How to Build Endpoint Threat Containment Protocols
Post Summary
Endpoint threat containment is all about isolating and controlling cybersecurity threats on devices that handle sensitive healthcare data, like patient records or medical devices. Unlike traditional security measures that focus on preventing attacks, containment assumes a breach has already occurred and focuses on limiting the damage quickly.
Here’s what you need to know:
- Why it matters: Healthcare breaches cost an average of $10.93 million per incident (2023), and delays in containment can disrupt patient care, cancel procedures, and compromise sensitive data.
- Key steps:
- Establish governance with clear roles and escalation paths.
- Classify devices by risk level (e.g., life-critical medical devices vs. office laptops).
- Create detailed playbooks for common threats like ransomware or phishing.
- Use tools like Endpoint Detection and Response (EDR) and network segmentation for fast action.
- Challenges: Medical and IoMT devices often require special handling since they can’t always be powered down or patched like regular IT systems.
- Best practices: Test protocols regularly, involve clinical leaders in decisions impacting patient care, and track metrics like Mean Time to Contain (MTTC) to improve over time.
Fast containment is critical in healthcare to minimize risks, maintain patient safety, and meet regulatory requirements like HIPAA. The rest of this guide dives into how to set up governance, classify endpoints, create playbooks, and deploy technical controls effectively.
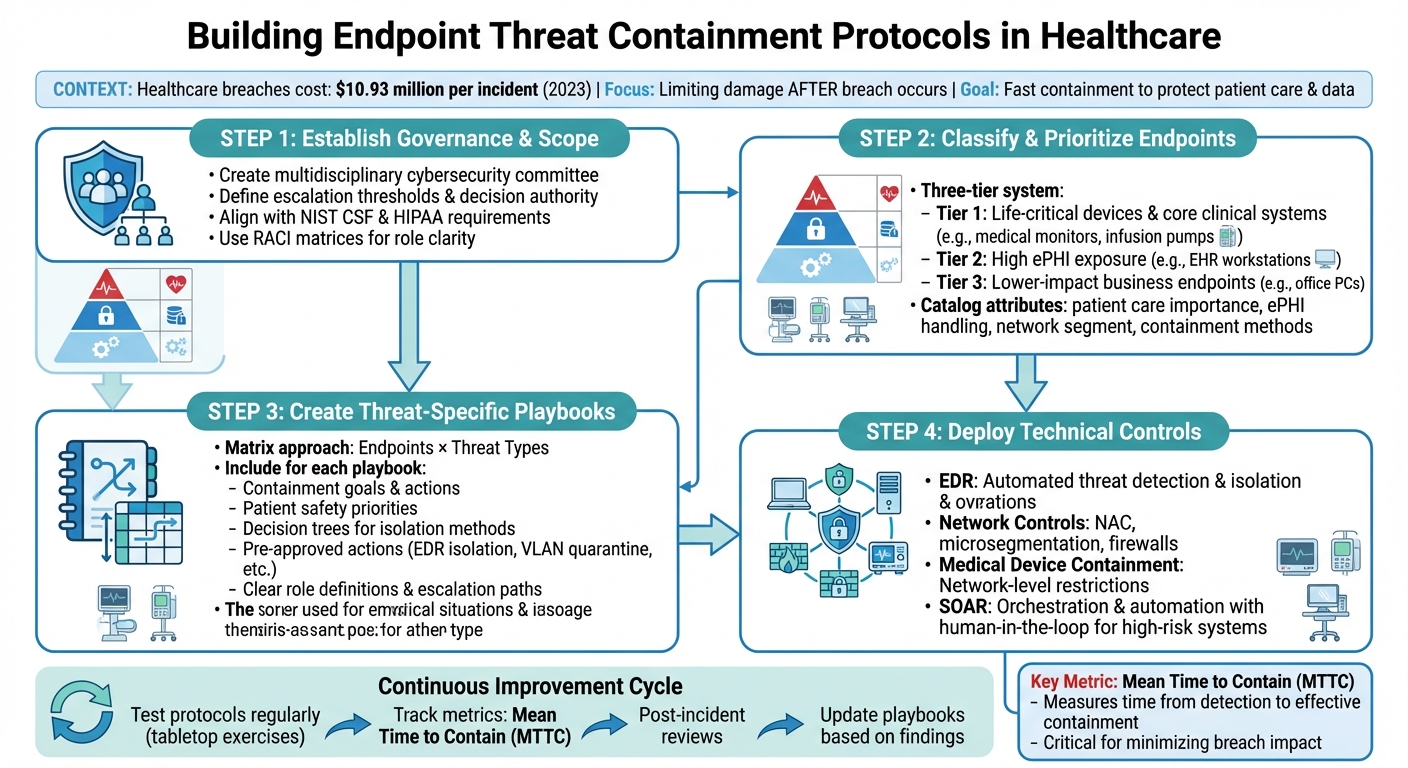
Healthcare Endpoint Threat Containment Framework: 4-Step Implementation Process
Setting Up Governance and Scope
Creating Governance Frameworks
A solid governance framework is essential for making quick, coordinated decisions during a cybersecurity incident. By integrating incident response principles with risk management, healthcare organizations can ensure their containment strategies address both cybersecurity needs and patient care priorities. To achieve this, a multidisciplinary cybersecurity committee should be established. This team might include IT security experts, clinical leaders, compliance and privacy officers, biomedical engineers, and risk management professionals. Their combined expertise ensures containment decisions are practical and patient-centered.
To align with established standards, containment activities should follow the NIST Cybersecurity Framework (Detect, Respond, Recover) and comply with HIPAA regulations. For example, actions like isolating a compromised workstation should be mapped to these frameworks to support both immediate response and long-term improvement. The HHS 405(d) Health Industry Cybersecurity Practices guidance provides a strong starting point, with recommendations like maintaining asset inventories, implementing endpoint protections, and ensuring systems are regularly patched.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
- Matt Christensen, Sr. Director GRC, Intermountain Health
Governance charters should clearly outline escalation thresholds and decision-making authority. For instance, isolating a critical electronic health record (EHR) server might require executive approval, while quarantining a billing workstation could be handled by the security operations team. Using tools like RACI matrices can help define roles and responsibilities. Automated platforms, such as Censinet RiskOps™, can further simplify the process by tracking risks across third-party and enterprise systems, assigning accountability, and monitoring critical assets like PHI systems and medical devices.
Classifying Endpoints and Setting Priorities
To make informed, risk-based containment decisions, healthcare organizations need a detailed classification system for their endpoints. Devices should be grouped into categories such as user IT endpoints (laptops, desktops, tablets, smartphones), clinical workstations, servers hosting EHRs, and medical or IoMT devices like infusion pumps and patient monitors. Each device should be cataloged with attributes that aid in containment decisions, including its importance to patient care, whether it handles ePHI, its network segment, available containment methods (like EDR isolation or VLAN quarantine), and any vendor or maintenance constraints.
This enriched inventory allows for automated containment of lower-risk devices while reserving high-risk decisions for human review. Prioritization should balance cybersecurity needs with patient safety, taking into account factors like the device’s role in clinical outcomes, the sensitivity and volume of ePHI it processes, and its connectivity. Many organizations use a tiered system to manage this balance:
- Tier 1: Life-critical devices and core clinical systems.
- Tier 2: Devices with high ePHI exposure, such as EHR workstations.
- Tier 3: Lower-impact business endpoints.
For example, Tier 3 devices showing malicious activity might be automatically isolated, while decisions involving Tier 1 devices typically require clinical approval to avoid jeopardizing patient safety.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
- Brian Sterud, CIO, Faith Regional Health
These classifications not only guide containment actions but also help ensure compliance with regulatory standards.
Meeting Regulatory and Operational Requirements
Strong governance and careful endpoint classification are critical for meeting HIPAA and clinical safety standards. HIPAA’s Security Rule requires measures like unique user identification, access controls, audit logging, and data integrity protections for ePHI. Containment strategies must preserve audit logs and evidence to support incident response and breach notification requirements under HIPAA and HITECH. Privacy and compliance officers should be involved in escalation processes to confirm regulatory compliance.
Patient safety adds another layer of complexity. Containment actions must be designed to minimize disruptions to care. For example, abruptly disconnecting medical devices could pose risks to patients. Governance frameworks should include clinical risk assessments and define safe modes for containment, such as diverting patients, using backup equipment, or delaying non-urgent procedures. For medical and IoMT devices, which often run on outdated or vendor-locked systems that can’t support standard security tools, responsibility for containment decisions should be shared between biomedical engineering and IT security teams. Policies should also require vendors to provide documentation on supported security controls and safe network modifications. Clinical leaders should help classify life-sustaining devices and define acceptable degraded modes of operation to ensure patient care remains uninterrupted.
Creating Endpoint Containment Playbooks
Organizing Playbooks by Endpoint and Threat Type
To effectively handle security incidents, playbooks should be organized in a matrix format. Use endpoints like clinical workstations, laptops, servers, and medical devices as rows, and threat types such as ransomware, data exfiltration, and credential compromise as columns. Each cell in this matrix links to a customized playbook, factoring in patient care importance and regulatory concerns like PHI exposure risk [11][2].
This setup allows for tailored responses to specific scenarios. For example, a hospital should have dedicated playbooks for situations like:
- Ransomware detected on an EHR workstation at a nurses' station.
- Malware beaconing from a radiology PACS server.
- Suspicious network activity from an infusion pump or patient monitor in an ICU.
- Phishing-induced credential compromise on a physician's laptop with remote EHR and VPN access.
- Unauthorized remote access on a vendor-managed imaging modality.
Each playbook must strike a balance between immediate containment and maintaining patient care. This might involve diverting patients, switching to downtime procedures, or reallocating workloads to backup systems [2][4][5].
Defining Containment Goals and Actions
Building on the matrix structure, each playbook should define clear containment goals and actions. These must align with governance frameworks and endpoint classifications, translating policy into practical steps.
Each playbook should include:
- A defined scenario and containment objective.
- The scope of the response and its impact on patient safety.
- Step-by-step containment procedures.
- Roles and responsibilities.
- Decision trees for isolation methods.
- Communication templates.
- Guidelines for handling forensic evidence and post-incident recovery, adhering to HIPAA and HITECH requirements [2][3].
For general IT endpoints like workstations, laptops, and office servers, the main goals are to stop the threat, protect PHI and business data, and preserve forensic evidence. These devices can often be fully isolated and reimaged if necessary. For medical and IoMT devices, the priority is maintaining patient safety and clinical functions. Instead of full shutdowns, containment might involve network-level controls, access restrictions, or partial isolation. Each playbook should specify the patient safety priority (e.g., High, Medium, Low) and define the minimum acceptable clinical function before initiating isolation [2][4][5].
Playbooks should also outline pre-approved actions such as:
- EDR one-click host isolation.
- Disabling specific network ports or VLAN access.
- Blocking outbound domains or IP addresses.
- Forcing user logoffs and credential resets.
- Disabling application or database accounts.
- Restricting devices to a quarantine network.
- Transitioning from full isolation to monitored production.
Decision-making criteria should consider factors like whether PHI is at risk, if the endpoint directly supports patient care, the likelihood of threat spread, compliance requirements for preserving evidence, and the availability of validated downtime or backup processes. For instance, a decision tree might state: "If a life-sustaining function is present, never power off; consider network microsegmentation and heightened monitoring instead." This ensures decisions are consistent and auditable [2][3][4].
Clear role definitions are also crucial. An SOC or EDR analyst might confirm alerts and initiate containment. The IT endpoint team handles technical actions for workstations or servers, while clinical engineering manages medical devices. Nursing or clinical leadership approves actions affecting patient care. Privacy and compliance assess PHI exposure and breach requirements, while the CISO or incident commander oversees high-impact decisions. Escalation thresholds should also be specified, such as notifying leadership if multiple clinical endpoints are affected or if PHI exfiltration is a concern [2][7][9].
Comparing Containment Methods
Healthcare organizations typically rely on three containment methods:
- Hard Isolation: Disconnects the endpoint from all networks and disables logins. While effective at suppressing threats and preserving forensic evidence, it can cause significant operational disruption and is unsuitable for critical care devices.
- Soft Containment: Limits network access, blocks outbound traffic, and restricts user actions. This approach balances containment with moderate operational impact.
- Monitor-Only: Keeps the device functional while enhancing logging and alerting. This is ideal for critical devices where immediate disruption is not an option [4][5][6].
| Method | Patient Safety Risk | Forensics Quality | Operational Disruption | Time to Implement | Typical Use Cases |
|---|---|---|---|---|---|
| Hard Isolation | High for critical devices; low for non-clinical endpoints | Excellent (full evidence preservation) | High (device becomes unavailable) | Minutes | Workstations with ransomware; compromised billing servers; non-clinical endpoints |
| Soft Containment | Low to moderate | Good (most evidence retained) | Moderate (reduced functionality) | Minutes to hours | EHR workstations with malware; PACS servers with suspicious traffic; clinical devices tolerating restrictions |
| Monitor-Only | Low (maintains function) | Fair (relies on logging) | Minimal | Immediate | Life-sustaining medical devices; systems under investigation; endpoints awaiting downtime |
Playbooks should also distinguish between automated and manual actions. For example, EDR tools can automate host isolation, create incident tickets, block domains, or quarantine devices. For devices requiring human or clinical approval, automation can still pre-stage actions, such as tagging devices in asset management platforms or triggering clinical review tasks. Tools like Censinet RiskOps™ can help ensure automation decisions are informed by accurate assessments of device criticality and patient safety [2][4].
Deploying Technical Controls and Automation
Setting Up EDR and Network Controls
Endpoint Detection and Response (EDR) systems play a key role in automated threat containment for healthcare environments. These systems continuously monitor endpoint activity, flag suspicious behavior, and can take immediate action - like isolating infected devices, terminating harmful processes, or quarantining malicious files - before a threat can spread [2].
To get the most out of EDR, tailor its policies to match the needs of different endpoint types. For example, administrative workstations can have stricter automated responses, such as full isolation or immediate process termination. On the other hand, clinical endpoints, like those in intensive care units or operating rooms, may need more cautious settings. These could include alerting the security team and blocking specific processes without disrupting critical patient care workflows.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
- Terry Grogan, CISO, Tower Health [1]
Network Access Control (NAC) is another essential tool. It ensures that only authorized devices connect to clinical networks and can move noncompliant or suspicious endpoints into restricted VLANs. When integrated with EDR, NAC can respond to alerts by quarantining compromised devices at the network level. Pairing NAC with microsegmentation - dividing networks into tightly controlled zones for systems like electronic health records, imaging, pharmacy, and IoMT devices - further restricts lateral movement, containing threats within minutes [4][6].
Next-generation firewalls add another layer of defense, using application-aware rules and intrusion prevention to block malicious traffic. Secure DNS filtering can stop connections to known harmful domains or command-and-control servers. For example, if EDR detects ransomware activity on a workstation, NAC can quarantine the device while the firewall and DNS filtering block its outbound communication - achieving containment in seconds [3][4].
Containment Approaches for Medical and IoMT Devices
While EDR and NAC can protect most endpoints, medical and IoMT devices often require a different approach. These devices pose unique challenges - they may not support EDR agents due to vendor restrictions, FDA approvals, or patient safety concerns [8][9][11]. As a result, containment for these devices often relies on network-level controls rather than direct actions on the devices themselves.
One effective strategy is creating restricted clinical zones with tightly controlled access. For instance, if an infusion pump shows unusual behavior, it can be moved to a segment that only allows communication with its medication management system and time servers, while blocking all other traffic. Similarly, for imaging systems like CT scanners or PACS workstations, internet access can be blocked immediately, restricting connections to only the PACS server, VNA, and domain controllers.
For devices that cannot be patched, virtual patching through intrusion prevention systems or application-layer firewall rules can block exploit traffic, acting as a protective layer. Bedside monitors and telemetry systems can have their traffic restricted to essential systems like the central monitoring server, while remote vendor access is blocked unless urgently needed. Management interfaces should only be accessible through authenticated jump hosts, and unnecessary services - like web browsing or SMB - should be disabled, allowing only essential clinical protocols like DICOM or HL7.
Platforms such as Censinet RiskOps™ provide valuable insights into device criticality and patient safety, helping organizations make informed containment decisions. For devices critical to life support or monitoring, work with clinical leadership to define "safe mode" configurations. These partial containment measures disconnect nonessential networks while ensuring the device continues its local operation, containing threats without risking patient care.
Adding Orchestration and Automation
With technical controls in place, orchestration can tie everything together, making containment actions faster and more efficient. Security Orchestration, Automation, and Response (SOAR) platforms integrate tools like EDR, NAC, firewalls, and SIEM systems to execute multi-step containment workflows based on predefined playbooks. By analyzing logs and alerts across all security systems, SOAR can turn high-confidence detections into automated responses [3][4].
To balance speed and safety, use risk-tiered automation. For low-risk assets like kiosks and office PCs, fully automate containment. For example, if EDR detects ransomware, SOAR can isolate the endpoint, move it to a restricted VLAN, block its network traffic, and open a high-priority incident ticket. For high-impact systems in clinical environments like ICUs or PACS, adopt a "human-in-the-loop" model. Here, SOAR prepares a containment plan and waits for approval from security staff and clinical leaders before taking action.
Integrating SOAR with IT Service Management (ITSM) systems can further streamline response efforts. Automated workflows can attach forensic data - such as EDR timelines or network flow details - to incident tickets, and device statuses can be updated as analysts adjust containment actions. This reduces the time needed to contain incidents from hours to minutes while ensuring patient safety is not compromised. To maintain oversight, require multi-factor approval for high-impact actions, log all automated steps for compliance with HIPAA, and regularly review automation rules to minimize false positives and adapt to clinical needs.
Start with a monitoring phase to understand traffic patterns and clinical workflows before enforcing containment rules. This minimizes disruptions during deployment [6][10]. Conduct tabletop exercises and breach simulations to test and refine workflows, ensuring triggers, escalation paths, and exceptions are well-defined. This approach ensures automation enhances security without interfering with clinical operations [6][7][10].
sbb-itb-535baee
Running and Improving Containment Protocols
Adding Protocols to Incident Response
Endpoint containment protocols are only effective when seamlessly integrated into daily incident response workflows. To achieve this, embed detailed containment decision trees into every phase of incident response (IR). This ensures that alerts automatically trigger clear actions like isolation, account restrictions, or network segmentation. Customize runbooks for different endpoint types - such as clinical workstations, EHR servers, nurse workstations-on-wheels, telehealth devices, and medical/IoMT devices - and align these with common threats like ransomware, phishing-related malware, or unauthorized remote access.
Each playbook should outline authorized triggers, tools for isolation, clinical impact thresholds (e.g., ensuring life-support systems are not hard-isolated without a safe alternative), and documentation steps that comply with HIPAA and internal policies. Establish a cross-functional incident "bridge" team to address situations where containment actions could affect patient care or regulated data. While IT and security teams manage the technical response, appoint clinical liaisons - such as a nursing supervisor or CMIO delegate - to evaluate the clinical impact of isolating endpoints. Meanwhile, compliance and risk management teams, often led by the privacy officer or CISO, should document reportable events, assess HIPAA implications, and coordinate notifications with legal and communications teams.
Set Service Level Agreements (SLAs) to ensure IT notifies the clinical liaison within five minutes of initiating a high-severity containment action. Use secure communication channels and simplified status indicators (like green/yellow/red impact levels) to help non-technical leaders quickly understand the situation. To minimize disruptions in clinical workflows, implement tiered containment modes, such as "monitor only", "restrictive", and "full isolation", based on endpoint criticality and time of day. For non-critical endpoints like kiosks or administrative laptops, automated EDR isolation may suffice. For critical clinical systems, start with network microsegmentation, such as blocking malicious domains via DNS filtering or restricting outbound traffic while maintaining essential communications. These structured protocols form the foundation for further testing and improvements, as outlined in the next section.
Testing and Validating Protocols
Defining protocols is just the beginning - rigorous testing is essential to ensure they work as intended. Conduct tabletop exercises and simulations to validate containment steps, communication processes, and decision-making under pressure. These exercises should mimic realistic, high-stakes scenarios, such as ransomware infecting an imaging workstation or suspected malware appearing on a medication dispensing system. Participants should navigate detection, triage, containment decisions, clinical consultations (e.g., deciding whether to divert patients or initiate downtime), and communication with leadership and compliance teams.
Involve both IT/security and clinical leaders in these exercises. Use real network diagrams and asset inventories, test escalation thresholds (e.g., when to activate incident command), and document the timeline of every decision and action. After-action reports should highlight gaps in playbooks, unclear roles, tool limitations, and training needs. These reports should include actionable recommendations and assign responsibilities for addressing any issues. Conduct these exercises at least annually and whenever there are major changes to technology or policies to ensure protocols stay aligned with evolving threats and regulatory requirements.
Organizations can also work with internal red teams or external assessors to run controlled simulations that test tools like EDR, NAC, and segmentation responses without putting patient care at risk. Before starting these simulations, collaborate with clinical leadership to exclude life-critical systems, schedule during maintenance windows or low-activity periods, and establish clear rollback plans. Track metrics such as detection rates, time from detection to containment, accuracy in identifying endpoints, and any unintended consequences (like blocking legitimate traffic). These results provide valuable insights for refining protocols.
Measuring Results and Making Updates
Once protocols are implemented and tested, continuous measurement and refinement are key to improving containment strategies. Track metrics like Mean Time to Contain (MTTC) - the average time from confirmed threat detection to effective containment - and endpoint containment coverage, which measures the percentage of in-scope devices (such as workstations, servers, and medical/IoMT devices) that can be isolated or restricted using documented procedures. Additional metrics include the percentage of incidents contained before lateral movement occurs, the number of clinically significant service disruptions caused by containment actions, the false positive rate for automated containment, and the proportion of critical endpoints with updated and tested playbooks.
Use dashboards and leadership reviews to identify priorities, such as expanding EDR coverage or improving network segmentation. These reviews also serve as evidence of compliance for regulators and auditors. Establish a formal post-incident review process to analyze MTTC, root causes, control performance, and patient-care impact following significant incidents or exercises. These reviews should identify successful containment steps, areas of delay or confusion (e.g., unclear authority to isolate a radiology workstation), and whether policies need adjustments to address emerging threats. Based on these findings, update playbooks, refine automation thresholds, extend tool coverage, improve segmentation strategies, and revise training materials for both technical and clinical teams.
Trend analysis - such as reductions in MTTC or increases in endpoint coverage - can guide strategic planning and budgeting while demonstrating ongoing improvements in compliance with HIPAA and other regulatory standards. If using a platform like Censinet RiskOps™, incorporate lessons learned into third-party risk assessments and enterprise risk management strategies to ensure endpoint containment aligns with broader cybersecurity and vendor risk management goals.
Conclusion and Key Takeaways
To effectively manage endpoint threats in healthcare, a comprehensive and structured approach is essential. It starts with establishing clear governance and decision-making roles across security, IT, clinical engineering, and compliance teams. Prioritizing endpoints based on their clinical importance and the sensitivity of the data they handle is equally critical. Standardized playbooks for common scenarios - like ransomware attacks on workstations or compromised medical devices - should outline triggers, containment strategies, and escalation protocols.
Deploying tools like Endpoint Detection and Response (EDR) and network controls with policy-based isolation can help contain threats in seconds. For medical and IoMT devices, network-level containment - such as segmentation, access restrictions, and monitoring - should take precedence over full isolation to minimize risks to patient care. This approach integrates seamlessly into the broader incident response framework. Considering that healthcare data breaches cost an average of $10.93 million per incident, swift and effective containment is not just a regulatory necessity but also a financial safeguard [2].
Regular testing and refinement of protocols are equally important. Tabletop exercises and simulations involving both technical and clinical leaders can uncover weaknesses and improve response times. Metrics like mean time to contain (MTTC) and clinical impact should be monitored, and playbooks updated after major incidents. Aligning these strategies with HIPAA, HHS 405(d) guidelines, and frameworks like NIST CSF ensures compliance while supporting enterprise risk management. Platforms like Censinet RiskOps™ can further integrate endpoint containment insights into broader risk management efforts, creating a unified approach to safeguarding patient data and medical devices.
Endpoint containment must be treated as an evolving program, adapting to new threats, technologies, and regulatory changes. Collaboration across security, clinical, and compliance teams ensures that containment measures are both effective and safe for patient care. Metrics should be reviewed regularly as quality indicators, with investments directed toward addressing any gaps. By combining strong governance, automation, and continuous improvement, healthcare organizations can respond to threats faster, reduce the impact of breaches, and protect both their patients and their operations.
FAQs
What’s the difference between hard isolation and soft containment for endpoint threats?
When dealing with an infected endpoint, hard isolation takes a no-nonsense approach. It completely cuts off the endpoint from the network, severing all communication channels. This method acts as an impenetrable barrier - whether enforced physically or through network controls - ensuring the threat can't spread any further.
On the other hand, soft containment is more flexible. Instead of a full disconnect, it limits the endpoint's network activity to specific resources or functions. This approach allows for continued monitoring and controlled actions, keeping the endpoint partially connected to avoid major disruptions to operations.
Both strategies play important roles in managing endpoint threats. The choice between them depends on the severity of the threat and how much operational continuity your organization needs to maintain.
What steps can healthcare organizations take to ensure endpoint containment strategies meet HIPAA requirements?
To meet HIPAA requirements, healthcare organizations need to prioritize strong security measures for endpoint containment. This involves enforcing strict access controls, encrypting protected health information (PHI), keeping detailed audit logs, and crafting policies that align with HIPAA's security guidelines.
Using specialized risk management tools designed for healthcare can simplify compliance efforts. These tools can automate risk assessments, identify vulnerabilities, and ensure security protocols are consistently applied. By following these practices, organizations not only stay compliant but also strengthen the protection of sensitive patient information.
What is the role of clinical leaders in creating and implementing endpoint threat containment protocols?
Clinical leaders play a key role in designing and implementing endpoint threat containment protocols. Their clinical expertise ensures that these protocols are not only aligned with healthcare operations but also prioritize patient safety above all else. By bridging the gap between IT teams and clinical staff, they help develop strategies that effectively identify and address potential threats while keeping disruptions to patient care to a minimum.


