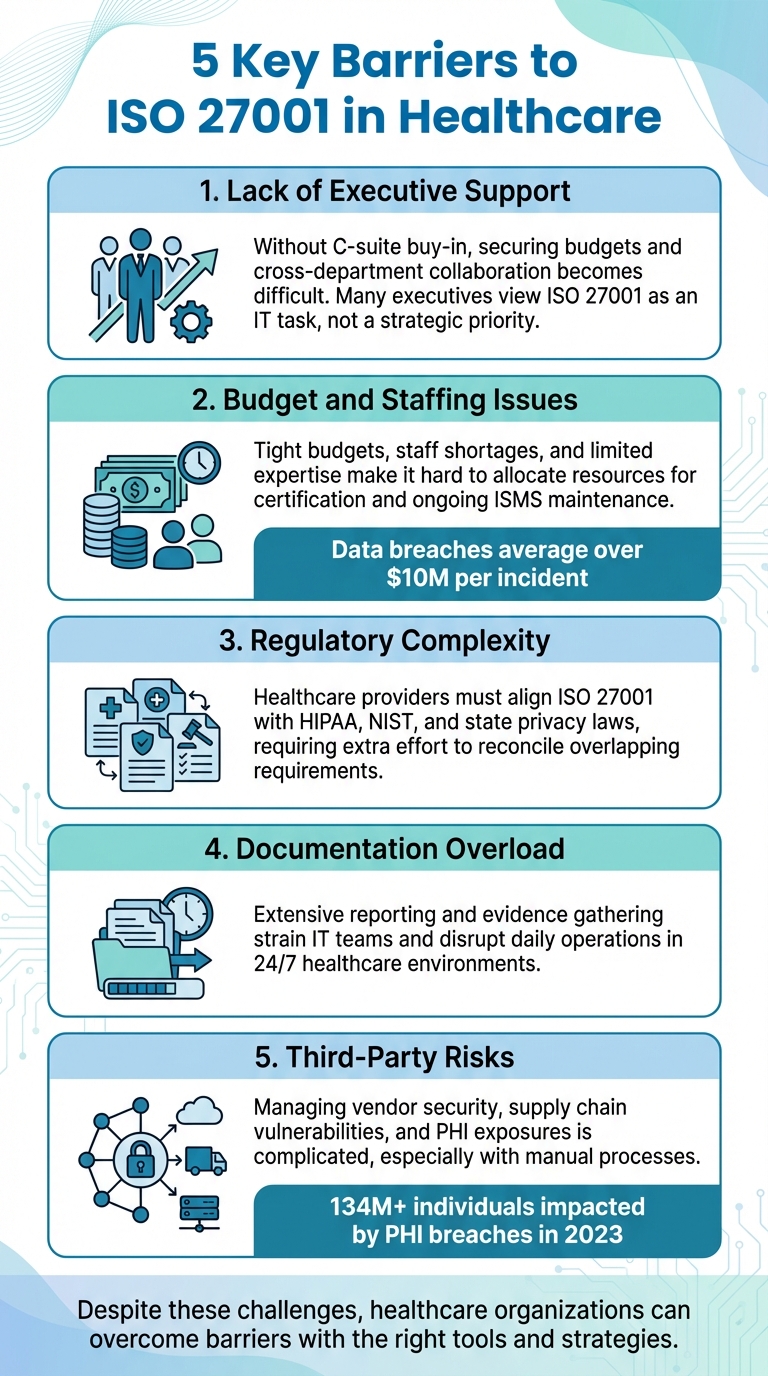
Top 5 Barriers to ISO 27001 in Healthcare
Post Summary
ISO 27001 helps healthcare organizations protect sensitive data like PHI and EHRs by establishing a structured security framework. However, many U.S. healthcare providers face significant challenges when pursuing certification. Here’s a quick overview of the five biggest barriers:
- Lack of Executive Support: Without leadership buy-in, securing budgets and cross-department collaboration becomes difficult. Many executives see ISO 27001 as an IT task, not a broader organizational priority.
- Budget and Staffing Issues: Tight budgets, staff shortages, and limited expertise make it hard to allocate resources for certification and ongoing ISMS maintenance.
- Regulatory Complexity: Healthcare providers must align ISO 27001 with frameworks like HIPAA, NIST, and state privacy laws, requiring extra effort to reconcile overlapping requirements.
- Documentation Overload: Extensive reporting and evidence gathering can strain IT teams and disrupt daily operations.
- Third-Party Risks: Managing vendor security, supply chain vulnerabilities, and PHI exposures is complicated, especially with manual processes.
These challenges make ISO 27001 adoption tough but not impossible. Tools like Censinet RiskOps™ can simplify risk assessments, automate workflows, and reduce manual effort, enabling healthcare providers to strengthen security while maintaining focus on patient care.
5 Key Barriers to ISO 27001 Certification in Healthcare Organizations
1. Missing Executive Support and Organizational Alignment
Executive support is the backbone of ISO 27001 success. Without consistent commitment from the C-suite and board, healthcare organizations face an uphill battle securing the budget, staff time, and cross-departmental cooperation required to establish and maintain an Information Security Management System (ISMS). With data breaches in the U.S. averaging over $10 million per incident[3][4], this is an issue that demands leadership’s attention. Unfortunately, many healthcare executives still view ISO 27001 as just another IT project, rather than a strategic initiative that safeguards patient safety, ensures operational continuity, and strengthens regulatory compliance.
Beyond leadership challenges, internal misalignment can derail progress. ISO 27001 implementation requires collaboration across multiple departments - IT, security, compliance, clinical operations, supply chain, and vendor management. When these teams operate in silos or when clinical leaders fail to see how the ISMS directly supports patient care, the process grinds to a halt.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."[1]
Using data to build a strong business case is key to securing executive buy-in and aligning stakeholders around shared security goals.
Framing ISO 27001 in terms that resonate with executives is critical. Highlighting benefits like reduced downtime, minimized breach impact, faster vendor onboarding, and improved regulatory readiness can make a compelling case. Demonstrating how ISO 27001 controls align with existing frameworks like the HIPAA Security Rule or NIST Cybersecurity Framework shows that the ISMS simplifies compliance rather than adding complexity[3][6]. Tools such as Censinet RiskOps™ can further support this effort by centralizing risk assessments, providing leadership-friendly dashboards, and fostering collaboration across IT, security, and clinical teams. This structured approach helps secure long-term, measurable support.
Keeping executive sponsorship alive requires ongoing engagement. Assigning clear accountability for risk ownership and control implementation is essential. Use business-focused metrics - like avoided breach costs or reduced downtime - to keep leadership invested.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."[1]
Efficiency gains like these provide the ROI executives need to remain committed to ISO 27001 throughout its lifecycle.
Lastly, education plays a crucial role. Many leaders mistakenly believe ISO 27001 duplicates HIPAA or is purely a technical certification. Addressing these misconceptions and linking the ISMS to patient safety and operational continuity helps clinical and operational leaders see their role in the initiative[2][3]. When everyone understands that ISO 27001 is a management system designed to protect patients and operations, alignment naturally follows.
2. Budget Limitations, Staff Shortages, and Skills Gaps
Healthcare organizations often grapple with three major hurdles - tight budgets, staffing shortages, and skills gaps - that make adopting ISO 27001 a tough challenge. Despite facing some of the highest data breach costs across industries, many healthcare organizations still allocate insufficient resources to information security compared to their risk levels[3][4]. When security is viewed as just another expense rather than a strategic priority, securing the funds and personnel needed to establish and maintain an ISMS becomes a daunting task. These constraints weigh heavily on the budgeting process for ISO 27001 adoption.
Budget constraints cover both direct and indirect costs. Direct costs include certification audits, consulting fees, and technology upgrades, while indirect expenses come from staff time, training, and ongoing monitoring efforts. Smaller clinics and physician groups often see ISO 27001 as a luxury unless a major contract or partner requires it[5]. Larger health systems might have bigger budgets, but they too face competing IT priorities and remain underfunded relative to their exposure to risks[3][4]. To create a practical budget, organizations must account for both types of costs and position ISO 27001 as a strategic investment. This approach can help address multiple regulatory requirements - such as HIPAA, state privacy laws, and payer security assessments - through a single, unified framework[3][6].
Staffing shortages further complicate the situation. Many healthcare organizations operate with small IT teams, often relying on one or two generalists or outsourced providers who lack dedicated security or compliance expertise[5]. Even larger systems with established security teams struggle to allocate resources for ISO 27001 projects and ongoing maintenance[2]. For example, conducting risk assessments alone requires significant staff time. Tower Health tackled this issue by using Censinet RiskOps, which allowed CISO Terry Grogan to shift 3 full-time employees (FTEs) to other critical tasks while the remaining 2 FTEs managed a higher volume of risk assessments more effectively.
The skills gap only makes things harder. ISO 27001 implementation requires specialized knowledge in areas like risk management, security controls, audit preparation, and documentation - skills that many healthcare IT teams don’t have. Regular training is essential to stay compliant and keep up with evolving threats[2], but training budgets are often the first to be trimmed. Censinet RiskOps™ addresses this issue by automating and centralizing tasks like third-party and enterprise risk assessments, cybersecurity benchmarking, and risk management collaboration tailored to healthcare organizations and vendors[2]. By streamlining workflows for PHI, clinical applications, medical devices, and supply chain risks, the platform reduces the need for specialized expertise and minimizes the hands-on time required. This makes it easier for resource-limited organizations to maintain a functional ISMS and prepare audit-ready documentation efficiently.
Despite these challenges, healthcare organizations can still make progress by adopting targeted strategies. Overcoming budget, staffing, and skills constraints requires a mix of strategic advocacy and practical tools. Cybersecurity benchmarking can help identify resource gaps and build a case for funding. As Brian Sterud, CIO of Faith Regional Health, explained:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."[1]
To secure ongoing executive support, tie ISO 27001 funding to measurable business outcomes, such as avoiding breach costs, reducing downtime, and speeding up vendor onboarding. Organizations can also explore on-demand risk management services to expand their security capabilities without committing to permanent staff or budget increases. These approaches allow healthcare providers to work within their current resource limits while steadily moving toward ISO 27001 certification.
3. Complex Regulatory and Framework Requirements
Healthcare organizations in the U.S. face a uniquely challenging regulatory environment when it comes to implementing ISO 27001. Unlike other industries, these organizations must align ISO 27001 with mandatory frameworks such as HIPAA, HITECH, state privacy and breach laws, CMS conditions of participation, and in some cases, 42 C.F.R. Part 2 and FTC rules [3][6]. While ISO 27001 is a voluntary standard, it cannot be implemented in isolation - it must be carefully mapped to these existing legal and regulatory obligations [3][6]. This requires significant effort to demonstrate how a single Information Security Management System (ISMS) can address multiple, and sometimes conflicting, requirements.
One of the key challenges lies in the overlap between HIPAA and ISO 27001. HIPAA specifically addresses protected health information (PHI) and mandates certain safeguards, while ISO 27001 takes a broader, risk-based approach to managing all information assets [3][6]. While many HIPAA Security Rule standards align with ISO 27001 controls, there are notable gaps - particularly in areas like the maturity of risk management processes and the continuous improvement model central to ISO 27001 [6]. To address this, organizations must create a formal crosswalk that maps HIPAA requirements to ISO 27001 controls (including Annex A) to clearly identify and manage compliance gaps [6].
The challenge grows when additional frameworks come into play. Many U.S. healthcare providers already follow the NIST Cybersecurity Framework or NIST SP 800-53, making it essential to reconcile NIST, HIPAA, and ISO 27001. This involves eliminating duplicate controls and resolving conflicting terminology [6]. On top of that, organizations must adapt to evolving regulations, such as OCR HIPAA guidance, new state privacy laws, and changing expectations around medical device and cloud security, which require ongoing updates to ISO 27001 programs [3][4].
Fortunately, targeted solutions are available to help navigate this complexity. Purpose-built platforms like Censinet RiskOps™ have been designed specifically for healthcare, offering workflows that align ISO 27001 with U.S. healthcare regulations. These platforms streamline risk management for patient data, PHI, clinical applications, medical devices, and supply chains, all within a single framework. By centralizing risk assessments and documentation, healthcare organizations can position their ISMS as a unified governance layer that integrates HIPAA, NIST, CMS, and vendor risk requirements. This eliminates the need for multiple, disconnected compliance programs and allows teams to operate from a single, cohesive set of controls [3][6].
Given the intricate regulatory environment, a unified approach to ISO 27001 is crucial. This means treating ISO 27001 not as an additional compliance burden but as a framework that ties together various regulatory requirements under one umbrella. To achieve this, organizations should establish a joint working group that includes the CISO, Privacy Officer, and Compliance/Legal teams. This group can interpret overlapping requirements, resolve conflicts across frameworks, and document how each ISO 27001 control corresponds to specific regulations (e.g., HIPAA 164.308(a)(1)). This approach simplifies audits and external reviews while ensuring alignment [3][6].
It’s important to remember that HIPAA compliance alone does not equal ISO 27001 certification. ISO 27001 demands more - demonstrable governance, robust risk management, and a commitment to continuous improvement that goes beyond HIPAA’s minimum requirements [3][6]. By using structured control mapping and leveraging the right tools, healthcare organizations can transform regulatory complexity into an opportunity to strengthen their security posture and governance framework.
sbb-itb-535baee
4. Documentation Requirements and Operational Continuity Issues
Meeting ISO 27001 standards demands extensive documentation, which can stretch the already limited resources in healthcare settings. Hospitals and health systems must maintain formal policies, procedures, risk registers, treatment plans, audit logs, and evidence of continuous monitoring for their information assets. This includes patient data, PHI, clinical applications, and medical devices. For organizations operating 24/7, this creates a constant flow of documentation that can interfere with daily operations, potentially affecting system uptime and incident response.
The problem isn’t just the sheer volume of documentation - it’s the impact on operational continuity. IT and security teams often have to divert their attention from core responsibilities to manage records and gather evidence, increasing the risk of disruptions. For example, Tower Health implemented a healthcare-specific solution that allowed three full-time employees (FTEs) to return to their primary duties, while two FTEs handled a larger volume of risk assessments more efficiently. This highlights how manual documentation processes can drain resources that are critical for maintaining system uptime and responding to incidents effectively.
Healthcare organizations also face the challenge of aligning ISO 27001 documentation with other continuity standards, such as the CMS Emergency Preparedness Rule, Joint Commission requirements, and HIPAA contingency planning. Without careful coordination, teams risk duplicating efforts, maintaining separate policies and playbooks for cyber incidents, clinical downtime, and third-party outages. The 2022 revision of ISO 27001 has intensified this challenge by emphasizing operational resilience and structured documentation for continuity testing and recovery.
To avoid operational silos, bridging documentation with continuity strategies is essential. Purpose-built platforms designed for healthcare can significantly ease this burden. For instance, Censinet RiskOps™ consolidates third-party risk assessments, PHI data flows, and control evidence into a single platform. This streamlines ISO 27001 documentation management in complex healthcare environments. Features like automated evidence collection and shared workflows reduce manual effort, ensuring compliance without compromising patient care.
Integrating documentation efforts into broader governance strategies can also make a big difference. Unified playbooks that cover cybersecurity, risk management, and continuity planning eliminate silos and ensure that critical risk mitigation tasks - like vendor remediation or device patching - happen without unexpected downtime. This cohesive approach not only satisfies ISO 27001 requirements but also enhances an organization’s ability to maintain operations during disruptions, a necessity in the healthcare sector.
5. Third-Party, Supply Chain, and Data Ecosystem Risks
Managing third-party risks adds a layer of complexity to the already challenging cybersecurity landscape in healthcare. Hospitals and health systems often rely on a vast network of external vendors - think EHR systems, cloud providers, medical device manufacturers, billing services, and telehealth platforms. While these partnerships are essential, they also expose sensitive patient health information (PHI) to potential threats. This interconnected web of vendors poses significant cyber risks and creates hurdles for achieving ISO 27001 certification[4]. The 2022 update to ISO 27001 directly addresses these issues with controls (A.5.19 through A.5.23) that focus on defining supplier security requirements, monitoring their performance, and managing ICT supply chain security throughout the vendor relationship.
The challenge isn’t just the sheer number of vendors - it’s also the effort required to assess and monitor them effectively. Traditional methods, like manual risk assessments and spreadsheet tracking, consume extensive staff time and resources. Generic risk management tools often fall short when dealing with the unique demands of healthcare, such as managing PHI flows, clinical applications, and medical devices, all while navigating a complex regulatory environment.
Real-world examples highlight the risks. A misconfigured cloud-based patient portal could expose sensitive PHI and disrupt access to patient records. Similarly, vulnerabilities in the software of networked infusion pumps might allow unauthorized access to clinical networks. In both cases, insufficient vendor oversight or weak continuous monitoring could lead to serious weaknesses in an Information Security Management System (ISMS), noncompliance with ISO 27001, and potentially devastating clinical or reputational consequences[4]. According to the U.S. Department of Health and Human Services, business associates are responsible for a significant portion of large PHI breaches, underscoring how third-party failures can jeopardize both compliance and patient safety.
To address these risks, healthcare organizations are shifting from periodic vendor assessments to continuous monitoring strategies. This approach aligns with ISO 27001’s focus on ongoing improvement and involves moving beyond static questionnaires to embrace automated workflows, security ratings, and proactive contract management. Platforms like Censinet RiskOps™ are designed specifically for healthcare, enabling centralized third-party risk assessments, automated evidence collection, and benchmarking of vendor security against ISO 27001 and healthcare-specific standards[2].
To mitigate these risks effectively, organizations should integrate robust security requirements into business associate agreements and vendor contracts. These agreements should address critical aspects like incident reporting, encryption, data residency, and audit rights. Establishing a formal third-party risk management program with clear criteria for vendor tiers - based on their criticality and access to PHI - is equally important. Ultimately, leveraging healthcare-specific platforms that understand the intricate connections between patient data, clinical systems, and supply chains is essential. Even when data processing is outsourced, the responsibility for data security remains firmly with the organization, and demonstrating comprehensive supplier risk management is crucial for ISO 27001 compliance.
Conclusion
The five hurdles - lack of executive support, limited budgets and staffing, complex regulations, documentation overload, and third-party risks - can make ISO 27001 certification feel like an uphill battle for many U.S. healthcare organizations. In 2023, over 134 million individuals were impacted by breaches involving unsecured PHI, highlighting the pressing need for stronger security frameworks to safeguard patient data and ensure continuity of care[7]. When implemented alongside healthcare-focused frameworks like HIPAA and NIST CSF, ISO 27001 can bolster cyber resilience and demonstrate the due diligence necessary to reduce regulatory penalties in the event of a breach[3]. Addressing these challenges requires a tailored strategy that not only ensures compliance but also enhances operational resilience.
Healthcare organizations need specialized solutions to navigate these barriers effectively. Purpose-built platforms like Censinet RiskOps™ simplify the complexities of healthcare risk management by automating third-party and enterprise risk assessments, streamlining evidence collection, and enabling benchmarking aligned with healthcare standards[2]. These tools are already delivering tangible results. For example, Terry Grogan, CISO at Tower Health, shared that "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required"[1]. Baptist Health eliminated the need for spreadsheets while gaining access to a larger collaborative network of hospitals, and Faith Regional Health leveraged benchmarking to secure critical resources[1]. These success stories show how the right platform can transform ISO 27001 from an intimidating challenge into a manageable and effective standard.
This effort goes beyond checking compliance boxes - it's about building the cyber resilience necessary to protect patient safety in an increasingly digital healthcare landscape. By integrating ISO 27001's structured governance with tools designed specifically for healthcare, organizations can better manage risks tied to PHI, clinical systems, medical devices, and supply chains. The investment in modern risk management platforms not only reduces breach costs and strengthens vendor oversight but also helps healthcare providers demonstrate robust security practices to regulators, patients, and partners alike.
FAQs
What strategies can healthcare organizations use to gain executive support for ISO 27001 certification?
To secure executive backing for ISO 27001 certification, healthcare organizations should focus on its role in minimizing cybersecurity risks, meeting regulatory requirements, and protecting patient data. Highlighting measurable benefits - like potential cost reductions and alignment with industry standards - can effectively showcase the strategic advantages of adopting ISO 27001.
Tying the certification effort to broader organizational objectives, such as boosting operational efficiency or building patient trust, can also make a compelling case. Sharing examples of success from similar organizations and keeping leadership informed about evolving cybersecurity threats through regular education can further solidify their support. Ultimately, showing how ISO 27001 helps ensure long-term risk management and strengthens operational stability is crucial to gaining buy-in.
How can healthcare providers align ISO 27001 with regulations like HIPAA and NIST?
Healthcare providers can align ISO 27001 with regulations like HIPAA and NIST by adopting a risk-based approach that merges controls from all these frameworks. A good starting point is mapping the Annex A controls in ISO 27001 to HIPAA’s Security Rule and the NIST Cybersecurity Framework. This helps pinpoint overlaps and uncover any gaps that need attention.
By performing regular risk assessments, organizations can stay compliant while efficiently prioritizing mitigation efforts. Specialized healthcare cybersecurity platforms can make this process smoother by offering real-time monitoring, minimizing redundant tasks, and ensuring policies meet regulatory standards. This method not only simplifies compliance but also enhances security measures and reinforces trust with both regulators and patients.
How does ISO 27001 help healthcare organizations manage risks from third-party vendors?
ISO 27001 offers a clear framework for managing risks tied to third-party vendors in the healthcare sector. It requires organizations to thoroughly evaluate the security practices of their vendors, ensuring they meet the necessary standards to safeguard sensitive information, including patient data and PHI (Protected Health Information).
The framework prioritizes ongoing monitoring and collaboration, enabling healthcare organizations to tackle potential vulnerabilities in their supply chain and clinical operations before they become serious issues. Tools such as Censinet RiskOps™ make this process easier by streamlining risk assessments and providing a more efficient way to manage cybersecurity risks across various vendors and partners.


