approach helps close security gaps, ensures adherence to security regulations, and shields sensitive patient information from breaches.
In addition, real-time monitoring simplifies risk assessments and supports proactive security strategies. This not only helps healthcare organizations protect their clinical operations but also reinforces trust in their systems.


