Cancer Center Vendor Risk: Oncology Equipment, Drugs, and Treatment Safety
Post Summary
Cancer centers depend on third-party vendors for critical services like oncology equipment, drug supply, and treatment systems. However, these partnerships come with risks that can threaten patient safety and disrupt care. Here's what you need to know:
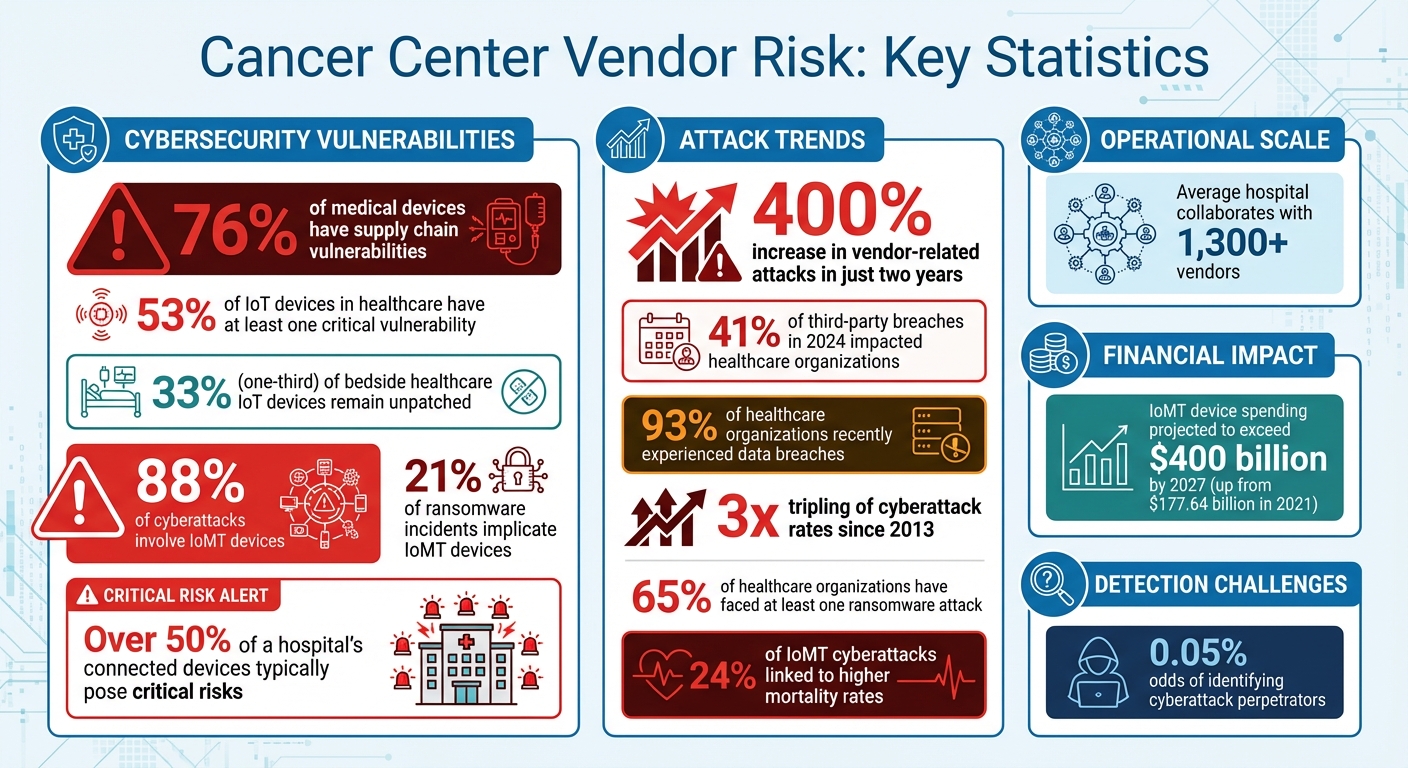
- Cybersecurity Threats: Over 76% of medical devices have supply chain vulnerabilities, and ransomware attacks on vendor systems can delay treatments and expose sensitive patient data.
- IoMT Risks: More than half of healthcare IoT devices have critical vulnerabilities, putting patients at risk during cyber incidents.
- Regulatory Compliance: Vendors must meet HIPAA and FDA standards to ensure patient data protection and device security.
- Drug Supply Chain Weaknesses: Breaches in multi-tiered supply networks can disrupt chemotherapy deliveries.
Cancer centers must implement vendor risk management programs, continuous monitoring, and AI-powered tools to mitigate these risks. Proactive measures like secure onboarding, incident response planning, and centralized dashboards are key to maintaining uninterrupted care and protecting patient safety.
Cancer Center Vendor Risk Statistics: Cybersecurity Threats in Healthcare
Cybersecurity Risks in Oncology Vendor Networks
Cancer centers face distinct cybersecurity challenges when working with vendors supplying oncology equipment and pharmaceuticals. These risks arise from the critical role of cancer treatment technologies, the complexity of interconnected medical devices, and the sensitive patient data exchanged across vendor networks. Addressing these vulnerabilities is crucial to safeguarding patient safety and maintaining uninterrupted treatment. Below, we explore key concerns such as ransomware threats, IoMT vulnerabilities, and risks within the drug supply chain.
Ransomware and Data Breaches in Oncology Supply Chains
Ransomware attacks can bring oncology systems to a standstill - disabling radiation equipment, exposing protected health information (PHI), and delaying vital treatments. When a vendor's system is compromised, attackers can interfere with treatment planning software, causing significant disruptions to patient care [1][2].
Recovery from such incidents often requires extensive resources, including overhauling treatment schedules, which can result in substantial financial losses [2]. For patients, the consequences are far-reaching: delays in care increase anxiety, exposed personal data heightens privacy concerns, and identity theft can lead to financial hardship [2].
Security Gaps in Oncology Equipment and Internet of Medical Things (IoMT)
Oncology equipment connected to hospital networks significantly broadens the attack surface. Studies reveal that 53% of IoT devices in healthcare have at least one critical vulnerability, while one-third of bedside healthcare IoT devices remain unpatched, jeopardizing service availability, data security, and patient safety [4]. Even more concerning, 88% of cyberattacks involve IoMT devices, and 24% of these incidents are linked to higher mortality rates [7].
Radiation oncology facilities are particularly at risk due to their reliance on interconnected systems for treatment planning and data sharing [2][1]. Many IoMT devices lack standardized security protocols, and manufacturers often delay releasing patches, leaving devices exposed to known threats [3]. In fact, IoMT devices are implicated in 21% of ransomware incidents, and over half of a hospital's connected devices typically pose critical risks [7].
The financial impact of these vulnerabilities is growing. Spending on IoMT devices is projected to surpass $400 billion by 2027, a sharp increase from $177.64 billion in 2021 [5]. This surge, driven by the COVID-19 pandemic and the rise of remote medical care, has introduced new security and privacy challenges [5][6]. Beyond equipment vulnerabilities, the complexity of the drug supply chain adds another layer of cybersecurity risks.
Fourth-Party Risks in Drug Supply Chains
The intricate nature of drug supply chains introduces additional cybersecurity threats. Pharmaceutical vendors often rely on a web of suppliers, distributors, and technology providers to manage inventory, track shipments, and process orders. Each layer in this network represents a potential vulnerability.
When a breach occurs at any point in the supply chain, the effects can ripple through the system - disrupting chemotherapy deliveries and exposing sensitive treatment data [1]. The reliance on multi-tiered supplier networks amplifies the risk, as a single weak link can jeopardize the entire chain. This highlights the need for cancer centers to not only secure their direct partnerships but also monitor the cybersecurity practices of their vendors' partners.
Regulatory and Compliance Requirements
Cancer centers and their partners must navigate strict regulations to protect patient data and ensure the safety of medical devices. Falling short of these requirements can lead to hefty fines, legal trouble, operational setbacks, and a loss of patient confidence [8]. Below, we break down the critical compliance areas for managing patient information and securing oncology devices.
HIPAA Compliance for Vendor-Handled PHI
Vendors handling Protected Health Information (PHI) are required to meet the stringent standards set by HIPAA. Cancer centers must verify that vendors have up-to-date privacy policies, properly obtain patient consent, and implement clear breach notification procedures with thorough documentation [8]. To minimize risks, organizations should:
- Use multi-layered security measures.
- Encrypt patient data during transmission and while stored.
- Implement strict role-based access controls paired with mandatory multi-factor authentication (MFA).
Trusting vendors solely based on self-certifications is risky. Independent third-party assessments are crucial to ensure the vendor's security measures are genuinely robust [9].
FDA Cybersecurity Requirements for Oncology Devices
Oncology devices often operate within vulnerable networks, making compliance with FDA cybersecurity standards essential. The FDA has ramped up its focus on medical device security [12][13][14]. Under Section 524B of the FD&C Act and the June 2025 guidance titled "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions," manufacturers must prove their devices have strong cybersecurity protections before they can be marketed [12][13][15][16]. Failure to comply may result in devices being classified as adulterated or misbranded, exposing manufacturers and healthcare providers to federal enforcement actions.
Cancer centers must carefully evaluate vendors by reviewing their security protocols, encryption methods, regulatory compliance, and history of security incidents [11]. Keeping up with changing regulations and discontinuing partnerships with vendors who fail to adapt can protect patient safety and shield institutions from potential liabilities [10].
Vendor Risk Assessment and Mitigation Methods
Vendor-related attacks have skyrocketed by over 400% in just two years [19], with 41% of third-party breaches in 2024 impacting healthcare organizations [20]. Considering that the average hospital collaborates with more than 1,300 vendors [20], having a well-structured approach to assessing and addressing these risks is no longer optional - it's essential. Below are some strategies tailored to meet the challenges of this evolving threat landscape.
Continuous Monitoring of Third-Party Vendors
Gone are the days when a yearly review was enough. Continuous monitoring allows cancer centers to keep a dynamic inventory of their vendors, enabling them to classify and address risks in real time [18]. This approach involves comprehensive reviews that examine technical, legal, and policy aspects of Third-Party Risk Management (TPRM) programs and Business Associate Agreements (BAAs) [17]. Moreover, vendors must now meet cybersecurity and cyber insurance standards that align with their specific risk profiles [17]. Platforms like Censinet RiskOps™ provide tools for benchmarking cybersecurity performance, helping cancer centers track vendor compliance with industry standards and detect emerging threats before they become critical.
AI-Powered Tools for Vendor Oversight
Building on the foundation of continuous monitoring, AI-powered tools bring much-needed efficiency to vendor oversight. Traditional manual assessments demand significant resources, but tools like Censinet AITM™ can transform this process. These tools enable vendors to complete security questionnaires in seconds, automatically summarize supporting documentation, and capture details about product integrations and fourth-party risks. The system generates comprehensive risk summary reports, helping healthcare organizations address vulnerabilities more effectively. By automating routine tasks while preserving human oversight for critical decisions, these tools are especially useful in oncology supply chains, where complex fourth-party relationships can hide risks that traditional methods might miss.
Secure Vendor Onboarding Practices
Effective vendor risk management starts well before contracts are signed. Cancer centers should establish dedicated Vendor Risk Management (VRM) teams, including representatives from executive leadership, legal, compliance, IT, and procurement. For example, Adobe’s vendor program requires suppliers to complete detailed questionnaires and provide certifications like SOC 2 Type II, PCI DSS, or ISO 27001. Vendors categorized as medium or high risk must also undergo remediation steps and agree to continuous monitoring and annual reviews [19]. Similarly, Microsoft’s Supplier Security and Privacy Assurance Program ensures vendors comply with all necessary data protection measures before offering services [19].
To ensure thorough vetting, cancer centers should conduct two separate risk assessments for each vendor - one focused on information security and another on compliance. Vendors must provide measurable proof of compliance, such as logs, audit records, and metrics detailing anti-phishing training or endpoint device policies. For oncology equipment vendors, this might also include penetration tests on connected devices before they are integrated into the network. Such rigorous onboarding practices protect oncology treatments and enhance patient safety. Tools like Censinet One™ simplify this process by enabling cancer centers to evaluate new vendors quickly and thoroughly, ensuring their systems remain secure from the start.
sbb-itb-535baee
Incident Response and Recovery in Oncology Operations
Cyberattacks pose serious risks to oncology operations, where delays in treatments like radiation therapy for cancers such as head and neck, cervical, vulvar, anal, and medulloblastoma are directly tied to poorer tumor control outcomes [2]. With over 93% of healthcare organizations recently experiencing data breaches [22] and the rate of cyberattacks tripling since 2013 [24], cancer centers must be prepared with strong response plans. Just as proactive vendor management is vital, a swift and coordinated incident response is crucial to safeguarding patient care during disruptions. This calls for clear, actionable strategies that prioritize getting clinical operations back on track quickly.
Creating Playbooks for Ransomware and Cyber Incidents
An effective incident response plan should put clinical continuity front and center. Cancer centers need to ensure they have access to each patient’s current and planned treatment doses, even without their oncology information system (OIS), and establish methods to resume treatments as quickly as possible [1]. Offline backups are essential to verify active treatments, monitor progress, and log delivered doses. These measures help prevent errors like misidentifying patients, incorrect treatment tracking, or dosing mistakes during ransomware incidents [24].
Regional response plans are another critical component, as they allow facilities to work together to maintain care continuity during cyber outages [1][21]. This type of coordination ensures that patients can still receive treatment even if one center is compromised. Aligning cybersecurity strategies with the NIST Cybersecurity Framework adds another layer of preparedness by providing a systematic approach to evaluating risks, identifying vulnerabilities, and addressing gaps in remediation [23][25].
In addition to these plans, centralized dashboards can play a key role in maintaining oversight and ensuring a coordinated response.
Using Centralized Dashboards for Risk Management
Centralized dashboards give organizations real-time visibility into their security posture and compliance, making them invaluable during an incident. By maintaining detailed logs of device communications, policy decisions, and security events, these tools allow for thorough analysis and help meet FDA compliance requirements. During a ransomware attack, this visibility enables Governance, Risk, and Compliance teams to quickly identify affected systems, assess the scope of the breach, and implement an effective response.
Censinet RiskOps™ is an example of a platform designed to centralize incident management across oncology operations. Acting as a command center, it routes critical findings and tasks to the appropriate stakeholders, ensuring the right teams address the right issues promptly. This level of coordination is particularly important when vendor-related incidents threaten patient care, as it allows cancer centers to implement security measures without interrupting vital treatments [26].
Conclusion
Cancer centers are increasingly vulnerable to cybersecurity threats that directly affect patient safety and treatment outcomes. Alarmingly, vendor-related attacks have surged by over 400% in just two years, and more than 65% of healthcare organizations have faced at least one ransomware attack [19]. These statistics highlight the pressing need for robust security measures, especially in areas like radiation oncology, where treatment delays can have serious consequences for patients.
Under HIPAA regulations, vendor risk management isn't just a recommendation - it's a requirement. Protecting patient data and ensuring the functionality of clinical operations means addressing risks across medical devices, pharmaceutical suppliers, and IoMT (Internet of Medical Things) systems. A well-structured, systematic approach to managing these risks is key to creating effective and integrated solutions.
Platforms like Censinet RiskOps™ offer a practical example of how centralized monitoring can help mitigate these challenges. By consolidating vendor risk management processes, such platforms provide real-time security insights and route critical findings to the appropriate teams. This level of coordination is crucial, particularly when vendor-related incidents could disrupt radiation therapy or expose sensitive patient information.
The stakes couldn't be higher. Poor vendor oversight can lead to financial losses and damage to a cancer center's reputation - costs that far outweigh any perceived savings [19]. As discussed, managing third-party cybersecurity risks is essential for ensuring uninterrupted oncology care. Cancer centers that prioritize comprehensive vendor risk management are better equipped to safeguard patient data, maintain treatment schedules during cyber incidents, and meet strict regulatory requirements. With the odds of identifying cyberattack perpetrators as low as 0.05% [1], proactive measures are the cornerstone of safe, reliable cancer care. Taking these steps is not just about compliance - it's about protecting lives and ensuring continuous, effective treatment.
FAQs
What steps can cancer centers take to secure IoMT devices from vulnerabilities?
Cancer centers can protect their IoMT (Internet of Medical Things) devices by taking a few essential steps. Enforcing strict access controls ensures that only authorized staff can use these devices, keeping them secure from unauthorized interactions. Keeping up with regular software updates and patches is another critical step, as it helps fix known vulnerabilities and guards against new security threats.
Performing thorough risk assessments can uncover potential weak points in the system. Meanwhile, consistent staff training on cybersecurity best practices minimizes the chances of accidental breaches. Another effective measure is network segmentation, which separates IoMT devices from more sensitive systems, limiting the potential impact of a security issue. Together, these strategies help protect patient data and ensure the safety of critical medical devices.
What are the essential elements of a successful vendor risk management program?
A robust vendor risk management program is essential for protecting patient safety, securing sensitive data, and staying compliant with regulations. Start by creating a detailed inventory of all vendors to maintain clear oversight of your supply chain. Then, perform in-depth risk assessments to uncover vulnerabilities and prioritize actions to address them.
Make sure your vendor contracts include specific cybersecurity and compliance requirements to set clear expectations and hold vendors accountable. Use real-time monitoring to quickly identify and mitigate risks, and have well-prepared incident response plans in place to manage potential breaches effectively. Additionally, leverage automation tools to improve efficiency and transparency, and establish proper offboarding protocols to ensure a smooth and secure end to vendor partnerships.
How can ransomware attacks disrupt oncology treatment schedules?
Ransomware attacks pose a serious threat to oncology treatment schedules by targeting hospital systems and critical infrastructure. These attacks can lock healthcare providers out of patient records, delay crucial diagnostic procedures, or even disable life-saving medical equipment. The result? A direct impact on the timely delivery of care.
The fallout from such disruptions is significant. Treatments may be delayed, adding stress for both patients and medical staff. Even more concerning, these interruptions can jeopardize patient safety. To counter these risks, healthcare facilities must prioritize strong cybersecurity defenses and implement thorough vendor risk management practices. These steps are essential to keeping oncology care running smoothly and ensuring patients receive the care they need without delay.
Related Blog Posts
- Building Vendor Risk Frameworks for Healthcare IT
- Medical Device Vendor Risk Management: FDA Compliance and Patient Safety Best Practices
- Insurance and Benefits Administration Vendor Risk for Healthcare Organizations
- Rehabilitation Hospital Vendor Risk Management: Specialized Equipment and Patient Safety


