Checklist for Evaluating Telehealth Security Maturity
Post Summary
Telehealth has transformed healthcare delivery, but its rapid adoption has expanded cybersecurity risks. Vulnerabilities like data breaches, weak encryption, and unauthorized access to electronic protected health information (ePHI) can jeopardize patient safety and lead to regulatory violations. This guide provides practical steps to assess and improve telehealth security maturity by focusing on key areas such as governance, technical safeguards, vendor management, and workforce training.
Key Takeaways:
- Define Your Scope: Identify all telehealth platforms, devices, and workflows, including third-party integrations.
- Inventory Assets and Vendors: Catalog critical devices, software, and vendors handling ePHI.
- Strengthen Security Controls: Implement multi-factor authentication (MFA), encryption, and role-based access controls (RBAC).
- Governance and Compliance: Establish a governance committee, create telehealth-specific policies, and ensure HIPAA compliance.
- Vendor Risk Management: Conduct regular assessments, require business associate agreements (BAAs), and monitor vendor security.
- Workforce and Patient Training: Educate staff and patients on secure telehealth practices to reduce human error.
By addressing these areas systematically, healthcare organizations can mitigate risks, protect patient data, and ensure secure telehealth operations.
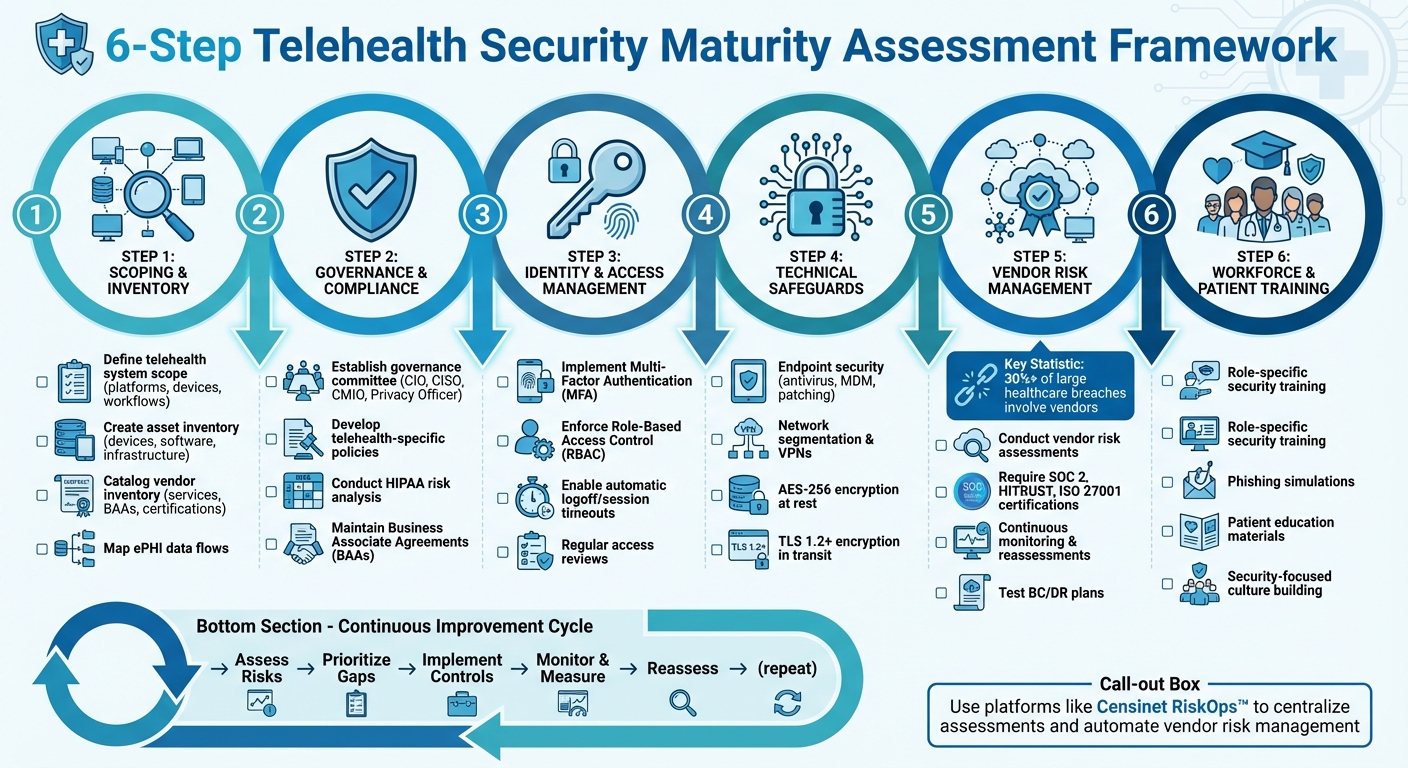
6-Step Telehealth Security Maturity Assessment Framework
Scoping and Inventory
Establish clear telehealth boundaries, take stock of all assets and vendors, and map out ePHI flows to uncover potential vulnerabilities.
Define Your Telehealth System Scope
Start by identifying every channel and workflow where telehealth plays a role in your organization. This includes platforms for video visits, remote patient monitoring (RPM) devices, patient portals, mobile health apps, secure messaging tools, telephonic triage systems, and e-visit platforms. Don't forget the integrations with your EHR, practice management systems, billing software, imaging tools, data lakes, and analytics platforms.
Break down the scope by care setting, clinical specialty, and user type. For U.S.-based organizations, ensure you include all HIPAA-covered entities and business associates involved in telehealth. This also means accounting for third-party platforms with signed Business Associate Agreements (BAAs).
Matt Christensen, Sr. Director of GRC at Intermountain Health, explains, "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." This complexity is especially evident in telehealth, where pilot projects, departmental tools, and shadow IT often operate beyond the reach of central IT oversight. To address this, include every tool - formal or informal - so hidden risks can be identified early.
Create an Asset and Vendor Inventory
Once you've defined your telehealth scope, the next step is cataloging the specific assets and vendors that support your system.
Start with the assets. List all devices used by clinicians (like laptops, tablets, and smartphones) and patients (RPM kits, loaner tablets). Include on-premises infrastructure, IoT devices, and medical equipment. Document telehealth platforms, mobile apps, APIs, middleware, integration engines, and cloud services (IaaS, PaaS, SaaS) that enable telehealth workflows. For data storage, include EHR modules used for telehealth, data warehouses, log archives, cloud storage, and backup systems.
Each asset should be classified by its importance - critical, high, medium, or low - based on factors like patient safety, the amount of ePHI it handles, and regulatory exposure. Capture details such as the asset's name, type, owner, location, use cases, ePHI involvement, and connectivity. This structured approach, aligned with NIST and HIPAA risk frameworks, helps prioritize security investments.
Equally important is your vendor inventory. Document vendor names, the services they provide (e.g., video visits, SMS, payment processing, RPM), hosting models, data residency, HIPAA business associate status, ePHI volume, key integrations, authentication methods, security certifications, risk assessment results, incident history, SLAs, and sub-processor dependencies.
Platforms like Censinet RiskOps™ can simplify this process by centralizing vendor data, streamlining assessments, and enabling continuous monitoring of telehealth vendors, clinical applications, and medical devices.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health
Map ePHI Data Flows
After cataloging your assets and vendors, the next step is to map out how ePHI moves through your telehealth ecosystem.
Track ePHI across every stage of telehealth interactions - scheduling, registration, consent, intake, live visits, documentation, prescribing, billing, and follow-ups. This helps pinpoint areas where risks are most likely to arise.
Use data flow diagrams to illustrate sources, processing points, storage locations, and transmission methods. Include details like data elements, transmission protocols, and security controls. Collaborate with IT, security, clinical operations, and vendor representatives to ensure the diagrams reflect actual workflows, including edge cases like after-hours calls, emergency escalations, and device troubleshooting.
Pay close attention to hotspots where ePHI is most vulnerable. These might include data transmitted over public networks, stored on personal or unmanaged devices, connected via APIs to third-party services, or temporarily stored in logs or browser caches. Areas like video session recording, SMS/email notifications, device pairing, and manual workarounds involving personal devices or consumer apps also deserve scrutiny. For each hotspot, document the existing controls and any gaps, such as unencrypted channels, shared accounts, unmanaged BYOD (Bring Your Own Device), or missing logging capabilities. This detailed mapping helps prioritize fixes to meet HIPAA requirements effectively.
Governance and Compliance Requirements
Effective governance is the backbone of telehealth security, weaving it seamlessly into an organization’s overall strategy. Without a clear structure, well-defined policies, and consistent compliance oversight, even the most advanced technical measures can falter. Governance provides the foundation for enforcing the technical and operational safeguards discussed later.
Establish Governance Structures
Start by forming a telehealth governance committee that includes key stakeholders: the CIO or CISO, CMIO, clinical and nursing leaders, compliance and privacy officers, legal counsel, and risk management professionals. Each member should have a clearly defined charter outlining their decision-making responsibilities. For instance, the CISO would oversee security standards and incident response, while the privacy officer ensures HIPAA privacy compliance. Clinical leaders would manage workflow changes, particularly those affecting patient consent or identity verification.
The governance committee should report quarterly to executive leadership, presenting telehealth security metrics as part of the organization's risk register. Accountability should be embedded into job roles and performance objectives. For example, IT teams can be evaluated on telehealth platform uptime and patching, clinical leaders on adherence to secure workflows, and compliance teams on completing risk assessments and audits on time.
To ensure clarity, use a RACI matrix to define responsibilities and decision-making authority. A telehealth risk dashboard can track critical metrics like security incidents, staff training completion rates, vendor risk assessments, and remediation progress. Decision-making protocols should be explicit: IT cannot deploy a new telehealth platform without approval from privacy and compliance teams, and clinical leadership must sign off on workflow changes impacting patient consent or identity verification.
Develop Telehealth-Specific Policies
Generic IT and HIPAA policies alone won’t cut it. Create a dedicated telehealth security and privacy policy set addressing key areas like acceptable use of telehealth tools, remote access, device security, identity verification, session management, data retention, and vendor usage.
Policies should specify approved platforms and prohibit unvetted consumer apps for handling PHI. Encryption, authentication (e.g., multifactor authentication for clinicians), and clear documentation practices for telehealth encounters must be mandatory. Define how chat messages, images, and videos are stored or excluded and outline scenarios where telehealth is appropriate versus requiring in-person visits.
For remote work, enforce strict device and network security. Require secure, managed devices, and implement BYOD controls through MDM, VPN, and encryption. Home-office setups should meet minimum standards, such as private workspaces, no public Wi-Fi without a VPN, and the use of headsets for privacy. Access from outside the U.S. should either be prohibited or tightly controlled with geo-blocking, explicit approval, and regulatory review to address cross-border data risks.
Identity verification is crucial to prevent fraud or misidentification. Policies should mandate multi-step patient identity verification, such as confirming two identifiers (e.g., name and date of birth) against the EHR or comparing a government-issued ID to the individual on video. For high-risk cases, like prescribing controlled substances, stronger measures like knowledge-based questions or patient portal authentication with multifactor authentication are necessary. Providers should log in via authenticated systems integrated with the EHR, ensuring their name, credentials, and organization are clearly displayed during sessions.
Session management policies should address who can be present during visits, how to document consent for third-party presence, rules against recording unless explicitly permitted, and emergency address verification at the start of each session. Review these policies annually, align them with HIPAA guidance, and communicate them through formal training sessions with attestation.
Ensure Regulatory Compliance
Telehealth services must adhere to the HIPAA Security Rule (administrative, physical, and technical safeguards for ePHI), the HIPAA Privacy Rule (use, disclosure, and patient rights), and HITECH breach notification requirements. Implement these standards by conducting a telehealth-specific HIPAA risk analysis, enforcing role-based access controls, encrypting data both in transit and at rest, and establishing policies that address telehealth use, disclosures, and patient rights, such as access to visit notes and recordings.
State-specific requirements, including those related to consent, documentation, and licensure, must also be tracked and updated regularly. Assign compliance and legal teams to monitor changes in state laws and keep the governance committee informed.
A telehealth risk analysis should cover all relevant assets - platforms, EHR integrations, devices, networks - and map out data flows, user groups, and third-party vendors. For each asset or data flow, identify potential threats (e.g., video interception or lost devices), assess their likelihood and impact, and evaluate current controls and residual risks. Document findings in a risk register with prioritized remediation plans, assigned owners, deadlines, and progress tracking. Update the analysis annually or whenever significant changes occur.
Vendor compliance is another critical area. Maintain Business Associate Agreements (BAAs) and review contracts to ensure vendors meet security and compliance standards. Require vendors to align with frameworks like NIST or HITRUST, undergo annual assessments, and provide evidence such as SOC 2 or HITRUST reports. Governance processes should involve legal, compliance, security, and procurement teams in reviewing vendor contracts, with periodic reassessments based on performance and incident history.
Platforms like Censinet RiskOps™ can simplify vendor management by centralizing inventories, automating risk assessments, and benchmarking cybersecurity practices. These tools streamline workflows with structured questionnaires, automated reviews, and dashboards that flag high-risk vendors or unresolved issues. By integrating such platforms into telehealth governance, organizations can ensure risk assessments and BAA verification are completed before go-live, track vendor remediation efforts, and monitor vulnerabilities across clinical apps, medical devices, and supply chain partners.
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." - Brian Sterud, CIO, Faith Regional Health
Technical and Operational Security Controls
This section builds on the governance and compliance measures discussed earlier, focusing on implementing technical safeguards to protect telehealth platforms, devices, and patient data. These measures are essential for maintaining the confidentiality of electronic protected health information (ePHI), ensuring system availability, and preventing unauthorized access.
Identity and Access Management
A strong security foundation starts with identity and access management. For clinicians and staff accessing telehealth platforms, electronic health records (EHRs), or administrative tools, multi-factor authentication (MFA) is a must. MFA combines elements like passwords (something you know), tokens or apps (something you have), or biometrics (something you are) to significantly reduce the risk of account breaches. For patients, secure one-time access codes or optional MFA via patient portals can enhance security while considering varying levels of digital literacy.
To limit exposure to sensitive data, role-based access control (RBAC) ensures users only access the information necessary for their specific roles. Physicians, nurses, schedulers, billing staff, and IT administrators should each have unique user IDs, with shared logins strictly prohibited. Enforce password policies, enable automatic logoff and session timeouts, and regularly review access permissions to identify dormant accounts or inappropriate access. When staff leave or change roles, promptly revoke or adjust their access rights.
Endpoint and Network Security
Telehealth involves a wide range of devices, including clinic workstations, mobile phones, tablets, home computers, and telehealth carts. Every device interacting with ePHI should have antivirus or anti-malware software, host-based firewalls, and a regular patching schedule for operating systems and applications. Implement mobile device management (MDM) or similar platforms to enforce encryption, screen locks, remote wipe capabilities, and app restrictions on smartphones and tablets used for virtual care.
For personal devices under bring-your-own-device (BYOD) policies, require MDM enrollment, encryption, and containerization to separate personal and work data. While patient devices can't be directly managed, design telehealth apps to minimize locally stored ePHI by using encrypted and sandboxed storage.
Network segmentation is another key control. Keep telehealth traffic and ePHI systems separate from guest Wi-Fi and general office networks to prevent lateral movement in case of a breach. Remote clinicians should connect through VPNs with device posture checks and least-privilege access to internal systems. All telehealth communication - whether video, messaging, or file sharing - must use encrypted connections like TLS 1.2 or higher over HTTPS. Additionally, configure firewalls and intrusion detection/prevention systems to monitor traffic, block unauthorized access attempts, and ensure telehealth bandwidth remains stable during peak usage. While patients' home network security is beyond your control, provide guidance on securing Wi-Fi with passwords and WPA2 or WPA3 encryption.
These measures set the stage for protecting telehealth data effectively.
Data Protection and Encryption
To safeguard ePHI, encrypt all data at rest - whether on servers, databases, backups, or endpoint devices - using AES-256 encryption. Protect encryption keys with role separation and, where possible, hardware security modules (HSMs) or cloud-based key management services. Similarly, ensure end-to-end encryption in transit for all telehealth interactions, including video calls, chat messages, image sharing, and data exchanges, using TLS 1.2 or higher.
Regular data backups are crucial. Store backups securely offsite or in the cloud, with clearly defined recovery time objectives (RTO) and recovery point objectives (RPO). Establish and enforce data retention and destruction policies for telehealth records - such as recordings, chat logs, and remote monitoring data - in line with clinical, legal, and HIPAA requirements. When retiring devices or storage media, securely wipe all data and obtain destruction certificates from vendors when applicable.
Maintain tamper-proof audit logs and conduct periodic reviews to monitor activity. Integrate telehealth systems into your incident response plan and run tabletop exercises to prepare for scenarios like platform outages or compromised accounts. Finally, establish redundant connectivity and backup workflows - such as alternative platforms, phone-based appointments, or SMS alerts - to ensure continuity of care during disruptions. These steps help create a resilient telehealth environment capable of handling unexpected challenges.
sbb-itb-535baee
Third-Party and Supply Chain Risk Management
When it comes to telehealth security, managing third-party and supply chain risks is a crucial piece of the puzzle. Every virtual visit relies on a network of vendors - think video conferencing providers, cloud hosting services, remote patient monitoring (RPM) device manufacturers, electronic health record (EHR) integrations, payment processors, and internet service providers. Here’s a startling fact: over 30% of large healthcare data breaches involve a vendor or business associate. Even more concerning, more than half of U.S. healthcare organizations have experienced a third-party-related data breach in the past two years [1].
Conduct Vendor Risk Assessments
Start with your vendor inventory and assess risks at every connection point. Before signing any contracts, evaluate the risks associated with telehealth and RPM vendors. Identify all vendors handling electronic protected health information (ePHI), then rank them based on the sensitivity of the data they manage and their criticality to your operations. High-risk categories often include telehealth platforms, RPM device manufacturers, cloud hosting providers, EHR vendors, and payment processors.
Use detailed security questionnaires to evaluate vendors. These should cover topics like HIPAA compliance, encryption standards (e.g., TLS 1.2+/AES-256), multi-factor authentication (MFA), role-based access controls (RBAC), audit logging, and incident response protocols. Request independent certifications such as SOC 2 Type II reports, HITRUST certifications, ISO 27001 certificates, or recent penetration test summaries. Match these controls to telehealth workflows like video visits, messaging, and RPM data uploads.
For vendors handling ePHI, tailor your questionnaires and require business associate agreements (BAAs) that define security expectations, breach notification requirements, and remediation timelines. Include service-level agreements (SLAs) for uptime (e.g., 99.9% monthly availability for telehealth sessions), incident response, and recovery objectives. Platforms like Censinet RiskOps™ can simplify this process by offering healthcare-specific questionnaires, centralized evidence collection, and workflows built for managing third-party risks in complex environments.
Monitor Vendor Risks Continuously
A one-time assessment won’t cut it. Vendor security postures evolve as vulnerabilities surface, certifications expire, mergers happen, and breaches occur. High-risk vendors, like core telehealth platforms or RPM hubs, should be reassessed periodically - ideally at least once a year or more frequently after major changes. Use automated alerts to stay informed about expired certifications or breach disclosures and track remediation commitments with clear deadlines and updates. Integrate vendor-related incidents into your broader incident management processes.
Make sure there’s clear accountability. Whether it’s the third-party risk management team, Information Security, or Supply Chain, someone needs to own this process. Define metrics to measure success, such as the percentage of critical vendors with current risk assessments, the number of unresolved high-risk findings, and the average time to resolve issues.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
This continuous monitoring helps strengthen your overall supply chain defenses.
Strengthen Supply Chain Resilience
Pinpoint single points of failure in your telehealth ecosystem. What’s your backup plan if your primary video platform fails, your cloud region goes offline, or your RPM device manufacturer faces a ransomware attack? Map out the service chain for each telehealth use case, assess the impact of outages, and create redundancy through backup platforms, multi-region failovers, and alternative communication methods.
Require vendors to maintain and test their business continuity and disaster recovery (BC/DR) plans. These plans should cover recovery procedures for telehealth services, RPM data ingestion, and scheduling systems. Work with vendors to develop incident coordination playbooks that outline communication channels, joint response actions, and decision-making procedures for temporary shutdowns or failovers during cyber incidents.
For RPM and medical devices, ensure there are processes for firmware updates, vulnerability patching, device recalls, and secure decommissioning. Safety-critical devices should come from reputable manufacturers with strong cybersecurity practices and clear replacement processes. Test these expectations through failover simulations and outage drills, and include them in your procurement criteria and overall continuity plans.
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health
Workforce and Patient Preparedness
Even the best technical safeguards can falter if users aren't equipped with secure telehealth practices. Human errors - like sending messages to the wrong person, using weak passwords, or falling for phishing scams - are among the top causes of telehealth security breaches. A strong telehealth security program understands that workforce training and patient education aren't optional - they're essential layers of defense. To truly protect telehealth platforms, technical measures must go hand-in-hand with comprehensive training for both staff and patients.
Train Staff on Security Practices
Effective training starts by tailoring it to the roles and responsibilities of each team. For example:
- Clinicians should learn how to verify patient identities remotely, set up secure telehealth sessions, and avoid discussing sensitive health information where it could be overheard.
- Schedulers and call center staff need to understand secure messaging practices, patient portal usage, and how to identify suspicious requests.
- IT and security teams require in-depth, frequent training on emerging telehealth threats, platform configurations, and incident response strategies.
Training shouldn't be a one-and-done event. Onboarding sessions should be followed by annual role-specific refreshers, with additional updates after major system changes. Incorporate phishing simulations that mimic telehealth scenarios to teach staff how to spot and respond to threats. Track metrics like click rates and reporting rates, and use that data to provide timely coaching through short videos or tip sheets.
At key telehealth touchpoints, staff should follow simple, actionable checklists. These might include steps like verifying the platform is approved and updated, confirming patient identity using two identifiers, logging out properly, and reporting any unusual activity - such as unexpected disconnections or suspicious messages during sessions.
Educate and Support Patients
Patients also need clear, practical guidance to protect their telehealth interactions. Provide step-by-step instructions on securing their devices, such as:
- Using strong, unique passwords
- Enabling automatic software updates
- Connecting through home Wi-Fi with WPA2 or WPA3 encryption
- Avoiding public Wi-Fi for video visits
It’s equally important to explain how your organization communicates with patients. For instance, let them know you’ll never request passwords, full Social Security numbers, or payment details through email or text. Share examples of legitimate appointment reminders and portal messages alongside examples of scams to help patients recognize red flags.
Offer guidance in multiple formats - emails, PDFs, FAQs, videos, and pre-visit reminders - to ensure accessibility. Consider hosting pre-visit tech checks, where staff assist patients with setting up their devices and adjusting privacy settings. High-risk groups, such as older adults or those using shared devices, may benefit from extra support. You can gauge the effectiveness of these efforts by monitoring metrics like open rates for portal messages or the number of patient security-related inquiries. These steps encourage a broader awareness of cybersecurity among patients.
Build a Security-Focused Culture
A secure telehealth program depends on fostering a culture that values security at every level. Leadership should make it clear that telehealth security is a priority by linking it to performance goals, modeling secure behaviors, and including telehealth risks in governance and quality discussions.
Encourage staff to report issues early by creating low-barrier reporting channels - such as hotlines, dedicated email addresses, or in-app reporting buttons. Adopt a no-blame policy for good-faith reports to ensure employees feel comfortable flagging potential problems.
Track progress through measurable indicators like training completion rates, phishing simulation outcomes, adherence to secure visit protocols, and the number of self-reported incidents. Tools like Censinet RiskOps™ can help centralize risk assessments across telehealth platforms, enabling organizations to identify high-risk areas, prioritize training efforts, and share insights across departments. Building this kind of security-focused culture is a cornerstone of a mature telehealth security strategy.
Conclusion
This checklist provides a foundation for an ongoing process of identifying and managing risks, which is essential for maintaining strong telehealth security.
Assess and Prioritize Your Risks
Start by using this checklist to conduct a structured risk assessment. Identify your telehealth program's vulnerabilities and map each security control - such as governance, access management, encryption, vendor oversight, and workforce training - to related risks. These risks might include unauthorized access, data loss, or service interruptions. Evaluate each risk based on its likelihood and the potential impact on operations and patient safety.
From this analysis, create a ranked list of security gaps. For instance, unencrypted devices used for video visits or vendors without proper business associate agreements should be flagged as high priorities. Document these vulnerabilities in a risk register, assigning owners, deadlines, and clear mitigation plans. Pay particular attention to risks that could compromise electronic PHI (ePHI), as issues like weak identity controls, insufficient encryption, or poorly vetted vendors can directly jeopardize patient safety, regulatory compliance, and data security.
Develop a phased roadmap to address these gaps, using key data points like affected user counts, audit logs, incident histories, and vendor risk scores. Break down actions into short-term (0–3 months) critical fixes, such as enforcing multi-factor authentication and securing remote endpoints; medium-term (3–12 months) structural improvements, like standardizing workflows and enhancing vendor risk management; and long-term (12+ months) efforts, such as integrating telehealth security into broader enterprise risk strategies. Align these phases with your organization's budget and strategic goals to ensure security investments support telehealth expansion. Once the risks are ranked, consolidate them into a unified action plan for remediation.
Use Platforms for Continuous Improvement
With a risk roadmap in hand, focus on continuously strengthening your defenses. Telehealth security isn’t a one-and-done task - it’s an ongoing effort that must evolve with new technologies, emerging threats, and changing regulations. Reassess your security maturity regularly, whether annually or semiannually, using this checklist to track your progress. Monitor key performance indicators like the closure rate of high-risk findings, the percentage of telehealth systems with complete encryption, and the completion rates for staff security training.
Platforms like Censinet RiskOps™ can streamline this process, centralizing risk assessments for vendors, applications, and medical devices that handle patient data. The platform automates tasks like distributing questionnaires, scoring vendor responses, identifying control gaps, and creating risk treatment plans. By reducing manual work and shortening assessment cycles, Censinet RiskOps™ helps organizations stay agile. It also aggregates data from telehealth systems, clinical apps, medical devices, and supply chains, offering benchmarking and trend analysis. This allows you to track whether telehealth-related risks are increasing or decreasing and how your organization compares to others.
FAQs
What steps can healthcare organizations take to ensure their telehealth platforms comply with HIPAA requirements?
To make sure telehealth platforms meet HIPAA standards, healthcare organizations need to prioritize robust security measures. This includes encrypting data during transmission and storage, enforcing strict access controls, and keeping comprehensive audit logs. Conducting regular risk assessments is also crucial to spot and fix any potential weaknesses.
Solutions like Censinet RiskOps™ can play a key role in simplifying compliance. They streamline third-party risk assessments and offer tools for cybersecurity benchmarking, helping to protect patient data and uphold HIPAA's privacy and security guidelines.
How can healthcare organizations effectively manage telehealth vendor risks?
To manage telehealth vendor risks effectively, healthcare organizations need to prioritize ongoing risk monitoring, conduct detailed third-party risk assessments, and implement cybersecurity tools tailored to the healthcare sector.
Solutions like Censinet RiskOps™ make this process easier by simplifying risk evaluations, ensuring adherence to security standards, and improving vendor collaboration. These measures help protect patient data and sensitive information while keeping telehealth systems secure and compliant with industry standards.
Why is training for staff and patients important for telehealth security?
Training is a crucial part of keeping telehealth systems secure - for both staff and patients. It ensures everyone knows how to follow security protocols, recognize potential threats, and use telehealth platforms safely.
Human error, like falling for phishing attempts or improperly handling sensitive data, is a common weak spot in cybersecurity. By addressing these risks through education, training helps prevent breaches and other cyber incidents. When staff and patients are well-informed, sensitive data such as patient health information (PHI) is better protected, and trust in telehealth services remains intact.


