Change Management for Healthcare TPRM Programs: Overcoming Resistance and Driving Adoption
Post Summary
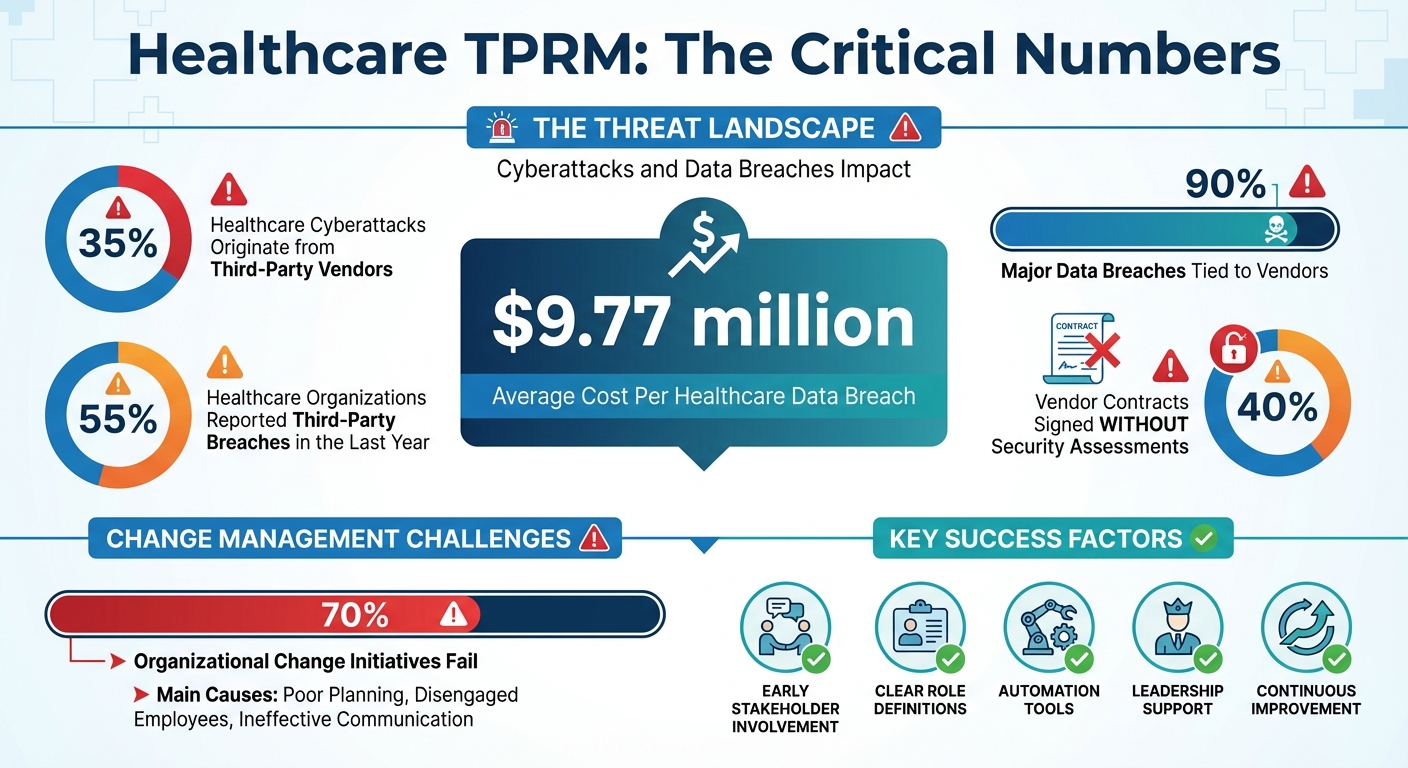
Healthcare organizations face a major challenge: third-party vendors are responsible for 35% of cyberattacks in the industry, and breaches cost an average of $9.77 million per incident. Despite these risks, 40% of vendor contracts are signed without security assessments. To address these vulnerabilities, healthcare providers must implement effective third-party risk management (TPRM) programs. However, success requires more than tools and policies - it demands a structured change management approach to overcome internal resistance and ensure adoption.
Key Points:
- Why TPRM Matters: 55% of healthcare organizations reported third-party breaches last year, with 90% of major data breaches tied to vendors.
- Barriers to Change: Manual processes, siloed teams, vendor fatigue, and outdated systems undermine TPRM efforts.
- Solutions: Early stakeholder involvement, clear role definitions, automation tools like Censinet RiskOps™, and leadership support are critical for success.
- Leadership Buy-In: Highlight financial risks, regulatory updates like the January 2025 HIPAA changes, and ROI to secure executive approval.
- Continuous Improvement: Regular testing, defined workflows, and performance tracking help maintain TPRM effectiveness.
Bottom Line: A well-executed change management strategy ensures that TPRM programs protect patient data, reduce risks, and align with evolving regulations.
Healthcare Third-Party Risk Management Statistics and Key Challenges
Recognizing and Reducing Resistance to Change
Where Resistance Comes From
Resistance often stems from the discomfort of uncertainty [8]. In healthcare TPRM programs, this is compounded by the intricate nature of existing systems and deeply rooted practices [9][10]. Statistics show that nearly two-thirds of change initiatives fail, with about 70% of organizational changes falling short of their goals due to poor planning, disengaged employees, and ineffective communication [11][13].
For physicians, resistance can arise when new TPRM requirements are perceived as unnecessary or lacking clear value. They may see these changes as just more paperwork [13]. IT teams, on the other hand, may worry that new vendor assessment processes will stretch their already limited resources even thinner. Third-party vendors often share their own frustrations, particularly when they are repeatedly asked to complete security questionnaires or when certifications quickly become outdated, sometimes within just months [5].
A lack of strong leadership support can make matters worse. Without visible backing from executives and clear communication about the purpose of these changes, TPRM efforts can come across as low-priority administrative tasks rather than meaningful, strategic initiatives.
Addressing these challenges requires focused strategies to break down resistance and encourage acceptance.
Practical Solutions to Remove Barriers
Reducing resistance begins with involving stakeholders early in the process. Engaging clinicians, IT teams, procurement staff, and vendors from the start of the TPRM program design ensures their voices are heard [12][13]. When stakeholders understand how these changes enhance patient care and improve operational efficiency, they’re more likely to support them. Encouraging "bottom-up" input - where those on the front lines contribute ideas - can also lead to practical solutions and stronger buy-in [13].
Identifying and empowering change champions within different departments is another key step. These individuals can act as bridges between leadership goals and day-to-day operations. Providing them with ongoing training and support networks helps maintain alignment and momentum [11][12]. For technology rollouts, using phased approaches or pilot programs can address potential issues without disrupting clinical workflows [12].
Highlighting how automation can reduce workloads is also essential. Tools like vendor assessments, continuous monitoring, and streamlined workflows can save time and effort, rather than adding to existing burdens [12][14]. Regular feedback sessions allow teams to refine strategies based on real-world experiences, ensuring that the program meets diverse needs [12][13]. And don’t underestimate the power of celebrating small wins - recognizing these achievements can keep morale high and maintain progress [11].
Building Leadership Support and Governance Alignment
Getting Executive Approval
To gain executive approval for Third-Party Risk Management (TPRM) initiatives, it’s crucial to tie them directly to financial and reputational stakes. The numbers speak volumes: in healthcare, the average cost of a data breach hit $9.77 million, and over the past year, 55% of healthcare organizations reported breaches linked to third-party vendors. Even more concerning, 35% of all healthcare cyberattacks originated from these third parties [2][5]. Using visual dashboards to present these risks makes the impact clear and actionable for decision-makers.
The urgency becomes even more apparent when you consider that 40% of vendor contracts in healthcare are finalized without any security risk assessment, leaving organizations exposed [2]. Real-world examples, like the Change Healthcare breach, illustrate how vulnerabilities in third-party systems can ripple through and disrupt entire healthcare networks [2]. To strengthen your case, calculate the return on investment (ROI): compare the $9.77 million potential breach cost to the resources needed to implement a robust TPRM program [5].
"There's hope. Every incident, every headline, is a chance to move forward. Keep making the case." - Tamra Durfee, vCISO, Fortified Health Security [3]
Regular stakeholder meetings are another critical step. These sessions ensure that key risk indicators and cybersecurity performance remain top of mind across all organizational levels [5]. Additionally, the proposed updates to the HIPAA Security Rule, announced on January 6, 2025, introduce new mandates for comprehensive risk assessments and ongoing monitoring, adding regulatory weight to the argument for TPRM [5].
Creating Centralized Oversight
Once executive support is secured, the next step is establishing structured governance. This means bringing together teams from risk management, compliance, procurement, security, and commercial operations right from the beginning [4]. Centralized oversight addresses one of healthcare TPRM’s biggest challenges: bridging the gaps between departments. Clearly defining roles and responsibilities for managing third-party risks avoids confusion and ensures accountability [1].
Standardizing onboarding processes is another critical piece. Precontract checklists can help weed out low-risk vendors early, allowing teams to focus their efforts on those that pose significant risks [5]. A centralized vendor inventory that tracks all third parties with system access is essential for maintaining oversight [4]. Additionally, implementing risk tiering - categorizing vendors based on their criticality and risk level - helps prioritize due diligence and allocate resources effectively [4].
Aligning your TPRM program with established frameworks like NIST CSF 2.0 ensures that assessments follow recognized best practices [5]. Cross-functional impact analysis, involving input from multiple departments, can reveal risks that a single team might overlook [1]. To further strengthen governance, integrate cyber incident response plans into your organization’s broader emergency preparedness strategy. This ensures smoother coordination when issues arise [6]. While maintaining a stable core framework, keep governance adaptable to accommodate strategic shifts [1].
Building Adoption Through Training and Communication
Educating Stakeholders
Training shouldn't be limited to just one team - it needs to reach everyone involved in purchasing technology, services, or supplies. Why? Because understanding third-party cybersecurity requirements and risks is crucial for managing vendor-related issues effectively. This includes educating teams in risk management, compliance, procurement, security, and commercial operations on how to identify and address information security risks. With this knowledge, they can track vendor issues and ensure remediation efforts stay on course [5][6].
It’s not just internal teams that need this training - your third-party vendors should be part of the process too. Regularly involving them in downtime drills and cyberattack simulations can strengthen their incident response skills. These exercises simulate real-world scenarios, helping everyone stay prepared and emphasizing the importance of working together during a crisis [6].
When planning your training programs, think bigger. Make them a key part of a larger change management strategy [1]. Tools like visual dashboards can be incredibly helpful here, as they showcase risk data in a way that's easy to understand. This approach reinforces the importance of strong third-party risk management (TPRM) training. Well-structured training not only clarifies responsibilities but also lays the groundwork for smooth communication across teams.
Defining Clear Roles and Responsibilities
Training alone isn’t enough - success hinges on clearly defined roles. Without clarity, responsibilities can fall through the cracks, weakening your TPRM efforts. But when roles are well-defined, accountability improves, ensuring vendor follow-ups and risk remediation don’t get overlooked [3][7].
To make this happen, structured governance is essential. Create a communication plan that outlines TPRM updates and establishes clear protocols. For example, include service-level agreements (SLAs) that define expectations for escalating and resolving vulnerabilities. This ensures vendor risks are addressed promptly and efficiently [1][2][5][7]. When everyone knows their role and the timelines involved, the chances of missing critical vendor-related risks drop significantly.
sbb-itb-535baee
Using Automation with Censinet RiskOps™
Automating Assessments and Monitoring
Manual risk assessments can eat up valuable time that could be spent on more strategic tasks. That’s where Censinet RiskOps™ steps in, automating repetitive processes and centralizing data to simplify third-party risk evaluations and compliance monitoring.
With the help of Censinet AI™, vendors can complete security questionnaires in just seconds. The system automatically summarizes vendor-provided evidence, logs integration details, identifies fourth-party risks, and generates detailed risk reports. This means you can handle more assessments without needing to bring in additional staff. Plus, real-time data aggregation keeps you in the loop, so you can address emerging issues as they arise.
This efficient system doesn’t just speed up assessments - it lays the foundation for smoother collaboration across your teams.
Improving Collaboration and Efficiency
A centralized platform can do wonders for breaking down communication barriers between risk, compliance, procurement, and security teams. Censinet RiskOps™ acts as a shared workspace where everyone can access risk data, monitor vendor issues, and coordinate remediation efforts. Its command center features visual dashboards that translate complex risk information into formats that are easy for both technical and non-technical stakeholders to understand.
Censinet AI™ takes collaboration a step further by intelligently routing assessment results and critical tasks to the right people. This ensures that risk management efforts are both efficient and targeted. With real-time data consolidated in one place, governance, risk, and compliance teams can make faster, better-informed decisions. The system doesn’t replace human expertise - it enhances it by streamlining workflows and keeping essential oversight intact while scaling operations effectively.
Maintaining Continuous Improvement in TPRM
Setting Up Risk Reduction Phases
Once you’ve secured leadership buy-in and established strong workflows, the next step is ensuring your Third-Party Risk Management (TPRM) program remains effective over time. This means setting up processes that continuously reduce risks and address vulnerabilities. A structured approach to vendor follow-up, accountability, and remediation is key.
Start by designing clear remediation workflows that include defined escalation paths. For instance, if you uncover a critical issue - like a vendor not using multi-factor authentication for privileged access - you need a solid plan in place. Addressing such vulnerabilities often requires collaboration across multiple teams and stakeholders over time [3]. Your remediation process should also include periodic reassessments of vendor risk, especially after significant incidents or changes, to ensure you’re adapting to any shifts in risk exposure [15].
Beyond remediation, it’s important to regularly test your readiness. Conduct downtime drills and simulate cyberattacks to evaluate your defenses. This is especially critical in sectors like healthcare, where 55% of organizations faced third-party breaches between April and June 2023. With the average cost of a healthcare data breach reaching $9.77 million, as noted in IBM's Cost of a Data Breach 2024 report [5], proactive testing can help mitigate costly incidents.
Once you’ve established these remediation and testing processes, the next step is to focus on evaluating your program’s overall performance.
Measuring Program Performance
To understand how well your TPRM program is working, track key metrics like assessment efficiency, remediation progress, and compliance rates [2]. These metrics provide valuable insights into your program’s resilience and effectiveness.
Real-time dashboards can offer a comprehensive view of internal risks, third-party vulnerabilities, and accepted risks across your organization. These tools enable a shift from a purely compliance-driven approach to one that prioritizes resilience [3][15]. Regular reviews are essential to ensure your risk management efforts remain cost-effective. If the cost of controls starts to outweigh the potential impact of a risk, adjustments should be made [15].
Additionally, structured reports for auditors and insurers can showcase your program’s effectiveness. Benchmarking your results against industry standards is another way to pinpoint areas for improvement and demonstrate progress [2].
Conclusion
Managing change effectively in healthcare TPRM requires structured strategies, strong leadership support, and reliable, repeatable processes. With the growing frequency and cost of data breaches, it's clear that healthcare organizations need to modernize. The days of relying on outdated, manual approaches are over - it's time to embrace more dynamic TPRM processes.
Moving from a compliance-focused mindset to one that actively reduces risk requires tools that bring data together, simplify workflows, and provide real-time insights into vendor risks[3]. Solutions like Censinet RiskOps™ make this shift possible by automating assessments, consolidating risk data, and fostering collaboration among security teams, vendors, and stakeholders. This approach helps organizations move away from spreadsheet-based tracking to a scalable, efficient platform. Such advancements set the stage for continuous improvement and long-term resilience.
Change management in TPRM isn’t a one-time effort - it's an ongoing journey that evolves with new threats, regulations, and organizational growth[1]. By combining strong governance, focused training, and advanced technology, healthcare organizations can create a framework that not only protects patient data but also strengthens their operational resilience.
As regulations change - such as the upcoming HIPAA Security Rule update on January 6, 2025[5] - organizations need flexible frameworks that go beyond basic compliance. Those that commit to structured change management will be better prepared to adapt quickly to new requirements while ensuring smooth business operations.
To make risk management part of daily operations, it’s essential to integrate it seamlessly into workflows. When teams understand their responsibilities, have access to user-friendly tools, and see leadership fully engaged, adoption becomes second nature. This integration ensures that risk management becomes a natural and effective part of the organization’s culture.
FAQs
What are effective ways for healthcare organizations to address resistance to changes in TPRM programs?
Healthcare organizations can tackle resistance to updates in third-party risk management (TPRM) programs by prioritizing clear communication and fostering collaboration. A great starting point is securing executive support. When leadership visibly backs the initiative, it sends a strong message about its importance and alignment with the organization's broader goals. Use visual aids and straightforward messaging to highlight the advantages of these changes to all stakeholders.
Getting employees involved early is another key step. Include them in the planning and decision-making process to ensure their voices are heard. Conducting impact analyses can help illustrate how the changes will streamline workflows, minimize risks, and improve compliance with industry standards. To ease the transition, offer ongoing training so staff feel equipped and confident in adopting new procedures.
Lastly, create a structured change management plan. This should include regular feedback opportunities, clearly defined responsibilities, and avenues for collaboration. By maintaining transparency and addressing concerns head-on, you can build trust and encourage successful implementation of TPRM program updates.
How does leadership influence the success of TPRM adoption in healthcare?
Strong leadership plays a key role in successfully adopting third-party risk management (TPRM) in the healthcare sector. Leaders set the direction by outlining clear priorities, promoting accountability, and encouraging a mindset of ongoing improvement. Their involvement ensures that every department is aligned and working toward common objectives.
Leadership is also critical for gaining executive support, securing necessary resources, and keeping the organization focused on compliance, cybersecurity, and managing risks effectively. By steering organizational commitment, leaders lay the groundwork for a TPRM program that is both effective and sustainable.
Why is automation critical for third-party risk management in healthcare?
Automation plays a key role in healthcare third-party risk management (TPRM) by streamlining intricate tasks, reducing manual errors, and delivering quicker, more precise risk assessments. With automated processes handling data collection, risk scoring, and compliance tracking, organizations can shift their focus to addressing critical risks instead of getting caught up in time-consuming administrative duties.
One of the standout benefits of automation is real-time risk monitoring, which is crucial in the ever-evolving healthcare landscape. It allows organizations to stay ahead by identifying potential threats promptly, adhering to industry regulations, and upholding strong cybersecurity practices. This not only boosts operational efficiency but also strengthens trust with patients and business partners.
Related Blog Posts
- Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
- How to Build a TPRM Team That Actually Reduces Healthcare Risk (Step-by-Step Guide)
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?
- Healthcare TPRM Process Automation: Efficiency Gains and Implementation Strategies


