CMMC Roadmap: Avoiding Common Mistakes
Post Summary
The CMMC roadmap is a step-by-step guide to achieving compliance with the Cybersecurity Maturity Model Certification (CMMC) framework.
Common mistakes include underestimating the scope, incomplete documentation, misaligned priorities, and neglecting vendor compliance.
By conducting thorough gap analyses, planning realistic timelines, maintaining proper documentation, and ensuring vendor compliance.
Non-compliant vendors can jeopardize your contracts and overall cybersecurity posture.
Proactive planning ensures sufficient time, resources, and personnel are allocated to meet CMMC requirements.
Tools like Censinet RiskOps™ can automate gap analyses, track compliance progress, and manage vendor risks.
If your organization works with Department of Defense (DoD) contracts, meeting CMMC 2.0 requirements is critical to maintaining eligibility. Many healthcare organizations fail to prepare adequately, leading to lost contracts, compliance gaps, and increased risks. This guide focuses on five common mistakes and how to avoid them.
Key Takeaways:
- Don't treat CMMC as an IT-only project. It requires input from clinical, legal, and operational teams to align with broader risk management.
- Scope Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) accurately. Over-scoping inflates costs, while under-scoping risks compliance failures.
- Conduct a gap analysis and create a Plan of Action and Milestones (POA&M). Skipping this leads to inefficiencies and missed deadlines.
- Address third-party and supply chain risks. Ensure vendors handling CUI/FCI meet CMMC requirements and are continuously monitored.
- Maintain detailed documentation. Up-to-date System Security Plans (SSP), policies, and training records are essential for passing assessments.
By integrating CMMC into daily operations and prioritizing collaboration across departments, organizations can meet compliance requirements effectively while protecting sensitive data.
5 Common CMMC Compliance Mistakes Healthcare Organizations Must Avoid
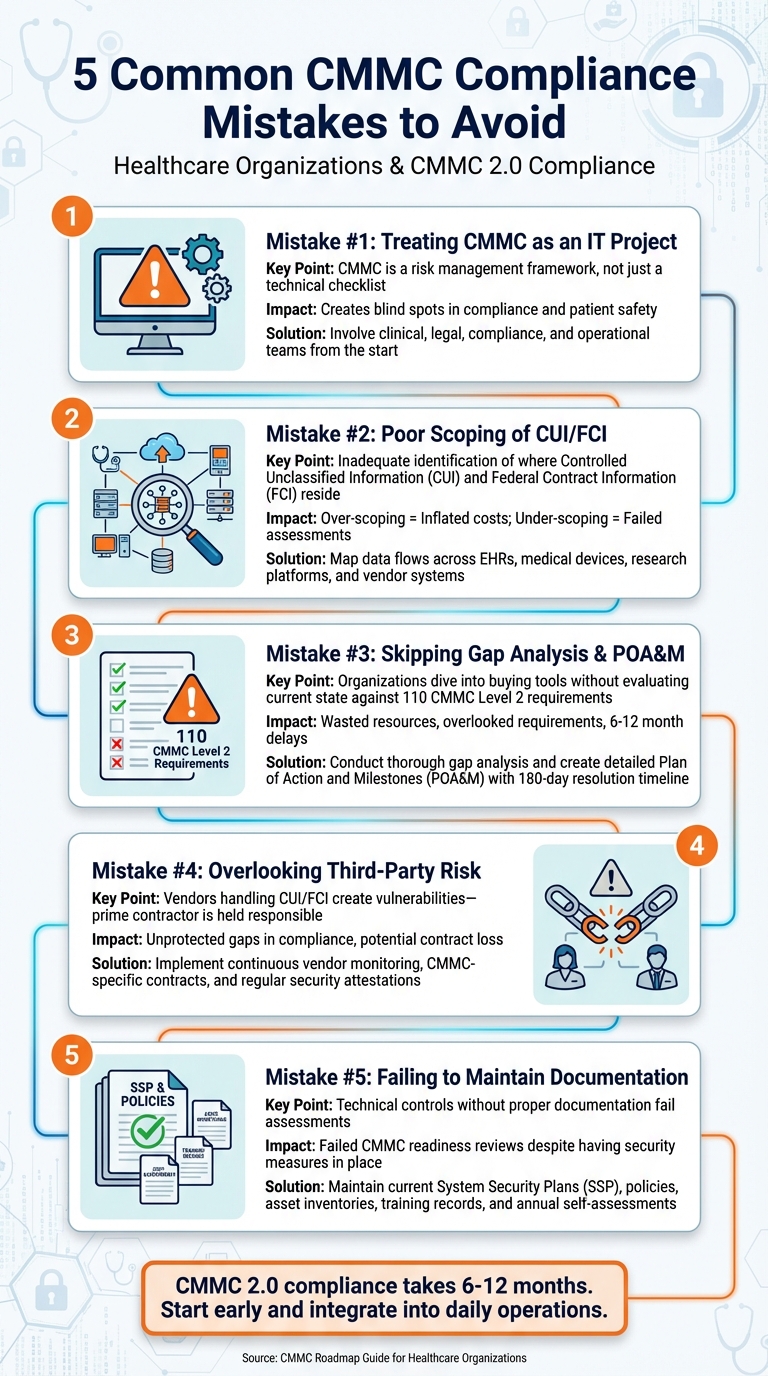
Mistake 1: Treating CMMC as an IT Project Instead of a Risk Management Program
When healthcare organizations land their first Department of Defense (DoD) contract requiring CMMC certification, they often assign the task to their IT department. While this might seem logical at first glance, it can create serious blind spots that jeopardize both compliance efforts and, more importantly, patient safety.
Why Limiting CMMC to IT Is a Problem
CMMC 2.0 isn’t just a checklist of technical tasks - it’s a comprehensive risk management framework tailored to address varying levels of risk. Treating it as an IT-only project can lead to critical oversights, especially in a complex field like healthcare.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
– Matt Christensen, Sr. Director GRC, Intermountain Health [1]
Common pitfalls found during CMMC assessments include incomplete risk evaluations, weak incident response strategies, inadequate access controls, and poor configuration management [2]. These aren’t just IT issues - they require collaboration from clinical, legal, compliance, and operational teams. For example, if IT implements access controls without consulting clinical staff, it can unintentionally disrupt workflows, forcing staff to adopt workarounds that compromise security.
CMMC readiness demands more than technical fixes - it’s about building a sustainable risk management program that protects sensitive data across the organization. This includes safeguarding medical devices, research systems, clinical applications, and even third-party vendors.
Shifting to a Risk Management Mindset
The key to success is integrating CMMC requirements into your existing risk management framework instead of treating them as a standalone compliance exercise. For healthcare organizations, your current HIPAA risk analysis can serve as a strong starting point. Both frameworks share similar goals: identifying where sensitive information resides, evaluating threats, and implementing safeguards.
Here’s a practical way to approach it: map CMMC practices to your existing HIPAA Security Rule controls and NIST guidelines. Many requirements overlap, such as encryption, access controls, audit logging, and incident response. Focus on addressing the most pressing risks first. For instance, if your gap analysis shows both a missing intrusion detection system and inadequate incident response procedures, prioritize the response plan - because even the best detection tools are useless without a strategy to act on alerts.
Involve non-IT stakeholders from the beginning. Clinical engineers, legal advisors, compliance officers, and operations leaders all bring essential perspectives. Whether it’s segmenting medical device networks, reviewing vendor contracts, or ensuring proper documentation, their input is critical for success. This collaborative, risk-based approach lays the groundwork for a strong, unified compliance strategy.
The Role of Centralized Risk Operations
Taking it a step further, centralized risk operations can streamline efforts across departments. Think of this as a cross-functional hub that connects IT, compliance, clinical teams, legal, and vendor management. This approach ensures nothing gets overlooked.
For example, Tower Health’s CISO, Terry Grogan, shared that adopting Censinet RiskOps allowed three full-time employees to shift back to their core responsibilities, all while the organization conducted more risk assessments with just two dedicated staff members [1].
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
– James Case, VP & CISO, Baptist Health [1]
Purpose-built for healthcare, Censinet RiskOps™ helps organizations manage risks across vendors, patient data, medical devices, research, and supply chains - key areas where healthcare operations intersect with controlled information. By embedding CMMC compliance into everyday risk management, rather than isolating it within IT, organizations can create a seamless and effective system.
A true shift happens when risk assessments guide budget decisions, clinical staff actively contribute to security planning, vendor contracts reflect CMMC requirements, and your Plan of Action and Milestones (POA&M) tracks risks across the enterprise. This centralized, integrated approach is the foundation for avoiding the pitfalls outlined in this guide.
Mistake 2: Poor Scoping and Misidentification of CUI/FCI
One of the most expensive missteps healthcare organizations can make is failing to properly identify where Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) reside within their systems. Inadequate scoping is consistently flagged as a major CMMC challenge, leading to two significant issues: over-scoping, which drives up costs, and under-scoping, which risks failing assessments [2][5].
The problem often starts with assumptions. Some organizations believe their entire network must meet CMMC compliance, while others underestimate how far CUI/FCI spreads across their systems [2][5]. Both scenarios create headaches. Over-scoping forces the implementation of costly controls on systems that don’t even handle defense-related data. On the other hand, under-scoping leaves critical gaps that assessors will likely uncover - after months of effort and resource investment. To effectively safeguard sensitive healthcare data and stay compliant, precise scoping of CUI/FCI is essential.
Where CUI/FCI Exists in Healthcare
In healthcare, CUI and FCI don’t sit neatly in one database. They flow across multiple systems supporting defense-related work, research, and clinical care for DoD beneficiaries. Beyond electronic health records (EHR), you’ll find CUI/FCI in network-connected devices such as imaging systems, infusion pumps, and patient monitors, as well as in research platforms, telehealth tools, secure messaging systems, cloud file shares, backups, and SIEM logs [4].
It’s important to consider the entire data lifecycle. CUI isn’t limited to its point of creation - it moves through HL7/FHIR interfaces, APIs, VPN connections, and data exports between systems like EHRs, research platforms, billing systems, and analytics tools [4][9]. Mapping these touchpoints is crucial. Tools like data discovery and data loss prevention (DLP) can help locate files and messages containing DoD identifiers, project codes, or standard CUI markings, allowing you to differentiate CUI/FCI from general PHI or PII [9].
How to Define Your Assessment Boundary
Defining an accurate assessment boundary starts with mapping data flows. Document every connection where contract-related data moves: which systems generate CUI/FCI, where it’s processed, how it’s transmitted, and where it’s stored [9]. Create detailed diagrams that show data sources, processing points, storage locations, external connections, backups, and logs - marking every instance of CUI/FCI [9].
Once you’ve mapped these flows, you can design a CUI enclave - a segmented network zone dedicated to systems handling CUI/FCI, protected with firewalls and secure gateways [9]. For employees working with CUI, implement tools like virtual desktop infrastructure (VDI) or secure remote access to keep data within the enclave and prevent it from being copied to unmanaged devices [9].
Network segmentation plays a key role in avoiding unnecessary costs. Devices that don’t store or process CUI/FCI should remain out of scope through proper isolation. Systems that do handle such data must either be moved into the enclave or configured to prevent CUI storage [4]. This targeted approach ensures your assessment boundary is logical and based on evidence, instead of defaulting to an inefficient “everything is in scope” model.
The stakes are high. Over-scoping inflates costs by requiring CMMC controls across large networks that don’t handle CUI/FCI, slowing operations and complicating configuration management [4][9]. Under-scoping risks assessment failure, exposing gaps that could lead to CUI breaches, contract loss, and costly rework that delays timelines by months [9]. For organizations not aligned with NIST SP 800-171, addressing these gaps can take 6–12 months, with scoping errors adding even more delays [7].
Creating a Repeatable Scoping Process
As your healthcare environment evolves with new DoD contracts, system upgrades, and vendor changes, establish a formal CMMC scoping procedure. Trigger this process whenever you sign a new DoD contract, implement a system or feature that may handle contract-related data, or onboard a vendor that could store, process, or transmit potential CUI [9]. Your scoping boundary should adapt to your organization’s changing risk landscape. Assign clear roles to teams such as information security, clinical engineering, research administration, contracting, and supply chain. Define required documentation, including updated data-flow diagrams, asset inventories, vendor lists, and network diagrams showing how new elements interact with existing CUI/FCI flows.
Maintain a centralized system inventory where each system is tagged with its associated contracts and whether it handles CUI/FCI [9]. Use version-controlled data flow diagrams and scoping worksheets to demonstrate how your environment has evolved. This documentation provides essential evidence to assessors that your boundary decisions are logical and risk-based.
Platforms like Censinet RiskOps™ simplify ongoing scoping by integrating contracts, vendors, risk assessments, and system inventories. These tools help healthcare organizations manage risks in areas where CUI/FCI typically resides, such as vendor systems, patient data, medical devices, and research platforms. By centralizing these elements, you create a dynamic system boundary that evolves with your environment, rather than relying on a one-time scoping exercise that quickly becomes outdated.
Don’t forget to include third-party vendors and partners in your scoping process. Identify all vendors tied to DoD contracts who handle, store, or access CUI, and determine if they need to meet CMMC Level 2 requirements [3]. Include their systems and connections in your scoping diagrams and risk assessments. If a vendor can’t meet the requirements, you’ll need to consider isolation techniques or alternative providers - but you can’t make these decisions without first identifying the vendors involved.
Mistake 3: Skipping Gap Analysis and POA&M Planning
Once you've defined your assessment boundary, the next logical step is evaluating how your organization measures up against CMMC Level 2 requirements. Unfortunately, many healthcare organizations skip this crucial gap analysis phase. Instead, they dive straight into buying tools or implementing controls, often resulting in wasted resources and overlooked requirements [2]. Let’s break down why a thorough gap analysis is so important.
Why Gap Analysis Matters
A CMMC gap analysis is essentially a detailed review of your current security practices compared to the 110 CMMC Level 2 requirements. It helps pinpoint which controls are fully implemented, partially in place, or missing entirely. This process not only avoids unnecessary spending but also creates a clear, actionable plan to address deficiencies without delays [4]. By focusing on the actual risks to controlled unclassified information (CUI), patient care, and contract timelines, you can avoid decisions driven by vendor pitches or generic checklists.
One surprising insight from gap analyses is that documentation gaps often carry more weight than technical ones. For example, you might have multi-factor authentication fully deployed across your CUI environment. But if you can't provide documentation showing how it's configured, enforced, and maintained, assessors may still flag that control as deficient [8].
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." – Brian Sterud, CIO, Faith Regional Health [1]
A proper gap analysis involves mapping all 110 CMMC Level 2 practices to your organization's environment. For each practice, document its implementation status (fully, partially, or not implemented), gather evidence, identify residual risks, and estimate the effort required to close the gap. This isn't just an IT task - teams like clinical engineering, research administration, and supply chain should also be involved to ensure nothing falls through the cracks. This comprehensive approach sets the stage for creating an effective Plan of Action and Milestones (POA&M) that aligns with your overall risk management strategy.
How to Build a POA&M
The gap analysis results feed directly into your POA&M - a document that details each identified deficiency, outlines specific remediation steps, assigns responsibility, and sets a timeline for completion [10]. Under CMMC 2.0, POA&Ms are limited to lower-weighted requirements and must meet a minimum assessment score. Typically, any open POA&M items need to be resolved within 180 days, and high-priority controls cannot be deferred [11]. This makes the POA&M a focused tool for bridging the gap between "almost ready" and full compliance - not just a wishlist of future projects.
For healthcare organizations, a well-structured POA&M should include:
- The CMMC practice identifier and description
- Current status and any residual risks
- Specific remediation steps (e.g., implementing multi-factor authentication or formalizing vendor risk procedures)
- Assigned owner or responsible party
- Estimated costs (including licensing, services, and staffing)
- Start and target completion dates aligned with DoD timelines
- Dependencies (e.g., network segmentation or identity modernization projects)
- Evidence required for closure (e.g., policy documents, screenshots, logs, or training records)
- Risk rating or priority score to help allocate resources effectively
Focus on resolving POA&M items that are critical for certification, pose significant risks to CUI or clinical operations, or offer quick wins that can boost your compliance score [11]. For instance, if your gap analysis highlights missing incident response procedures for CUI breaches - a high-priority requirement - updating documentation could resolve the issue in weeks. On the other hand, a multi-year infrastructure project affecting only lower-priority practices can be scheduled later.
As with centralizing risk operations, your POA&M should integrate seamlessly into your broader risk management framework.
Connecting POA&M with Risk Management
Once you've identified the gaps, it’s essential to fold them into your organization's risk management processes. A POA&M shouldn’t exist in isolation. Instead, integrate each CMMC gap into your enterprise risk management (ERM) framework by recording it in your risk register, assigning owners, and outlining mitigation plans. Regular updates in governance forums - like CIO or compliance committee meetings - ensure that CMMC readiness remains a priority.
To track progress effectively, consolidate all POA&M items in a centralized system. Each task should have a clear status, assigned owner, due date, supporting evidence, and links to related risks. Regular reviews (monthly or quarterly) should focus on overdue tasks, risks tied to contract deadlines, and scope changes affecting sensitive data like FCI or CUI. Tools like Censinet RiskOps™ can simplify this process by linking CMMC gaps to enterprise risks, automating workflows, and centralizing evidence like policies, vendor assessments, and risk reports [4].
Delaying self-assessment and gap analysis can seriously impact your ability to meet contract deadlines. Depending on your organization’s size and complexity, preparing for CMMC compliance can take anywhere from six months to over a year [3]. Without a structured POA&M, you risk uncovering critical gaps just weeks before an assessment - leading to rushed fixes, incomplete documentation, and potentially failed certifications that could jeopardize contracts and revenue.
sbb-itb-535baee
Mistake 4: Overlooking Third-Party and Supply Chain Risk
Even with a well-defined assessment boundary and a detailed Plan of Action and Milestones (POA&M), many organizations fail to account for risks posed by third-party vendors and their supply chains. This oversight creates critical vulnerabilities. If a vendor mishandles controlled unclassified information (CUI) or federal contract information (FCI), the prime contractor - not the vendor - can be held responsible for any exposure or non-compliance [2].
How Vendors Impact CMMC Compliance
Just as internal risks require careful management, external vendor risks demand equal attention. Under CMMC 2.0, organizations must manage external service providers and suppliers that could influence the security of CUI or FCI [6]. For healthcare organizations working with the Department of Defense, this includes a wide range of partners - cloud hosting providers, managed service providers, billing firms, telehealth platforms, electronic health record vendors, medical device manufacturers, and clinical research partners. Essentially, any entity that stores, processes, transmits, or otherwise impacts the confidentiality of CUI is within the compliance scope [6].
A common misstep is focusing solely on internal systems without considering how CUI flows through vendors and the broader supply chain. This creates unprotected gaps that weaken CMMC readiness and leave vulnerabilities outside the organization’s immediate controls [2][6]. CMMC assessors expect organizations to demonstrate clear oversight of external providers and their impact on CUI. This means maintaining a detailed vendor inventory, enforcing stringent selection policies, and regularly assessing third-party risks.
Setting Up Third-Party Risk Management
Establishing a solid third-party risk management (TPRM) program starts with identifying all vendors that interact with CUI or FCI. Once identified, assign appropriate CMMC levels to these vendors and ensure contracts include specific security and audit requirements [6]. Contracts should outline incident reporting timelines, right-to-audit clauses, evidence-sharing obligations, and flow-down clauses requiring subcontractors to meet and maintain the necessary CMMC level. Vendors should also notify you of any significant security changes [6].
To assess vendor compliance, use standardized questionnaires mapped to CMMC requirements. These should evaluate vendor security controls both during onboarding and at regular intervals thereafter [2][6]. Track vendor risk based on their criticality and exposure to CUI, and document any remediation efforts in your POA&M to support CMMC assessments. For healthcare organizations already managing HIPAA business associates, existing oversight processes can be expanded to include CMMC-specific requirements by integrating NIST 800-171 controls into vendor due diligence.
Monitoring Vendor Risks Over Time
Vendor risk management doesn’t stop at onboarding. CMMC compliance requires continuous monitoring of third-party risks over time. This includes reviewing regular security attestations, penetration test summaries, and reports such as SOC 2 or ISO 27001. Stay informed about any security incidents that could affect CUI, incorporate threat intelligence updates into your reviews, and ensure vendor risks are reflected in your overall risk register and governance practices.
Given the sheer volume of vendor relationships - often hundreds or thousands - manual tracking is impractical. Centralized tools like Censinet RiskOps™ can simplify the process by automating third-party questionnaires, centralizing vendor evidence, and tracking POA&Ms over time [1].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health [1]
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." – James Case, VP & CISO, Baptist Health [1]
Mistake 5: Failing to Maintain Documentation and Compliance
Relying solely on technical controls isn't enough - assessors need up-to-date, detailed documentation to confirm those controls are effectively implemented. This step in your CMMC roadmap is just as crucial as the technical measures themselves. Many healthcare organizations put solid security measures in place but fail to maintain the documentation necessary to prove their compliance. This oversight can become a major issue during assessments, as assessors require clear evidence of consistent implementation [8][2].
What Documentation Does CMMC Require?
Under CMMC 2.0, organizations must maintain a wide range of documents that evolve alongside their systems and contracts. At the core of this requirement is an accurate and current System Security Plan (SSP). Generic or outdated SSPs are a common reason organizations fail CMMC readiness reviews [14]. Additionally, organizations need:
- A detailed Plan of Action and Milestones (POA&M) with tasks and timelines.
- Written policies covering areas like access control, incident response, change management, backups, vulnerability management, and monitoring.
- Comprehensive asset inventories for all systems handling CUI (Controlled Unclassified Information) or FCI (Federal Contract Information).
- Training records that include dates, content, and attendee information [2][8][14].
All of this documentation should be stored in a central evidence repository, such as a secure document management or risk operations platform. Each document should be tagged and mapped to specific CMMC practices. Evidence should include metadata like owner, date, scope, and related systems or contracts, and it must be retained for the full CMMC assessment cycle and any contractually required period [12][13]. Tools like Censinet RiskOps™ are often used by healthcare contractors to centralize these records, making it easier to produce evidence during C3PAO audits or internal reviews [4].
How to Document Continuous Monitoring
Once your documentation practices are in place, continuous monitoring ensures your controls remain effective over time. Schedule regular reviews for logs, vulnerabilities, patch management, and user access. Keep records such as SIEM reports, remediation tickets, scan results, patch deployment logs, exported access lists, signed attestations from system owners, and details of accounts modified or removed. These records demonstrate that your controls are functioning as intended [12][13].
Healthcare environments often involve diverse systems, including EHR platforms, clinical apps, medical devices, and SaaS solutions that handle FCI or CUI [4][12]. For systems like medical devices or third-party platforms where direct logging or patching may not be possible, document compensating controls. Examples include network segmentation, enhanced monitoring, and vendor agreements. Keep vendor security attestations, penetration test summaries, and risk assessments up to date as well [4][12].
Although a C3PAO assessment is valid for three years, organizations are required to conduct annual self-assessments and maintain security controls year-round [3]. Ideally, internal reviews of the SSP, POA&M, policies, and evidence should happen quarterly, but at a minimum, they must occur annually. Tie these reviews to a CMMC documentation calendar that aligns with contract and technology changes. For instance, any new system, major upgrade, or DoD contract should trigger a review of the SSP, risk register, and vendor assessments [12][13].
Assigning Compliance Ownership
Clear documentation is only effective if someone is accountable for keeping it up to date. Assign a dedicated compliance owner - usually the CISO or a risk leader - who will oversee the ongoing maintenance of CMMC documentation. This person should coordinate with IT, security teams, clinical engineering, and vendors to make sure updates are integrated into daily operations between assessment cycles.
Using a centralized risk operations platform, like Censinet RiskOps™, can streamline this process. Such platforms help track third-party assessments, monitor remediation commitments, and generate reports that map vendor and device risks to CMMC practices. These tools replace manual methods, such as spreadsheets, and allow for more efficient management of cybersecurity and risk data across various areas [1].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." – Terry Grogan, CISO, Tower Health [1]
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." – James Case, VP & CISO, Baptist Health [1]
Conclusion: Building a CMMC Roadmap That Works
Key Lessons for Avoiding CMMC Mistakes
Steering clear of common CMMC missteps starts with a sharp focus on risk management from the very beginning. Success lies in getting the basics right: precise scoping, a detailed gap analysis, strong third-party risk management, and solid documentation. Accurate scoping is critical - it pinpoints exactly where Controlled Unclassified Information (CUI) and Federal Contract Information (FCI) are stored, whether that's in electronic health records, medical devices, or cloud environments. A formal gap analysis paired with an evolving Plan of Action and Milestones (POA&M) turns abstract requirements into actionable steps, complete with assigned responsibilities, deadlines, and risk priorities. Managing third-party risks ensures that vendors handling CUI are evaluated, monitored, and held to strict contractual security measures. Lastly, comprehensive documentation - covering policies, system security plans, training logs, and monitoring records - provides assessors with the evidence they need to verify that security measures are consistently effective.
Organizations that establish clear accountability for compliance, maintain ongoing documentation, and integrate CMMC into their broader strategy are better positioned to avoid setbacks, unnecessary expenses, and compliance burnout. On the flip side, those without executive backing or who scramble to gather evidence just before an audit often find themselves stuck in a frustrating cycle of repeated failures.
Making Compliance Part of Daily Operations
To make compliance sustainable, CMMC practices need to be woven into the fabric of daily operations. It’s not about adding more tasks but about embedding CMMC requirements into existing workflows. This includes integrating CMMC into processes like change management, vendor onboarding, system updates, and staff training. For example, when rolling out a new clinical application or signing a vendor contract, update your CMMC scoping, risk assessments, and documentation as part of your standard procedures.
Healthcare leaders can speed up this integration by establishing unified governance structures, such as risk committees or board subcommittees, to oversee both clinical and cybersecurity risks. This ensures CMMC compliance gets the same level of attention as patient safety. Tools like Censinet RiskOps™, tailored specifically for healthcare, simplify this process by consolidating enterprise, vendor, and cyber risk management. With features like consistent scoring, reporting, and benchmarking, it helps organizations manage risks across patient data, Protected Health Information (PHI), clinical applications, medical devices, and the supply chain. This approach transforms CMMC investments into a cornerstone of safe, reliable care delivery rather than just another regulatory requirement.
FAQs
Why should teams outside of IT be involved in CMMC compliance planning?
Including non-IT teams in CMMC compliance planning is crucial because cybersecurity affects every corner of a healthcare organization. Teams like clinical, legal, and administrative departments regularly manage sensitive data and workflows that must meet compliance standards. Bringing them into the process helps uncover risks and vulnerabilities that might otherwise go unnoticed.
Involving these teams also encourages stronger communication and teamwork across the organization, streamlining the implementation of security measures. This collaborative effort ensures the development of a CMMC roadmap that truly reflects the specific needs and challenges of healthcare settings.
What steps can healthcare organizations take to properly identify and manage CUI and FCI?
To effectively handle Controlled Unclassified Information (CUI) and Federal Contract Information (FCI), healthcare organizations need to start by taking stock of their assets. This means identifying exactly where sensitive data is stored - whether it’s in clinical applications, medical devices, or within the supply chain.
Regular risk assessments play a key role in spotting vulnerabilities and staying compliant with CMMC standards. Using tools tailored for healthcare, like Censinet RiskOps™, can simplify this process by helping organize and manage sensitive data more efficiently. Aligning these efforts with CMMC requirements strengthens data security and minimizes potential risks.
How can healthcare organizations effectively manage third-party risks under CMMC?
To tackle third-party risks under CMMC, healthcare organizations need a well-organized and forward-thinking strategy. Begin with ongoing risk assessments to uncover any weaknesses in third-party systems. Make sure to establish clear security standards for vendors that align with CMMC requirements.
Leveraging specialized cybersecurity platforms designed for healthcare can simplify the risk management process. These tools can assist in tracking vendor performance and resolving security gaps. Consistent communication and collaboration with vendors are equally important to ensure compliance and safeguard sensitive patient information and key systems.
Related Blog Posts
Key Points:
What is the CMMC roadmap?
- Definition: The CMMC roadmap is a structured, step-by-step guide designed to help organizations achieve compliance with the Cybersecurity Maturity Model Certification (CMMC) framework.
- Purpose: It ensures organizations meet the Department of Defense (DoD) cybersecurity requirements for handling Controlled Unclassified Information (CUI).
What are the most common mistakes in CMMC compliance?
- Underestimating Scope: Many organizations fail to define CUI boundaries and system scope accurately, leading to gaps in compliance.
- Incomplete Documentation: Missing or poorly maintained records can derail audits and delay certification.
- Misaligned Priorities: Focusing on the wrong areas or skipping critical steps in the compliance process can lead to failure.
- Neglecting Vendor Compliance: Non-compliant vendors can introduce risks that jeopardize your contracts.
- Rushing the Process: Insufficient time and resources often result in cutting corners and failing assessments.
How can organizations avoid CMMC compliance pitfalls?
- Conduct Gap Analyses: Identify gaps in your current cybersecurity posture and address them proactively.
- Plan Realistic Timelines: Allocate sufficient time and resources to avoid rushing the process.
- Maintain Proper Documentation: Ensure all policies, procedures, and evidence are complete and audit-ready.
- Ensure Vendor Compliance: Regularly assess and monitor the cybersecurity posture of your supply chain.
- Engage Experts: Work with CMMC consultants or partners to navigate complexities and avoid common mistakes.
Why is vendor management important in CMMC compliance?
- Supply Chain Risks: Non-compliant vendors can introduce vulnerabilities that compromise your cybersecurity posture.
- Contractual Obligations: Vendors’ lack of compliance can put your DoD contracts at risk.
- Continuous Monitoring: Regularly assess vendor compliance to ensure alignment with CMMC requirements.
What role does proactive planning play in CMMC success?
- Resource Allocation: Proactive planning ensures sufficient budget, personnel, and time are dedicated to compliance efforts.
- Avoiding Delays: Early preparation helps organizations avoid last-minute surprises and costly delays.
- Strategic Focus: A well-defined plan prioritizes critical areas and aligns efforts with CMMC requirements.
What tools can help streamline CMMC compliance?
- Censinet RiskOps™: Automates gap analyses, tracks compliance progress, and manages vendor risks.
- Continuous Monitoring Tools: Provide real-time insights into cybersecurity posture and identify vulnerabilities.
- Documentation Management Systems: Ensure all policies, procedures, and evidence are organized and audit-ready.


