Best Practices for Third-Party Incident Response
Post Summary
Third-party cybersecurity incidents can disrupt patient care, expose sensitive data, and create compliance challenges for healthcare organizations. Managing these risks requires clear governance, strong vendor relationships, and effective recovery strategies. Here's a quick breakdown of key practices:
- Governance: Define roles using frameworks like NIST CSF and HHS Cybersecurity Performance Goals. Use tools like RACI matrices to assign responsibilities for detection, containment, and recovery.
- Vendor Contracts: Ensure agreements cover breach notifications, evidence sharing, and recovery timelines. Include "kill switch" clauses for compromised vendor access.
- Risk Prioritization: Focus resources on critical vendors tied to patient care and sensitive data. Use platforms like Censinet RiskOps™ to centralize vendor risk management.
- Incident Response Plans: Collaborate with vendors on detailed playbooks for ransomware, data breaches, and system outages. Regularly test and refine these plans through simulations.
- Clinical Continuity: Prepare backup workflows for critical systems, train staff in downtime procedures, and prioritize patient safety during disruptions.
- Detection & Containment: Monitor vendor activity for anomalies and act quickly to isolate threats. Use multi-layered monitoring and maintain detailed documentation for compliance.
- Recovery & Improvement: Restore systems with updated safeguards, communicate clearly with stakeholders, and conduct thorough post-incident reviews to strengthen defenses.
These steps help healthcare organizations protect patient care, meet regulatory requirements, and respond efficiently to third-party incidents.
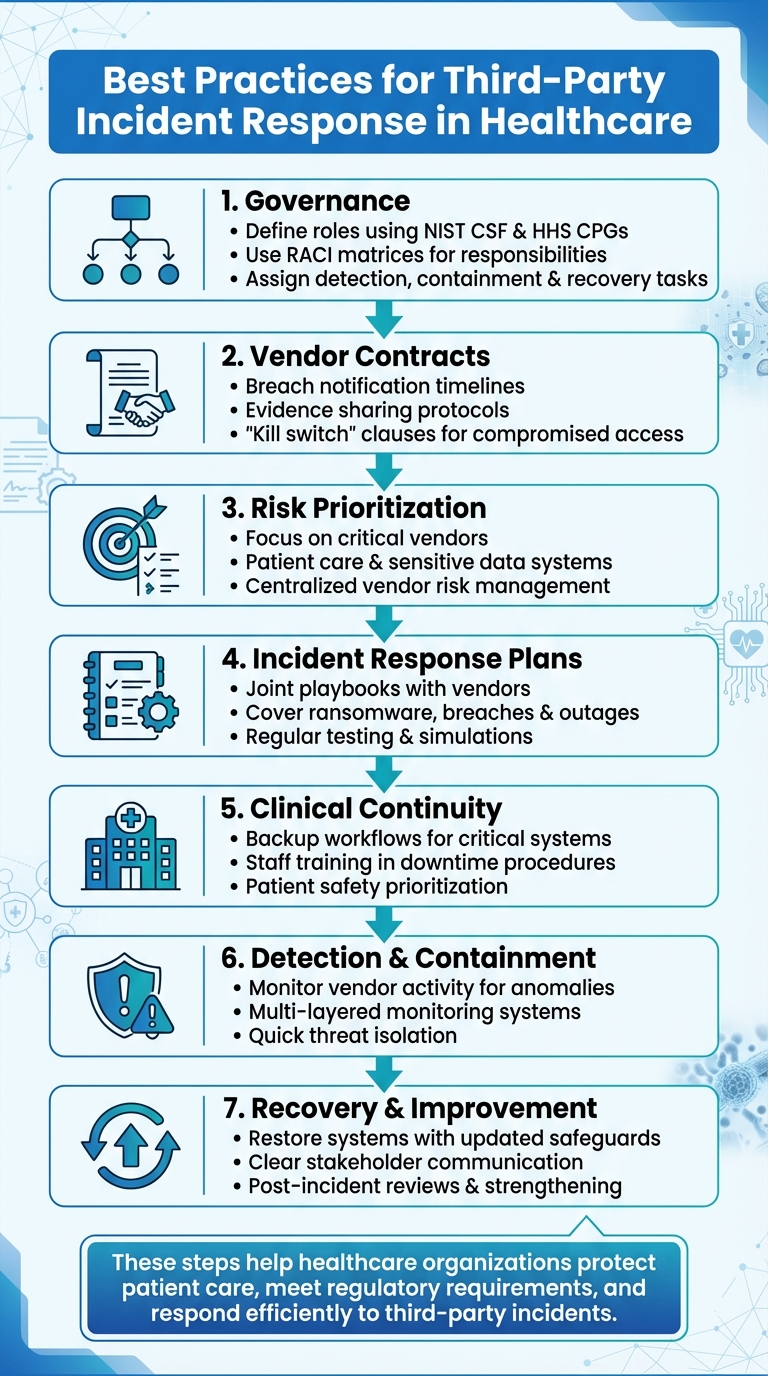
7-Step Third-Party Incident Response Framework for Healthcare Organizations
Setting Up Governance and Clear Responsibilities
When it comes to handling third-party incidents, having a well-defined governance structure is critical. Without clear responsibilities, organizations risk delays, missed regulatory deadlines, and confusion during high-stakes situations. According to the 2025 KLAS Healthcare Cybersecurity Benchmarking Study, healthcare organizations tend to excel in the "Respond" function - covering incident procedures, mitigation tactics, and communication - but often fall short in long-term recovery and business continuity efforts [4]. This highlights the need for a governance framework that not only addresses immediate responses but also supports sustained recovery. A crucial step in this process is clearly defining roles and responsibilities.
Defining Roles and Responsibilities
To establish effective governance, organizations should align incident response roles with NIST CSF 2.0 and the HHS 405(d) HPH Cybersecurity Performance Goals (HPH CPGs). These frameworks are widely adopted by U.S. healthcare organizations to set governance standards, assign responsibilities, and measure the maturity of their incident response and third-party risk management processes [4][7]. The American Hospital Association has emphasized that the HHS Cybersecurity Performance Goals help counter common third-party attack methods [7].
A RACI matrix is a practical tool to clarify who is Responsible, Accountable, Consulted, and Informed for various tasks like detection, triage, containment, forensics, regulatory reporting, patient communication, legal discussions, and recovery when a vendor is involved in an incident. This matrix should extend to third-party responsibilities for each NIST CSF function - Identify, Protect, Detect, Respond, and Recover. It’s also essential to include business continuity and clinical safety criteria, ensuring that decisions factor in patient safety alongside IT risk [4].
Contract and Regulatory Requirements
Once roles are defined, formal agreements need to solidify breach response expectations. Contracts and Business Associate Agreements (BAAs) should outline critical details such as breach notification timelines, evidence-sharing protocols, fourth-party risk responsibilities, and rights to suspend access during incidents. A 2025 review by AccountableHQ highlighted that third-party compromises remain one of the top breach vectors, pushing regulators and payers to demand stronger third-party risk management practices. These include vendor kill switches and robust BAAs [10]. Clear agreements should also specify responsibilities for service restoration and, where applicable, compensation [10]. Additionally, organizations should categorize vendors based on data sensitivity and connectivity, and ensure BAAs enforce appropriate controls tailored to each vendor's risk level. These contractual measures not only enhance accountability but also strengthen the overall incident response framework.
Centralized Risk Management Platforms
To streamline incident response, a centralized platform can consolidate vendor profiles, incident obligations, and historical records. For example, Censinet RiskOps™ serves as a cloud-based risk exchange, facilitating secure collaboration among healthcare delivery organizations (HDOs) and more than 50,000 vendors and products. Terry Grogan, CISO at Tower Health, shared that using Censinet RiskOps allowed the organization to reassign 3 full-time employees to other tasks while still increasing the number of risk assessments conducted with just 2 full-time employees [1]. Similarly, James Case, VP & CISO at Baptist Health, noted that adopting Censinet RiskOps eliminated the need for spreadsheets in risk management and opened opportunities for collaboration with a broader network of hospitals [1]. By centralizing vendor data and contractual obligations, organizations can ensure that critical governance information is readily available during an incident, enabling faster and more coordinated responses.
Planning for Incident Response
Being prepared can mean the difference between a minor hiccup and a full-on crisis. For healthcare organizations, this means working closely with vendors to create incident response plans. These plans should align with established frameworks like the NIST CSF "Respond/Recover" functions and the HHS Cybersecurity Performance Goals [4]. The American Hospital Association has pointed out that many major attacks on health systems now stem from third parties and supply chain partners, making teamwork essential to safeguard patient data [7].
The latest 2025 healthcare cybersecurity guidance acknowledges a stark reality: breaches and vendor-related incidents are no longer "if" scenarios but "when." This shift has placed a greater emphasis on rapid detection, coordinated responses with vendors, and resilience-focused strategies [5]. These plans are not just about compliance - they're about ensuring clinical safety and protecting sensitive information. With this groundwork in place, organizations can move on to more specific strategies.
Creating Joint Playbooks
Joint playbooks turn broad policies into actionable, vendor-specific plans for handling incidents like ransomware attacks or data breaches. These playbooks should clearly outline roles, detection triggers, escalation procedures, containment steps, evidence preservation, notification protocols, and recovery processes. For instance, a playbook might specify when to escalate an issue, who to notify, and the exact steps for system recovery.
Testing these playbooks is critical. Joint exercises, such as simulating cloud compromises or supply chain attacks, can help refine the plans and ensure they’re effective [4]. These exercises also highlight areas where continuity across vendor services needs to be prioritized.
Risk-Based Vendor Prioritization
Not every vendor requires the same level of incident response preparation. Healthcare organizations should map vendor services to clinical workflows and establish acceptable downtimes for each service [5]. By categorizing vendors based on factors like data sensitivity, system criticality, and connectivity, organizations can pinpoint which vendors need more detailed playbooks and rigorous testing.
Prioritizing vendors based on risk helps focus resources where they’re needed most - on those whose failure could jeopardize patient safety or lead to major regulatory challenges. Tools like Censinet RiskOps™ can assist in this process by maintaining detailed vendor profiles that capture these risk factors.
Maintaining Clinical Continuity
Ensuring clinical continuity starts with an impact analysis to identify critical systems needed for patient care and to determine maximum tolerable downtimes. For these systems, organizations should develop backup procedures, such as using paper order sets or manual record-keeping, and train staff through regular drills [2][3].
Joint testing with vendors should include simulations of full or partial system outages. These exercises help ensure clinicians can access essential information, reconcile orders and results once systems are restored, and monitor patient safety risks during disruptions. Recovery plans must also address data reconciliation to avoid errors [3]. According to the KLAS 2025 Healthcare Cybersecurity Benchmarking Study, while many organizations excel in mitigating incidents and maintaining clear communication protocols, "recovery plan execution is an area for improvement." This underscores the need to better integrate incident response with broader business and clinical continuity efforts [4].
Detection, Containment, and Triage
When it comes to incident response, the ability to detect and contain vendor-related issues quickly is essential to safeguarding patient care. The moment an incident occurs, identifying, analyzing, and containing it promptly is crucial. This requires a combination of robust monitoring systems, rapid triage, and decisive action.
Coordinated Monitoring
Detecting vendor incidents starts with multi-layered monitoring, such as SIEM alerts that flag unusual activity. These might include irregular access to PHI, strange API behavior, or unexpected data transfers. Automated systems should also pull logs from applications, databases, and endpoints to track failed logins, privilege escalations, or access during unusual hours.
But technology alone isn’t enough. Threat intelligence from sources like ISACs, HHS, FBI, and AHA provides early warnings about potential risks [7][8][9]. Additionally, empowering staff with easy-to-use phishing reporting tools can make a big difference. For example, clinicians and employees can report suspicious vendor-branded emails, feeding valuable information into incident response workflows [10].
Monitoring should also extend to API activity, endpoint behavior, and network traffic from vendor IPs. Look for red flags like unusual protocols or large data transfers, which could indicate a compromise [11]. These efforts not only help detect threats but also set the stage for effective containment.
Impact Analysis and Containment
The moment a vendor-related incident is suspected, it’s vital to assess its impact. Are critical clinical systems affected? Could patient care be at risk? Does the situation involve PHI exposure that requires HIPAA reporting [11]? Immediate communication with the incident commander and clinical leadership is crucial, especially if patient safety is on the line. This allows teams to quickly implement downtime protocols, such as switching to paper workflows or activating diversion plans [2][12].
Impact analysis should combine technical forensics, legal assessments, and clinical insights. Determining whether the incident qualifies as a reportable breach under HIPAA/HITECH involves evaluating if PHI was improperly accessed or disclosed [11]. Operational impacts must also be quantified by identifying disrupted clinical workflows and estimating the extent of the disruption. Up-to-date data-flow diagrams and asset inventories that map vendors to systems and data stores can speed up this process significantly [10].
Containment measures should be risk-based and swift. For example, disabling compromised vendor access - often referred to as a "vendor kill switch" - can protect clinical operations [10]. Temporarily shutting down non-critical vendor functions, like analytics exports, can help contain the issue while ensuring vital clinical tools remain operational. If a critical vendor platform is compromised, organizations may need to rely on downtime procedures, such as paper documentation or local failover systems, to maintain patient care [2][12]. Network segmentation and deny-by-default policies can also prevent the threat from spreading further [10].
Throughout the containment process, maintaining detailed records - such as decision logs, timelines, and chain-of-custody documentation - is essential. These records not only support regulatory compliance but also provide insights for improving future responses [10]. Using centralized platforms like Censinet RiskOps™ can streamline alert management, automate impact analysis, and ensure timely communication across teams, ultimately improving response efficiency.
sbb-itb-535baee
Recovery and Post-Incident Improvement
Once containment is achieved, the focus shifts to recovery. This phase involves restoring systems, issuing timely notifications, and analyzing lessons learned to improve future responses. According to a 2025 KLAS benchmarking study, while the NIST CSF Respond function shows strong adoption among surveyed providers, recovery and business continuity efforts continue to lag behind [4].
Remediation and Recovery Steps
Recovery efforts build on existing vendor controls, ensuring that all safeguards remain effective. Start by prioritizing patient-facing systems - like EHRs, clinical management platforms, imaging tools, order entry systems, and life-support interfaces. Before these systems are brought back online, confirm that vulnerabilities have been patched, credentials updated, and vendor environments secured [6]. Many organizations now include a "vendor kill switch" in their plans. This feature allows them to quickly isolate or disable compromised vendor connections - such as VPNs, APIs, or SSO feeds - while maintaining safe alternatives for clinical operations.
Preparation plays a huge role in recovery speed. Organizations that maintain hardened, unchangeable backups and regularly practice restoration drills are better positioned to resume care delivery during ransomware attacks or vendor outages [6][10]. Scheduled recovery exercises with key vendors can also reveal weaknesses in recovery plans and clarify roles and responsibilities before a real incident occurs [2][13].
Incident Reporting and Communication
Recovery isn’t complete without effective post-incident communication. A pre-established communications plan should outline notification protocols, approved public statements, and methods to avoid conflicting messages. Legal and compliance teams must ensure vendor reports align with HIPAA, state data breach laws, and HHS OCR requirements [10][5]. Internally, stakeholders like IT/security, clinical leadership, legal/compliance, risk management, and executive leaders need timely updates. These updates should include the incident’s status, its impact on clinical services, regulatory risks, and recovery progress [12][13].
Externally, clear and consistent messaging is critical. Patients should be informed in plain language about what happened, what data was involved, and the steps being taken to safeguard their information. This may include recommendations like credit monitoring services [11]. Regulators often require detailed reports that cover the number of individuals affected, mitigation efforts, and plans to prevent future incidents [11]. Keeping a detailed communications log - tracking who was notified, when, and with what information - helps ensure compliance and supports post-incident evaluations [10].
Post-Incident Reviews and Risk Scoring
Each incident provides an opportunity to improve defenses. A structured post-incident review should bring together teams from IT/security, clinical operations, legal, risk management, and vendor partners to evaluate what went well and what needs improvement [2][13]. Insights gained should lead to updates in vendor contracts and internal response playbooks. Documenting corrective actions, assigning clear responsibilities, and maintaining evidence like timelines and decision logs is essential to meet regulatory and legal expectations [10].
Vendor risk scores and contracts should also reflect the findings from the incident. This might involve updating BAAs and contracts to include stronger security measures, clearer breach notification timelines, and required participation in incident simulations. Tools like Censinet RiskOps™ can simplify this process by centralizing risk scoring and tracking for clinical applications, medical devices, and supply-chain vendors. These platforms enable quick updates based on new risk data. Additionally, incident insights should guide ongoing training for staff and vendors, focusing on areas like phishing, identity compromises, and third-party access vulnerabilities [10].
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO at Faith Regional Health [1].
Conclusion
Managing third-party incident response in healthcare hinges on three core principles: establishing clear governance, preparing effectively with vendors, and committing to ongoing improvement. By defining roles early, crafting shared playbooks, and regularly practicing response scenarios, organizations can better protect patient care during incidents. The 2025 KLAS cybersecurity benchmarking study highlights a critical gap - strong immediate response capabilities but weaker long-term recovery efforts - underscoring the importance of structured post-incident reviews and continuous refinement [4]. These practices lay the groundwork for using advanced platforms to streamline risk management across vendors.
Platforms designed for healthcare risk management bring vendor data into one place, speeding up responses and optimizing resources. For example, Censinet RiskOps™ simplifies vendor risk processes by automating tasks like questionnaire completion, evidence validation, and risk reporting with its AI-driven tools. Terry Grogan, CISO at Tower Health, shared that adopting this platform allowed three staff members to return to their main responsibilities while significantly boosting the number of risk assessments completed [1]. Its network connects healthcare organizations with over 50,000 vendors, facilitating the secure exchange of cybersecurity data and risk insights across patient records, clinical systems, medical devices, and supply chains [1]. By leveraging such scalable solutions, healthcare providers can continuously refine their incident response strategies.
As threats from third-party dependencies and supply chain attacks grow, incident response must remain a strategic priority - not just a technical task. Regular benchmarking ensures organizations can secure the resources they need and stay ahead of emerging risks. With the right mix of governance, preparation, and technology, every incident becomes an opportunity to strengthen defenses and protect patient care more effectively.
FAQs
What are the best ways for healthcare organizations to prioritize vendor risks?
Healthcare organizations can better manage vendor risks by regularly conducting risk assessments, particularly focusing on vendors that handle sensitive data, such as patient records, or those managing critical systems. Tools like Censinet RiskOps™ can simplify this process by pinpointing vendors with higher risk levels, allowing organizations to allocate resources more effectively while staying aligned with healthcare industry standards.
By taking these steps, organizations can minimize cybersecurity threats, safeguard patient information, and ensure smooth operations throughout their systems.
Why are joint playbooks important in managing third-party incidents?
Joint playbooks are key to managing third-party incidents with precision and teamwork. They outline specific procedures and communication guidelines, ensuring everyone involved stays on the same page during a crisis.
By setting clear expectations for roles, responsibilities, and actions ahead of time, these playbooks cut down on uncertainty and delays. This leads to quicker resolutions and helps protect critical systems, sensitive patient information, and essential operations.
Why is ongoing improvement important for managing third-party incidents?
Ongoing improvement plays a key role in managing third-party incidents, helping your organization stay ahead of constantly changing cybersecurity threats. By routinely assessing and refining your response plans, you can pinpoint vulnerabilities, close gaps, and bolster your overall risk management efforts.
Taking this proactive stance not only lowers the chances of incidents occurring but also enhances your organization’s ability to react swiftly and efficiently. This minimizes disruptions and protects essential resources, such as patient data and clinical systems.


