5 Common Cloud Vendor Risks in Healthcare
Post Summary
Cloud vendors play a critical role in U.S. healthcare, powering systems like EHRs, billing, and telehealth. However, this reliance introduces serious risks that can jeopardize patient safety, compliance, and operations. Here are the top five risks healthcare organizations face when working with cloud vendors:
- Data Breaches and PHI Exposure: Misconfigured settings, weak access controls, and ransomware attacks can expose sensitive patient data. In 2025 alone, 1,542 healthcare data breaches were confirmed, with an average cost of over $10 million per incident.
- Compliance Failures: Vendors often struggle to meet healthcare-specific regulations like HIPAA and HITECH, leading to regulatory violations and financial penalties.
- Service Downtime: Outages caused by cyberattacks or vendor failures disrupt critical systems, delaying care and impacting patient outcomes.
- Data Governance and API Risks: Poorly managed integrations and unclear data flows increase the risk of unauthorized access and compliance issues.
- AI and Emerging Technology Risks: AI tools and IoMT devices introduce new vulnerabilities, such as data misuse, security gaps, and ethical concerns.
Addressing these risks requires healthcare-specific vendor risk management, including continuous monitoring, clear contractual terms, and tools like Censinet RiskOps™ to streamline assessments and improve security.
1. Data Breach and PHI Exposure Risk
Impact on Patient Safety and PHI Security
When cloud vendors experience breaches, Protected Health Information (PHI) often ends up in the hands of cybercriminals. PHI is particularly attractive on the black market due to its long-term value. Unlike credit card numbers, which can be canceled quickly, PHI includes enduring personal details such as Social Security numbers, medical histories, and insurance data - information that criminals can exploit for years through identity theft and fraud [6][7].
The scope of these breaches is staggering. The healthcare industry consistently reports some of the highest rates of data disclosure across all sectors [7]. Beyond the immediate risk to patient safety, these incidents highlight deeper flaws in vendor security practices.
Vendor Compliance with Healthcare Regulations
Minimizing the risk of PHI exposure hinges on vendors adhering to strict compliance measures. A concerning 72% of organizations report cloud account compromises, with 61% noting an increase in incidents year over year [8]. Cybercriminals exploit weak identity and access management (IAM) systems, stolen credentials, and insecure remote access points to infiltrate PHI repositories. Once inside, they often move laterally through third-party systems, such as EHR platforms, billing solutions, and telehealth services, to access data across interconnected networks [10][11][12].
Ransomware attacks have become a major threat, with cloud vendors and managed service providers increasingly targeted as "central hubs" to breach multiple healthcare organizations simultaneously [13]. In just the first nine months of 2025, 130 ransomware attacks impacted healthcare businesses - including vendors, billing companies, and health tech firms - representing a 30% rise compared to the previous year [13]. These attacks compromised 6,049,434 records, with ransom demands averaging $532,000. One notable campaign, the Interlock ransomware attack on DaVita and other providers, resulted in the breach of 2,735,407 records [13].
To safeguard PHI, healthcare organizations must ensure their cloud vendors implement critical security measures. These include multi-factor authentication (MFA) for all administrative accounts, enforcing least-privilege access controls, and maintaining secure configurations - such as encryption for data at rest and in transit [7][9]. Vendors should also provide on-demand audit logs and continuous monitoring to flag unusual activity involving PHI [7][9]. Additionally, clear contractual agreements are essential, outlining Business Associate Agreement (BAA) terms, breach notification timelines, and accountability for security lapses or misconfigurations.
2. Compliance and Regulatory Failure Risk
Vendor Compliance with Healthcare Regulations
When cloud vendors fall short of meeting HIPAA, HITECH, and other U.S. healthcare regulations, the impact is felt across patient care and data security. One of the most common issues? Misconfigurations. These preventable mistakes lead to lingering regulatory headaches.
Part of the problem lies in the sheer complexity of healthcare regulations. Matt Christensen, Sr. Director GRC at Intermountain Health, puts it plainly:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
Off-the-shelf cloud compliance frameworks often overlook critical healthcare-specific requirements, such as those related to patient data, research protocols, and device integration [1]. This lack of alignment creates a ripple effect, complicating data governance and the adoption of emerging technologies.
Data Governance and Integration Transparency
Good data governance ensures that PHI (Protected Health Information) is handled responsibly - collected, stored, shared, and accessed only when necessary and by authorized individuals. This requires applying principles like role-based access controls and adhering to "minimum necessary" standards across cloud environments [3][4][5]. But problems arise when vendors fail to provide transparency around how APIs manage data. Without this clarity, healthcare organizations may unknowingly experience "undocumented data transfers" into non-compliant services or regions. These issues make breach investigations, access requests, and legal holds more complex, driving up audit costs [4][5].
To tackle this, healthcare providers need vendors to offer standardized governance frameworks and detailed architectural documentation. Without clear insight into which systems handle PHI, where data is stored or replicated, and how APIs expose sensitive information, staying compliant with HIPAA is a daunting task [3][4]. Poorly managed integrations leave gaps that often come to light only after a breach has occurred - when it's too late.
AI and Emerging Technology Risk Governance
Emerging technologies like AI introduce a whole new set of compliance challenges. When AI systems process PHI, questions arise about data ownership, secondary usage rights, training data, and cross-border transfers [2][5]. Risks include unauthorized use of PHI, insufficient de-identification, and the use of opaque algorithms. To mitigate these risks, governance frameworks must enforce strict limits on PHI use, require robust de-identification processes, and ensure human oversight for high-risk applications [2][5].
Regular audits of AI workflows are essential to ensure they remain within both regulatory boundaries and the organization’s risk tolerance [2][5]. Without these safeguards, AI technologies could inadvertently introduce new compliance vulnerabilities.
Addressing these regulatory and governance challenges is essential for building a secure and compliant cloud environment in healthcare.
3. Downtime and Service Disruption Risk
Impact on Patient Safety and PHI Security
When cloud systems experience downtime, the effects ripple far beyond mere inconvenience. Ransomware attacks and other cyber incidents are leading causes of cloud and application outages, cutting off clinicians from essential systems and directly impacting patient care [7][4]. A stark example is the February 2024 ransomware attack on Change Healthcare, which disrupted operations nationwide. This single incident delayed prescriptions and claims processing across pharmacies, hospitals, and payers [4].
The 2025 Verizon DBIR report paints a concerning picture: the healthcare sector faced 1,710 security incidents, with 1,542 confirmed data breaches. Such attacks can disable clinical systems, slow down care delivery, and compromise sensitive patient information [7][4]. These challenges highlight the critical importance of building strong operational resilience.
Operational Resilience and Service Uptime
To minimize these risks, healthcare providers must prioritize operational resilience. Migrating to the cloud shifts much of the control over outages to vendors, making vendor selection and contract terms a top priority [3]. Providers should evaluate vendors on their uptime guarantees, ensure they maintain immutable or offline backups, and confirm their recovery procedures have been thoroughly tested. This ensures systems can be restored promptly without succumbing to ransomware demands [7][3].
Contract terms that address data portability and provide transition support are essential to reduce downtime risks [4]. Healthcare organizations should also regularly test offline contingency plans for critical functions like patient registration, medication administration, and documentation. Additionally, clear communication strategies - such as SMS alerts, phone trees, or secure messaging - are vital for keeping clinicians and leadership informed during outages, including updates on restoration timelines.
AI and Emerging Technology Risk Governance
Service continuity becomes even more critical when advanced technologies like AI are involved. Outages in cloud-hosted AI services can disrupt diagnostic workflows and reduce efficiency, even if core EHR systems remain operational [2][14]. Governance frameworks for these technologies should go beyond performance metrics and bias controls. Vendors must also demonstrate reliable uptime architectures, fallback mechanisms for service interruptions, and clear guidelines distinguishing clinical from non-clinical use. These measures ensure that appropriate continuity plans are in place to manage risks effectively [2][14].
4. Data Governance and API Integration Risk
Data Governance and Integration Transparency
Cloud account breaches impact a staggering 72% of healthcare organizations, with 61% reporting an increase in incidents[8]. These troubling numbers often result from weak identity and access management practices and insufficient oversight of cloud accounts and APIs. When healthcare applications rely on APIs to connect through shared cloud platforms, misconfigurations or lax access controls can leave protected health information (PHI) vulnerable to exposure[7][9]. To counter these risks, it’s essential to establish clear contractual standards that emphasize security in these integrations.
The real danger of poor data governance is that its consequences might go unnoticed for years, leaving patient data exposed and unprotected over time. This highlights the critical need for consistent and thorough oversight of cloud services and API integrations.
Vendor Compliance with Healthcare Regulations
Generic data governance tools often aren’t equipped to handle the intricacies of managing healthcare data with cloud vendors. Healthcare organizations need solutions that can be tailored to meet the unique demands of their industry.
But technology alone isn’t enough. Organizations must map out all data flows and integrations in detail. This includes identifying systems that exchange PHI, specifying the types of data being transferred, and clarifying who is responsible for securing each integration point[7][9]. Vendor contracts should also address critical details like data ownership, retention policies, portability, and compliance with HIPAA and state privacy regulations. With the growing role of AI in healthcare, these governance measures need to extend to AI systems as well.
AI and Emerging Technology Risk Governance
When AI and other emerging technologies interact with cloud-hosted PHI through APIs, strong governance frameworks are non-negotiable. These frameworks should restrict AI’s access to PHI, mandate detailed documentation of training data and de-identification processes, and ensure that only the minimum necessary data is transferred[2][5][12]. Vendor contracts must also prohibit secondary use of PHI, require detailed logs of AI outputs, and enforce strict access controls[5][12].
Purpose-built platforms designed specifically for healthcare, like Censinet RiskOps™, simplify the complex governance challenges healthcare organizations face. James Case, VP & CISO at Baptist Health, shared how adopting specialized risk management tools transformed their processes:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."[1]
This kind of collaborative approach promotes standardized risk assessments and encourages transparent data sharing across the healthcare landscape.
sbb-itb-535baee
5. AI and New Technology Risk
Impact on Patient Safety and PHI Security
AI-powered cloud services bring both opportunities and risks, especially when it comes to protecting patient safety and safeguarding Protected Health Information (PHI). When AI tools are used to analyze clinical data - whether for adjusting medication doses, monitoring vital signs, or recommending treatments - a security breach can do more than just expose sensitive records. It can also disrupt patient care by compromising the accuracy of critical clinical inputs[7]. Recent reports highlight how the increased reliance on cloud-connected systems has amplified these vulnerabilities, creating new risks for healthcare organizations.
Internet of Medical Things (IoMT) devices add another layer of concern. Devices running on outdated software or with weak encryption are prime targets for attackers. Once they gain access, cybercriminals can manipulate device settings, falsify vital signs, or extract large volumes of sensitive data, all of which heighten risks to patient safety[8].
These challenges underscore the importance of robust security measures, particularly in AI-driven data management processes.
Data Governance and Integration Transparency
Developing AI tools typically involves copying PHI into various environments for training, validation, and testing. This process makes it harder to track where the data resides and how long it’s retained[15][17]. To complicate matters further, cloud vendors often aggregate data from multiple healthcare organizations to create generalized AI models. This raises thorny questions about consent, permissible use under Business Associate Agreements, and the ethics of sharing data across entities[16].
Integration issues add another layer of complexity. A striking 59% of healthcare organizations report that incorporating new cloud solutions into their existing IT systems is a major hurdle[4]. On top of that, opaque AI pipelines and undisclosed third-party data calls limit visibility into how PHI is handled. To address these issues, healthcare organizations should demand detailed data flow diagrams from vendors. These diagrams should clearly map out all systems and subprocessors that interact with PHI. Vendors should also provide explicit documentation of any PHI used in model training and implement automated tools to enforce data retention limits[3][17].
AI and Emerging Technology Risk Governance
Given these governance challenges, it’s clear that effective AI oversight requires human involvement at every critical decision point. Healthcare’s unique complexities call for tools tailored specifically to the industry. For example, Censinet RiskOps™ functions like an "air traffic control" system for AI risks. It routes assessment findings and potential risks to the appropriate stakeholders, such as members of an AI governance committee, for review and approval. This "human-in-the-loop" approach ensures that automation supports, rather than replaces, critical decision-making processes. The platform also provides real-time data through an intuitive AI risk dashboard, centralizing all policies, risks, and tasks related to AI.
Platforms like these also empower healthcare organizations to hold vendors accountable. For instance, they can require vendors to complete thorough security questionnaires with supporting documentation during the procurement process. Strong identity controls and detailed activity logs further help detect and mitigate suspicious actions[7][8]. By embedding AI governance into broader vendor risk management frameworks, healthcare organizations can tackle both the challenges posed by emerging technologies and the ongoing risks associated with cloud vendors.
Risk Comparison Table
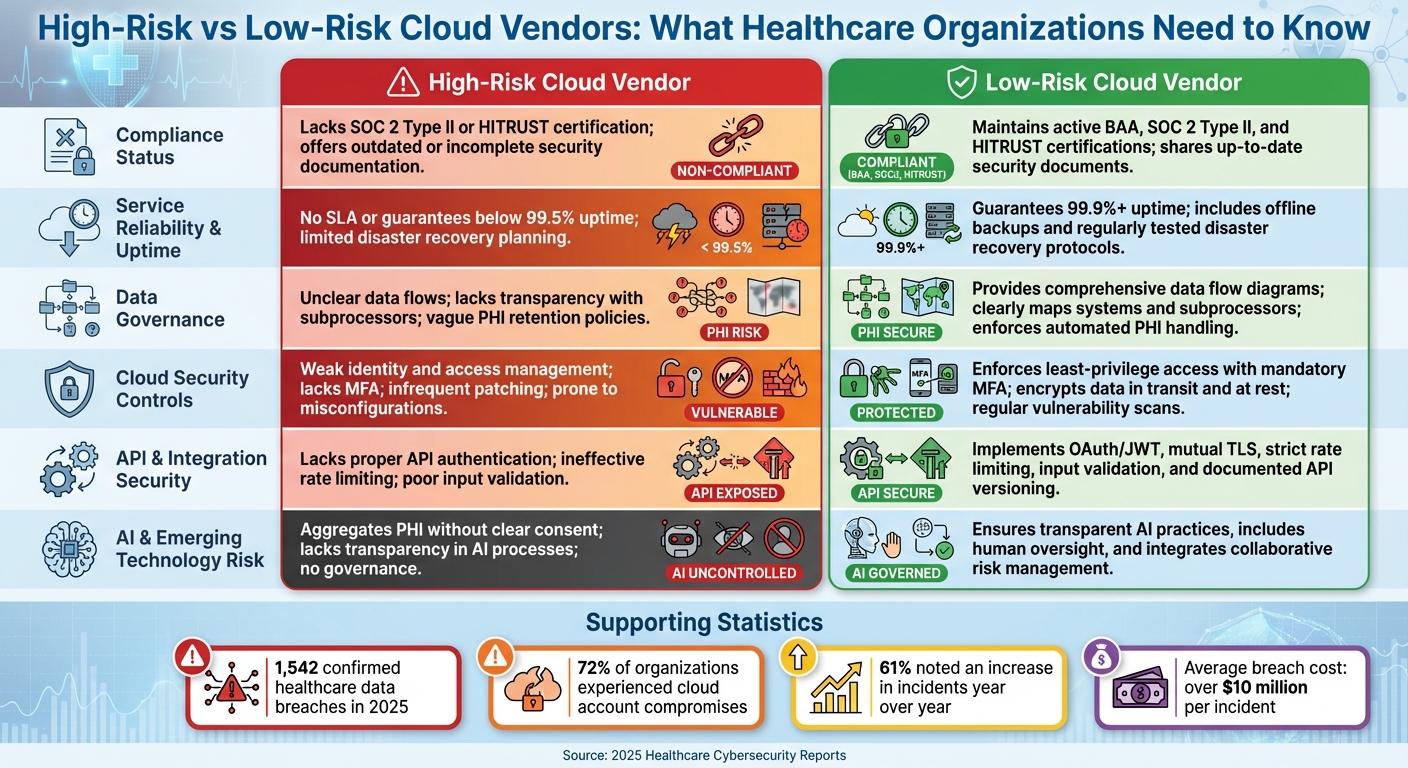
High-Risk vs Low-Risk Cloud Vendors in Healthcare: Key Comparison Criteria
This table provides a straightforward way to differentiate between cloud vendors that pose a high risk to healthcare organizations and those that prioritize security and governance. By examining key criteria, healthcare providers can identify vendors that safeguard patient data and operations versus those that may introduce vulnerabilities.
| Criteria | High-Risk Cloud Vendor | Low-Risk Cloud Vendor |
|---|---|---|
| Compliance Status | Lacks SOC 2 Type II or HITRUST certification; offers outdated or incomplete security documentation | Maintains active BAA, SOC 2 Type II, and HITRUST certifications; shares up-to-date security documents via Censinet Connect™ |
| Service Reliability & Uptime | No SLA or guarantees below 99.5% uptime; limited disaster recovery planning | Guarantees 99.9%+ uptime; includes offline backups and regularly tested disaster recovery protocols |
| Data Governance | Unclear data flows; lacks transparency with subprocessors; vague PHI retention policies; no detailed data flow diagrams | Provides comprehensive data flow diagrams; clearly maps systems and subprocessors; enforces automated PHI handling and retention policies |
| Cloud Security Controls | Weak identity and access management; lacks multi-factor authentication (MFA); infrequent patching; prone to misconfigurations like exposed storage buckets | Enforces least-privilege access with mandatory MFA; encrypts data in transit and at rest; performs regular vulnerability scans and monitoring |
| API & Integration Security | Lacks proper API authentication; ineffective rate limiting; poor input validation; no API versioning or change management | Implements OAuth/JWT, mutual TLS, strict rate limiting, input validation, and well-documented API versioning |
| AI & Emerging Technology Risk | Aggregates PHI without clear consent; lacks transparency in AI processes; no governance for AI usage | Ensures transparent AI practices, includes human oversight, and integrates collaborative risk management frameworks |
The 2025 Verizon Data Breach Investigations Report revealed 1,710 security incidents and 1,542 confirmed data breaches in healthcare, with system intrusions being a persistent issue [7]. Another 2025 report on healthcare cybersecurity found that 72% of organizations experienced cloud account compromises, with 61% noting an increase in incidents compared to the previous year [8]. These figures highlight the pressing need for rigorous vendor evaluations, especially when misconfigurations remain a leading cause of breaches [7].
Matt Christensen, Sr. Director of GRC at Intermountain Health, underscores the importance of tailored solutions for healthcare:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
Low-risk vendors recognize these complexities and align their practices with healthcare-specific risk management frameworks. In contrast, high-risk vendors often rely on generic solutions that fail to address the unique challenges of protecting sensitive patient data. This comparison lays the groundwork for actionable recommendations on managing vendor risks effectively.
Conclusion
The five risk categories - data breaches and PHI exposure, compliance failures, service disruptions, data governance/API integration issues, and AI/emerging technology risks - touch every corner of healthcare operations. Each presents unique challenges, threatening patient safety, financial health, and regulatory adherence. When cloud vendors fall short in addressing these risks, the ripple effects can disrupt clinical workflows, stall revenue cycles, and erode patient trust.
Tackling these challenges requires moving beyond outdated evaluation methods like manual spreadsheets, annual questionnaires, or binary checklists. These traditional approaches often lack the depth and flexibility needed to keep up with evolving threats. A more effective solution lies in structured vendor risk scoring. This quantitative, repeatable framework evaluates factors such as PHI volume, clinical importance, internet-facing vulnerabilities, compliance certifications, and past incidents. With this method, healthcare organizations can categorize vendors by risk level, focus deeper assessments on high-risk partners, and adjust scores as vendors expand their data processing or introduce AI-driven features.
This structured approach doesn’t just measure risk - it simplifies decision-making. For example, Censinet RiskOps™ integrates structured scoring by automating third-party risk assessments and standardizing data collection across a network of over 50,000 vendors. Terry Grogan, CISO at Tower Health, shared:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Similarly, James Case, VP & CISO at Baptist Health, remarked:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
Adopting healthcare-specific, modern risk management solutions is critical for safeguarding patient safety and ensuring the resilience of essential operations.
FAQs
What steps can healthcare organizations take to ensure their cloud vendors meet HIPAA and HITECH requirements?
To keep patient data secure and comply with HIPAA and HITECH regulations, healthcare organizations should focus on a few critical steps:
- Perform thorough risk assessments to uncover any weak points in vendor systems.
- Establish continuous monitoring to ensure vendors remain compliant and promptly handle any issues that arise.
- Utilize specialized tools like Censinet RiskOps™ to simplify third-party risk management, keep compliance on track, and benchmark cybersecurity efforts.
By taking a proactive approach and using tailored solutions, healthcare organizations can protect sensitive data while meeting regulatory requirements.
How can healthcare organizations secure patient data and prevent breaches in cloud environments?
To keep patient data safe and avoid breaches in cloud environments, healthcare organizations need to focus on ongoing risk assessments and use cybersecurity solutions designed specifically for healthcare, like Censinet RiskOps™. Key measures include setting up strict access controls, encrypting data both when stored and during transmission, and ensuring full compliance with HIPAA regulations.
Building a strong culture of cybersecurity awareness, frequently updating security protocols, and working closely with reliable vendors can also help reduce risks and safeguard sensitive patient information.
What risks do AI and IoMT devices pose to healthcare cloud systems?
AI and Internet of Medical Things (IoMT) devices are reshaping healthcare, but they also bring new security challenges to cloud systems. Here's why: AI systems can be targeted for harmful activities like tampering with data, launching phishing attacks, or even fabricating fake medical records. These kinds of breaches don't just compromise data - they can erode trust and put patient safety at serious risk.
On the other hand, IoMT devices, such as network-connected medical tools, often come with weak security features. This makes them prime targets for hackers. A successful attack could expose sensitive patient data, disrupt hospital operations, or even jeopardize lives if critical devices are taken offline. As healthcare increasingly relies on these technologies, addressing their vulnerabilities becomes crucial to safeguarding patient information and ensuring care goes uninterrupted.


