Best Practices for Vendor Network Monitoring in Healthcare
Post Summary
Healthcare organizations depend heavily on vendors for critical operations, but these connections also introduce significant cybersecurity risks. Without proper monitoring, vendor access can expose systems to ransomware, disrupt patient care, and lead to regulatory penalties. Here's how to manage vendor network monitoring effectively:
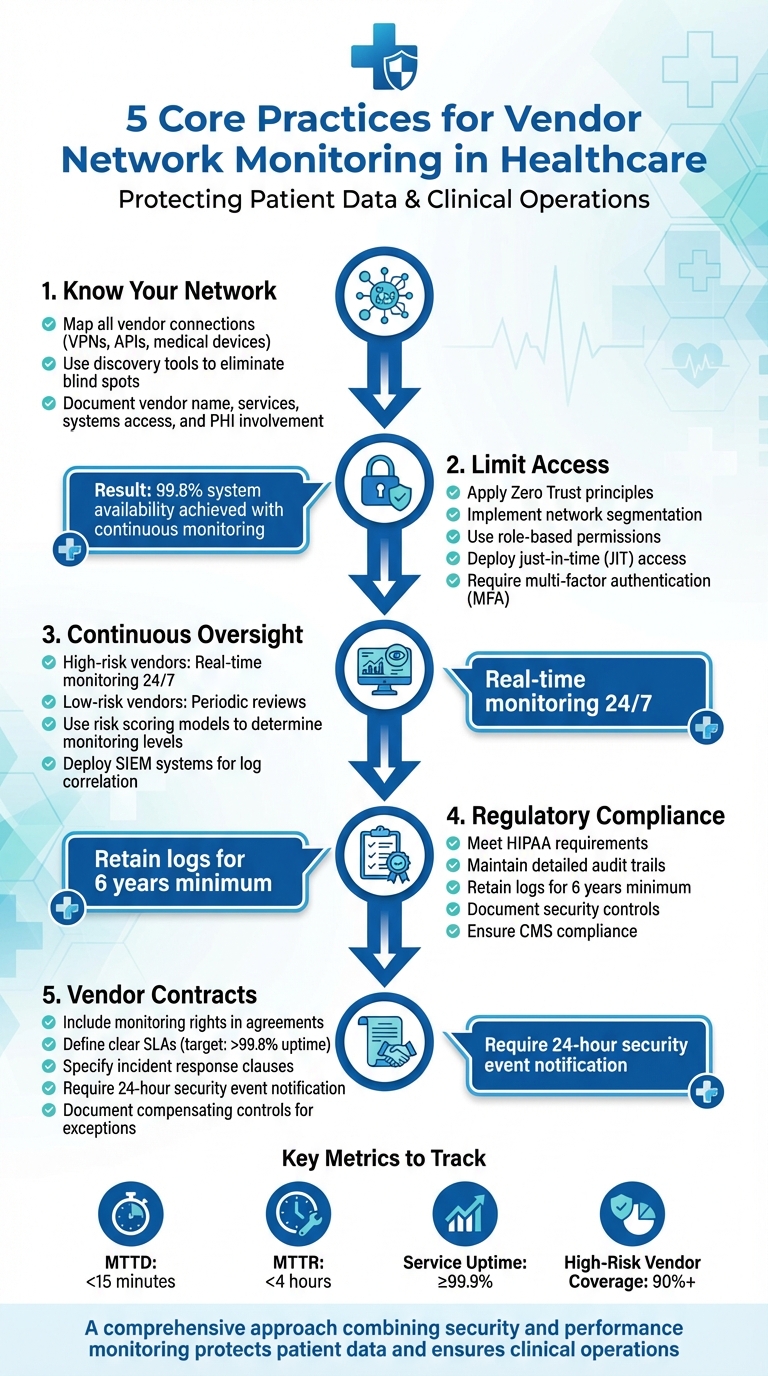
- Know Your Network: Map all vendor connections, including VPNs, APIs, and medical devices. Use discovery tools to ensure no blind spots.
- Limit Access: Apply Zero Trust principles with segmented networks, role-based permissions, and just-in-time access.
- Continuous Oversight: High-risk vendors require real-time monitoring, while low-risk ones may need periodic reviews.
- Regulatory Compliance: Meet HIPAA and CMS requirements with detailed logs, audit trails, and security controls.
- Vendor Contracts: Include monitoring rights, SLAs, and incident response clauses in agreements.
5 Core Practices for Effective Vendor Network Monitoring in Healthcare
Core Practices for Vendor Network Monitoring
Keeping a healthcare network secure and functional requires three key practices: knowing every connection to your network, limiting access to only what’s necessary, and maintaining constant oversight instead of relying on occasional reviews. These steps work together to close potential security gaps and ensure clinical systems stay up and running. Let’s break down these practices into the following core areas.
Achieving Full Network Visibility
"You cannot manage, secure, or optimize what you cannot see" [9].
Healthcare organizations need a complete view of all vendor-related connections. This includes VPNs, remote access tools, cloud services, APIs, and connected medical devices. To avoid blind spots, deploy sensors on key network devices.
For each vendor connection, document essential details - vendor name, the services they provide, systems they can access, any protected health information (PHI) involved, and the protocols they use. Storing this information in a configuration management database and automating updates with discovery tools ensures nothing is missed. Mapping data flows between your organization, vendors, and their subcontractors also helps pinpoint where sensors and logs should be placed for effective monitoring.
Here’s an example: one healthcare provider achieved 99.8% system availability by adopting continuous monitoring [3]. Hospitals often use clinical network management tools with real-time dashboards to catch issues early, like overheating network closets, and take action before patient care is disrupted. Once you’ve identified vendor connections, the next step is securing them.
Applying Zero Trust and Least Privilege Principles
Vendor traffic should be segmented into dedicated zones that allow only the necessary protocols, keeping critical systems isolated.
Use identity-based controls to require unique vendor accounts, multi-factor authentication, and role-based permissions. Implement just-in-time (JIT) access, where vendors must request temporary elevated privileges, which are approved by an internal team and automatically revoked after the task is done. Tools like privileged access management (PAM), VPNs with temporary certificates, and bastion hosts can help enforce these controls while keeping a detailed audit trail. Service accounts tied to vendor applications should have only the permissions they need, undergo regular reviews, and have their credentials rotated frequently to prevent privilege creep.
Continuous vs. Point-in-Time Monitoring
Regulatory requirements emphasize continuous oversight, but monitoring should be adjusted based on vendor risk. Not every vendor needs the same level of scrutiny. Always-on monitoring is critical for high-risk vendors - those handling large amounts of PHI, integrating with critical clinical systems, remotely accessing hospital networks, managing security infrastructure, or having a history of security issues. For these vendors, combine constant monitoring - such as traffic analysis, behavioral analytics, log collection, and real-time alerts - with scheduled security reviews.
For lower-risk vendors, periodic assessments and basic log reviews are often sufficient. A risk scoring model can help determine the appropriate level of monitoring by considering factors like data sensitivity, connectivity, business importance, and threat intelligence. As healthcare risk experts note:
"a year is a long time between reviews" [6].
To detect anomalies, use tools like firewall logs, NetFlow data, and IDS/IPS systems. For medical devices and clinical networks, specialized monitoring tools are essential to understand clinical protocols and device behavior, distinguishing normal activity from potential threats. Centralizing this data in a SIEM or similar platform allows for better correlation of information, supports compliance efforts, and helps maintain HIPAA audit trails, detailing who accessed data, when, and from where.
Building Governance and Policy Frameworks
To effectively monitor vendor networks, organizations need clear policies and well-defined responsibilities. These elements help eliminate oversight gaps and ensure compliance, creating a solid foundation for monitoring and managing vendor-related risks.
Developing a Vendor Network Monitoring Policy
A strong governance framework is key to maintaining full network visibility and continuous monitoring. This framework should align with your enterprise's security policy and risk tolerance.
The Vendor Network Monitoring Policy should outline clear objectives, such as ensuring security, availability, performance, and regulatory compliance. It must also specify required controls like logging, alerting, network segmentation, multi-factor authentication, and encryption [3][9]. For vendors with higher risk - those with direct network connections, VPN access, APIs, or medical device integration - continuous monitoring is essential, not just periodic reviews [5][6].
The policy should mandate critical controls, including multi-factor authentication, encryption for data in transit, endpoint protection, secure remote access, and thorough logging [3][7]. Log retention is another key element. For instance, HIPAA requires that certain logs and documentation be retained for six years to support security monitoring and forensic investigations [3]. Additionally, Indiana's healthcare vendor management guidance recommends vendors implement measures like email and endpoint protection, access management, data loss prevention, asset management, vulnerability management, and incident response capabilities [7].
To oversee these efforts, establish a multi-disciplinary governance body, such as a Third-Party Risk Steering Committee. This group should regularly review and update policies, evaluate monitoring results for high-risk vendors, and oversee remediation processes. The policy should also incorporate risk-based vendor tiering. High-risk vendors (Tier 1) with direct network access, large-scale handling of PHI, or involvement in critical clinical operations may require continuous monitoring, quarterly reviews, and annual independent audits. Moderate-risk vendors (Tier 2), with limited PHI access or system interaction, might only need semi-annual assessments.
Assigning Roles and Responsibilities
Once the policy is in place, assigning clear roles ensures accountability across different teams.
- IT and network teams handle tasks like setting up network segmentation, VPNs, and logging for vendor connections, while maintaining updated inventories [3][9].
- Security teams analyze monitoring data, investigate alerts, and coordinate incident responses.
- Procurement and legal teams integrate monitoring, audit, and service-level clauses into contracts, ensuring provisions for audits and data-sharing requirements during security incidents [6][7].
- Compliance teams ensure that monitoring practices meet HIPAA, CMS, and state regulations by maintaining detailed audit trails [3].
- Clinical, biomedical, and operations teams assess the business impact, acceptable downtime, and operational risks while participating in vendor performance reviews [3][4].
Terry Grogan, CISO at Tower Health, shared that after adopting Censinet RiskOps, staffing needs dropped from three to two full-time employees [1]. This efficiency allows organizations to focus on specialized monitoring tasks. Using a centralized risk platform can further streamline operations by serving as a repository for vendor inventories, risk assessments, monitoring findings, remediation plans, and related evidence. Automated workflows and reminders can ensure timely review and follow-up.
Integrating Monitoring into Vendor Contracts
Internal governance alone isn't enough - contracts must also enforce monitoring standards with vendors.
Contracts and business associate agreements should explicitly grant monitoring rights, allowing your organization to review vendor network traffic, security logs, and system audits. Vendors must also provide timely access to security event logs and alerts [3].
Set clear service level agreements (SLAs) for both availability and security. For example, CMS recommends availability targets above 99.8% for critical clinical systems, and your SLAs should reflect similar expectations [3]. For security incidents, contracts should specify reporting obligations, requiring vendors to notify your organization within a defined timeframe (e.g., 24 hours) of any security event impacting PHI or clinical services. Vendors should also provide detailed incident reports and collaborate on remediation efforts.
In cases where a vendor cannot meet standard monitoring or access requirements due to technical, regulatory, or clinical constraints, the contract should document these exceptions. Compensating controls must be implemented, and these exceptions should be periodically reviewed to ensure continued security.
Designing Vendor Network Monitoring Architecture
To ensure secure and efficient vendor connections in clinical systems, it's essential to build a network monitoring architecture that prioritizes visibility and minimizes access risks. This approach is grounded in the principles of complete transparency and restricted access.
Creating a Network Inventory and Data Flow Map
"Without an accurate inventory and data flow map, monitoring becomes guesswork" [2].
Start by identifying all devices, connections, and data flows involving vendors.
Build a detailed inventory that accounts for every device and system, including switches, routers, firewalls, medical devices, servers, wireless access points, and vendor-specific remote access paths [2][9]. For each asset, document configuration details, vendor ownership or management, support contacts, and access needs [2].
Using automated discovery tools can simplify this process, generating real-time network maps that update as devices are added or removed - an essential feature for dynamic clinical environments [2].
Next, develop a vendor-specific data flow map. This should detail how vendor systems connect (e.g., VPN, private circuits, remote desktop, cloud APIs), the internal subnets they access, and the data exchanged (e.g., EHR, imaging, billing). Key areas to map include:
- Remote support connections to clinical systems like EHR, PACS, and lab information systems.
- Interfaces handling healthcare-specific protocols.
- File transfers for billing or claims.
- Connections crossing boundaries between vendor zones and core hospital systems [2][3][4].
Include details like data sources, destinations, protocols, encryption status, and typical volumes to baseline normal activity and detect anomalies [10][9]. This documentation also helps identify critical monitoring points for sensors, firewalls, or proxies, allowing you to observe and control vendor traffic without compromising performance. Additionally, it highlights vulnerable vendor paths, enabling precise placement of security controls [2][3][9].
Once you’ve mapped the network and vendor flows, the next step is to enforce access restrictions and reduce risks through segmentation.
Implementing Segmented Network Zones
Network segmentation acts as a safeguard, limiting the impact of compromised vendor connections. Instead of giving vendors unrestricted access to your network, place their systems in dedicated VLANs or virtual segments. Use next-generation firewalls and access control lists (ACLs) to regulate traffic between these segments and core clinical networks [2][3][9].
A common approach is to establish a vendor DMZ or remote access zone, where VPN concentrators, jump hosts, and remote support tools terminate. From this zone, connections to internal systems are tightly controlled [3][11]. For medical device vendors, many healthcare organizations isolate patient monitoring and imaging networks into separate segments with specific firewall rules, often using distinct SSIDs and wired VLANs for vendor-managed devices [2][4][11].
To prevent lateral movement, block unnecessary traffic between vendor zones and other internal segments. Enforce application-layer rules that specify permitted ports, protocols, and destinations based on your documented data flows [2][9][11]. For instance, a billing vendor might only need HTTPS access to a claims processing server, not the entire network.
Document communication rules between zones, including ports, protocols, and business purposes. These rules should be enforced via firewalls, ACLs, or micro-segmentation tools, particularly around high-risk or legacy clinical devices. To maintain operational continuity, ensure segmented zones include redundant paths and failover mechanisms for critical systems like patient monitoring networks [4].
With segmentation in place, the focus shifts to implementing advanced monitoring controls to detect potential threats.
Key Monitoring Controls and Detection Capabilities
Deploy tools that can identify and respond to threats within vendor connections. Network Detection and Response (NDR) systems analyze traffic patterns for suspicious behavior, while Deep Packet Inspection (DPI) and Intrusion Detection/Prevention Systems (IDS/IPS) examine protocol details and content [3][9][11]. Robust logging of system, application, and access events involving vendor accounts completes the monitoring framework.
Place NDR and DPI sensors at strategic points, such as Internet/VPN gateways, data center cores, clinical VLAN uplinks, wireless controllers, and cloud interconnects. This ensures comprehensive visibility without blind spots. These tools must support healthcare-specific protocols without disrupting them.
NDR solutions should baseline normal vendor access patterns and flag anomalies, such as unexpected destinations, unusual protocols, or large data transfers during off-hours [10][2][9]. For example, an alert should trigger if a vendor account accesses an unapproved subnet, initiates large data transfers at odd times, or repeatedly fails authentication from unfamiliar locations [10][2]. DPI and IDS/IPS can be configured with healthcare-relevant rules to guard against ransomware and remote access exploits commonly targeting vendor channels [2][3][11].
Centralize logs from systems like Syslog, Windows Event logs, VPN logs, and application logs into a Security Information and Event Management (SIEM) system. This enables correlation of network anomalies with authentication events and Protected Health Information (PHI) access [3].
"CSAM Health Group, a provider of clinical systems, monitors its infrastructure with more than 1,000 SNMP queries every minute to track application queues and system health, maintaining greater than 99.8% availability" [3].
Log management tools should automatically collect and retain logs for durations required by HIPAA and organizational policies - often up to six years for certain audit trails - supporting investigations and audits [3][11].
Centralized platforms that integrate mapping, inventory, performance, and security events can streamline operations. For example, AI-powered platforms like Censinet RiskOps enable healthcare organizations to securely share cybersecurity and risk data with third-party vendors, reducing risks more efficiently [1]. These tools are specifically designed for healthcare, offering faster and more effective protection.
sbb-itb-535baee
Operationalizing Vendor Monitoring and Incident Response
Keeping vendors in check requires more than just having policies in place - it calls for active oversight and quick action when something goes wrong. By building on established network architecture and governance policies, operational monitoring takes those policies off the page and puts them into practice. This means shifting from static configurations to active, real-time monitoring that not only identifies threats as they happen but also strengthens vendors' roles in safeguarding patient care.
Real-Time Monitoring and Alerting
To keep tabs on vendor activity, deploy tools like SIEM systems, network traffic analysis, and log management solutions. These systems should monitor events across VPNs, firewalls, EHR systems, medical device networks, and vendor gateways. Real-time alerts should be based on well-defined rules and baselines, flagging suspicious activities like unusual vendor logins (e.g., odd times, locations, or devices), abnormal data transfers involving PHI repositories, and unexpected permission changes on systems handling ePHI [3][9].
HIPAA compliance is non-negotiable here. Logs must be retained for at least six years, as required by HIPAA, to support post-incident investigations [3].
Integrating monitoring platforms with on-call schedules and ticketing systems ensures alerts don’t just sit in an inbox. Instead, they trigger immediate notifications - like pages - and go straight to the incident response team [3][9]. Platforms such as Censinet RiskOps™ can further enhance this process by centralizing vendor risk data, assessment results, and remediation plans. This gives security teams the context they need to act swiftly when an alert is triggered.
Vendor-Inclusive Incident Response
Incident response plans should explicitly include vendors. Develop playbooks that outline notification timelines, evidence requirements (like logs or forensic data), and joint triage steps. These might include actions such as disabling vendor accounts, isolating network segments, or revoking access tokens. Contracts and SLAs should clearly define security expectations, such as log collection standards, retention policies, and the vendor's role in supporting continuous monitoring for high-risk connections [6][3].
Regular incident response drills - like tabletop exercises - can help prepare for scenarios such as ransomware spreading from a vendor's network or a compromised vendor admin account in your EHR system. Include vendor representatives in these drills to ensure everyone is on the same page. Also, embed monitoring and incident response requirements into Business Associate Agreements (BAAs) and contracts. These agreements should cover continuous monitoring obligations, audit rights, and SLAs for incident response and remediation support.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [1]
Beyond just security, it’s equally important to monitor vendor performance to ensure they meet operational standards.
Performance Monitoring in Addition to Security
Monitoring performance is about more than just keeping systems secure - it’s about ensuring they run smoothly. Key metrics to track include:
- Service uptime and availability (e.g., aiming for ≥99.9% for critical systems like EHR or PACS)
- Mean time to detect and resolve issues (MTTD and MTTR)
- Transaction latency for vital workflows (e.g., medication orders, image retrieval, claims processing)
- Error rates in interfaces and APIs
- SLA adherence, especially response times [8][3]
Clinical systems demand near-perfect availability. For example, one healthcare vendor achieved over 99.8% uptime by consistently monitoring critical systems through SNMP and server metrics [3]. This level of vigilance ensures issues like EHR slowness or imaging delays are caught and resolved before they disrupt patient care [3][9].
Centralized healthcare TPRM platforms can also play a crucial role. They help maintain a real-time inventory of vendors and services, track risk assessments, and manage remediation plans. These platforms allow healthcare organizations to securely collaborate with third-party vendors by sharing cybersecurity and risk data, making risk management more efficient [1].
Measuring Success and Improving Vendor Monitoring Programs
Once your vendor monitoring program is up and running, the next challenge is making sure it delivers results - and figuring out how to make it better over time. This involves tracking meaningful metrics, reassessing vendor risks regularly, and using centralized tools to transform data into actionable insights.
Defining Key Metrics and KPIs
Start by identifying critical KPIs that focus on both security and operational performance. Metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), segmented by vendor risk and connection type, are great places to begin. For high-risk vendors, you might set specific targets, such as detecting issues within 15 minutes and resolving them within 4 hours [3][6][9].
Other useful performance indicators include:
- Service uptime: Aim for at least 99.9% availability for critical systems.
- Transaction latency: Monitor delays in key workflows.
- Error rates: Track errors in vendor interfaces.
Additionally, keep an eye on the percentage of high-risk vendor connections actively monitored. For example, if only 60% of high-risk vendors are under active monitoring, you might set goals like increasing that coverage to 90% or improving MTTR by 20% over a year or six months [9][12]. These metrics provide a solid foundation for assessing and reducing risk.
Periodic Risk Assessments and Reviews
Vendor risks are constantly evolving, so your monitoring efforts need to evolve, too. High-risk vendors should undergo a formal risk reassessment at least once a year - or more often if needed [9][12]. For example, if dashboards show a vendor triggering frequent failed logins or unusual after-hours access attempts, these red flags might call for stricter access controls, such as narrowing access windows, enforcing multi-factor authentication (MFA), or tightening firewall rules [3][4].
Dashboards can also highlight operational issues. For instance, if a vendor-managed EHR interface experiences periodic latency spikes, trend analysis might reveal that these spikes align with scheduled vendor jobs. Adjusting the job schedules could improve system uptime [3][4]. Regular governance reviews involving security, IT, compliance, and vendor management teams should analyze such findings. These reviews can identify vendors with slow remediation times and use that information to push for better contractual agreements [4][6]. Consolidating these insights into a centralized platform can help elevate your program’s effectiveness.
Leveraging Centralized Platforms for Program Maturity
Centralized platforms are game-changers for improving vendor monitoring. Tools like Censinet RiskOps™ bring together vendor risk assessments, continuous monitoring data, incident reports, and corrective action plans into one unified view. This eliminates the need for spreadsheets and manual tracking, freeing up your team to focus on more strategic tasks.
These platforms also provide tailored dashboards and benchmarking tools, especially useful in industries like healthcare. They allow you to measure your performance against peers and identify areas where you can improve. As Brian Sterud, CIO at Faith Regional Health, puts it:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Conclusion
Vendor network monitoring plays a crucial role in safeguarding patient data, ensuring smooth clinical operations, and complying with regulatory standards. As healthcare organizations face increasingly complex vendor connections and evolving cyber threats, gaining full visibility into network access, data flow, and incident response capabilities is more important than ever.
A well-rounded approach combines security measures with performance monitoring. The strategies discussed in this article - such as achieving comprehensive network visibility, implementing Zero Trust principles, establishing strong governance frameworks, designing segmented network architectures, and enabling real-time monitoring - work together to create a resilient defense. By integrating these practices, healthcare organizations can not only detect and address cyber threats but also identify operational challenges before they impact patient care. Embedding monitoring requirements into vendor contracts and incident response plans transforms vendors into proactive partners in managing risk.
Centralized platforms simplify these efforts by turning complex data into actionable insights. Censinet RiskOps™ offers a scalable solution by unifying vendor risk assessments, continuous monitoring, incident reports, and corrective actions into a single system. This platform streamlines decision-making and enhances collaboration. Its benchmarking tools also enable teams to compare performance with peers, advocate for resources, and continuously improve their programs. As Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
Whether your organization is just beginning to map vendor connections or refining advanced monitoring workflows, the key is to start now and build progressively. Focus first on high-risk vendors and systems handling PHI, then expand monitoring efforts and integrate insights into governance reviews and leadership dashboards. Track critical metrics - like MTTD (Mean Time to Detect), MTTR (Mean Time to Respond), uptime, and coverage rates - to showcase measurable progress in security, compliance, and operational resilience.
Vendor network monitoring is a shared responsibility. Healthcare organizations must lead with clear policies, effective tools, and consistent oversight, while vendors should commit to transparency, rapid issue resolution, and secure configurations. This collaborative effort safeguards not only sensitive data but also the quality and safety of patient care.
FAQs
What are the benefits of using Zero Trust principles for monitoring vendor networks in healthcare?
In healthcare, applying Zero Trust principles to vendor network monitoring bolsters security by demanding constant identity verification and strictly limiting access to essential resources. This method significantly lowers the chances of unauthorized access, blocks attackers from navigating across systems, and helps keep sensitive healthcare data secure.
Another advantage of Zero Trust is the improved visibility it provides into vendor activities. This enhanced oversight helps identify suspicious behavior early, allowing organizations to address potential threats before they escalate. By reducing exposure points and enforcing rigorous segmentation, healthcare providers can better protect patient information, clinical tools, and operational systems.
What’s the best way for healthcare organizations to balance continuous and periodic vendor risk monitoring?
Healthcare organizations can strike a balance between continuous and periodic vendor risk monitoring by adjusting their approach based on the risk level each vendor presents. For high-risk vendors - those managing sensitive patient information or operating critical systems - continuous, real-time monitoring is essential. This allows for the rapid detection and resolution of potential threats. Meanwhile, lower-risk vendors can be monitored through scheduled assessments at regular intervals.
This risk-based approach helps organizations allocate resources efficiently while maintaining robust security measures. Using advanced tools, such as AI-powered platforms, can make this process more manageable. These tools provide valuable insights, helping healthcare providers safeguard patient data and stay compliant with regulatory requirements.
How do vendor contracts support effective network monitoring and incident response in healthcare?
Vendor contracts are essential for maintaining effective network monitoring and incident response in healthcare organizations. These agreements clearly define security expectations, responsibilities, and compliance requirements, creating a strong framework for managing third-party risks.
When crafted thoughtfully, these contracts ensure vendors align with healthcare cybersecurity standards, such as safeguarding patient information and securing clinical systems and devices. They also play a key role in ongoing risk management by holding vendors accountable for upholding stringent security measures and incident response protocols, ultimately protecting both the organization and its patients.


