2025 HIPAA Requirements for Vulnerability Scanning
Post Summary
Starting in 2025, HIPAA requires covered entities and business associates to conduct vulnerability scans at least every six months and penetration testing annually.
Vulnerability scans detect risks early, provide remediation steps, and ensure the confidentiality, integrity, and availability of ePHI.
The updates require encryption of ePHI at rest and in transit, annual penetration testing, and biannual vulnerability scans.
Penetration testing must be conducted at least once every 12 months.
Non-compliance can result in regulatory penalties, data breaches, and reputational damage.
Organizations should implement automated scanning tools, conduct regular risk assessments, and ensure compliance with encryption and testing standards.
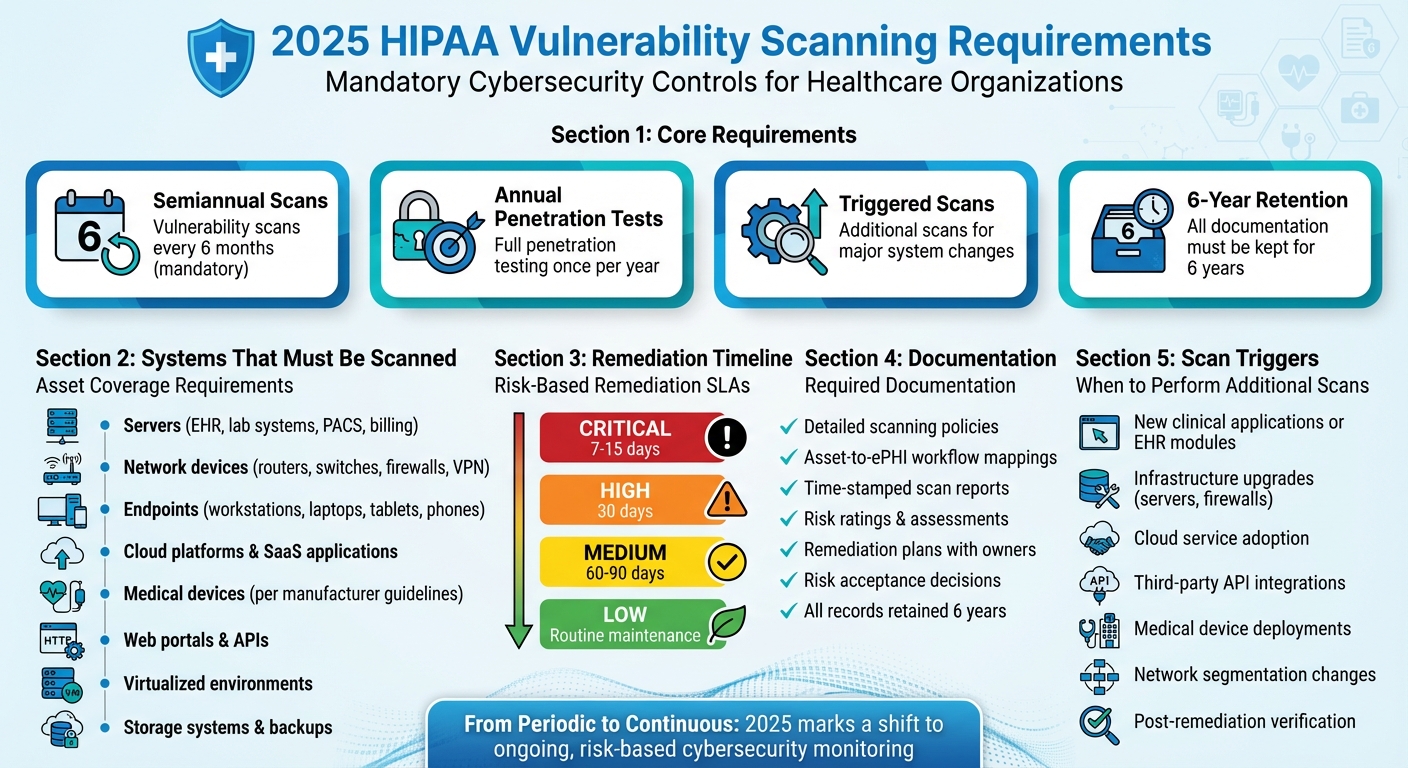
Starting in 2025, HIPAA mandates stricter cybersecurity measures for healthcare organizations handling electronic protected health information (ePHI). Vulnerability scanning is now a required, auditable control, with scans every six months and annual penetration tests. These updates aim to reduce risks like data breaches and service disruptions by enforcing proactive risk management.
Key changes include:
- Mandatory semiannual vulnerability scans and annual penetration tests.
- Triggered scans for major system changes (e.g., new software, infrastructure upgrades).
- Comprehensive asset coverage, including servers, networks, endpoints, cloud services, and medical devices.
- Documentation requirements: Policies, scan reports, remediation plans, and risk assessments must be retained for six years.
- Remediation timelines based on risk levels, such as 7–15 days for critical vulnerabilities.
To comply, healthcare organizations must integrate vulnerability scanning into their risk management programs, maintain updated asset inventories, and ensure continuous monitoring where possible. Tools like Censinet RiskOps™ can streamline compliance by centralizing scan data, remediation workflows, and audit evidence.
These updates mark a shift from periodic assessments to a more ongoing, risk-based approach, reinforcing the importance of cybersecurity in protecting patient data.
2025 HIPAA Vulnerability Scanning Compliance Requirements and Timeline
Required Vulnerability Scanning Standards Under 2025 HIPAA
The 2025 HIPAA update requires covered entities and business associates to conduct vulnerability scans every six months and penetration tests annually. Not documenting these scans could lead to HIPAA violations. This update lays out detailed compliance and operational requirements, which are explained below.
How Often to Scan and What Triggers Additional Scans
While the baseline requirement is semiannual scanning, organizations should also perform scans whenever there’s a significant change that impacts electronic protected health information (ePHI). These changes might include:
- Adding new clinical applications or electronic health record (EHR) modules
- Upgrading servers, firewalls, or other critical infrastructure
- Adopting cloud services that store or process PHI
- Integrating third-party APIs into workflows involving PHI
- Deploying large numbers of connected medical devices
- Modifying network segmentation or VPN access
- Addressing high- or critical-severity vulnerabilities to verify remediation
A thorough, documented risk analysis should identify these triggers, tie them to the organization’s change management process, and set specific timeframes for scans - such as within 7–14 days of a system going live. Many healthcare organizations also complement these requirements with more frequent internal and external scans. These proactive measures ensure that all assets interacting with ePHI are evaluated promptly, as outlined in the next section.
Which Assets and Systems Must Be Scanned
The 2025 HIPAA updates emphasize the importance of maintaining a detailed inventory of technology assets and a network map covering all systems that handle ePHI. At a minimum, vulnerability scanning should include:
- On-premises servers used for EHR, laboratory information systems, PACS, billing systems, and identity management
- Network components like routers, switches, firewalls, wireless controllers, and VPN gateways
- Endpoints such as workstations, laptops, tablets, and smartphones accessing PHI
- Virtualized environments and hypervisors
- Cloud platforms and SaaS applications that store or process PHI
- Storage systems and backups
- Public-facing web portals and APIs used by patients, providers, or partners
For connected medical devices, organizations should follow manufacturer recommendations and document any limitations related to scanning these devices.
Documentation and Record Retention Rules
HIPAA mandates that all security safeguards be implemented, thoroughly documented, and auditable, with regular reviews and tests to ensure their effectiveness. For vulnerability scanning, this means maintaining:
- Detailed policies that outline scanning procedures
- Documentation linking scanned assets to ePHI workflows
- Archived scan reports that include risk ratings, remediation plans, assigned responsibilities, and target completion dates
All documentation must be retained for six years. This ensures that scan reports, remediation records, risk acceptance decisions, and related communications are available for internal assessments, external audits, or investigations by the Office for Civil Rights.
Building Vulnerability Scanning Into Risk Management Programs
Incorporating vulnerability scanning into your HIPAA risk management framework can significantly enhance its effectiveness. The 2025 updates emphasize that scan results should directly feed into your risk analysis rather than remain siloed as standalone technical reports [2]. To meet this requirement, map each vulnerability to its associated asset, assign likelihood and impact scores, and track the issue through remediation or document it as an accepted risk. Additionally, connect scan outputs to your risk register, update Business Associate evaluations, and use the data to guide decisions on patching, network segmentation, and access controls [6, 14, 13].
Establish strong governance practices to ensure vulnerability metrics are integrated into risk registers and executive reports. Metrics like the number of unresolved critical findings, average remediation times, and exposure on high-risk systems should become regular agenda items for risk or security steering committees. By aggregating this data, you can provide meaningful insights for board-level or executive reporting. When scans uncover high-impact vulnerabilities, escalate them to enterprise risk registers alongside strategic risks like "Unauthorized disclosure of ePHI" or "Clinical service disruption." This approach strengthens compliance efforts and helps mitigate risks effectively.
Moving from Periodic Scans to Continuous Monitoring
Continuous monitoring builds on integrated risk management by providing real-time oversight of vulnerabilities. While HIPAA mandates semiannual scans and annual penetration tests, industry best practices recommend near-real-time visibility into vulnerabilities and misconfigurations in systems handling ePHI [5, 12, 13, 9]. Transitioning to continuous monitoring involves using automated tools and processes to maintain ongoing awareness, rather than relying solely on periodic assessments. For example, you might increase scan frequency by running monthly authenticated scans on critical systems and integrating scanners with security analytics platforms to ensure high-risk vulnerabilities trigger immediate alerts.
Organizations can also deploy agent-based or cloud-native scanners that continuously assess endpoints, automatically discover assets, and scan them as they are added [9, 14]. To support this shift, update governance structures by revising policies, defining monitoring responsibilities, and aligning metrics. These updates allow for faster identification and remediation of vulnerabilities, minimizing the risk to systems that store or process patient data.
Setting Priorities and Remediation Timelines
A risk-based SLA matrix is key to linking vulnerability severity levels to remediation timelines, as outlined in HIPAA security policies. For example, many organizations mandate that critical vulnerabilities - like easily exploitable remote code execution flaws on internet-facing systems with ePHI - be resolved within 7 days. High-severity issues typically require remediation within 30 days, medium-severity vulnerabilities within 60–90 days, and low-severity issues as part of routine maintenance. Actively exploited vulnerabilities often demand even faster timelines [7, 13, 3].
Prioritization should also account for business context. Systems hosting large amounts of ePHI, supporting direct patient care, or exposed to the internet may require shorter remediation timelines compared to internal administrative systems. Integrating scan results into ticketing tools like ITSM platforms can streamline the process by automatically generating and tracking remediation tasks based on severity. Regular reporting - such as the percentage of vulnerabilities resolved within SLA and documentation of exceptions requiring risk acceptance - demonstrates that vulnerability management is closely tied to overall risk management and HIPAA compliance efforts.
sbb-itb-535baee
Using Censinet for HIPAA-Aligned Vulnerability Management
Healthcare organizations preparing for the 2025 HIPAA requirements can rely on Censinet RiskOps™ to simplify and organize their vulnerability management efforts. This platform brings together vulnerability scan evidence, remediation workflows, and compliance documentation into one audit-ready system. By integrating vulnerability scanning with risk assessments, it directly supports HIPAA's mandate for continuous monitoring.
Managing Vulnerability Scanning and Risk Assessments in One Platform
With RiskOps™, scan outputs are automatically processed, normalized, and linked to asset risk registers. These registers include assigned owners, due dates, and clear remediation steps. Each vulnerability is tracked as a specific risk item, ensuring alignment with the HIPAA risk management plan and compliance with the 2025 continuous assessment requirements. For instance, if a biannual scan flags a critical vulnerability on a patient portal or EHR database server, the platform classifies it as high risk due to its direct exposure to ePHI. It then assigns an owner, sets a remediation deadline (e.g., 7–14 days for critical issues), and creates a detailed audit trail that aligns with HIPAA safeguards.
Evidence such as screenshots, configuration exports, and change tickets can be directly attached to each risk item, making it easier for auditors and regulators to review. This streamlined approach reduces the need for additional staff while increasing the volume of assessments.
Additionally, RiskOps™ connects third-party vulnerabilities to vendor profiles and business associate agreements (BAAs), addressing HIPAA requirements for managing third-party risks and ensuring proper oversight.
Enhancing Efficiency with Censinet AI
Taking this integrated approach further, Censinet AI helps healthcare organizations accelerate their path to 2025 HIPAA compliance by automating key tasks like evidence validation, policy creation, and governance. The AI reviews uploaded scan reports and maps them to specific HIPAA Security Rule requirements, including technical mandates for regular vulnerability scans and continuous risk assessments. This automation reduces the time spent manually interpreting reports. It can also draft policies and procedures tailored to the organization, such as a Vulnerability Scanning and Remediation Standard, which outlines scan frequency, asset coverage, SLAs, and documentation practices. Compliance leaders can then refine these drafts as needed.
Censinet AI also adds business context to vulnerability data. For example, it considers whether an affected system supports patient care, connects to medical devices, or stores significant amounts of PHI. This context allows the platform to adjust risk scores beyond standard CVSS severity ratings. A high vulnerability on a lab interface feeding results into an EHR might be escalated to critical due to its potential impact on PHI and clinical operations, while a similar issue on a low-priority back-office system might receive less attention.
Before audits, the AI ensures that required evidence - such as recent scans, penetration test reports, or proof of remediation - is available for all relevant assets. It flags any gaps that could jeopardize HIPAA compliance. By combining automation with human oversight, security teams can scale their risk management efforts while staying aligned with the 2025 Security Rule's expectations for ongoing assessments and continuous monitoring.
Preparing for 2025 HIPAA Vulnerability Scanning Requirements
What You Need to Know for Compliance
By 2025, the HIPAA Security Rule will make vulnerability scanning a mandatory control. This means covered entities and business associates must conduct and document vulnerability scans at least every six months for all systems that create, receive, maintain, or transmit electronic protected health information (ePHI) [3]. This requirement complements other critical measures like annual penetration testing, multi-factor authentication, encryption, and ongoing risk analysis.
To meet compliance, organizations should maintain detailed records, including time-stamped scan reports, remediation documentation, risk mappings, and formal policies. These records need to be stored for six years to ensure they’re accessible for OCR audits or inquiries [2]. Additionally, integrating vulnerability findings into a centralized risk register - with assigned risk owners, scores, and remediation deadlines - will be essential for continuous risk assessment.
With these changes on the horizon, healthcare organizations must act quickly to align their practices with the new requirements.
Action Steps for Healthcare Organizations
Healthcare organizations need to ensure their asset inventories and network maps are comprehensive, covering every system that interacts with ePHI. This includes electronic health record (EHR) platforms, clinical applications, medical devices, cloud services, and systems hosted by third parties. These inventories should be reconciled monthly to stay accurate. Organizations should also establish or update a formal vulnerability scanning policy, specifying semiannual scans as the minimum standard and requiring additional scans after significant system changes, vendor onboarding, or the discovery of new exploits.
It’s important to set clear remediation timelines based on risk levels:
- Critical vulnerabilities: Address within 7–15 days.
- High vulnerabilities: Resolve within 30 days.
- Medium vulnerabilities: Fix within 60 days.
Each vulnerability should be mapped to the relevant assets, data flows, and business processes, with risk owners and deadlines clearly assigned. Organizations should also secure evidence of semiannual scans and annual penetration test attestations for both business associates and third-party vendors. For situations where immediate patching isn’t possible - such as with legacy systems or certain medical devices - document alternative controls like network segmentation, access restrictions, or enhanced monitoring.
Tools like Censinet RiskOps™ can simplify this process by consolidating scan evidence, risk assessments, and vendor management into a single platform. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
Matt Christensen, Sr. Director GRC at Intermountain Health, echoed the importance of healthcare-specific solutions:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
FAQs
What changes are coming to HIPAA vulnerability scanning requirements in 2025?
Starting in 2025, healthcare organizations will need to step up their game when it comes to vulnerability scanning, thanks to updated HIPAA requirements. These changes push for continuous and automated scanning to spot and handle security gaps in real-time, offering stronger safeguards for sensitive patient information.
The updated rules place a spotlight on proactive risk management across clinical, administrative, and IT systems. By aligning with established industry practices, these measures aim to protect protected health information (PHI) more effectively and lower the risks tied to cybersecurity threats.
What steps should healthcare organizations take to address vulnerabilities under the 2025 HIPAA guidelines?
Healthcare organizations need to take a risk-based approach when tackling vulnerabilities, prioritizing those that pose the greatest threat to patient data or safety. By addressing critical risks first, they can significantly reduce potential harm. Regular and automated vulnerability scans are a must for quickly spotting and addressing potential security issues.
To stay in step with updated HIPAA guidelines, organizations should focus on continuous monitoring, use automated risk assessments, and adopt proactive strategies to maintain compliance. Tools like Censinet RiskOps™ can simplify these efforts, helping to speed up responses, manage resources efficiently, and better protect sensitive information.
How can organizations simplify compliance with the 2025 HIPAA requirements for vulnerability scanning?
Organizations looking to meet the 2025 HIPAA vulnerability scanning requirements can make the process easier by using solutions like Censinet RiskOps™. Designed specifically for healthcare cybersecurity and risk management, these tools offer automated assessments, continuous monitoring, and efficient workflows. This reduces the need for manual effort while helping ensure compliance with regulatory standards.
With features built for healthcare, such as assessments focused on patient data, clinical applications, and medical devices, these platforms enable organizations to identify and address vulnerabilities proactively while staying aligned with HIPAA's evolving requirements.
Related Blog Posts
Key Points:
What are the new HIPAA vulnerability scanning requirements for 2025?
- Biannual Scans: Covered entities and business associates must conduct vulnerability scans at least every six months.
- Annual Penetration Testing: Organizations are also required to perform penetration testing at least once every 12 months.
- Purpose: These measures aim to strengthen the cybersecurity posture of healthcare organizations and protect ePHI from evolving threats.
Why are vulnerability scans important for HIPAA compliance?
- Risk Detection: Vulnerability scans identify weaknesses in systems that could expose ePHI to unauthorized access.
- Remediation: They provide actionable steps to address vulnerabilities before they are exploited.
- Compliance: Regular scans support adherence to HIPAA’s Security Rule and ensure the confidentiality, integrity, and availability of ePHI.
What additional security measures are included in the 2025 HIPAA updates?
- Encryption: All ePHI must be encrypted both at rest and in transit.
- Penetration Testing: Annual testing is now mandatory to simulate real-world attacks and validate system security.
- Continuous Monitoring: Organizations are encouraged to adopt continuous monitoring practices to detect and respond to threats in real time.
How often must penetration testing be conducted under the 2025 HIPAA updates?
- Frequency: Penetration testing must be conducted at least once every 12 months.
- Purpose: This ensures that healthcare organizations can identify and address vulnerabilities that automated scans might miss.
What are the consequences of non-compliance with the 2025 HIPAA requirements?
- Regulatory Penalties: Non-compliance can result in significant fines and legal action.
- Data Breaches: Failure to conduct regular scans and tests increases the risk of breaches, compromising patient trust.
- Reputational Damage: Organizations that fail to meet HIPAA standards may face long-term reputational harm.
How can organizations prepare for the 2025 HIPAA vulnerability scanning requirements?
- Automated Tools: Implement tools that automate vulnerability scanning and provide real-time insights.
- Risk Assessments: Conduct regular risk assessments to identify gaps in compliance.
- Encryption Standards: Ensure all ePHI is encrypted at rest and in transit to meet HIPAA requirements.
- Training and Awareness: Educate staff on the importance of vulnerability scanning and penetration testing.


