5G Healthcare Applications and Vendor Risk: Network Security and Patient Safety
Post Summary
5G healthcare applications include telemedicine, remote surgery, real-time patient monitoring, wearable devices, and connected ambulances.
It ensures network security, protects patient data, and mitigates risks associated with third-party vendors in 5G-enabled healthcare systems.
Risks include cybersecurity threats, data breaches, interoperability challenges, and vulnerabilities in IoT and medical devices.
By conducting vendor assessments, implementing zero-trust architecture, and leveraging tools like Censinet RiskOps™ for continuous monitoring.
Compliance ensures adherence to regulations like HIPAA and HITECH, protecting patient data and ensuring secure network operations.
5G enables faster data transfer, low-latency telemedicine, enhanced remote surgery, and real-time monitoring, improving patient outcomes and operational efficiency.
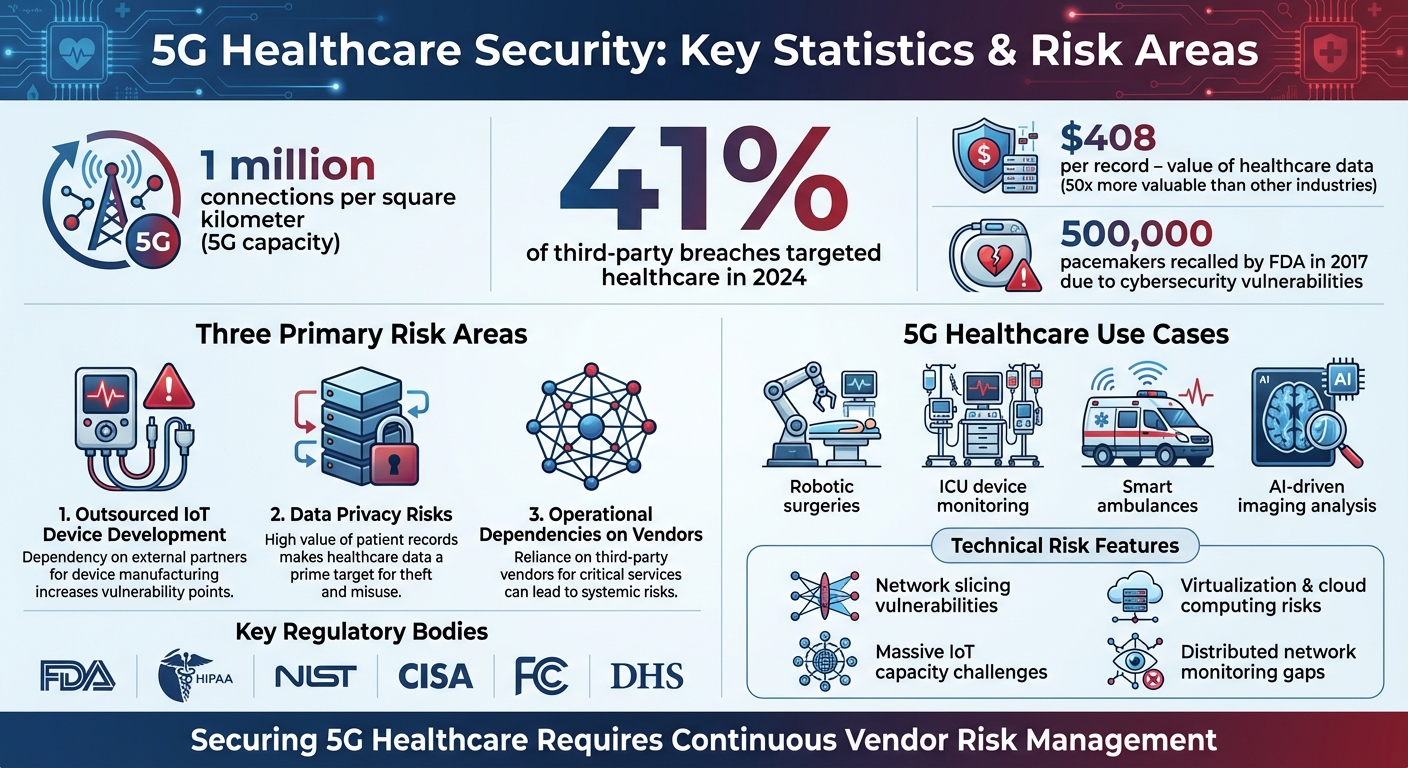
5G is transforming healthcare with faster speeds, lower latency, and the ability to connect countless devices. This enables advancements like real-time patient monitoring, robotic surgeries, and smart ambulances. However, these benefits come with serious risks. The increased reliance on third-party vendors, IoT devices, and cloud services creates vulnerabilities that threaten patient safety and data security. In 2024, 41% of third-party breaches targeted healthcare, highlighting the urgent need for better risk management.
Key takeaways:
To secure 5G-powered healthcare, organizations must adopt robust vendor risk management strategies, prioritize patient safety, and implement continuous monitoring of networks and devices.
5G Healthcare Security Risks and Statistics
How 5G Expands the Healthcare Attack Surface
5G Healthcare Use Cases
5G technology is revolutionizing healthcare with applications that were once unimaginable. It enables robotic surgeries with ultra-low latency, links ICU devices like ventilators, cardiac monitors, and infusion pumps for real-time monitoring, powers smart ambulances to transmit diagnostic data while en route, and speeds up AI-driven imaging analysis. However, with these advancements come new vulnerabilities. Each connected device or system becomes a potential entry point for attackers, meaning a single breach could compromise entire networks. In essence, these diverse applications significantly increase the risk landscape.
5G Technical Features That Increase Risk
The architecture of 5G differs fundamentally from earlier network technologies, introducing unique security challenges. For instance, network slicing - which allows multiple virtual networks to run on the same physical infrastructure - can be exploited if one slice is compromised, potentially allowing attackers to pivot to others. Additionally, 5G's reliance on virtualization and cloud computing shifts many network functions from hardware to software, expanding the attack surface to include cloud providers and their security measures.
The massive IoT capacity of 5G is another concern. With the ability to support up to 1 million connections per square kilometer, hospitals can connect far more devices than before. Unfortunately, many IoT devices prioritize affordability and ease of use over robust security measures [3][4].
Moreover, the distributed nature of 5G networks, which relies heavily on edge computing and device-to-device communication, complicates centralized monitoring. Traditional security controls may no longer capture all network traffic, creating blind spots where malicious activity can go undetected [3]. These vulnerabilities make 5G-powered healthcare systems more susceptible to cyberattacks, posing serious risks to both operations and patient safety.
Patient Safety and Operational Consequences
The security issues tied to 5G aren't just technical - they have direct and potentially devastating impacts on patient care. A breach in 5G services or among vendors could jeopardize patient safety in several ways. For example, if connected medical devices lose network access due to a security incident, clinicians might be unable to retrieve critical real-time data, delaying care. Worse yet, tampered data transmitted over compromised networks could lead to incorrect diagnoses or medication errors. Ransomware or botnet attacks could render essential devices like ventilators or infusion pumps inoperable, creating life-threatening situations.
The high speed and bandwidth of 5G, while beneficial for legitimate uses, also work in favor of attackers. Cyberattacks, such as botnets or ransomware, can propagate across networks faster than security teams can respond. With up to 1 million connections per square kilometer, attackers can launch large-scale traffic assaults using numerous compromised devices [3]. This enhanced connectivity and bandwidth also allow hackers to steal vast amounts of sensitive patient data in a fraction of the time it would take on older networks. The stakes in securing 5G healthcare systems couldn't be higher.
Vendor Risk and Network Security Challenges in 5G Healthcare
The 5G Healthcare Vendor Ecosystem
The 5G healthcare landscape involves a complex web of interconnected players, each contributing to the delivery of connected care. This ecosystem includes network providers like AT&T, Verizon, and T-Mobile, manufacturers of medical devices, cloud service providers such as Amazon Web Services, Microsoft Azure, and Google Cloud, and AI analytics companies. Together, they form the backbone of 5G-enabled healthcare.
However, this interconnectedness brings its own set of challenges. When multiple vendors share responsibilities, pinpointing accountability becomes tricky. A security flaw in one vendor's product can ripple across the entire system, complicating efforts to identify who should fix the issue - or who bears liability if patient safety is compromised [5].
Primary 5G Risk Areas
Three main areas of concern dominate the security conversation in 5G healthcare:
To tackle these risks, U.S. regulations emphasize the need for clear vendor accountability and enforce stringent security protocols.
U.S. Regulatory Requirements for Vendor Risk Management
Healthcare providers must adhere to various regulations, including HIPAA, HITECH, FDA cybersecurity guidelines, and state-specific laws, to ensure that vendors meet established security standards. Formal agreements between healthcare organizations and vendors are essential to enforce compliance.
The FDA has highlighted the growing gap between medical device security measures and the rapid pace of new device introductions [1]. Meanwhile, federal bodies like the Department of Homeland Security (DHS), Cybersecurity and Infrastructure Security Agency (CISA), National Institute of Standards and Technology (NIST), and Federal Communications Commission (FCC) are actively shaping 5G security standards and publishing threat models [6].
NIST’s National Cybersecurity Center of Excellence (NCCoE) has developed a 5G cybersecurity project that offers a security reference architecture for 5G networks. Key publications, such as NIST SP 1800-33A (Executive Summary) and NIST SP 1800-33B (Approach, Architecture, and Security Characteristics), provide actionable guidance for securely designing and operating 5G networks [7]. At the state level, laws like California’s CCPA (California Consumer Privacy Act) impose stricter controls on data management, which is increasingly vital as 5G networks handle larger volumes of patient information [8].
How to Assess 5G Vendor Risk
5G Vendor Risk Assessment Framework
Healthcare organizations need more than just basic checklists to evaluate 5G vendor risks effectively. A structured framework is essential - one that looks at both technical controls (like endpoints, MEC, RAN, NFV, network slicing, and IoT devices) and managerial controls (such as governance, personnel, and operations) [9].
To strengthen these evaluations, adopting a Zero-Trust Architecture (ZTA) is key. This approach examines four critical dimensions:
When assessing vendors, healthcare organizations should scrutinize their cybersecurity policies, patch management processes, incident response strategies, and compliance with frameworks like the NIST Cybersecurity Framework. The goal? To ensure vendor practices align with the unique challenges that 5G technology introduces to patient care environments. This framework sets the stage for thorough and effective vendor evaluations.
Using Censinet RiskOps™ for Risk Management
Putting this framework into action can be complex, but tools like Censinet RiskOps™ make it much easier. This platform automates vendor risk assessments, reducing manual work and providing continuous visibility across the intricate 5G ecosystem. It allows healthcare organizations to conduct detailed security questionnaires, validate vendor-provided evidence, and monitor risks continuously - moving beyond the outdated approach of annual, point-in-time reviews.
With Censinet AITM™, third-party risk assessments become faster and more efficient. Vendors can complete security questionnaires in seconds, while the platform automatically summarizes their documentation, highlights key product integration details, and identifies fourth-party risk exposures. The platform’s command center offers real-time risk visualization, helping security teams pinpoint which vendors pose the highest threats to patient safety. This centralized, proactive approach is especially important in 5G environments, where multiple vendors - ranging from network providers to AI analytics companies - must be monitored simultaneously.
Risk Scoring Matrix for Patient Safety
Not all vendor risks are created equal, especially when it comes to their impact on patient care. Healthcare organizations should adopt a risk scoring system that ties vendor vulnerabilities directly to potential clinical outcomes. This matrix should evaluate factors like:
For example, vendors managing systems that affect patient monitoring, diagnostic equipment, or emergency response should be prioritized. A 5G-connected infusion pump vendor, for instance, would score higher on the risk scale compared to a vendor providing administrative software. This patient-focused scoring ensures that security resources are directed where they matter most - protecting the critical aspects of care delivery and supporting the overarching mission of healthcare organizations.
sbb-itb-535baee
Solutions for Secure 5G Healthcare Deployments
Reducing IoT and Device Risks
With the expansive connectivity brought by 5G, healthcare organizations face increased vulnerabilities, especially from IoT devices. Addressing these risks starts with adopting a Zero-Trust Architecture. This approach assumes no user, device, or application is trustworthy until thoroughly verified. It incorporates continuous identity authentication, least privilege access, and dynamic controls while segmenting networks to isolate critical devices. For instance, a 5G-connected infusion pump should operate on a separate network segment from administrative systems, minimizing potential damage if one segment is compromised [3][11].
Strong authentication practices are also non-negotiable. By deploying unified Identity and Access Management (IAM) and Multi-Factor Authentication (MFA), healthcare organizations can eliminate outdated access privileges and ensure devices are registered using trusted hardware. This is vital, especially considering incidents like the FDA's 2017 recall of half a million pacemakers due to vulnerabilities that allowed hackers to drain batteries or manipulate heartbeats [11].
Another critical step is centralized patch management, which ensures timely updates across devices, even older ones that are harder to upgrade. This requires cooperation among multiple stakeholders [11]. Coupling patch management with robust data encryption - both at rest and in transit - adds another layer of protection. Even if attackers breach the network, encrypted patient data remains unreadable [3][11]. Real-time monitoring and distributed security tools provide the visibility needed to counter threats from technologies like multi-access edge computing (MEC) and Device-to-Device (D2D) connections. Together, these measures strengthen device-level security and set the stage for broader infrastructure oversight.
Improving Visibility into Vendor-Managed Infrastructure
The intricate 5G infrastructure, built by multiple vendors and reliant on cloud, virtualization, and software-defined networking, introduces significant supply chain risks [10]. To address this, healthcare organizations must establish clear contractual security baselines. These agreements should outline security requirements, incident response protocols, and compliance standards before vendors are entrusted with critical infrastructure.
Shared monitoring tools can help eliminate blind spots between healthcare organizations and their vendors. Instead of relying solely on vendor reports, organizations should implement continuous monitoring of external interfaces [12]. Explicit Service Level Agreements (SLAs) are also essential, covering metrics like response times for security incidents, patch deployment schedules, and audit rights. These measures allow healthcare organizations to independently verify vendor security practices. Considering healthcare data is valued at approximately $408 per record - making it 50 times more valuable than data in other industries [2] - these protections are indispensable for safeguarding patient information.
Using Platforms to Streamline Risk Management
Managing the sprawling 5G vendor ecosystem manually is no longer practical. Centralized platforms offer a solution by simplifying risk management. Tools like Censinet RiskOps™ provide integrated governance and automated assessments, ensuring security at scale. Its centralized command center allows security teams to monitor a wide array of vendors, from network providers to AI analytics companies, all through a single interface.
These platforms address the expanding attack surface that comes with each new connected device or vendor relationship. The inclusion of a human-in-the-loop approach ensures that automation enhances, rather than replaces, critical decision-making. This balance helps maintain oversight while improving operational efficiency, making it easier for healthcare organizations to manage risks in an increasingly complex 5G environment.
Conclusion
The arrival of 5G is reshaping healthcare in profound ways - enabling breakthroughs like remote surgeries and real-time patient monitoring. However, it also introduces new security risks that require immediate attention and robust management strategies [3]. With virtualization, cloud-based services, and multi-vendor ecosystems expanding the attack surface, healthcare organizations must rethink their approach to vendor risk management.
Unchecked vulnerabilities pose a direct threat to patient care [3]. Traditional, manual methods simply can't keep pace with the complexity of modern healthcare environments. That's where solutions like Censinet RiskOps™ come into play, offering automated tools for real-time risk tracking and continuous trust evaluation. By providing centralized oversight and supporting human decision-making, these tools help protect sensitive patient data and streamline risk management across entire vendor portfolios [3].
To address these challenges, healthcare organizations need to move beyond outdated practices. Adopting a Zero-Trust framework, establishing stringent vendor security standards, and implementing continuous monitoring of 5G infrastructure are essential steps to ensure both security and patient safety.
FAQs
How does 5G impact patient safety in healthcare?
5G is reshaping healthcare by making real-time remote monitoring, telemedicine, and quick data sharing possible, all of which have the potential to elevate patient care and safety. Imagine doctors monitoring patients from miles away with almost no delay or critical medical data being shared instantly during emergencies - this technology is opening doors to faster, more efficient healthcare solutions.
But with these advancements come challenges. The expanded connectivity of 5G increases the risk of cyberattacks and potential network failures, which could jeopardize life-saving equipment or services. To address these vulnerabilities, healthcare organizations need to prioritize robust cybersecurity strategies to protect sensitive patient information and maintain uninterrupted operations.
What are the key security risks of using 5G in healthcare?
The integration of 5G in healthcare brings undeniable advancements, but it also opens the door to new security challenges. With an increase in connected devices and more intricate infrastructures, the risk of cyber threats grows. These threats include data breaches, ransomware attacks, and DDoS incidents, all of which can disrupt operations and compromise sensitive information.
Another concern is the massive amount of data generated by IoT devices. If these devices lack proper security protocols or are poorly managed, patient privacy can be at serious risk. Weak links in the supply chain and flaws in network components further amplify these vulnerabilities, potentially exposing critical patient data.
To protect healthcare systems, it's essential to establish strong security protocols. This includes conducting regular vendor risk assessments, securing IoT devices, and reinforcing network defenses to keep sensitive information safe.
How can healthcare organizations manage vendor risks effectively in a 5G-powered environment?
To tackle vendor risks in a 5G-driven healthcare environment, adopting a zero-trust security model is essential. This approach continuously evaluates trust based on factors like user behavior, device integrity, and network activity. Key actions include implementing real-time monitoring, applying precise access controls, and ensuring complete visibility into network traffic to mitigate potential vulnerabilities.
Securing private 5G and LTE networks is another critical step. Isolating essential medical devices from broader networks and performing regular security assessments can significantly reduce risks. Additionally, healthcare organizations must stay aligned with data privacy regulations and leverage advanced cybersecurity tools to address the broader attack surface that 5G technologies bring. These strategies are vital for protecting patient data and maintaining a secure healthcare ecosystem.
Related Blog Posts
- How to Secure Healthcare Supply Chains in 2025
- Building Vendor Risk Frameworks for Healthcare IT
- Patient Safety and Vendor Risk: The Hidden Threats Healthcare Organizations Must Address
- Edge Computing in Healthcare: Vendor Risk Management for Distributed Processing
Key Points:
What are 5G healthcare applications?
- Telemedicine: High-definition video conferencing and real-time data transmission enable remote consultations and diagnoses.
- Remote Surgery: Low latency allows surgeons to perform precise operations from remote locations.
- Real-Time Monitoring: Continuous data transmission from wearable devices supports chronic disease management and early detection of health issues.
- Connected Ambulances: Real-time communication between paramedics and hospitals ensures faster, more effective emergency care.
- Wearable Devices: 5G-powered wearables provide real-time health data, improving preventive care and patient monitoring.
Why is vendor risk management critical in 5G healthcare?
- Network Security: Protects against cyberattacks and unauthorized access to sensitive patient data.
- Data Privacy: Ensures compliance with privacy regulations like HIPAA and HITECH.
- Operational Continuity: Mitigates risks from vendor failures or system disruptions, ensuring uninterrupted healthcare services.
- Interoperability: Addresses challenges in integrating diverse IoT devices and medical systems.
What are the main risks in 5G healthcare networks?
- Cybersecurity Threats: Increased attack surface due to the proliferation of IoT devices and connected systems.
- Data Breaches: Vulnerabilities in network security can expose sensitive patient information.
- Interoperability Challenges: Integrating diverse devices and systems can create security gaps.
- IoT Vulnerabilities: Medical devices connected to 5G networks are susceptible to malware and unauthorized access.
How can healthcare organizations address 5G vendor risks?
- Vendor Assessments: Evaluate vendor security practices, compliance history, and risk profiles.
- Zero-Trust Architecture: Implement continuous identity verification and fine-grained access controls.
- Continuous Monitoring: Use tools like Censinet RiskOps™ to track vendor risks and ensure compliance.
- Incident Response Plans: Develop and test protocols for responding to security breaches or system failures.
What role does compliance play in 5G healthcare?
- Regulatory Adherence: Ensures compliance with HIPAA, HITECH, and other regulations to protect patient data.
- Vendor Accountability: Business Associate Agreements (BAAs) ensure vendors adhere to security and privacy standards.
- Trust and Transparency: Compliance fosters trust among patients and stakeholders by demonstrating a commitment to data security.
What are the benefits of 5G in healthcare?
- Faster Data Transfer: Enables real-time communication and collaboration among healthcare providers.
- Low-Latency Telemedicine: Improves the quality and accessibility of remote consultations.
- Enhanced Remote Surgery: Allows surgeons to perform precise operations from remote locations.
- Real-Time Monitoring: Supports continuous patient monitoring and early detection of health issues.
- Operational Efficiency: Streamlines workflows and enhances collaboration across healthcare systems.


