Common Challenges in Role-Based Access Control Implementation
Post Summary
Role-Based Access Control (RBAC) can simplify managing access to sensitive healthcare data like electronic health records (EHRs) and protected health information (PHI). But implementing it in healthcare is far from easy. Here's why:
- Complex Workflows: Healthcare roles are dynamic - clinicians switch departments, hold multiple roles, or work in emergencies. Static role definitions often fail to match these realities.
- Role Explosion: Overly specific roles lead to hundreds of overlapping ones, creating administrative chaos and security risks.
- Privilege Creep: Staff often accumulate excessive permissions over time, violating the principle of least privilege and increasing risks.
- Misaligned Roles: Many RBAC systems don't reflect actual clinical workflows, causing inefficiencies and security gaps.
- Weak Identity Governance: Poor onboarding and offboarding processes lead to orphaned accounts and inconsistent role assignments.
Key Solutions:
- Streamline Roles: Use task-based roles with clear permissions (CRUD: Create, Read, Update, Delete) to reduce role sprawl.
- Regular Reviews: Conduct quarterly access audits to prevent privilege creep.
- Emergency Access Protocols: Implement "break-glass" access with strict controls and logging.
- Centralized Identity Governance: Automate role assignments and deactivations through IAM/IGA platforms.
RBAC in healthcare isn't just about compliance - it's about safeguarding patient safety and data integrity. Addressing these challenges requires disciplined governance, regular reviews, and tools like centralized logging and risk management platforms.
Challenge 1: Too Many Roles and Poor Role Design
Well-Designed vs Role-Exploded RBAC Systems in Healthcare
One of the biggest hurdles healthcare organizations face when rolling out Role-Based Access Control (RBAC) is "role explosion." Instead of simplifying access management, IT teams often end up juggling hundreds - or even thousands - of slightly different roles. This creates a massive administrative burden, with endless maintenance, documentation, and reviews.
What is Role Explosion in Healthcare?
Role explosion, sometimes called role sprawl, happens when organizations create overly specific or overlapping roles instead of reusing broader, job-based ones. A Guidehouse analysis described this issue as "the most costly and complex process limitation" in hospital RBAC models. The problem is particularly pronounced in healthcare because of large staff sizes, frequent turnover, and the reliance on temporary workers like travelers and contractors.
The causes are fairly predictable. When under pressure, IT teams often create quick, one-off roles instead of leveraging existing ones. Add in new clinical applications or third-party systems that don’t align with central standards, and the role catalog balloons. Poor documentation only makes things worse, leaving security teams unsure of each role’s purpose. The result? A bloated system where reviewing access becomes a nightmare, and onboarding new clinicians becomes unnecessarily complicated.
A review of four electronic health record (EHR) systems highlighted troubling gaps, such as failures in separating duties and inconsistent permission reviews. Poorly designed roles - like using vague permissions such as "access EHR" instead of specific Create, Read, Update, Delete (CRUD) privileges - can lead to over-assigned permissions. This not only violates the principle of least privilege but also increases the risk of breaches and insider threats.
The solution lies in better role engineering, as outlined below.
Solutions: Better Role Engineering and Governance
To tackle role explosion, healthcare organizations need to adopt disciplined role engineering and governance practices. Start by auditing roles and permissions across all systems to identify duplicates and unused entries. Collaborate with leaders from nursing, medical staff, revenue cycle, and operations to understand actual workflows. This ensures roles align with what clinicians do rather than just their job titles. Create job-function–based roles (e.g., RNs, physicians, registration clerks) and add specialty or location-specific variants only when absolutely necessary. Use a clear CRUD permission framework to define exactly what each role can and cannot do.
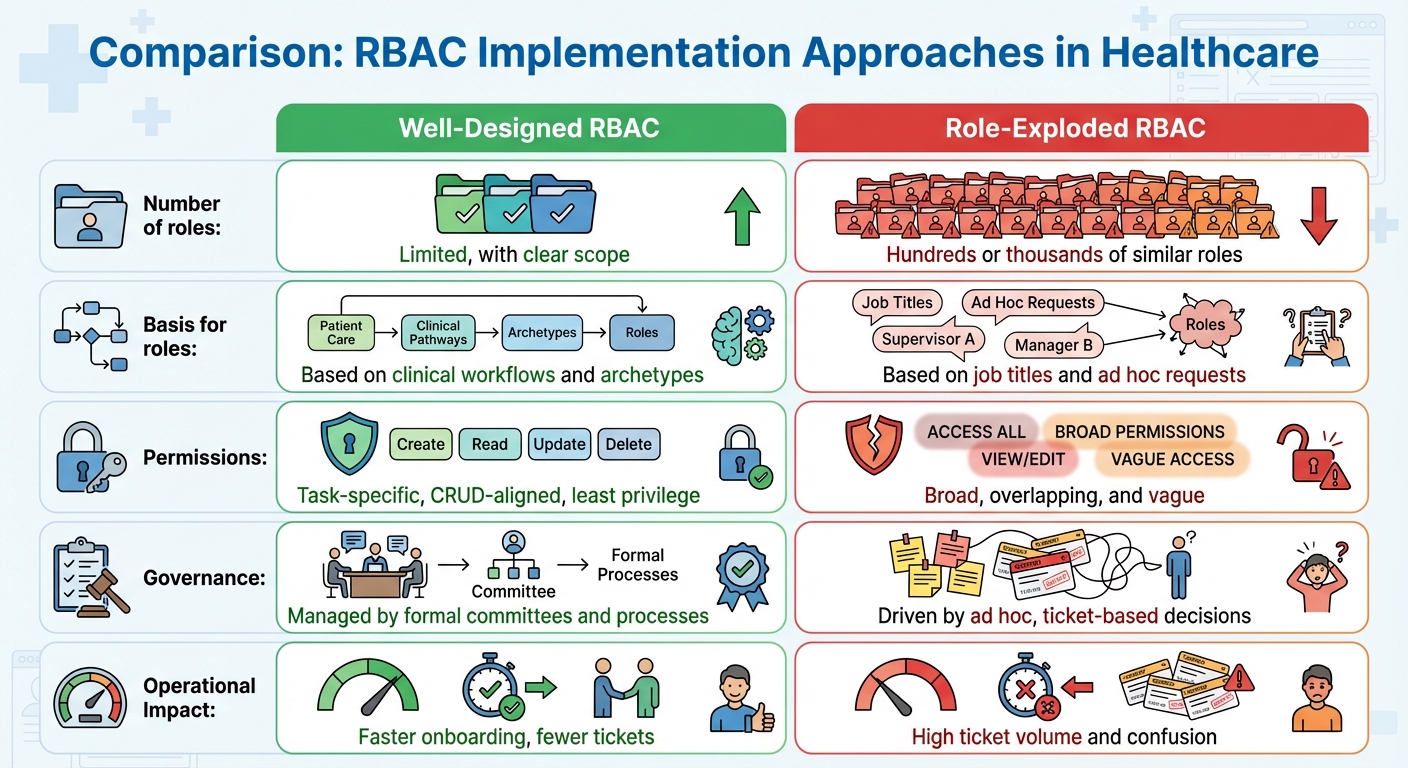
Here’s a comparison to illustrate the difference:
| Aspect | Well-Designed RBAC | Role-Exploded RBAC |
|---|---|---|
| Number of roles | Limited, with clear scope | Hundreds or thousands of similar roles |
| Basis for roles | Based on clinical workflows and archetypes | Based on job titles and ad hoc requests |
| Permissions | Task-specific, CRUD-aligned, least privilege | Broad, overlapping, and vague |
| Governance | Managed by formal committees and processes | Driven by ad hoc, ticket-based decisions |
| Operational Impact | Faster onboarding, fewer tickets | High ticket volume and confusion |
Effective governance starts with forming a cross-functional RBAC committee. This team should include representatives from IT, security, compliance, HR, and key clinical and business departments. Their job? Oversee new roles, manage changes, and retire outdated ones. A formal role lifecycle process - covering proposal, review, testing, approval, and documentation - is essential. Clear naming conventions (e.g., "HOSP_INPATIENT_RN_READWRITE_ORDERS") also help reduce duplication and ambiguity.
For roles that involve third-party systems, tools like Censinet RiskOps™ can centralize risk assessments and monitor vendors continuously. This platform provides visibility into which roles access external applications and what types of sensitive data - like PHI or medical device telemetry - are involved. Such insights help the RBAC committee prioritize cleanup efforts and tighten controls, especially for remote access scenarios like imaging or telehealth.
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
Finally, tracking metrics such as the total number of active roles, the average number of roles per user, and the percentage of orphaned roles can help measure progress. Testing roles in a staging environment with clinicians ensures that access is appropriate - not too much, not too little. Monitoring related service tickets can also signal where adjustments might still be needed.
Challenge 2: Privilege Creep and Least-Privilege Drift
Healthcare organizations face another pressing challenge beyond the proliferation of roles: the gradual expansion of access permissions over time. Even when roles are initially well-defined, permissions often grow unchecked. This phenomenon, known as privilege creep or access creep, happens when users accumulate more access than they need to perform their current job. In healthcare, where staff frequently switch departments, take on temporary roles, or handle emergency shifts, privilege creep is particularly common - and dangerous.
How Privilege Creep Impacts Healthcare
Privilege creep usually follows predictable patterns. For instance, employees might retain access from previous roles when they transition to new ones. Analysts may keep elevated database permissions long after a project ends. Contract workers often leave with access levels that exceed the scope of their assignments.
This unchecked accumulation of access directly conflicts with HIPAA's Security Rule, which mandates that access to electronic protected health information (PHI) be limited to the minimum necessary for job functions. When privilege creep occurs, more accounts have access to PHI than needed, making compliance audits more challenging and increasing the risk of data breaches. For example, if a nurse's account is compromised, it could potentially access clinical notes, prescribing tools, or download patient reports - privileges that should have been restricted.
The risks aren’t limited to external threats. Over-provisioned access also amplifies the danger of insider threats. Malicious insiders with excessive permissions can extract far more PHI, billing data, or research materials than their roles justify. This makes detection harder and increases the damage they can cause. Even accidental misuse becomes more likely when access is overly broad. A study of four RBAC-enabled EHR systems highlighted poor separation of duties and weak permission reviews, underscoring governance gaps that contribute to privilege creep [3].
Solutions: Enforcing Least-Privilege Access
Tackling privilege creep requires a mix of technical measures and strong governance practices. Start by designing roles based on actual job workflows using a CRUD model - Create, Read, Update, Delete - rather than vague permissions like "access data." For example:
- Front-desk staff might need Create/Read/Update access for scheduling and insurance data, but only Read access for basic patient demographics, with no access to clinical notes.
- Nurses might require Read/Update permissions for vitals and notes but no Delete privileges for encounter records.
- Billing analysts could need Read access to clinical summaries and Create/Update permissions for claims, but no access to prescribing systems.
Regular access reviews are critical. Conduct these reviews quarterly or semiannually, requiring managers and data owners to validate team member roles and adjust permissions as needed. High-risk permissions, such as those allowing mass data exports or billing overrides, should be reviewed monthly. Event-driven reviews - triggered by hires, transfers, promotions, or terminations - ensure outdated access is promptly removed while new permissions are granted. Enforcing segregation of duties (SoD) prevents any single user from performing conflicting tasks, like both submitting and approving high-value claims or documenting and signing off on orders.
Temporary or emergency access should also have strict controls. Use time-bound provisioning to ensure access automatically expires. For locums, residents, students, contractors, or other short-term roles, assign clear end dates for access rather than leaving privileges open-ended. Emergency "break-glass" access should include enhanced logging and mandatory post-event reviews. Centralized identity governance through an IAM/IGA platform integrated with HR systems can automate provisioning, de-provisioning, and access changes, reducing reliance on manual updates in tools like Active Directory.
Platforms such as Censinet RiskOps™ can support these efforts by consolidating risk data across internal and third-party systems that handle PHI. These tools enable standardized risk assessments to verify adherence to least-privilege principles, enforce SoD controls, and schedule periodic access reviews. Centralized workflows help identify issues like overly broad roles or missed reviews, assigning follow-up tasks to IT and compliance teams. Benchmarking against similar organizations can reveal gaps in access control practices, guiding improvements in identity governance, role design, or monitoring systems.
Finally, centralized logging paired with anomaly detection can help identify unusual access patterns, reducing misuse risks from over-provisioned accounts. Documenting role definitions, permission levels, approval processes, and exceptions creates an audit trail for when and why changes occur. Combining RBAC with multi-factor authentication for remote access and encrypting PHI both at rest and in transit adds additional safeguards, even if privilege creep results in unauthorized access.
Addressing privilege creep is essential for aligning roles with actual clinical workflows - a topic explored further in the next section.
Challenge 3: Roles That Don't Match Clinical Workflows and Emergency Access
Misaligned roles in healthcare systems go beyond the issue of privilege creep, creating additional challenges for Role-Based Access Control (RBAC). When roles fail to reflect real clinical workflows, they disrupt operations and complicate access management.
Why Roles Don't Align with Workflows
Most RBAC setups are built around IT system features rather than actual clinical tasks. For instance, a role like "EHR basic user" doesn’t clarify whether it’s meant for a night ICU nurse, a telehealth hospitalist, or a remote coder working across departments. This disconnect forces clinicians to request constant exceptions or even share accounts to complete routine tasks, creating security risks and workflow inefficiencies [2][3].
Healthcare operations further complicate this issue. Clinicians often rotate between units, work variable shifts, or cover multiple facilities. However, standard RBAC roles are usually designed with fixed locations and schedules in mind. This leads to access gaps - like when a hospitalist needs temporary access to another team’s patients - or over-broad access, such as a float nurse being granted permanent permissions for all units they might occasionally visit [3]. Modern care models, including telehealth and remote coding, add yet another layer of complexity. Traditional role structures can’t keep up with the need for secure access to EHRs, imaging systems, and e-prescribing tools from remote locations like home offices or satellite clinics [3][4].
A systematic review of RBAC in health information systems revealed troubling findings: among four evaluated RBAC-aware EHR systems, none fully implemented separation of duties, and two lacked "permission-role review" practices [3]. The research highlighted a widespread consensus that standard RBAC models require adaptations to address healthcare’s unique needs, including emergency access and complex workflows [3].
Solutions: Workflow-Based Role Design and Emergency Access Protocols
To address these challenges, roles should be mapped to clinical workflows instead of generic job titles. Start by conducting a collaborative discovery process involving IT teams, clinicians, charge nurses, and department leaders. This process should document key workflows - such as admissions, medication ordering, telehealth visits, and discharges - and identify the systems and data required at each step [2][6]. Roles should then be designed around specific tasks and contexts. For example:
- An "ED triage nurse – nights" role might include permissions for triage documentation, order entry under protocol, and viewing all ED patients, while excluding inpatient modules [2][4].
- A telehealth physician role could focus on remote visit documentation, e-prescribing, diagnostic result reviews, and secure messaging, while restricting access to on-site-only functions like OR scheduling [3][4].
Dynamic constraints can further refine access. Time-of-day or location-based restrictions can limit high-risk permissions - like broad patient list access or cross-facility chart access - to scheduled shifts and secure areas. Similarly, device-aware policies can allow view-only access from personal devices while restricting sensitive tasks, like exporting data or running bulk reports, to managed devices [3].
For emergencies, implement formal "break-glass" protocols that provide time-limited, case-specific access. These protocols should include strict eligibility criteria, clear documentation of the justification, enhanced logging, and automatic revocation after a set period [3][6].
Censinet RiskOps™ offers tools to support these dynamic controls. By continuously correlating role definitions with risk profiles, the platform helps healthcare organizations identify and address access risks. It inventories high-risk workflows - such as EHRs, telehealth platforms, and medical devices - and flags roles that grant overly broad access to sensitive data. This enables organizations to redesign roles or add controls where necessary. Censinet also centralizes risk assessments, benchmarks cybersecurity posture, and facilitates collaboration between healthcare organizations and vendors. This ensures that as workflows evolve - such as through new telehealth services or expanded remote monitoring programs - access risks are monitored and addressed to protect patient safety, privacy, and compliance [3].
Finally, assign clear ownership of roles and emergency access policies to a joint clinical-IT steward, such as a Chief Medical Information Officer (CMIO) paired with a nursing informatics lead. Establish regular review cycles - quarterly for standard roles and monthly for high-risk permissions. Regular audits can track metrics like the frequency of emergency access events, the number of access change requests, and audit findings related to role misalignment. This data helps refine RBAC designs over time, ensuring they stay aligned with evolving clinical practices.
Next, we’ll explore the challenge of weak identity governance during onboarding and offboarding.
sbb-itb-535baee
Challenge 4: Weak Identity Governance in Onboarding and Offboarding
Even the most well-crafted RBAC roles can crumble if identity governance is lacking. Weak governance leaves unauthorized access lingering long after it should be revoked, creating vulnerabilities and setting the stage for the access control challenges outlined below.
How IAM/IGA Problems Lead to RBAC Failures
In healthcare, manual processes for creating and terminating accounts often lead to identity governance breakdowns. When HR termination data isn't automatically integrated with IAM and IGA tools, user accounts frequently remain active after employees or contractors leave. These “orphaned accounts” can persist in electronic health records (EHRs), VPNs, and shared drives [4]. Not only do these dormant accounts become prime targets for attackers, but they also make it harder to prove to auditors that access is restricted to those with legitimate operational needs.
These issues compound when onboarding and role updates are handled poorly. Without connecting HR and credentialing systems to directories and EHRs, new clinicians often face significant delays - sometimes days - before gaining access due to manual role assignments. This ticket-based system often results in inconsistent role mapping across platforms. For instance, a "Nurse Practitioner" role might grant different permissions in an EHR compared to an imaging system, creating confusion and inefficiencies.
The problem escalates when employees change departments or roles. Without proper role cleanup, users can accumulate permissions from previous positions, leading to "privilege creep." This violates the principle of least privilege and can result in excessive access rights. Given the high turnover rates and reliance on contractors or temporary staff in healthcare, these issues are especially pressing. The Office of Inspector General has frequently highlighted the failure to terminate access for former employees and contractors as a common HIPAA Security Rule violation [3]. These challenges highlight the importance of automated, centralized identity governance in maintaining effective RBAC.
Solutions: Centralized Identity Governance
To sustain effective RBAC, centralized identity governance with automated workflows is essential. While designing roles correctly is critical, keeping them accurate over time requires synchronized identity governance. Start by integrating your IAM or IGA platform with key data sources:
- HR systems: For employment status, start and end dates, job codes, departments, and locations.
- Credentialing systems: For clinical privileges and scope of practice.
- Directory services: Such as Active Directory or Azure AD, to serve as the central identity repository [4].
These integrations should enable automatic workflows for joiners, movers, and leavers. For example, new hires should receive their baseline RBAC roles on day one, role changes should reflect updated job codes or privileges, and terminations should trigger immediate deprovisioning across all connected applications.
When offboarding, enforce same-day deactivation for network, EHR, email, VPN, and other third-party systems. All access changes should go through controlled, auditable workflows to eliminate unauthorized manual adjustments.
Conduct regular access reviews where managers verify each user’s roles and permissions. This helps identify and clean up orphaned accounts or outdated elevated privileges. For contractors, residents, students, and vendors, set strict end dates, require sponsor approvals, and enforce automatic expiry unless re-certified for extensions.
Censinet RiskOps™ supports this centralized approach by integrating identity governance with broader risk management. The platform consolidates enterprise risk assessments, enabling healthcare organizations to track vendor and application risks alongside specific RBAC roles. By continuously monitoring systems handling electronic protected health information (ePHI), clinical applications, and medical devices, Censinet RiskOps™ ensures that identity governance aligns with the organization’s overall cybersecurity strategy. This unified view helps security and compliance teams prioritize reviews of high-risk access - such as broad EHR permissions or remote access - and track remediation efforts.
Next, we’ll explore how poor documentation and monitoring practices can lead to audit readiness challenges.
Challenge 5: Poor Documentation, Monitoring, and Audit Readiness
Even with well-designed roles and identity governance, healthcare organizations often stumble when it comes to documentation and monitoring. These gaps can severely impact their ability to pass audits. A robust RBAC system isn’t enough on its own - auditors need clear evidence that access is controlled, monitored, and regularly reviewed. Without detailed records and centralized logging, proving compliance with regulations like HIPAA becomes a serious hurdle.
Documenting Roles and Permissions for Audits
Auditors typically require a formal role catalog that explains each role, its purpose, the systems it interacts with, and the permissions it grants. Unfortunately, many healthcare organizations rely on outdated spreadsheets or obscure configurations buried in tools like Active Directory or EHR systems. Common documentation gaps include:
- Outdated or incomplete permission matrices
- Missing version histories for role creation or updates
- Poorly maintained user-to-role mappings
- Lack of records for access reviews or change control logs [2][4]
These gaps make it difficult to prove adherence to the principle of least privilege or to trace who accessed PHI and for what purpose.
A proper role catalog should include plain-language descriptions of each role, the associated job titles and departments (e.g., Registered Nurse, Emergency Department Physician), the systems involved (like EHR, PACS, or billing platforms), and the business rationale for PHI access [2][4]. The permission matrix should break down each role's access by system, specifying the data objects (e.g., lab results, billing codes) and actions allowed, all while aligning with the least privilege principle [2][4]. To strengthen audit readiness, documentation should also tie each role and permission to relevant regulatory requirements, creating a clear link between compliance rules and implemented controls [4].
Solutions: Centralized Logging and Regular Assessments
To address these documentation issues, organizations should focus on centralized logging and consistent access reviews. A centralized logging system can collect and standardize access data from various sources, such as EHRs, identity providers, VPNs, and medical devices. Key events to log include:
- Logons and logoffs
- Successful and failed attempts to access PHI
- Changes to roles or permissions
- Assignment or removal of roles
- Emergency access overrides [4][5]
Each log entry should capture critical details like user ID, roles, patient/record identifiers, action types, source system/location, timestamps, and any associated approvals or tickets [2][4]. By standardizing this data, organizations can provide auditors with a comprehensive view of user activity.
Regular access reviews are equally important. For high-risk systems like EHRs, reviews should happen quarterly, while lower-risk systems may only require annual reviews [2][4]. These reviews should verify that user roles align with their job functions, that roles reflect current permission matrices, and that temporary or emergency access has been revoked [2]. Additionally, annual role-level assessments can ensure that roles continue to uphold the least privilege principle, factoring in new services, integrations, or regulatory changes [5].
AI tools can make managing RBAC documentation and audit preparation far less labor-intensive. For instance, platforms like Censinet RiskOps™ centralize risk data and link it to specific clinical applications and PHI workflows. These tools can automatically organize RBAC-related evidence - such as policies, logs, and role catalogs - and map them to compliance frameworks like HIPAA or NIST [2][4]. They can also flag risks, such as roles with excessive permissions or unusual access patterns, and generate audit-ready reports. With platforms like Censinet, healthcare organizations can quickly compile and present documentation, including role definitions, vendor risk assessments, access logs, and review approvals, streamlining the audit process and reducing follow-up questions. This comprehensive approach ensures continuous oversight and simplifies compliance across the RBAC lifecycle.
Conclusion: A Step-by-Step Approach to RBAC Implementation in Healthcare
Phased Implementation for Long-Term RBAC Success
Rolling out Role-Based Access Control (RBAC) in healthcare demands a careful, step-by-step strategy. Begin by taking stock of all systems containing Protected Health Information (PHI) and cataloging roles to pinpoint areas with high-risk access. Then, assess potential risks and workflows to prioritize departments and align clinical tasks with specific permissions. Design standardized roles - like ED nurse, hospitalist, or HIM coder - using clear CRUD-style permissions, steering clear of overly broad access rights.
A pilot program in one department serves as a practical testing ground. This phase lets teams trial the roles in real-world workflows, gather feedback from clinicians, and fine-tune access controls before expanding the implementation. Once the pilot is successful, integrate RBAC into a centralized identity governance system. This ensures that processes like onboarding, role changes, and terminations automatically adjust access permissions. Keep the system dynamic by conducting regular access reviews, tracking key metrics, and updating roles as services and needs evolve.
Tools like Censinet RiskOps™ simplify this process by centralizing risk data and automating evidence collection. For instance, Tower Health managed to conduct more risk assessments with fewer resources after implementing this solution [1]. By streamlining audit preparation and automating workflows, such tools help healthcare organizations maintain RBAC as a flexible, adaptive control that evolves with emerging threats and regulatory demands.
Key Takeaways for Healthcare Organizations
A phased approach lays the groundwork for sustainable RBAC success. However, viewing RBAC as a one-time setup leads to failure. Challenges like role sprawl, privilege creep, misaligned workflows, weak governance, and poor documentation require ongoing attention. Effective RBAC hinges on designing roles around clinical workflows rather than rigid organizational charts. Enforcing least-privilege principles means automating processes for onboarding, role changes, and terminations, while also implementing time-limited privilege elevation and regular access reviews to curb excessive permissions.
Equally critical is integrating RBAC with centralized identity governance. This ensures access changes follow structured, policy-driven processes instead of being handled through uncoordinated administrative edits.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
FAQs
What strategies can healthcare organizations use to address role explosion in RBAC?
Healthcare organizations can address the challenges of managing role-based access control (RBAC) by implementing a hierarchical role structure. This approach organizes similar roles into broader categories, streamlining management and making it easier to handle access permissions. Regular audits and role reviews are also essential for identifying redundancies and ensuring permissions stay accurate and relevant.
Automation can play a key role in simplifying role assignments, reducing administrative workloads, and minimizing mistakes. Tools like Censinet RiskOps™ offer additional support by combining access control with risk management, providing a scalable and secure solution specifically designed for healthcare settings.
How can healthcare organizations prevent privilege creep when using role-based access control?
Preventing privilege creep in healthcare settings demands a thoughtful and organized strategy. One key step is to perform regular access reviews to confirm that employees only retain permissions directly tied to their current responsibilities. This ensures access isn’t unnecessarily broad or outdated.
Another essential practice is enforcing the principle of least privilege, which limits users to the minimum level of access they need to carry out their tasks. To streamline this process, consider using automated tools that can track and flag any instances of privilege creep. These tools make it easier to spot and resolve issues quickly.
Equally important is having a well-defined system to remove excess permissions when employees shift roles or exit the organization. By following these measures, healthcare organizations can better safeguard sensitive patient information and strengthen their overall security posture.
How can RBAC roles be tailored to fit clinical workflows effectively?
To make sure RBAC roles fit seamlessly into clinical workflows, it's crucial to include clinicians and other end-users in the process of defining these roles. Align roles closely with the actual tasks and responsibilities involved in patient care to improve usability while maintaining strong security. Additionally, it's important to routinely review and adjust roles to keep up with any changes in workflows or organizational priorities, ensuring they stay practical and effective.


