Cross-Border Data Transfers: Risks and Solutions
Post Summary
Cross-border healthcare data transfers are common but come with serious risks. When personal health information (PHI) moves across borders, organizations face regulatory challenges, security threats, and operational inefficiencies. Mismanaged transfers can lead to data breaches, fines, and reputational damage, especially with new U.S. rules restricting exports to high-risk countries.
Key Takeaways:
- Risks: Sensitive data can be misused or accessed in countries with weaker privacy laws. Compliance with regulations like HIPAA, GDPR, and the U.S. DOJ's new rules is complex.
- Challenges: Many healthcare providers lack visibility into their data flows and vendor activities, increasing the chances of unintentional violations.
- Solutions: Build detailed data inventories, use legal transfer mechanisms (e.g., SCCs, BCRs), strengthen vendor oversight, and implement safeguards like encryption and access controls.
To protect patient data and ensure compliance, healthcare organizations must focus on governance, technical defenses, and continuous monitoring.
Key Risks: Regulatory and Operational Challenges
This section dives into the complexities of global regulations and operational blind spots that healthcare organizations face, especially when dealing with cross-border data flows.
Fragmented Global Regulations
Healthcare organizations in the U.S. that operate internationally encounter a tangled web of conflicting rules. For instance, under the General Data Protection Regulation (GDPR), health data is classified as a special category requiring explicit consent or other narrowly defined legal bases. Data transfers outside the EU/EEA demand safeguards like Standard Contractual Clauses (SCCs), Binding Corporate Rules (BCRs), or an adequacy decision. In contrast, HIPAA enforces strict security protocols and Business Associate Agreements but doesn’t extend its reach beyond U.S. borders, leaving gaps in accountability.
The challenge doesn’t stop there. Countries like China, Saudi Arabia, and the UAE impose strict data localization laws and security assessments for health or other "important" data exports. These laws often require organizations to conduct transfer impact assessments and demonstrate adequate data protection in the destination country. This creates a compliance maze where a single data transfer might need to align with multiple, and sometimes contradictory, legal frameworks. Violating GDPR alone can lead to severe fines - up to 4% of global annual revenue or €20 million, whichever is greater.
These varied global regulations are paving the way for additional shifts in U.S. policies.
New U.S. Restrictions on Bulk Health Data Exports
Starting July 8, 2025, the U.S. Department of Justice introduced new rules under 28 C.F.R. Part 202 that impose strict limits on exporting sensitive personal data, such as health, genomic, and biometric information, to certain jurisdictions deemed high-risk. These regulations prohibit the sale or licensing of U.S. health data to entities in these regions. For permissible transfers, organizations must adhere to strict security protocols and maintain thorough documentation.
This poses significant challenges for routine operations like teleradiology, AI model training, and offshore billing services, which often involve cross-border data flows. Without proper oversight, organizations risk financial penalties, losing contracts, and damaging their reputation. To avoid these outcomes, healthcare providers must map their data flows and implement robust safeguards.
But regulatory hurdles aren’t the only issue - operational inefficiencies also play a major role in amplifying these risks.
Operational Blind Spots in Data Flow and Vendor Management
Many healthcare organizations struggle with outdated systems and manual processes, which limit their visibility into data flows and vendor activities. For example, Protected Health Information (PHI) shared with vendors like electronic health record providers, billing services, telehealth platforms, and AI analytics firms may be further processed or stored by sub-processors in other countries - often without the organization’s full knowledge. Data hosted in the cloud, diagnostic imaging, and analytics pipelines may also pass through foreign data centers, increasing the risk of unintentional cross-border transfers.
Research highlights widespread concerns about inconsistent standards, weak legal protections, and the potential for data misuse in such scenarios. Reliance on manual tools like spreadsheets or questionnaires makes it difficult to maintain continuous oversight of third-party data flows and cybersecurity measures. Many organizations lack accurate, up-to-date data inventories or transfer maps, leaving them unaware of cross-border flows that might breach GDPR, data localization laws, or the new DOJ restrictions.
The situation becomes even more complicated when vendors engage their own sub-processors abroad, creating what’s known as "fourth-party relationships." Without a centralized system to monitor these risks, healthcare providers face heightened exposure to regulatory violations. Closing these operational gaps is critical to ensuring compliance and reducing vulnerabilities, as discussed in upcoming sections.
Solutions for Reducing Cross-Border Data Risks
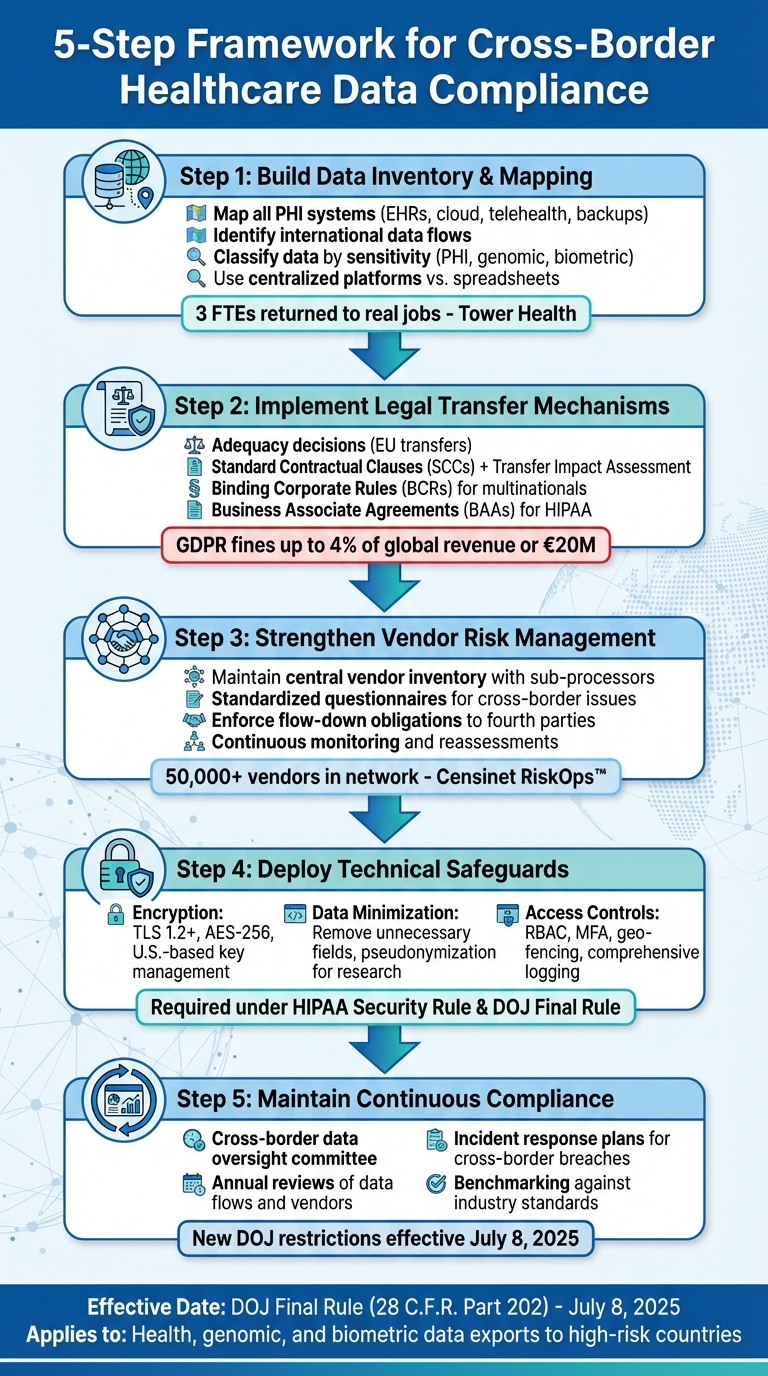
5-Step Framework for Cross-Border Healthcare Data Compliance
Healthcare organizations face a complex regulatory landscape and operational challenges when managing cross-border data flows. To navigate these challenges effectively, they need a combination of strong governance frameworks and technical controls. Below are practical steps to ensure safer and more compliant handling of cross-border data.
Build a Data Inventory and Mapping Program
A solid compliance strategy begins with understanding your data: what you have, where it resides, and who accesses it. This means mapping all systems that store or process Protected Health Information (PHI), such as electronic health records (EHRs), research databases, cloud platforms, telehealth systems, and backup sites. It’s also crucial to identify any international data flows and to classify data by sensitivity - whether it’s PHI, genomic information, biometric data, or other regulated categories.
Maintaining an up-to-date data map requires continuous collaboration across teams, especially after system changes or updates to vendor contracts. Relying on manual tools like spreadsheets can lead to outdated or incomplete information, which may result in untracked systems transferring data internationally. Instead, consider using centralized risk-management platforms designed specifically for healthcare.
Terry Grogan, CISO at Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
Similarly, James Case, VP & CISO at Baptist Health, noted, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
Platforms like Censinet RiskOps™ offer cloud-based solutions that connect healthcare organizations with over 50,000 vendors and products. These tools enable secure sharing of cybersecurity and risk data while keeping a close eye on third-party data flows.
Once you’ve mapped your data flows, the next step is ensuring compliance through legal transfer mechanisms.
Use Compliant Data Transfer Mechanisms
With a clear understanding of data flows, organizations can implement legal frameworks to validate international transfers. The right approach depends on the jurisdictions involved and the type of data being transferred. For example, if you’re handling health data originating in the EU, adequacy decisions are the simplest option. These allow transfers to countries recognized by the European Commission as offering adequate data protection, minimizing additional compliance burdens.
If no adequacy decision exists, organizations can use Standard Contractual Clauses (SCCs) paired with a Transfer Impact Assessment to document legal risks and outline necessary safeguards. For large multinational healthcare systems or life sciences companies, Binding Corporate Rules (BCRs) - though requiring regulator approval - can streamline intra-group data transfers.
In cases where data transfers are non-routine, organizations might rely on exceptions like explicit patient consent or public interest needs. However, these should be reserved for exceptional circumstances rather than ongoing data flows. U.S. entities must also meet domestic rules. For example:
- HIPAA requires Business Associate Agreements (BAAs), adherence to minimum necessary standards, and secure transmission channels for offshored PHI.
- The DOJ’s Final Rule prohibits selling or licensing health data to certain countries and enforces strict security and contractual controls for restricted transactions.
In regions with strict localization laws, such as China’s PIPL or health data rules in the Gulf, organizations should assess whether data can remain in-country while being analyzed remotely using privacy-enhancing technologies. Only export data that meets regulatory conditions.
Strengthen Vendor and Fourth-Party Risk Management
Vendors and their sub-processors often present significant cross-border data risks. To mitigate these risks, maintain a central inventory of vendors processing PHI, including details about their infrastructure locations and sub-processors. Use standardized questionnaires to focus on cross-border data issues and ensure contracts include clear obligations for secure data processing. These should cover data location, encryption standards, and immediate breach notifications. Additionally, enforce flow-down obligations, requiring vendors to apply the same controls to their sub-processors.
Automated platforms tailored for healthcare, like Censinet RiskOps™, simplify vendor assessments, BAAs, and data processing agreements. They also benchmark vendor security against industry standards and facilitate collaboration on remediation plans.
Brian Sterud, CIO at Faith Regional Health, emphasized, "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
Matt Christensen, Senior Director of GRC at Intermountain Health, added, "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."
For high-risk vendors, implement continuous monitoring through periodic reassessments, updated certifications, security dashboards, and alerts for changes in hosting locations or major incidents. In cross-border healthcare partnerships - such as U.S.-Mexico telehealth or billing arrangements - ensure end-to-end encryption for PHI, role-based access controls, logging for remote staff, and strict device and network security policies.
Technical Safeguards to Reduce Data Transfer Risks
Technical safeguards play a critical role in protecting Protected Health Information (PHI) during international transfers. While governance and legal measures establish the foundation, technical safeguards actively prevent unauthorized access and misuse of data. For U.S. healthcare organizations handling cross-border transfers of PHI, implementing encryption, limiting data exposure, and enforcing strict access controls are essential under HIPAA and other regulations.
Encryption and Key Management Best Practices
Encryption is a must for transferring electronic PHI across borders. HIPAA's Security Rule explicitly prohibits the use of unencrypted email, consumer messaging apps, and public file-sharing platforms for transmitting PHI[3]. Organizations must encrypt data in transit using secure protocols like TLS 1.2 or higher and protect stored data with methods such as AES‑256 encryption[3].
Key management, however, is where things often get tricky. Storing cryptographic keys outside the U.S. can lead to risks like government access requests or insider threats. To mitigate these risks, healthcare organizations should keep key control within the U.S. Options include using U.S.-based Hardware Security Modules (HSMs), customer-managed encryption keys, or key-splitting methods that ensure no single party can decrypt data independently. Strengthen these measures with strict access policies, regular key rotation, and segregation of duties. These practices align with the Department of Justice's Final Rule under Executive Order 14117[5].
Once encryption is in place, organizations should also focus on minimizing data exposure to further reduce risks.
Data Minimization and Pseudonymization
Transferring only the minimum necessary data is a cornerstone of both GDPR and HIPAA's "minimum necessary" standard[8]. In practice, this means removing unnecessary fields, limiting the number of records shared, and excluding free-text clinical notes that might contain identifiable information. Sensitive fields, such as Social Security numbers or genetic markers, can be further protected using techniques like field-level masking or tokenization.
For secondary purposes like research, AI development, or outcomes analysis, pseudonymization provides an added layer of security. This involves replacing direct identifiers with codes and storing the re-identification key in a separate, highly secure environment - ideally within the U.S. By doing so, overseas data recipients cannot re-identify individuals without explicit, controlled collaboration. This approach is not only recommended under GDPR but also helps mitigate regulatory risks and the impact of potential data breaches. Organizations should clearly differentiate between de-identification, pseudonymization, and limited data sets based on their intended use and the jurisdiction involved.
Reducing data exposure is only part of the solution; robust access controls are equally important.
Access Controls and Monitoring
Even when data is encrypted and minimized, strict access controls remain essential. Role-based access control (RBAC) and the principle of least privilege are foundational safeguards required under HIPAA[3]. Cross-border access should be restricted to roles that genuinely need it, such as clinicians, authorized researchers, or billing staff. Additionally, multifactor authentication (MFA) must be enforced for any remote or international access to PHI systems.
Geo-fencing and conditional access policies provide an extra layer of security. For instance, restricting logins from high-risk countries or specific IP ranges and requiring additional verification for non-U.S. access can significantly enhance protection while complying with national transfer restrictions[5].
Comprehensive logging and monitoring are also critical for detecting and addressing cross-border data misuse. Every PHI access, export, and modification event should be recorded, including user identity, timestamps (using U.S. Eastern Time with a UTC offset), and IP addresses. Security Information and Event Management (SIEM) tools can then analyze these logs to quickly identify unusual activities. Platforms like Censinet RiskOps™ enable continuous monitoring, ensuring visibility across the entire cross-border data ecosystem.
Finally, organizations must prepare for incidents involving international data transfers. Incident response plans should include specific actions for foreign cloud regions, international vendors, or offshore processors. Teams must be equipped to quickly revoke unauthorized access, rotate encryption keys, and comply with HIPAA breach notification requirements, as well as any relevant foreign regulations, within mandated timelines[8]. Regular penetration testing and red-team exercises simulating cross-border attack scenarios can validate the effectiveness of these safeguards.
These technical measures are key to reinforcing the broader compliance strategies discussed earlier.
sbb-itb-535baee
Maintaining Cross-Border Data Compliance
To effectively manage cross-border compliance, organizations must go beyond technical and procedural safeguards. This involves establishing strong governance structures, implementing ongoing monitoring, and preparing for potential breaches. With stricter federal rules now governing the export of bulk health data under the DOJ's Final Rule [5], structured oversight is more critical than ever.
Governance Policies and Accountability
Start by drafting or revising a cross-border data transfer policy. This policy should clearly outline which data categories can be transferred, identify approved destinations, and specify the conditions under which transfers are allowed. It should also detail the mechanisms for transfer, such as Standard Contractual Clauses, Binding Corporate Rules, or data localization requirements, while setting risk thresholds for various transfer scenarios [5][6].
To ensure proper oversight, create a cross-border data oversight committee. This committee should include representatives from privacy, security, legal, compliance, IT, clinical operations, and procurement teams. Their role would be to evaluate data transfers, approve offshore vendors, and manage risk mitigation. Assign a senior leader, such as a Chief Privacy Officer, CISO, or VP of Compliance, to take accountability. Use a RACI matrix to clearly define roles and responsibilities [5][4].
Integrate these cross-border data requirements into existing frameworks like HIPAA policies, information security standards, vendor management processes, and research governance systems. By embedding these requirements, all teams handling international data can stay informed of their obligations without needing to consult separate documents [5][3].
These steps provide a solid foundation for continuous compliance monitoring.
Continuous Monitoring and Benchmarking
Compliance isn’t a one-and-done task. Regularly update inventories and data flow maps for systems containing PHI, noting their hosting locations and identifying vendors with cross-border access. Conduct annual reviews - or more frequently if regulations change - to reassess data flows, transfer tools, and vendor risks [5][6].
Automated platforms like Censinet RiskOps™ can simplify this process. These tools support ongoing risk assessments, track vendor remediation efforts, and benchmark security and compliance maturity against a network of healthcare organizations and over 50,000 vendors.
Brian Sterud, CIO at Faith Regional Health, emphasized: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
Stay vigilant about regulatory and geopolitical changes, such as localization laws, adequacy decisions, sanctions, and updates to "countries of concern." Adjust your policies and contracts accordingly. Additionally, vendors should be required to notify you promptly about changes such as sub-processor updates, shifts in data storage locations, or security incidents. This allows your oversight committee to act quickly and appropriately [5][6][4].
By maintaining continuous monitoring, your organization not only ensures compliance but also stays prepared to handle incidents effectively.
Incident Preparedness for Cross-Border Breaches
Even with the best safeguards, breaches can still occur. Develop or update your incident response plan to address the complexities of cross-border breaches. This plan should include jurisdiction-specific breach notification timelines and account for restrictions on transferring forensic evidence or logs due to localization laws [2][6][4].
Vendor-origin breach playbooks are essential. These should outline contractual obligations for rapid notification, joint investigation protocols, and coordinated communication with regulators, affected individuals, and business partners. Conduct regular tabletop exercises to simulate cross-border breach scenarios involving offshore vendors. These drills help validate communication channels, clarify decision-making authority, and fine-tune notification workflows [5][2][4].
Research on cross-jurisdictional health data sharing shows that stakeholders value a strong response to breaches and clear accountability as much as they value prevention. A well-prepared incident response plan not only ensures compliance but also builds trust with patients, partners, and regulators when incidents arise [2].
Conclusion
Cross-border healthcare data transfers play a vital role in everyday operations, from offshore billing and cloud storage to international research collaborations and telehealth services. However, with the Department of Justice's Final Rule now limiting bulk health data exports to "countries of concern" and increasing regulatory scrutiny, healthcare organizations must elevate cross-border data governance to a core enterprise risk - far beyond just an IT responsibility [5]. Earlier discussions in this piece have highlighted the regulatory challenges and operational vulnerabilities tied to these data transfers.
To navigate these complexities, focus on three key areas: proactive governance, technical defenses, and ongoing monitoring. Integrate cross-border compliance requirements into vendor agreements and HIPAA policies, fortify your technical safeguards, and establish a dedicated oversight committee with clear accountability. Tools like Censinet RiskOps™ can simplify third-party risk assessments, track vendor remediation efforts, and help benchmark cybersecurity readiness.
While budget constraints and talent shortages may pose challenges, a phased approach can yield meaningful progress. Start by addressing the highest-risk vendors and the most sensitive data categories - such as genomic information, offshore analytics partners, or cloud service providers operating in restricted regions - and gradually expand your efforts.
Brian Sterud, CIO at Faith Regional Health, remarked: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters" [1].
Leverage this data to build a stronger case for additional investments.
Data breaches happen, but stakeholders will evaluate your response based on how quickly, transparently, and responsibly you act [2]. By implementing these preparedness measures alongside earlier strategies, organizations can create a unified defense against cross-border risks. Make sure vendor agreements include provisions for rapid breach notifications and collaborative investigation protocols.
Cross-border data compliance is about more than avoiding penalties - it's about safeguarding patients, maintaining trust, and fostering global collaboration that leads to better diagnoses, treatments, and outcomes [7]. With structured governance, advanced technical protections, and constant vigilance, healthcare organizations can confidently manage these risks and fully realize the benefits of international data sharing.
FAQs
What are the updated U.S. regulations for transferring healthcare data to high-risk countries?
Starting on December 12, 2025, the U.S. implemented stricter rules for exporting healthcare data to countries classified as high-risk. These regulations mandate healthcare organizations to follow more rigorous licensing procedures, carry out thorough risk assessments, and adhere to national security standards. The goal? To ensure sensitive health information remains secure and protected from potential misuse or cyber threats.
Healthcare organizations now face the critical responsibility of evaluating the risks tied to transferring patient data across borders. Full compliance with these guidelines is essential to uphold both data privacy and security.
What steps can healthcare organizations take to manage cross-border data transfers securely?
Healthcare organizations can take a proactive approach to secure cross-border data transfers by using advanced risk management tools such as Censinet RiskOps™. These platforms offer continuous risk assessments, detailed mapping of data flows, and automated monitoring to ensure compliance with regulations like HIPAA and GDPR.
To strengthen data security, organizations should focus on these key actions:
- Track and analyze data flows to uncover and address any weak points.
- Use automation tools to monitor risks in real-time and respond swiftly.
- Stay compliant with both international and local data protection laws.
By adopting these practices, healthcare providers can safeguard sensitive information, meet regulatory requirements, and enable secure international collaboration.
What are the key technical measures for securing cross-border healthcare data?
To keep healthcare data secure during cross-border transfers, start with encryption - both for data stored on systems (at rest) and while it's being transmitted. This ensures that sensitive information remains protected from unauthorized access. Pair this with access controls and multi-factor authentication to restrict access strictly to authorized individuals. When transferring data, rely on secure protocols like TLS to add an extra layer of protection.
It's also vital to implement continuous monitoring and maintain detailed audit logs. These tools help track data activity, making it easier to spot and address potential risks. Together, these steps uphold the confidentiality and integrity of healthcare data, even across borders.


