Blockchain vs Traditional Data Security Methods
Post Summary
Healthcare organizations face a critical choice when it comes to protecting sensitive patient information: blockchain or traditional data security methods. Both approaches have distinct strengths and challenges, and the best option depends on specific needs like scalability, compliance, and risk management.
- Traditional Methods: Centralized systems like EHR databases use encryption, firewalls, and access controls. They are fast, efficient for large-scale operations, and allow data corrections but are vulnerable to breaches due to single points of failure.
- Blockchain: Decentralized and tamper-resistant, blockchain creates secure audit trails and reduces insider risks. It's ideal for multi-party trust scenarios, like tracking consent or supply chains, but has limitations like higher costs, complexity, and slower performance.
Quick Overview:
- Traditional Security: Works best for high-speed, high-volume tasks like billing and clinical workflows.
- Blockchain: Excels in scenarios requiring shared, tamper-proof records across multiple organizations.
Choosing the right approach often involves combining both methods, leveraging blockchain for transparency and trust while relying on traditional systems for speed and flexibility. Tools like Censinet RiskOps™ can help organizations assess risks and make informed decisions.
Traditional Data Security Methods in Healthcare
Common Security Architectures and Controls
To safeguard electronic protected health information (ePHI), healthcare organizations in the U.S. often rely on centralized electronic health record (EHR) systems. These systems are typically hosted either on-premises or in HIPAA-compliant cloud environments [4]. On-premises setups include virtualized servers and centralized databases that store PHI, with clear separations for production, testing, and disaster recovery environments. Cloud-based deployments follow a similar structure but require the healthcare organization to manage configuration, identity controls, and data governance [4].
Connections between EHRs and clinical applications are established using HL7 v2 interfaces, FHIR APIs, VPNs, and secure messaging systems. These connections are protected through measures like network segmentation, encryption, and access controls [4][7]. Security frameworks such as Active Directory are used to enforce authentication and role-based access control (RBAC) [4]. Additional safeguards include encryption protocols, firewalls, VPNs for remote access, intrusion detection/prevention systems (IDS/IPS), and network segmentation, which isolate sensitive clinical networks from guest Wi-Fi and administrative systems [3][4]. These layered defenses aim to support clinical workflows while addressing security risks.
Strengths of Traditional Data Security
Over the years, traditional security methods have been refined and are supported by a wide range of vendor tools, certifications, and experienced professionals. They are particularly well-suited for legacy systems, such as HL7 interfaces and older operating systems still widely used in hospitals [3]. These systems are known for their high performance and low latency, which are critical for maintaining efficient clinical workflows [2][7]. Additionally, their mature ecosystem simplifies deployment and troubleshooting [3].
Traditional systems also provide privacy controls and data lifecycle management features, such as data masking, access logging, and selective deletion. These capabilities help organizations comply with HIPAA and other privacy standards [4]. For instance, the ability to modify or delete records allows for correcting PHI and honoring patient rights under HIPAA. Tools like Censinet RiskOps™ further enhance these systems by helping healthcare organizations assess and manage risks across EHRs, medical devices, and supply chain partners.
Limitations and Common Breach Scenarios
Despite their reliability, traditional security systems have notable weaknesses. Centralized architectures inherently create single points of failure at critical levels like the database, application, or identity-management tiers. A successful breach at any of these points can compromise millions of records in a single incident [2][4][7]. Additionally, traditional databases lack immutability and distributed consensus, meaning attackers or insiders with elevated access can alter or delete records. Such tampering often goes unnoticed until anomalies in clinical or billing operations surface [2][4].
Large-scale breaches often stem from scenarios like ransomware attacks on hospital networks, exploitation of unpatched vulnerabilities in web applications or VPNs, and credential theft leading to mass data exfiltration from centralized databases [3][5]. A well-known example is the 2017 Equifax breach, where attackers exploited a web application vulnerability to access a centralized database, exposing the personal data of over 147 million individuals [3]. Similar patterns have emerged in U.S. healthcare, with breaches affecting millions of patient records, often due to weak network segmentation or inadequate monitoring. Insider threats remain another critical issue, as employees or contractors with legitimate access can misuse their privileges to view, export, or alter sensitive data. These actions often mimic normal activity, making them harder to detect [2][4][5].
Blockchain Data Security in Healthcare
Core Features and Use Cases
Blockchain brings three major security benefits to healthcare: decentralization, immutability, and tamper-evident audit trails. By decentralizing records, using cryptographic hashing to ensure immutability, and linking transactions into a secure audit trail, blockchain provides a robust framework for protecting healthcare data [2][3].
In the U.S., many healthcare systems employ permissioned blockchains like Hyperledger Fabric or Quorum. These systems limit participation to vetted entities such as hospitals, insurers, and laboratories, ensuring only trusted organizations are part of the consensus process [4]. To comply with HIPAA, sensitive personal health information (PHI) is typically stored off-chain in encrypted databases or secure FHIR servers. Only metadata, hashes, or pointers are recorded on the blockchain. For instance, patient consent events - such as timestamps, authorship, and scope - are logged on-chain, while the actual clinical data is stored off-chain and managed by smart contracts [3].
One exciting application is patient-controlled data sharing. Blockchain enables patients to decide who can access their data, for how long, and under what conditions. This is achieved by maintaining a ledger of granular consent records. In clinical trials, blockchain can also enhance trust by recording protocol versions, randomization lists, and outcome data, making it nearly impossible to manipulate results after the fact [3]. Another practical use is supply chain traceability, where a shared ledger tracks the journey of pharmaceuticals and medical devices - from manufacturers to hospitals. This helps detect counterfeit products or identify storage issues in near real-time [3].
Implementation Challenges
While blockchain has clear advantages, it also presents unique challenges, particularly in regulatory and operational contexts. Its append-only nature can complicate regulatory compliance. To address this, organizations often use logical amendment patterns, where updates are recorded as new transactions, preserving a complete audit trail [4]. When incorrect data is entered, some systems rely on crypto-shredding - destroying encryption keys to make data inaccessible - instead of physical deletion. However, this approach can create legal and operational hurdles [4].
Effective key management is another critical concern. Losing or compromising cryptographic keys can lead to severe consequences. To mitigate this, organizations should implement enterprise-grade solutions, including hardware security modules, strict role-based access controls, multi-factor authentication, and multi-signature models [4]. Additionally, blockchain's inherent limitations, such as higher latency and lower throughput, require careful system design. Techniques like batching, asynchronous processing, and selecting the right consensus algorithms can help meet the demanding needs of clinical environments [2].
These factors highlight the complexities of implementing blockchain compared to traditional data security methods, setting the stage for a deeper exploration of its practical applications and limitations.
Blockchain vs. Traditional Data Security: Direct Comparison
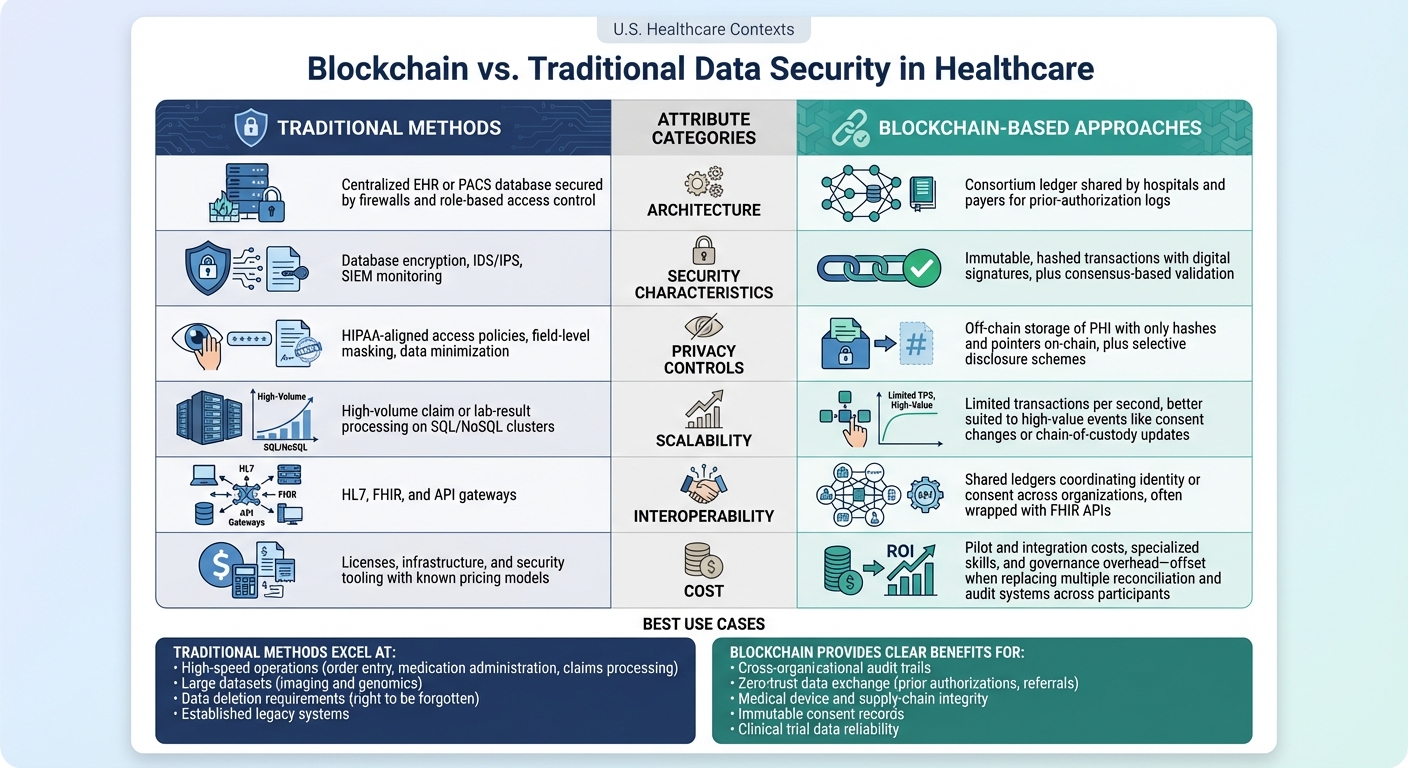
Blockchain vs Traditional Data Security Methods in Healthcare: Key Attributes Comparison
Comparison Table of Key Attributes
Healthcare organizations need to weigh the strengths and limitations of blockchain and traditional security methods when protecting patient data and maintaining operational efficiency. Below is a table that highlights how these two approaches compare across critical attributes. Following the table, we'll dive into scenarios where each method excels.
| Attribute | Traditional Methods in Healthcare | Blockchain-Based Approaches |
|---|---|---|
| Architecture | Centralized EHR or PACS database secured by firewalls and role-based access control | Consortium ledger shared by hospitals and payers for prior-authorization logs [2][3][6] |
| Security Characteristics | Database encryption, IDS/IPS, SIEM monitoring | Immutable, hashed transactions with digital signatures, plus consensus-based validation [3][4][5] |
| Privacy Controls | HIPAA-aligned access policies, field-level masking, data minimization | Off-chain storage of PHI with only hashes and pointers on-chain, plus selective disclosure schemes [4][5] |
| Scalability | High-volume claim or lab-result processing on SQL/NoSQL clusters | Limited transactions per second, better suited to high-value events like consent changes or chain-of-custody updates [2][4] |
| Interoperability | HL7, FHIR, and API gateways | Shared ledgers coordinating identity or consent across organizations, often wrapped with FHIR APIs [6] |
| Cost | Licenses, infrastructure, and security tooling with known pricing models | Pilot and integration costs, specialized skills, and governance overhead - offset when replacing multiple reconciliation and audit systems across participants [3][4][5] |
When Traditional Methods Work Best
Traditional security methods shine in environments that demand high-speed operations and low latency. For example, healthcare activities like order entry, medication administration, and claims processing - where systems handle millions of records daily - are ideally suited for these approaches [2][3][4]. Their ability to manage high throughput with millisecond response times gives them an edge over blockchain for these tasks.
In areas like imaging and genomics, where large datasets are frequently accessed and stored, traditional architectures are also the preferred choice. Organizations with established legacy systems, such as older EHRs or radiology information systems, often find upgrading to blockchain too costly or complex [2][3][4]. Additionally, when compliance with regulations like HIPAA and state privacy laws is already achieved through mature tools - such as encryption, role-based access control, and incident response plans - traditional methods continue to be reliable.
Another key advantage of traditional systems is their ability to handle data deletion requirements, such as the "right to be forgotten." Blockchain’s immutable nature can complicate compliance with these legal and operational needs [4][5]. However, blockchain's strengths emerge in scenarios requiring decentralized trust and transparency.
When Blockchain Provides Clear Benefits
Blockchain becomes indispensable when healthcare entities need a shared, tamper-proof record of critical events across organizations. For example, cross-organizational audit trails for PHI access are an excellent match for blockchain. A shared ledger can document who accessed what data, creating transparency across hospitals, payers, and health information exchanges.
In situations like zero-trust data exchange, blockchain offers robust solutions. It enables secure transactions for prior authorizations, referrals, and bundled payments while ensuring that PHI remains off-chain [3][4][5][6].
Blockchain also plays a key role in securing medical device and supply-chain integrity. It ensures the authenticity of items like implants, pharmaceuticals, and IoMT firmware. Additionally, it provides immutable consent records, which are valuable for managing patient agreements across EHRs, research networks, and mobile apps. In clinical research, blockchain strengthens the reliability of trial data by recording events and dataset hashes on-chain, minimizing disputes and enhancing trust [3][4][5][6].
sbb-itb-535baee
Implementation and Risk Management Considerations
Technical and Organizational Requirements
For healthcare organizations looking to adopt blockchain, a robust infrastructure is a must. This includes scalable network and storage systems, APIs (like HL7/FHIR or middleware) to connect blockchain transactions with existing EHR systems, and a strong identity and access management (IAM) framework to handle cryptographic keys. Losing these keys can result in permanent loss of access for legitimate users, making key management a critical priority.
Organizations also need to update their data governance policies to align with blockchain's immutable nature. This involves clearly defining what data stays on-chain versus off-chain, creating protocols for generating, storing, rotating, and recovering keys, and providing targeted training. Clinicians must understand the permanence of blockchain records, while IT teams need to develop expertise in running nodes and managing smart contracts. Governance bodies, on the other hand, must expand their oversight to include consortium participation, node hosting duties, and shared risk models with external partners.
For those strengthening traditional security measures, familiar strategies remain effective. These include enhancing defense-in-depth practices like network segmentation, next-generation firewalls, endpoint protection, and intrusion detection systems. Role-based access control, multi-factor authentication, and privileged access management are critical for protecting EHRs and databases from insider threats. Investments in security operations centers, vulnerability management, and regular penetration testing help organizations stay ahead of evolving threats. Training programs should focus on phishing awareness, least-privilege access, and data loss prevention to reinforce these measures.
Once these technical and organizational elements are in place, a thorough risk assessment becomes essential. This step ensures that the organization is prepared to address security challenges and helps evaluate whether blockchain's advantages outweigh its complexities compared to traditional security solutions.
Risk Assessment with Censinet
To meet these requirements and manage risks effectively, healthcare organizations can turn to structured risk assessment tools. Censinet RiskOps™ offers a comprehensive approach tailored to U.S. healthcare settings, evaluating risks in both blockchain and traditional security frameworks. The platform enables standardized third-party risk assessments, examining vendors' security controls, key management strategies, hosting environments, and HIPAA compliance. It also supports enterprise-level risk assessments, detailing how blockchain nodes and services interact with clinical systems, medical devices, and supply chains. This helps pinpoint potential failure points and dependencies.
Censinet RiskOps™ also facilitates collaborative risk management. Healthcare organizations and their vendors can share remediation plans, monitor control gaps (such as consensus security, smart contract reviews, and node hardening), and document compensating controls. Designed specifically for healthcare, the platform maps blockchain-related risks to clinical outcomes, patient safety, and regulatory standards. This ensures organizations can make informed decisions about whether blockchain is the right fit for their specific applications.
Terry Grogan, CISO at Tower Health, shared how Censinet RiskOps™ transformed his team's workflow: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
Conclusion: Choosing the Right Approach
Healthcare leaders face a critical decision: stick with traditional security measures, explore blockchain for specific scenarios, or adopt a mix of both. If your main challenges include phishing attacks, system misconfigurations, unpatched vulnerabilities, or outdated infrastructure, focusing on identity and access management, network segmentation, endpoint detection, and backup recovery can deliver the best risk reduction. These traditional methods remain essential for core systems like electronic health records (EHRs), billing, and clinical workflows, where performance, availability, and adaptable data management are crucial.
On the other hand, blockchain shines in situations involving multiple independent organizations that need a shared, tamper-proof record. For example, provider credentialing across hospitals and payers or ensuring supply chain transparency to combat counterfeit medications. Blockchain's decentralized validation and immutable ledger help prevent unauthorized changes. However, it comes with its own challenges, including performance limitations, governance complexities, key management responsibilities, and privacy concerns. Often, a hybrid approach works best - storing sensitive patient health information (PHI) in traditional databases while anchoring hashes or metadata on the blockchain.
To navigate these options, a clear decision-making framework is key. Start by asking:
- What is the core problem we’re solving?
- How many organizations need to trust the data?
- What are the regulatory and performance requirements?
If the issue is internal security gaps, traditional controls are the way to go. For multi-party trust scenarios, blockchain may be more suitable. Workflows requiring low latency or strict data deletion policies often benefit from hybrid solutions. The best strategy is to phase investments: address traditional security gaps first, pilot blockchain where multi-organization trust is critical, and then scale hybrid models that prove effective.
Platforms like Censinet RiskOps™ can support this process by offering standardized evaluations of security controls, key management practices, hosting environments, and HIPAA compliance. Its collaborative risk network and benchmarking tools allow leaders to compare the residual risks of traditional, blockchain-enhanced, and hybrid approaches against peer organizations. By integrating risk management into the broader security strategy, healthcare executives can make evidence-based decisions that balance risks and rewards, ensuring regulatory compliance and operational efficiency. This thoughtful approach helps organizations choose the right mix of security measures tailored to their unique needs.
FAQs
How does blockchain enhance data security compared to traditional methods?
Blockchain enhances data security by establishing decentralized, tamper-proof records, which drastically minimize the risk of single points of failure. Instead of relying on centralized systems, blockchain employs cryptographic methods to maintain data integrity, making unauthorized changes extremely difficult.
On top of that, blockchain's transparency and unchangeable nature offer a dependable way to monitor data changes, fostering accountability and trust. These qualities make it especially effective for safeguarding sensitive information, such as patient records in the healthcare industry, where protecting data is paramount.
What obstacles exist when using blockchain for healthcare data security?
Blockchain holds great promise for securing healthcare data, but its implementation isn't without hurdles. One major challenge is scalability - handling the sheer volume of healthcare data can put a strain on blockchain networks, potentially slowing down processes. Another issue is integration. Merging blockchain with existing healthcare systems can be a complicated and lengthy process, often requiring advanced technical expertise.
Then there’s the matter of costs. Setting up and maintaining blockchain technology can be expensive, making it less accessible for smaller healthcare organizations. Regulatory compliance adds another layer of complexity, as blockchain systems must align with strict privacy laws like HIPAA. Lastly, for blockchain to truly transform healthcare, industry-wide adoption is crucial. This means fostering collaboration and setting standards across the sector - no small feat in such a diverse and fragmented industry.
When is it best to use a combination of blockchain and traditional data security methods?
A blended approach shines in situations where blockchain's transparency and security pair well with the scalability and regulatory adherence of traditional systems. This combination is especially effective in fields like healthcare, where managing sensitive data - such as patient records - demands both stringent protection and compliance with strict regulations.
For instance, blockchain can provide data integrity and traceability, ensuring information remains tamper-proof and verifiable. Meanwhile, traditional systems excel at handling large-scale processing and meeting established compliance standards. Together, they create a well-rounded solution for complex industries that require both forward-thinking technology and dependable performance.


