Why Patch Validation Matters for Medical Devices
Post Summary
Patch validation is critical for ensuring medical devices remain secure, functional, and safe for patient use. Medical devices rely on software updates to fix vulnerabilities, but without proper validation, these patches can create new risks, such as device malfunctions or data breaches. The FDA mandates manufacturers to validate software changes, including cybersecurity updates, to maintain device safety and effectiveness.
Key points to know:
- FDA Requirements: Manufacturers must validate all software updates under Quality System Regulations (QSRs) and Section 524B of the FD&C Act.
- Cybersecurity Risks: Patches address vulnerabilities but can introduce errors if not properly tested.
- Patient Safety: Unvalidated patches can cause device failures or expose sensitive patient data.
- Healthcare Challenges: Implementing updates can disrupt clinical workflows and increase operational costs.
- SBOMs: Software Bills of Materials (SBOMs) help track third-party components and prioritize patching efforts.
Proper patch validation safeguards devices, protects patient data, and ensures compliance with federal regulations, making it a cornerstone of modern healthcare cybersecurity.
Patch Validation's Role in Medical Device Security
Closing Security Gaps
Patch validation ensures that updates resolve existing vulnerabilities without introducing new ones [5]. For example, when manufacturers update authentication systems, encryption protocols, or connectivity features, validation confirms that these changes don't inadvertently create new security issues [5]. The FDA emphasizes this point:
A 'reasonable assurance of cybersecurity' can be part of FDA's determination of a device's safety and effectiveness [5].
The range of devices requiring this process is broader than many might think. The FDA considers any device with connectivity features - whether through Wi-Fi, Bluetooth, cellular networks, or even hardware ports like USB and serial connectors - as having the "ability to connect to the internet", making them subject to cybersecurity validation requirements [5].
Manufacturers must also ensure that the off-the-shelf and open-source components listed in the Software Bill of Materials (SBOM) remain secure after patches are applied [5][1]. Coordinated Vulnerability Disclosure (CVD) processes provide a structured way to identify and address exploits that demand validated patches [5]. These efforts not only strengthen device connectivity but also help safeguard sensitive patient information.
Protecting Patient Data
Validated patches play a critical role in securing Protected Health Information (PHI) and other sensitive patient data stored on or transmitted by medical devices. Deploying unvalidated updates can lead to unexpected vulnerabilities, potentially exposing patient records to unauthorized access or breaches.
To counter this, healthcare organizations increasingly rely on collaborative risk networks. These networks pool cybersecurity data from over 50,000 vendors and products, enabling healthcare providers to confirm that patches meet shared security standards before implementation [6]. James Case, VP & CISO at Baptist Health, highlights this shift:
Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with [6].
By moving from manual spreadsheets to automated risk assessments, one healthcare system reduced the workload from three full-time employees to just two, while improving overall security [6]. This streamlined approach enhances patient data protection across the medical device ecosystem.
Meeting Regulatory Requirements
Beyond addressing security gaps and safeguarding patient data, patch validation also ensures compliance with federal regulations. Quality System Regulations (QSRs) and Section 524B of the FD&C Act require manufacturers to document and validate patches to address cybersecurity risks. Non-compliance can result in an NSE (Not Substantially Equivalent) determination [1][5].
Under Section 524B, manufacturers must outline plans for monitoring, identifying, and addressing cybersecurity vulnerabilities in the postmarket phase. These plans must also justify the timelines for releasing validated patches [5].
Fortunately, the FDA typically does not require pre-approval for updates focused solely on improving cybersecurity. This policy allows manufacturers to deploy validated patches more quickly, ensuring devices remain secure without unnecessary regulatory delays [1].
sbb-itb-535baee
How Patch Validation Improves Patient Safety
Finding Software Vulnerabilities
Patch validation plays a crucial role in uncovering software flaws that could jeopardize patient care. It identifies coding errors - like buffer overflows or "use after free" issues - that attackers might exploit, potentially causing unpredictable device behavior[9]. Ken Hoyme, Senior Fellow of Global Product Cybersecurity at Boston Scientific, highlights this process:
"Elimination of manufacturer implementation errors is done through coding standards, typically enforced by static code analysis tools tuned for security coding errors that lead to vulnerabilities." [9]
Medical devices often rely on third-party components such as operating systems, libraries, and frameworks, which are frequent sources of vulnerabilities. Patch validation ensures that updates addressing these issues do not inadvertently introduce new risks[9]. It's important to note that not all vulnerabilities carry the same level of risk - some may directly impact device functionality and patient safety, while others might primarily affect data privacy[4].
By validating patches, manufacturers ensure both the identification of vulnerabilities and the preservation of device functionality.
Preventing Device Malfunctions
Properly validated patches help prevent malfunctions in critical systems, such as those responsible for delivering insulin or electrical stimulation, where precise timing is essential[9]. Without thorough validation, a patch could disrupt these time-sensitive processes, leading to failures in therapy delivery. As Hoyme explains:
"Cybersecurity patches may affect the overall performance of a non–real-time OS." [9]
The validation process includes regression testing to confirm that fixing one issue doesn’t inadvertently create new problems. Chad Waters, Senior Cybersecurity Engineer at ECRI, underscores this point:
"An unvalidated patch could do more harm than good." [8]
Healthcare organizations are encouraged to test patches on non-critical systems first, ensuring functionality remains intact before rolling them out widely[7]. Manufacturers also design their validation test suites to isolate platform service tests from device functionality tests. This approach ensures that patches for vulnerabilities in third-party software don’t accidentally disrupt communication channels or interfere with therapy controls.
2.3 | Learn Medical Software Validation: FDA's Foundational GPSV Guidance - Medical Software Course
Standards and Best Practices for Patch Validation
5 Core Steps for Medical Device Patch Validation
As of February 2, 2026, the FDA's Quality Management System Regulation (QMSR) aligns 21 CFR part 820 with ISO 13485:2016, requiring manufacturers to embed risk-based software validation throughout the entire device lifecycle [10][11]. This change highlights that cybersecurity isn’t just an add-on to device safety - it’s a core component. The FDA reinforces this by stating:
"Cybersecurity is a part of safety and effectiveness... A Secure Product Development Framework (SPDF) can be used to fulfill aspects of QS Regulation." [2]
Under Section 524B of the FD&C Act, manufacturers of "cyber devices" - devices with software connectivity and potential cyber risks - must create plans to monitor and address vulnerabilities that arise after the product hits the market [2][11]. This includes establishing patching protocols: routine updates for known issues and immediate out-of-cycle patches for critical threats. Frameworks like the NIST Cybersecurity Framework and tools such as the National Vulnerability Database provide structured methods for identifying and addressing these risks [11].
An FDA review of 3,140 medical device recalls revealed that 7.7% were due to software failures, with 79% of those failures caused by defects introduced during post-production changes [10]. These numbers highlight why patch validation is essential - it’s not just about fixing bugs; it’s about safeguarding patient safety and ensuring system reliability.
These regulations lay the groundwork for practical steps to ensure patch integrity and device security.
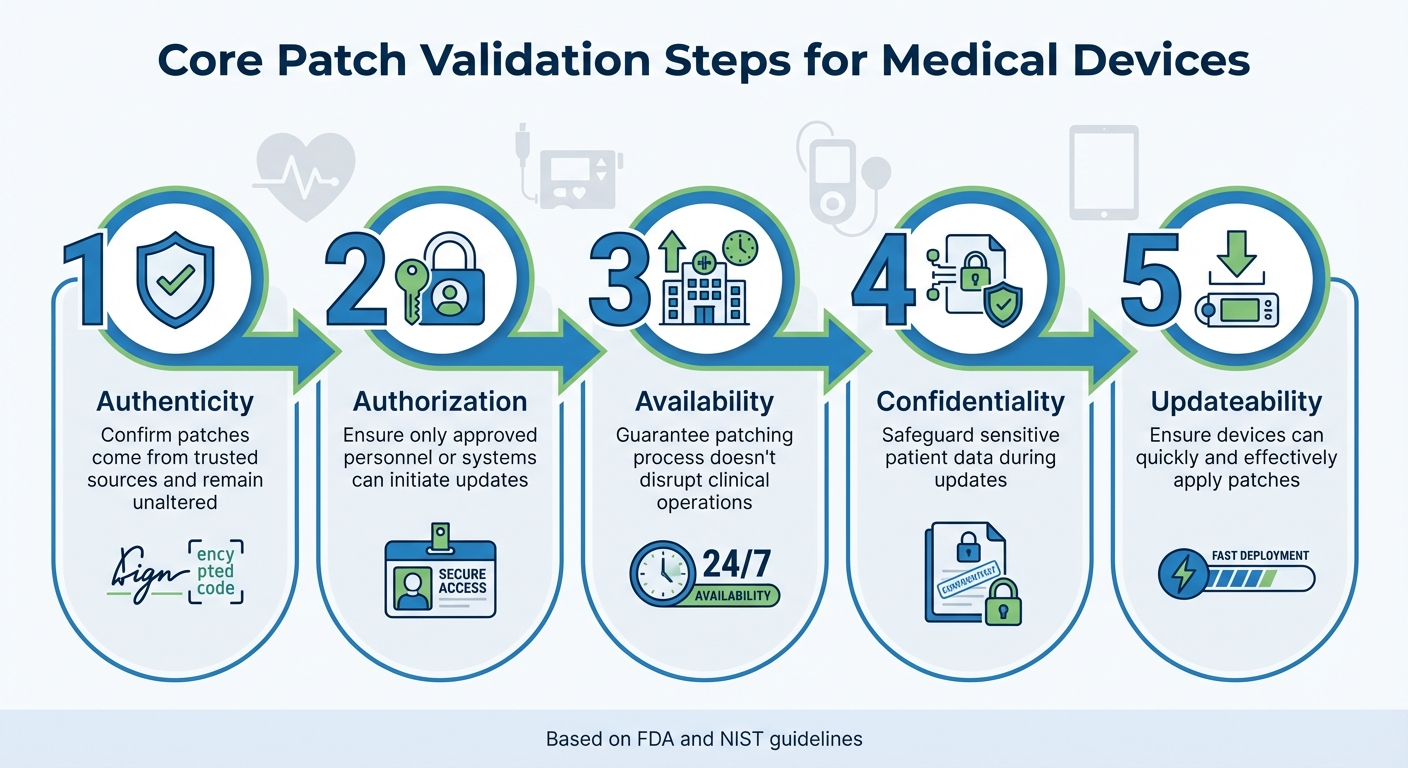
Core Validation Steps
Effective patch validation focuses on five key security goals, ensuring updates improve device safety without introducing new risks:
- Authenticity: Confirming patches come from trusted sources and remain unaltered.
- Authorization: Ensuring only approved personnel or systems can initiate updates.
- Availability: Guaranteeing the patching process doesn’t disrupt clinical operations.
- Confidentiality: Safeguarding sensitive patient data during updates.
- Updateability: Making sure devices can quickly and effectively apply patches [2][11].
Healthcare organizations should adopt a tiered patching approach consistent with FDA and NIST guidelines. This involves addressing known vulnerabilities on a regular schedule while deploying critical patches immediately when urgent risks are identified [2][11]. Digital signatures should be used to verify patch authenticity, and updates should be tested on non-critical systems before broader implementation.
Validation should also include rigorous security checks, such as threat mitigation assessments, vulnerability scans, and penetration testing [2]. Gradual deployment across the network, starting with non-critical systems, helps minimize potential disruptions.
Organizations are encouraged to request "Updateability/Patchability Views" from manufacturers. These diagrams detail security-relevant system components and their interactions during updates, helping IT teams identify potential conflicts and ensure smooth deployments [2].
Using Software Bill of Materials (SBOMs)
In addition to thorough testing, manufacturers are now required to provide machine-readable Software Bills of Materials (SBOMs) as per the FDA’s guidelines, which align with the 2021 NTIA "Framing Software Component Transparency" document [2][11]. These SBOMs list all software components - commercial, open-source, and off-the-shelf - used in a device, offering a complete inventory of its software ecosystem.
SBOMs shift patch validation from a reactive process to a proactive one. For instance, when vulnerabilities like URGENT/11 and SweynTooth were found in widely used third-party components, they posed risks across various clinical specialties [11]. With SBOMs, healthcare organizations can quickly identify affected devices and prioritize patching efforts accordingly.
SBOMs also support risk mapping by allowing organizations to cross-reference device inventories with databases like the NIST National Vulnerability Database [2][11]. This enables security teams to assess their exposure and respond swiftly when new vulnerabilities are identified.
Additionally, SBOMs facilitate coordinated vulnerability disclosure. By engaging in disclosure programs, healthcare organizations can report and address vulnerabilities before they’re publicly disclosed, reducing the window of opportunity for exploitation [2]. This approach helps security teams stay ahead of threats and manage risks more effectively.
Platforms like Censinet RiskOps™ can further streamline these practices, integrating patch validation into a broader cybersecurity framework and enhancing overall risk management strategies.
Patch Validation in Healthcare Settings
Clinical Implementation Examples
Research involving 23 stakeholders across nine healthcare organizations highlighted the complexity and cost of updating 25 medical devices [3]. While manufacturers are responsible for validating software design changes to ensure safety and effectiveness, healthcare delivery organizations (HDOs) face the task of securely deploying these devices and evaluating medical device security risks associated with patching [1].
Since October 2023, the PATCH Act has brought heightened attention to medical device cybersecurity. This has led to the FDA issuing a staggering 700% increase in deficiency letters, with each letter averaging 15 deficiencies. Around 70% of 510(k) submissions now receive requests for additional information [12]. These numbers emphasize the growing importance of meticulous patch validation in clinical environments.
On top of these challenges, HDOs must also ensure smooth communication between interconnected devices.
Validation for Device Interoperability
Interconnected devices, such as MRI scanners and wearable monitors, present unique interoperability issues. Ensuring seamless communication is critical to patient safety, as patches can unintentionally disrupt device interactions or introduce data transfer errors. The FDA has provided guidance on this issue, with Matthew Hazelett, Cybersecurity Policy Analyst at the FDA, stating:
Cybersecurity controls should not be intended to prohibit users from accessing device data [2].
The goal is to enhance security without interfering with clinical workflows.
To address these concerns, HDOs conduct system-level evaluations when validating patches for interoperable devices. This often involves using architectural diagrams - like "Global System Views" and "Security Use Case Views" - to trace device communication pathways and detect potential conflicts before rolling out updates. Balancing security and safety risks is crucial to ensuring devices function effectively [2].
Patching in the intricate healthcare landscape remains a daunting task. As Lorenz Kustosch and colleagues from TU Delft noted:
It is questionable if conventional security patching will actually work in the healthcare sector without overwhelming it operationally and financially [3].
Platforms like Censinet RiskOps™ offer a solution by integrating patch validation into broader risk management strategies. These tools help organizations prioritize critical updates based on factors like network exposure, device vulnerabilities, and clinical impact - keeping interoperability intact while maintaining security standards.
Conclusion
Ensuring patch validation is a critical step in maintaining the safety of medical devices and protecting patient care. The FDA mandates that manufacturers validate every software design change, including cybersecurity patches, to confirm that devices remain safe and effective throughout their lifecycle [1][11].
Cyber incidents have increasingly disrupted healthcare networks and medical device operations, leading to delays in diagnoses and treatments. The FDA has identified the exploitation of known vulnerabilities as a "reasonably foreseeable failure mode" for medical device systems [11]. Without proper validation, patches could introduce new malfunctions, jeopardizing device performance and patient safety.
Healthcare organizations also play a vital role in securely deploying patches and assessing associated risks [1][11]. The challenge grows with interconnected devices, where patches might interfere with interoperability or disrupt clinical workflows.
The regulatory framework highlights the urgency of addressing these risks. Beginning February 3, 2026, the FDA will require "cyber devices" to comply with specific standards under Section 524B of the FD&C Act [11]. The numbers speak volumes: since October 2023, deficiency letters have surged by 700%, and 70% of 510(k) submissions now receive additional information requests [12]. These trends emphasize the importance of thorough patch validation to uphold security and ensure uninterrupted patient care.
Censinet RiskOps™ offers a solution by integrating patch validation with risk management. It prioritizes critical updates based on network exposure and device vulnerabilities, balancing security needs with the demand for consistent patient care.
Validated patches are essential for protecting device functionality and ensuring positive patient outcomes, making them a cornerstone of modern healthcare cybersecurity efforts.
FAQs
What counts as a “cyber device” under FDA rules?
Under FDA regulations, a "cyber device" refers to a medical device that incorporates software or connects to a network. Because these devices are vulnerable to cybersecurity threats, they demand continuous risk management. This includes implementing updates and patches throughout their lifecycle to maintain both safety and regulatory compliance.
How can hospitals test patches without disrupting patient care?
Hospitals can approach patch testing with minimal disruption by focusing on risk-based strategies. This means prioritizing updates for critical devices while scheduling patches during planned maintenance periods to avoid interfering with operations.
To safeguard clinical workflows, network controls like segmentation and access restrictions can be applied. These measures help isolate patched devices, reducing the risk of unexpected issues spreading across systems.
Additionally, tools like automated inventory management simplify the process by keeping track of devices and their patching status. Working closely with device vendors also ensures smoother testing and deployment, all while maintaining the highest standards of patient safety.
How does an SBOM help decide what to patch first?
An SBOM acts as a comprehensive inventory of software components, enabling organizations to pinpoint vulnerabilities and address them efficiently. By focusing on the severity of these vulnerabilities and the importance of the impacted medical devices, it helps ensure both patient safety and the security of the devices remain intact.


