Cybersecurity Testing for 510(k) Submissions: Guide
Post Summary
Cybersecurity testing for 510(k) submissions ensures medical devices meet FDA requirements for secure design, risk management, and lifecycle cybersecurity.
It protects patient safety, prevents cyberattacks, ensures compliance with FDA regulations, and avoids delays or rejections during the approval process.
Requirements include risk management, vulnerability testing, penetration testing, a Software Bill of Materials (SBOM), and postmarket cybersecurity plans.
Challenges include managing complex documentation, ensuring compliance with FDA guidelines, and addressing vulnerabilities in connected devices.
Best practices include adopting a Secure Product Development Framework (SPDF), conducting threat modeling, and performing comprehensive testing like penetration and fuzz testing.
Organizations can streamline the process by using tools like Censinet RiskOps™, automating vulnerability tracking, and maintaining organized documentation.
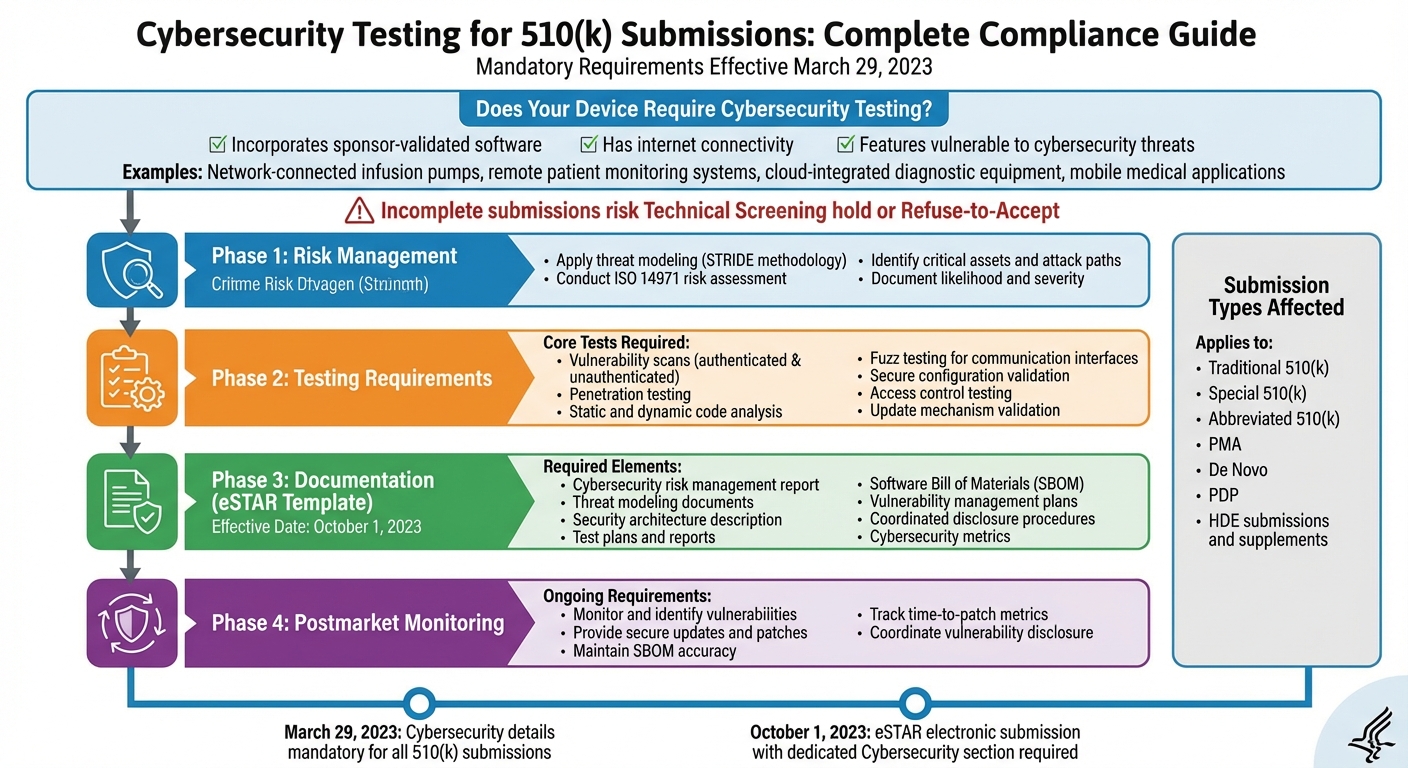
Cybersecurity is now a mandatory part of 510(k) submissions for medical devices. If your device connects to the internet, uses software, and could face cyber risks, you must meet FDA cybersecurity standards. Effective March 29, 2023, this includes detailed testing, risk management, and documentation to avoid delays or rejection. Key requirements include:
- Cybersecurity Risk Management: Identify risks using threat modeling (e.g., STRIDE) and ISO 14971 standards.
- Testing: Perform vulnerability scans, penetration tests, code analysis, and secure update validation.
- Documentation: Submit a Software Bill of Materials (SBOM), test results, and risk controls in the FDA’s eSTAR template.
- Postmarket Plans: Monitor vulnerabilities, provide secure updates, and maintain cybersecurity over the device's lifecycle.
Platforms like Censinet RiskOps™ can simplify this process by organizing evidence, automating vulnerability tracking, and ensuring compliance with FDA guidelines. Addressing cybersecurity early reduces risks, ensures patient safety, and streamlines regulatory approval.
FDA 510(k) Cybersecurity Testing Requirements and Compliance Workflow
FDA Regulatory Requirements for Cybersecurity Testing in 510(k) Submissions
FDA Definition of Cyber Devices and When Testing Is Required
Under Section 524B(c) of the FD&C Act, a "cyber device" is defined as a device that incorporates sponsor-validated software, has internet connectivity, and possesses features that could be vulnerable to cybersecurity threats [2][7].
Examples of these devices include network-connected infusion pumps, remote patient monitoring systems, cloud-integrated diagnostic equipment, and mobile medical applications. However, some devices - like those relying solely on local wired connections or Bluetooth - may require further evaluation to determine if they meet the "internet connectivity" standard [2][4][5].
As of March 29, 2023, all 510(k) submissions for cyber devices must include comprehensive cybersecurity details [2]. This applies to all types of submissions, including Traditional, Special, and Abbreviated 510(k)s, as well as PMA, De Novo, PDP, and HDE submissions and supplements [2][4]. If your device meets the criteria of a cyber device, your submission must include information on cybersecurity risk management, testing evidence, and lifecycle plans. Submissions lacking this information risk being placed on a Technical Screening hold or rejected under Refuse-to-Accept policies [2][3].
This framework outlines the foundational requirements, setting the stage for the specific testing and documentation expectations discussed below.
FDA Cybersecurity Premarket Guidance Overview
In September 2023, the FDA released its final guidance titled "Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions" [7][10]. This guidance emphasizes the importance of building devices with secure-by-design and secure-by-default principles, requiring manufacturers to integrate cybersecurity into their Quality System Regulation (21 CFR Part 820) processes, particularly in design controls and risk management [7][10].
Manufacturers are expected to adopt a Secure Product Development Framework (SPDF) that incorporates secure design principles like least privilege, defense in depth, and secure defaults. Testing requirements include vulnerability scanning, penetration testing, exploitation of known vulnerabilities, static and dynamic code analysis, fuzz testing for communication interfaces, and verification of controls like authentication, authorization, and encryption [4][7][10].
Section 524B(b) mandates that cyber devices demonstrate three key capabilities:
- A plan to monitor, identify, and address postmarket cybersecurity vulnerabilities and exploits.
- A plan to ensure cybersecure device operation, including coordinated vulnerability disclosure processes.
- Provision of a Software Bill of Materials (SBOM) that lists all commercial, open-source, and off-the-shelf software components [2][4].
Manufacturers must also prove that their devices can deliver authenticated, integrity-protected updates and patches promptly, addressing newly discovered vulnerabilities after market release [2][4].
These guidelines emphasize both premarket and postmarket cybersecurity responsibilities, with precise documentation requirements outlined in the eSTAR format.
Cybersecurity Documentation in the eSTAR Template
Starting October 1, 2023, the FDA requires most 510(k) submissions to be filed electronically using eSTAR, which includes a dedicated Cybersecurity section [2][5]. Accurate and complete answers, along with the necessary attachments, are essential for passing Technical Screening [2].
The cybersecurity section of eSTAR requires the following documentation:
- A cybersecurity risk management report.
- Threat modeling documents, such as attack trees and data flow diagrams.
- A description of the security architecture.
- Test plans and reports for cybersecurity controls.
- SBOM(s) detailing all software components.
- Plans for vulnerability management and updates.
- Coordinated vulnerability disclosure procedures.
- Cybersecurity metrics, such as the percentage of vulnerabilities patched and time-to-patch [5][6][9].
The FDA expects test results to be detailed enough for reviewers to understand the scope, methods, tools, configurations, acceptance criteria, and outcomes. This includes how identified vulnerabilities or nonconformances were addressed [4][7]. While summaries can be included in the main submission, appendices should contain full reports for critical tests, such as penetration testing, fuzz testing, and update mechanism validation. These should clearly map to specific risks and controls [4].
For SBOMs, manufacturers should provide comprehensive listings that include version numbers and supplier details. Additionally, they must explain how SBOMs will be maintained after market release and attach machine-readable SBOM files (e.g., SPDX or CycloneDX) to the submission [2][4][5].
Planning Your Cybersecurity Testing Strategy for 510(k) Submissions
Applying Threat Modeling and Risk Assessment
The foundation of a solid cybersecurity testing strategy lies in combining threat modeling with ISO 14971 risk management. Techniques like STRIDE (Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege) are particularly useful for pinpointing potential cyber attack paths targeting your device's critical assets - such as patient health information, control signals, firmware, cloud APIs, and wireless interfaces [3][6].
Once threats are identified, incorporate them into your ISO 14971 risk management process to evaluate both the likelihood of exploitation and the potential severity of clinical harm. For instance, scenarios like unauthorized remote adjustments to therapy parameters or ransomware attacks on life-sustaining devices are high-risk and require priority testing, including penetration testing, network hardening verification, and resilience assessments. Lower-risk concerns, on the other hand, may only call for simpler measures such as configuration checks or secure coding reviews [3][11].
Choosing the Right Cybersecurity Tests
The tests you choose should align closely with your device's architecture and its clinical use case [11][6]. For example, a networked implant programmer connected to a hospital LAN would typically need independent penetration testing and network fuzzing. Meanwhile, a stand-alone, non-networked accessory might focus more on secure boot validation and static code analysis. Regardless of the device type, the FDA expects all cybersecurity testing to include:
- Secure configuration and hardening
- Vulnerability scans for included software and open-source components
- Validation of the Software Bill of Materials (SBOM) completeness and vulnerability management
- Verification of logging, monitoring, and update mechanisms [5][11]
It's essential to clearly document your test selection criteria, linking the device's security risk level and connectivity type to the testing methods and depth you’ve chosen [9][6]. This ensures a clear rationale for your approach and demonstrates alignment with regulatory expectations.
Building Testing into Your Secure Product Development Framework
The FDA’s premarket cybersecurity guidance stresses the importance of embedding security within your Quality System and development lifecycle, rather than treating it as an afterthought [7][8]. A well-structured Secure Product Development Framework (SPDF) incorporates security activities at every stage of development.
- Concept phase: Conduct threat modeling and establish initial security and performance requirements.
- Design phase: Perform architecture reviews and security design evaluations [6][7].
- Implementation phase: Carry out secure coding practices, static analysis, and component-level unit testing with a focus on security.
- Integration and system testing: Include vulnerability scanning, dynamic testing, fuzzing of critical interfaces, and preliminary penetration testing.
- Pre-design freeze: Conduct formal penetration testing, fail-safe and resilience testing, and full system hardening verification [3][6].
Throughout this process, maintain thorough documentation of plans, procedures, test logs, and mitigations in a traceable repository. By the time you’re ready to submit your 510(k), your cybersecurity testing documentation, risk analysis, and security architecture description should be well-organized and prepared for review, aligning with eSTAR sections [5][12]. This proactive approach ensures you’re not scrambling to gather evidence at the last minute.
Conducting and Documenting Cybersecurity Tests for 510(k) Devices
Performing Core Cybersecurity Tests
Once your testing strategy is ready, focus on critical areas like configuration validation, access control testing, vulnerability assessments, and penetration testing. These tests should align with your device's risk level and clinical use case [4][7]. Start with configuration validation: confirm that default settings are secure (e.g., enforcing strong passwords, enabling logging, and disabling remote access unless absolutely necessary). Ensure that users or installers cannot bypass these security settings [4][7]. Access control testing should then verify the proper implementation of principles like least privilege, role-based access, session timeouts, and robust authentication across all interfaces, including clinical UIs, service ports, APIs, and cloud dashboards [4][6].
For vulnerability assessments, perform both authenticated and unauthenticated scans of all exposed services and components, cross-referencing findings with known CVEs [4][5]. Penetration testing should focus on clinically relevant attack scenarios, such as tampering with alarms, altering therapy settings, or disrupting monitoring functions, and confirm that these exploits do not endanger patient safety [3][4]. High-risk devices, like implanted systems, life-sustaining equipment, or devices integrated into hospital networks, require more extensive and frequent testing [4][7]. Beyond these tests, thoroughly examine all software components for vulnerabilities, keeping them tracked with an up-to-date SBOM.
Testing Software Components and Validating SBOMs
Your Software Bill of Materials (SBOM) should include every software component - whether proprietary code, open-source libraries, commercial off-the-shelf software, firmware, operating systems, or containers. It should detail the component name, version, supplier, dependency relationships, and licenses [5][6]. Use tools in your build pipeline to generate SBOMs by scanning source code, binaries, containers, and package managers. Stick to standard formats like SPDX or CycloneDX to ensure accuracy [5].
After generating the SBOM, automate vulnerability scans to cross-check components against public databases like the NVD and vendor advisories. Prioritize findings based on their exploitability and potential impact on device performance and safety [4][5]. For any identified vulnerabilities - such as exploitable remote code execution in a network-exposed component - document whether they are resolved, mitigated (e.g., through network segmentation or input filtering), or accepted, along with the rationale and plans for ongoing monitoring [4][7].
Additionally, test the secure update mechanisms to ensure updates are authenticated, protected for integrity, and resilient across all environments. This includes verifying cryptographic protections (e.g., signing, certificate management, rollback protection), testing update delivery methods (USB, local network, cloud), and evaluating failure handling (e.g., power loss during updates or partial downloads). These tests should confirm that devices can safely revert or transition to a secure state if an update fails or is tampered with [4][6][7].
Creating Cybersecurity Test Documentation
After completing the testing, document all results in alignment with the eSTAR cybersecurity requirements. Structure the documentation to clearly map each risk from your threat model to its mitigations and corresponding test results, demonstrating that any remaining risks are acceptable [7][10]. The FDA requires every test result to directly trace back to specific risk controls. For each test, include details such as the objective, scope, environment, procedures (with tool versions), criteria, results, and any deviations [10]. A requirements-to-test matrix can be particularly useful, linking security requirements and risk controls to specific test cases and outcomes, providing clear traceability for FDA reviewers [10].
Your test reports should explicitly connect results to risk controls, showing that residual risks fall within acceptable limits for the 510(k) submission [7][10]. For instance, if your threat model identifies unauthorized remote access as a high-risk scenario, the documentation should describe the penetration test simulating such an attack, the controls (e.g., multi-factor authentication, network segmentation, logging) that prevented it, and a risk analysis justifying the acceptability of the remaining risk [4][7]. Supporting evidence might include a summarized SBOM, a vulnerability assessment report categorizing findings by severity and risk, examples of remediation decisions, and references to ongoing postmarket monitoring processes [5][7].
sbb-itb-535baee
Using Cybersecurity Platforms to Manage Testing and Evidence
Consolidating Cybersecurity Testing Evidence
When evidence is scattered across emails, local drives, and spreadsheets, it can lead to incomplete records, version control issues, and delays in responding to the FDA. A dedicated cybersecurity platform solves this by centralizing test plans, penetration test results, vulnerability scans, risk assessments, SBOMs (Software Bill of Materials), and update procedures into a single, auditable system. This streamlined approach meets FDA expectations for clear and organized documentation throughout the lifecycle of a medical device.
Platforms like Censinet RiskOps™ are designed to help healthcare organizations and medical device manufacturers manage cybersecurity testing evidence efficiently. These systems consolidate key artifacts - such as test results, SBOMs, and risk assessments - into a cloud-based repository. Each device record serves as the single source of truth, with cybersecurity documentation mapped directly to FDA guidance and eSTAR requirements. Features like role-based access and version control ensure that modifications are carefully managed, preserving an audit trail and reducing the risk of missing critical elements in an eSTAR submission. Such omissions could otherwise result in Refuse-to-Accept or technical screening holds.
For SBOM management, a robust platform can centralize all component data - whether it’s commercial, open-source, or proprietary software. It can also link these components to their vendors and automate regular checks against vulnerability databases, ensuring that the information stays current and actionable.
Terry Grogan, CISO at Tower Health, shared how Censinet RiskOps improved efficiency: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." [1]
This example highlights how centralized platforms not only streamline evidence management but also support FDA expectations for ongoing vulnerability monitoring after devices hit the market. By centralizing evidence, teams can also collaborate more effectively across departments.
Coordinating Across Regulatory, Engineering, and Risk Teams
When engineering, regulatory, and risk teams rely on fragmented tools, it slows down 510(k) submissions and increases the likelihood of documentation gaps. A unified cybersecurity platform eliminates these inefficiencies by providing shared templates aligned with FDA guidelines, assigning and tracking tasks (like completing a STRIDE threat model or updating an SBOM after a software release), and maintaining a single, traceable risk register for each device. This risk register documents likelihood, impact, and mitigation strategies in one place.
Features like integrated commenting, workflows, and dashboards make collaboration seamless. Regulatory staff can flag missing evidence, engineers can upload raw test results, and risk teams can document decisions on residual risks - all within the same system.
James Case, VP & CISO at Baptist Health, emphasized the benefits: "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." [1]
By unifying documentation and processes, organizations can reduce rework and respond to FDA queries faster. Automated checks within the platform can flag missing or outdated elements, reducing the risk of technical screening holds. This approach not only speeds up 510(k) preparation but also supports ongoing compliance with postmarket cybersecurity requirements.
Supporting Postmarket Cybersecurity Requirements
After a device is on the market, the FDA mandates continuous vulnerability monitoring under its cybersecurity guidance and section 524B. To meet these requirements, platforms must maintain accurate asset inventories, track vulnerabilities and risk assessments, manage remediation timelines, and document communications such as safety notices and advisories.
A robust platform should also facilitate periodic security testing and compile results over time, creating a comprehensive evidence base that demonstrates ongoing cybersecurity management. For coordinated vulnerability disclosure, the platform can centralize external reports from researchers, healthcare organizations, or customers, while tracking triage, validation, and remediation steps. This ensures transparency and accountability in addressing vulnerabilities.
Censinet RiskOps™ is already widely used by healthcare organizations for enterprise and third-party risk assessments. Its capabilities extend to fostering two-way communication between manufacturers and healthcare organizations. Manufacturers can share structured cybersecurity and risk data, while healthcare providers can offer feedback, including incident reports, to help prioritize fixes and document real-world impacts. Time-based analytics - such as the average time to remediate high-severity vulnerabilities or patch adoption rates - can further demonstrate control effectiveness and responsiveness, aligning with FDA expectations for postmarket cybersecurity management.
Conclusion
Cybersecurity testing has become a non-negotiable requirement for 510(k) submissions under FDA regulations. Since March 29, 2023, manufacturers of cyber devices must provide structured, evidence-based demonstrations of cybersecurity rather than relying on general assurances. These updates reflect the changing regulatory environment and highlight the importance of implementing strong and continuous cybersecurity measures.
Achieving regulatory compliance begins with embedding cybersecurity into your product development process from the outset. As outlined earlier, this includes integrating threat modeling with ISO 14971 and NIST guidelines, employing a risk-based testing approach with vulnerability scans, penetration tests, authentication checks, and update mechanisms, and ensuring clear traceability between identified risks, implemented controls, and test outcomes. Your eSTAR submission must present a comprehensive cybersecurity package, including risk assessments, test protocols and reports, a validated SBOM, architectural documentation, and postmarket plans for monitoring vulnerabilities and coordinated disclosure.
Obtaining 510(k) clearance is only the beginning. Manufacturers are expected to maintain cybersecurity throughout the device's lifecycle, which means staying vigilant about new vulnerabilities, releasing timely patches, and updating risk assessments as threats evolve. This ongoing effort ties directly into the robust documentation and testing strategies discussed earlier. By aligning premarket testing with postmarket processes, manufacturers can create a seamless framework for managing security over time while building trust with users.
Centralized tools like Censinet RiskOps™ can simplify this process by consolidating test evidence, risk assessments, and SBOMs into a single auditable system. For organizations in healthcare, Censinet RiskOps™ offers additional benefits, such as managing third-party risks, benchmarking cybersecurity, and fostering collaboration around medical devices and systems that handle sensitive patient data. These capabilities strengthen overall security, ensuring patient safety in real-world clinical settings.
FAQs
What are the main cybersecurity testing requirements for 510(k) submissions?
To meet cybersecurity testing requirements for 510(k) submissions, manufacturers need to focus on three key areas: vulnerability assessments, validation of cybersecurity controls, and thorough documentation that adheres to FDA guidelines. Testing should evaluate the security features of medical devices, assess potential risks through threat modeling, and detail effective strategies to mitigate those risks.
These measures are critical for protecting patient data, ensuring device functionality remains uncompromised, and meeting regulatory standards. By performing rigorous testing and validation, manufacturers can reduce cybersecurity risks and streamline the 510(k) submission process.
What steps can manufacturers take to meet FDA cybersecurity requirements for 510(k) submissions?
To align with FDA cybersecurity requirements, manufacturers should take a forward-thinking approach to managing risks and conducting cybersecurity testing. This means performing ongoing risk assessments, promptly addressing vulnerabilities, and implementing strong validation processes to safeguard their devices.
Equally important is maintaining detailed documentation of all cybersecurity testing and validation efforts. This not only shows adherence to FDA guidelines but also simplifies the 510(k) submission process. Using cybersecurity platforms tailored for healthcare can further streamline risk management efforts and help ensure compliance is both thorough and efficient.
What is the importance of a Software Bill of Materials (SBOM) in cybersecurity testing for 510(k) submissions?
A Software Bill of Materials (SBOM) plays a critical role in cybersecurity testing by offering a comprehensive list of all software components and dependencies within a medical device or application. This level of detail allows for better visibility, making it easier to spot known vulnerabilities, verify the integrity of software elements, and meet security standards.
With an SBOM in hand, organizations can take a proactive approach to identifying risks, resolving potential security issues, and simplifying the 510(k) submission process. The result? Enhanced patient safety and a smoother path to regulatory compliance.
Related Blog Posts
Key Points:
What is cybersecurity testing for 510(k) submissions?
Definition: Cybersecurity testing for 510(k) submissions involves evaluating medical devices for vulnerabilities, ensuring secure design, and meeting FDA requirements for cybersecurity. This includes risk management, testing, and lifecycle plans to protect patient safety and device integrity.
Why is cybersecurity important for 510(k) submissions?
Importance:
- Protects patient safety by preventing cyberattacks on medical devices.
- Ensures compliance with FDA regulations, avoiding delays or rejections.
- Reduces risks of data breaches and unauthorized access.
- Builds trust with regulators, healthcare providers, and patients.
What are the key FDA requirements for cybersecurity in 510(k) submissions?
Requirements:
- Risk Management: Use threat modeling (e.g., STRIDE) and ISO 14971 standards to identify and mitigate risks.
- Testing: Perform vulnerability scans, penetration testing, fuzz testing, and secure update validation.
- Documentation: Submit a Software Bill of Materials (SBOM), test results, and risk controls in the FDA’s eSTAR template.
- Postmarket Plans: Include plans for vulnerability monitoring, secure updates, and coordinated vulnerability disclosure.
What are the challenges of cybersecurity testing for 510(k) submissions?
Challenges:
- Managing complex documentation requirements, including SBOMs and test reports.
- Ensuring compliance with evolving FDA guidelines and cybersecurity standards.
- Addressing vulnerabilities in connected devices with diverse architectures.
- Balancing security with usability and performance requirements.
What are the best practices for cybersecurity testing in 510(k) submissions?
Best Practices:
- Adopt a Secure Product Development Framework (SPDF) to integrate security into the device lifecycle.
- Conduct threat modeling to identify potential attack paths and prioritize risks.
- Perform comprehensive testing, including penetration testing, fuzz testing, and vulnerability scans.
- Maintain detailed documentation, including test plans, results, and mitigation strategies.
- Use tools like Censinet RiskOps™ to automate vulnerability tracking and streamline compliance.
How can organizations streamline cybersecurity testing for 510(k) submissions?
Streamlining Strategies:
- Use platforms like Censinet RiskOps™ to organize evidence, automate vulnerability tracking, and ensure compliance.
- Maintain a centralized repository for documentation, including SBOMs, test logs, and risk assessments.
- Train staff on FDA cybersecurity requirements and testing methodologies.
- Collaborate with cybersecurity experts to address vulnerabilities and prepare for FDA reviews.


