Top Features of Customizable Vulnerability Tools for Healthcare
Post Summary
Healthcare organizations face unique cybersecurity challenges, like protecting electronic protected health information (ePHI) and securing medical devices with outdated systems. Customizable vulnerability tools are essential for identifying, prioritizing, and addressing risks in these environments. Here's what you need to know:
- Key Features: Tools should offer tailored scanning, risk prioritization considering clinical impact, and integration with existing systems (e.g., ITSM tools like ServiceNow).
- Regulatory Support: Effective tools simplify compliance with HIPAA, HITECH, and state laws by generating audit-ready reports and maintaining risk documentation.
- Specialized Tools: Platforms like Censinet RiskOps™ focus on healthcare-specific risks, while others like Armis address IoMT and medical device security.
When choosing a tool, prioritize solutions that align with clinical workflows, regulatory needs, and patient safety.
Quick Comparison:
| Tool | Focus | Strengths |
|---|---|---|
| Censinet RiskOps™ | Vendor & enterprise risks | Tailored for healthcare, integrates clinical workflows, supports compliance. |
| Tenable.io | IT infrastructure | Continuous scanning, strong integrations, broad asset coverage. |
| Qualys VMDR | IT infrastructure | Cloud-based, combines discovery, assessment, and remediation. |
| Rapid7 InsightVM | Risk-based prioritization | Real-time clinical context, integrates with ITSM tools. |
| Nessus Professional | Point-in-time scanning | Flexible scanning, strong for IT systems, less suited for IoMT. |
| Kenna Security | Risk-focused management | Prioritizes exploitable vulnerabilities, integrates with scanners. |
| Armis | IoMT & medical devices | Focused on patient safety, secures connected medical devices. |
Selecting the right tool often requires combining solutions to address both IT and clinical vulnerabilities effectively.
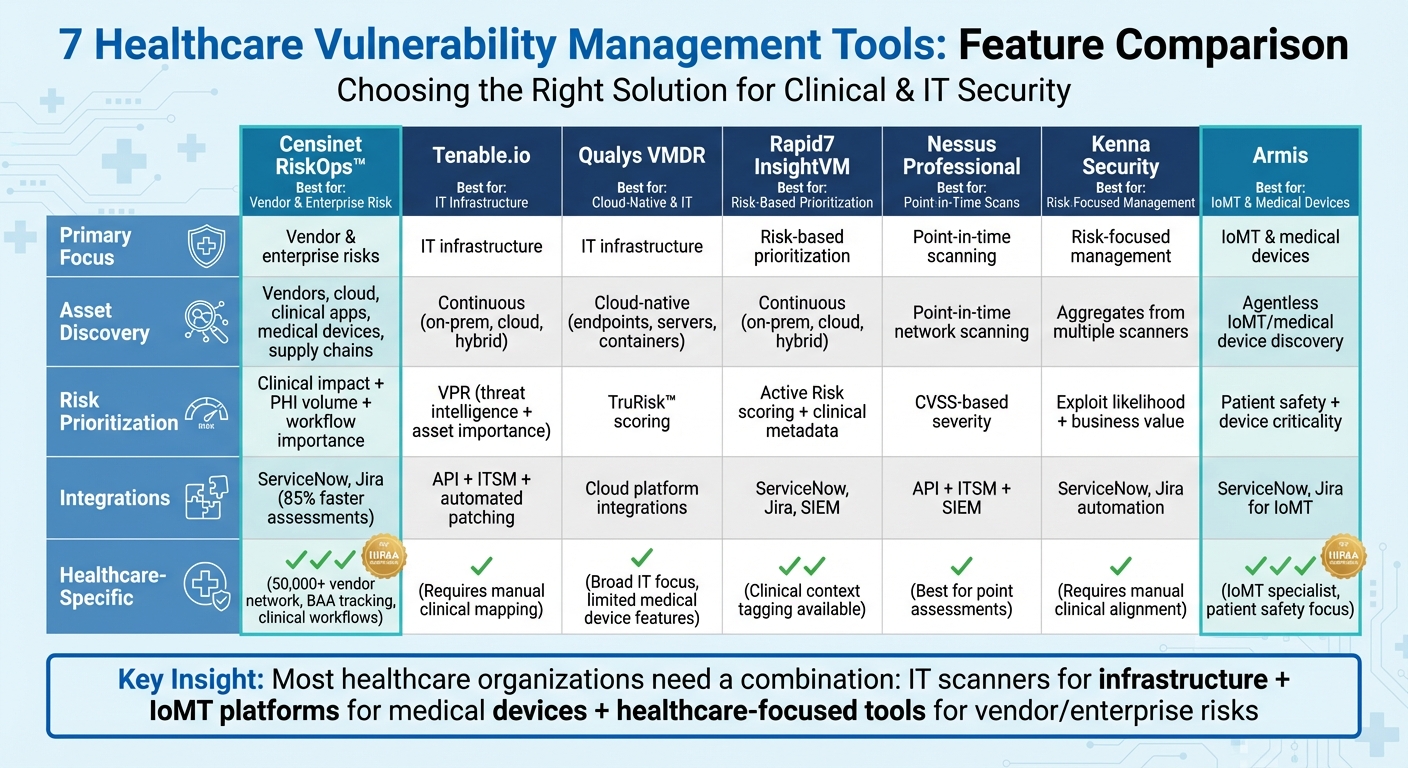
Healthcare Vulnerability Management Tools Comparison Chart
1. Censinet RiskOps™

Censinet RiskOps™ takes a broader approach to risk management by focusing on organizational, vendor, and enterprise risks rather than just technical patching. Designed specifically for healthcare, this platform tackles cyber risks across patient data, PHI, clinical applications, medical devices, and supply chains. It connects healthcare delivery organizations with a network of over 50,000 vendors and products through a centralized risk exchange.
Tailored discovery and scanning for healthcare
RiskOps™ goes beyond generic network scans by identifying and cataloging third-party products, services, and internal assets, linking them to clinical and data workflows. It pulls data from existing systems, tying risk assessments to specific clinical use cases. For example, when onboarding a new vendor, the platform automatically connects technical and security data to relevant clinical workflows, ensuring visibility into areas that traditional scans might miss. This detailed asset mapping helps healthcare organizations make better risk-based decisions.
Prioritizing risks with clinical context
What sets RiskOps™ apart is its ability to integrate clinical impact into risk scoring. It considers factors like patient care roles, PHI volume, and workflow importance to prioritize issues that could affect patient safety. For instance, a medium-severity vulnerability on an anesthesia workstation used in surgeries might take precedence over a critical issue on a non-clinical kiosk. Dashboards highlight high-risk vendors and services managing large amounts of PHI or supporting essential workflows like EHR, imaging, or telehealth. This allows CISOs and clinical engineering teams to focus their efforts where they’re needed most.
Flexible workflows and seamless integrations
U.S. healthcare organizations can adapt RiskOps™ to fit their vendor lifecycle and change-management processes. Risk assessments are automated using customized questionnaires aligned with HIPAA, HITECH, and state regulations. The platform also integrates with ITSM tools like ServiceNow and Jira to generate automated remediation tickets, cutting assessment cycle times by up to 85%. Vendor users can log in to respond to assessments, upload SOC 2 reports or HITRUST certifications, and track remediation tasks, streamlining communication and reducing manual effort. These workflows and integrations ensure smooth regulatory compliance support.
Simplifying U.S. regulatory compliance reporting
RiskOps™ simplifies compliance by aligning assessments with HIPAA, HITECH, and state laws, mapping controls to regulatory requirements, and generating detailed reports. In the event of an OCR or state attorney general investigation following a PHI breach, health systems can use these reports to demonstrate due diligence. This includes completed vendor risk assessments, documented follow-ups on high-risk findings, and periodic re-assessments. The platform also maintains an auditable history of changes and can export evidence like encryption practices, access controls, and patch-management processes for systems containing ePHI. This feature reduces the time needed to respond to regulators, accreditation bodies, and cyber insurers.
2. Tenable.io for Healthcare
Tenable.io, also referred to as Tenable Vulnerability Management, provides continuous discovery and scanning across IT infrastructure, cloud environments, containers, and web applications. Powered by Tenable Nessus, it ensures comprehensive network visibility, making it a reliable tool for identifying vulnerabilities in healthcare systems.
Tailored Discovery and Scanning for Healthcare
When it comes to medical devices and operational technology (OT) in healthcare, Tenable OT Security offers robust protection for industrial control networks. It provides clear visibility across IT and OT environments, ensuring seamless integration with Tenable Vulnerability Management. Available either as an add-on or through the Tenable One platform, this solution delivers a well-rounded approach to securing healthcare devices.
Risk Prioritization with Clinical Awareness
Tenable.io leverages automated risk prioritization alongside continuous scanning to identify critical exposures that could impact healthcare operations. Its Vulnerability Priority Rating (VPR) combines threat intelligence with asset importance, ensuring that the most dangerous vulnerabilities are brought to the forefront. This approach helps healthcare organizations focus their efforts where they matter most.
Streamlined Workflows and Seamless Integrations
Tenable.io offers a documented API and pre-built integrations to streamline remediation efforts by feeding vulnerability data directly into existing workflows. With Tenable Patch Management, it automates the patching process by linking vulnerabilities to their corresponding fixes. According to an Infosec Engineer, the web-based dashboard simplifies the review of both vulnerability and asset data. These features make it easier for healthcare organizations to align their security measures with clinical operations, ensuring efficient and effective protection.
3. Qualys Vulnerability Management, Detection, and Response (VMDR)
Qualys VMDR is a cloud-based tool designed to simplify vulnerability management in healthcare settings. It combines asset discovery, vulnerability assessment, and remediation into one streamlined solution. Built on the Qualys Cloud Platform, it keeps a close eye on assets across on-premises, cloud, and hybrid environments, ensuring inventories stay current and vulnerabilities are quickly identified.
The platform uses continuous scanning and integrates TruRisk™ scoring to help healthcare organizations prioritize vulnerabilities effectively. This makes tracking and resolving issues more efficient while addressing the unique challenges of healthcare environments.
Qualys VMDR also delivers detailed reporting tools that compile evidence of regular scans and remediation efforts. These reports are audit-ready, helping organizations maintain compliance with the HIPAA Security Rule.
4. Rapid7 InsightVM
Rapid7 InsightVM is a cloud-managed platform designed to tackle the unique security challenges in healthcare environments. It delivers continuous discovery and assessment across on-premises, cloud, and hybrid setups. The tool scans systems like Windows, Linux, and various operating systems used for EHRs, PACS, and clinical databases. It also identifies network-connected medical devices that handle electronic protected health information (ePHI) or support clinical workflows, making it a comprehensive solution for healthcare security needs [3].
Risk-based Prioritization with Clinical Context
One standout feature of InsightVM is its Active Risk scoring, which goes beyond standard CVSS ratings. It incorporates exploitability data, attacker behavior, and potential business impact to rank vulnerabilities effectively [7]. What makes it particularly useful in healthcare is its ability to tag assets with clinical metadata. For instance, systems critical to patient care, such as those used for medication administration or ePHI storage, are automatically assigned higher priority than non-clinical devices with the same vulnerability. This ensures that patching schedules focus on safeguarding patient safety.
Security teams often collaborate with clinical engineering and CMIO or CNIO leadership to keep these clinical context tags accurate. This teamwork ensures that risk scores remain aligned with operational priorities and patient care needs, providing a more focused approach to vulnerability management.
Configurable Workflows and Integrations
InsightVM integrates seamlessly with existing ITSM workflows while emphasizing real-time clinical context. It connects with platforms like ServiceNow, Jira, and various SIEM systems to automate remediation workflows from detection to resolution [3][4]. Healthcare organizations can set up rules to automatically generate change tickets for vulnerabilities on critical systems like EHR servers, ensuring that remediation happens efficiently and with minimal disruption to clinical operations.
The platform's APIs and webhook capabilities allow InsightVM to sync with clinical tools, aligning vulnerability management with maintenance schedules. For example, many U.S. health systems use these integrations to activate compensating controls, such as network segmentation, when patching is delayed due to vendor validation requirements on medical devices or clinical systems [4].
Support for U.S. Regulatory Compliance Reporting
InsightVM also plays a key role in helping healthcare organizations meet regulatory requirements. Its reporting and analytics capabilities provide evidence for HIPAA Security Rule compliance, particularly around technical safeguards and risk management activities [4][6]. The platform generates detailed reports that cover vulnerability exposure, remediation timelines, and risk trends, aligning with HIPAA §164.308(a)(1)(ii)(A)–(B) [6].
Customizable Liveboards offer real-time dashboards to track remediation SLAs, vulnerability trends, and program KPIs, making it easier to demonstrate compliance during OCR or third-party audits. These tools not only assist with remediation but also strengthen the organization’s overall compliance posture by documenting ongoing security efforts and risk management practices.
5. Nessus Professional
Nessus Professional, created by Tenable, is a widely used vulnerability scanner that helps identify misconfigurations, missing patches, and known vulnerabilities within IT systems that handle ePHI. This includes environments such as EHR servers, PACS workstations, domain controllers, and network devices [8]. What sets Nessus Professional apart is its focus on tailored scanning and the ability to prioritize vulnerabilities within a healthcare context. It plays a crucial role in vulnerability management by blending technical detection with risk assessments specific to healthcare needs.
Discovery and Scanning Tailored for Healthcare
Nessus Professional offers flexible scanning options, including agent-based, agentless, and credentialed scanning, providing deep visibility into Windows and Linux systems often found in hospital data centers [8]. To avoid disrupting critical systems, security teams can use safe scan templates - like scheduling scans during off-hours for production EHR environments or patient portals [4]. For medical devices and IoMT systems, such as infusion pumps, imaging systems, and bedside monitors, Nessus allows for lightweight, non-intrusive scans. These profiles use longer timeouts, reduced intensity, and fewer probes to prevent overloading sensitive equipment [2][4]. Organizations can inventory devices passively and then input specific IP ranges into Nessus for targeted assessments during maintenance windows, often in coordination with biomedical engineering teams [1][2].
Prioritizing Risks with Clinical Context
Once assets are discovered and scanned, the next step is prioritizing vulnerabilities based on their clinical impact. Nessus Professional uses CVSS scores, exploitability data, and plugin severity levels to rank vulnerabilities, helping teams focus on the most critical issues [3][4]. Healthcare organizations often take this a step further by mapping assets to their clinical importance. For example, systems that store ePHI or support life-saving care are marked as high-criticality, and scan results are overlaid with this context in ticketing or governance systems [1][6]. Advanced programs may also incorporate real-time threat intelligence to quickly identify vulnerabilities that require immediate action [4].
Flexible Workflows and Integrations
Nessus Professional's API and standardized reporting features make it easy to integrate scan results into ITSM tools like ServiceNow, Jira, or Cherwell [4][5]. Security teams can also link Nessus data to SIEM platforms to correlate scan findings with real-time events - for instance, flagging vulnerabilities in a VPN appliance under active brute-force attack [3][4]. Additionally, Nessus can be tied to a CMDB or clinical asset management system, allowing organizations to associate vulnerabilities with specific devices, their locations, and clinical service lines. This targeted approach streamlines responses. For broader risk management, Nessus outputs can be imported into platforms like Censinet RiskOps™, enabling organizations to connect technical findings with enterprise risk registers and generate reports suitable for board-level discussions [1].
sbb-itb-535baee
6. Kenna Security
Kenna Security, now known as Cisco Vulnerability Management, stands out as a tool designed to sharpen risk management by zeroing in on vulnerabilities that matter most. Instead of attempting to address every single issue, it prioritizes the ones most likely to be exploited. This approach is especially useful for healthcare organizations, where studies reveal that while 95% of vulnerabilities remain untouched by attackers, addressing the top 5–10% can reduce vulnerability backlogs by 20–40%.
Streamlined Workflows and Seamless Integrations
Kenna Security doesn’t just identify risks - it simplifies how they’re handled. By integrating with platforms like ServiceNow and Jira, it automates remediation workflows, ensuring critical vulnerabilities are assigned to the right teams without delay. Custom rules can be set up to route high-risk findings to appropriate teams, aligning with maintenance schedules and service-level agreements.
Additionally, its integration with asset management systems provides a consolidated view of vulnerabilities across both clinical and IT environments. This ensures that healthcare organizations can focus their efforts on vulnerabilities that directly impact patient care and compliance, keeping operations smooth and secure.
7. Armis for Healthcare IoT and Medical Devices

As healthcare technology evolves, the need to secure the Internet of Medical Things (IoMT) and connected medical devices has become more pressing. Devices such as infusion pumps, imaging systems, patient monitors, and even building management systems are now part of the healthcare ecosystem, creating visibility and security challenges that require specialized solutions.
Risk-Based Prioritization with Clinical Context
Armis takes a unique approach to managing vulnerabilities by combining technical data with clinical context. This means it doesn’t just look at a device's technical weakness - it also considers the device's role and how critical it is to patient care. For example, a device in a critical care unit might be flagged for immediate attention, even if its technical vulnerability score is similar to a less critical device in another area. This approach ensures that devices essential to patient safety are addressed first, aligning IoMT security with the broader priorities of healthcare operations.
Customizable Workflows and Integrations
To streamline operations, Armis integrates seamlessly with ITSM platforms like ServiceNow and Jira. These integrations automate processes like ticket creation and provide tailored dashboards, ensuring that actionable alerts reach the right teams promptly. This makes it easier for healthcare organizations to manage the unique security demands of IoMT and connected medical devices.
Feature Comparison Table
Below is a comparison of seven top healthcare vulnerability management tools, focusing on critical features like asset discovery, risk prioritization, workflow automation, compliance reporting, and their alignment with the unique needs of healthcare. This table serves as a quick-reference guide, summarizing each tool’s primary capabilities.
| Tool | Asset Discovery Coverage | Risk Prioritization Method | Workflow & Automation | Compliance & Reporting | Healthcare-Specific Focus |
|---|---|---|---|---|---|
| Censinet RiskOps™ | Covers vendors, cloud services, clinical apps, medical devices, supply chains, and PHI systems | Scores risks based on questionnaires, evidence validation, and business impact data (e.g., PHI volume, critical workflows, vendor reliance) | Offers collaborative workflows for vendor risk assessments, remediation plans, and shared attestations; includes role-based access control and automated routing to compliance/IT teams | Supports HIPAA, HITRUST, SOC 2, PCI; provides audit-ready reports, executive dashboards, and evidence exports for regulatory reviews | Tailored for healthcare with features like BAA tracking, medical device risk management, EHR/clinical app protection, and access to a network of 50,000+ healthcare vendors |
| Tenable.io for Healthcare | Continuous discovery across on-prem, cloud, and hybrid environments; scans networks, OS, and applications; uses cloud connectors and agents | Prioritizes vulnerabilities using CVSS, threat intelligence, exploit data, and asset criticality | Integrates with ITSM tools (e.g., Jira, ServiceNow) and SIEM; supports automated ticketing and CI/CD processes | Maps to CIS benchmarks, PCI, NIST CSF, HIPAA; offers customizable compliance reports | Suitable for healthcare IT environments but requires manual mapping to clinical priorities |
| Qualys VMDR | Provides cloud-native discovery for endpoints, servers, containers, and cloud workloads through active and passive scanning | Uses risk-adjusted scores based on threat intelligence, exploit availability, and asset context | Integrates with orchestration tools and ticketing systems; includes automated patch suggestions and triggers | Maps to CIS, PCI DSS, NIST, ISO 27001, HIPAA; generates audit-ready reports | Focuses on broad IT infrastructure scanning; lacks native medical device-specific features |
| Rapid7 InsightVM | Adaptive scanning with agent/agentless options; continuous discovery for endpoints, servers, and cloud environments; live dashboards | Combines exploit data, threat intelligence, and breach data into risk-based models; adjusts scan frequency based on risk | Integrates with SIEM; features live dashboards for patch status and exposure; supports automated remediation workflows | Supports NIST, PCI, HIPAA; includes compliance dashboards | Covers general healthcare infrastructure, scanning clinical application servers but missing IoMT-specific capabilities |
| Nessus Professional | Performs point-in-time network and system scanning; detects host and application vulnerabilities | Relies on CVSS-based severity scoring with exposure context; advanced risk ranking requires external platforms | Limited native workflow automation; often used as a scanner engine within broader platforms | Provides basic compliance checks (CIS, PCI); requires external tools for detailed HIPAA reporting | Best for point-in-time assessments; not designed for continuous workflows in healthcare environments |
| Kenna Security | Aggregates data from multiple scanners (e.g., Tenable, Qualys) and CMDB systems; normalizes and correlates assets rather than performing primary discovery | Uses risk-based vulnerability management by combining scanner data, threat intelligence, exploit likelihood, and asset business value | Features a centralized risk dashboard; integrates with ticketing systems (e.g., Jira, ServiceNow) for routing prioritized tickets; supports customizable workflows | Maps to frameworks like NIST, PCI, ISO; provides executive reporting on remediation trends | Consolidates data across healthcare environments but requires manual alignment of risk scores with clinical priorities |
| Armis for Healthcare IoT and Medical Devices | Offers agentless discovery for unmanaged IoMT/medical devices (e.g., infusion pumps, MRI machines, patient monitors); identifies assets via network-based methods | Scores clinical risks by considering device type, connectivity, ePHI capability, patient safety impact, and exploitability; prioritizes life-sustaining devices | Integrates with ITSM tools (e.g., ServiceNow, Jira) for automated ticketing; supports workflows for network segmentation, device isolation, and policy updates | Documents HIPAA safeguards like network segmentation, access controls, and device hardening; provides audit evidence for medical device inventories | Specializes in IoMT and medical devices; focuses on patient safety and fills gaps for devices that can’t run traditional agents |
Healthcare organizations face unique challenges in managing risks, requiring tools that address both IT infrastructure and clinical environments. Censinet RiskOps™ stands out by addressing third-party and enterprise risks specific to healthcare. Meanwhile, Armis excels in providing visibility and management for IoMT and medical devices. Tools like Tenable, Qualys, and Rapid7 focus more on IT infrastructure, often requiring manual adjustments to align with clinical needs.
Most healthcare providers need a combination of these tools to cover all bases. IT scanners are essential for infrastructure, IoMT platforms handle medical devices, and healthcare-focused solutions like Censinet manage vendor and enterprise risks. The key is selecting tools that integrate seamlessly with ITSM and SIEM platforms, meet HIPAA audit requirements, and support workflows that prioritize patient safety in the fast-paced, 24/7 healthcare environment.
Conclusion
When selecting a healthcare vulnerability tool, it's crucial to find one that aligns with your organization's needs while incorporating clinical context, compliance requirements, and scalable operations. The best tools go beyond just scanning for technical vulnerabilities - they assess how risks impact patient safety, care delivery, and the protection of PHI, not just your IT systems.
Look for solutions that provide automated risk insights and integrate smoothly into existing workflows. Tools that adopt a risk-based approach - factoring in exploit intelligence, potential clinical impacts, and continuous asset discovery across servers, endpoints, cloud workloads, and medical devices - are particularly effective. Automation is key, especially when it integrates with IT systems like ITSM, SIEM, and clinical systems. Additionally, healthcare-specific challenges, like managing legacy systems that can't be patched or securing IoMT devices with network segmentation, should be addressed.
A comprehensive strategy often combines IT scanners for infrastructure, IoMT platforms for medical devices, and healthcare-focused tools like Censinet RiskOps™ for managing third-party and enterprise risks. For example, Tower Health implemented Censinet RiskOps™, which allowed them to reallocate three full-time employees back to their primary roles while reducing the need for additional staff dedicated to risk assessments.
Finally, test potential tools in a realistic environment. Involve both security and clinical engineering teams to ensure the solution provides thorough discovery, accurate clinical context, and seamless workflow integration.
FAQs
How do customizable vulnerability tools help protect patient safety in healthcare?
Customizable vulnerability tools are essential for safeguarding patient safety in healthcare. These tools work by actively spotting and addressing security weaknesses in critical areas like clinical applications, medical devices, and patient data systems.
By keeping a constant watch for vulnerabilities, healthcare organizations can fend off potential breaches and interruptions before they occur. This not only protects sensitive patient information but also helps ensure that healthcare operations remain uninterrupted, fostering a safer and more secure environment for both patients and providers.
What factors should healthcare organizations consider when integrating vulnerability management tools with their systems?
Healthcare organizations face unique challenges, and the tools they use should be built with these in mind. It's crucial that these tools work seamlessly with existing systems like electronic health records (EHRs) and clinical applications to prevent any disruptions in daily operations.
When choosing tools, two key features stand out: real-time risk assessment and team collaboration capabilities. Real-time risk assessment helps healthcare providers quickly spot and address vulnerabilities, whether it's safeguarding patient data, securing medical devices, or managing risks in the supply chain. Meanwhile, tools that encourage collaboration across teams ensure a more unified and effective approach to tackling these challenges. By using solutions designed specifically for healthcare, organizations can strengthen their cybersecurity efforts where it matters most.
How do vulnerability management tools help healthcare organizations stay compliant with regulations?
Vulnerability management tools play a crucial role in helping healthcare organizations keep up with regulatory compliance. By continuously monitoring and assessing cybersecurity risks, these tools make it easier to spot vulnerabilities, automate compliance reporting, and document adherence to important regulations.
They’re especially useful for aligning with standards like HIPAA and HITECH. With features like real-time insights, benchmarking, and simplified risk assessments, these tools enable healthcare providers to manage risks tied to patient data, medical devices, and essential applications - all while ensuring they meet regulatory requirements.


