Emergency Medical Services Vendor Risk: Mobile Healthcare and Critical Response Systems
Post Summary
Emergency medical services (EMS) heavily rely on third-party vendors for critical systems like dispatch platforms, patient care records, and telemedicine tools. However, vendor-related cyberattacks can disrupt life-saving operations, exposing patient data, delaying ambulances, and causing system outages.
Key points:
- Cyber Threats: Ransomware attacks on vendors can lead to 22+ days of downtime, affecting EMS services and patient safety.
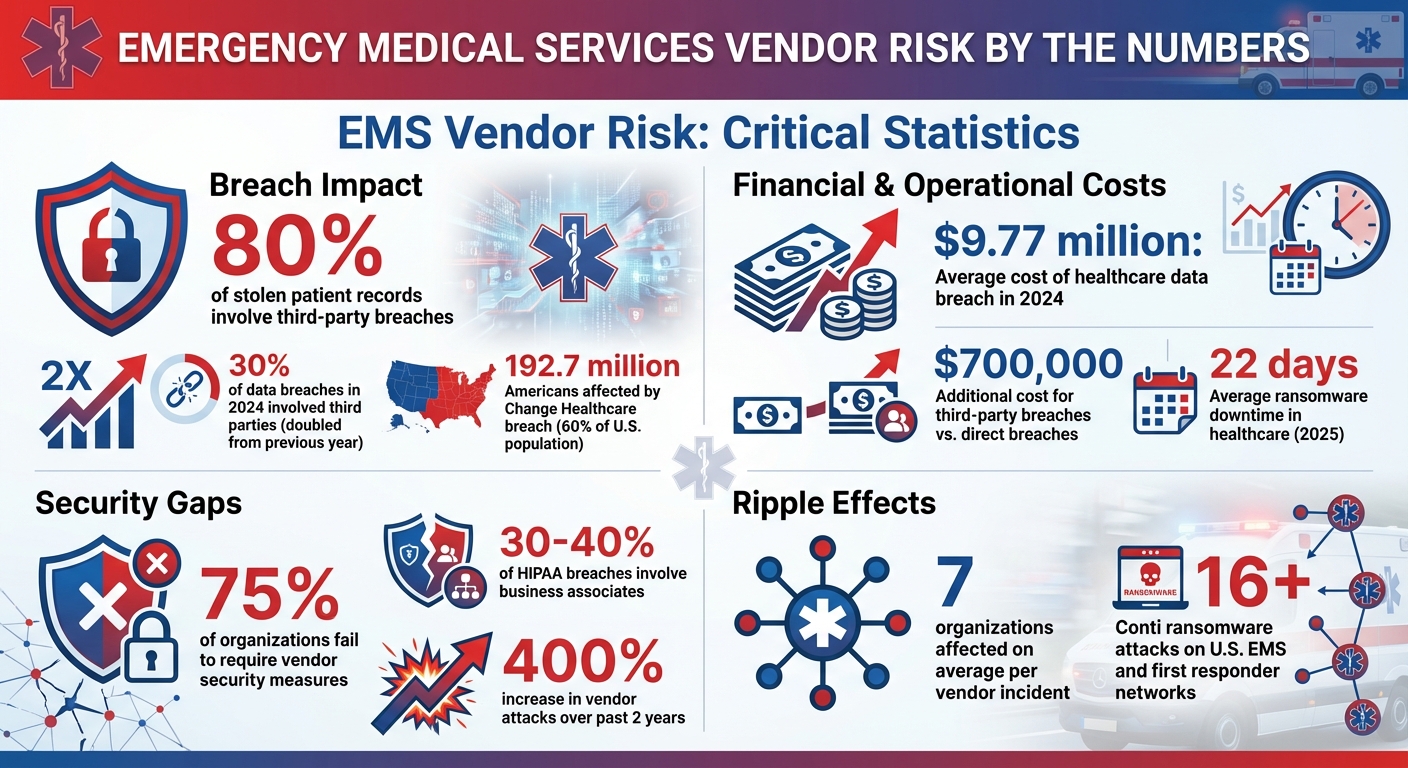
- Vendor Risks: 80% of stolen patient records involve third-party breaches, with limited visibility into vendors' security practices.
- Solutions: Classify vendors by risk, conduct thorough assessments, and set strict security requirements in contracts.
- Continuity Plans: Use downtime playbooks, redundant systems, and drills to maintain services during outages.
- Automation: Platforms like Censinet RiskOps™ help monitor vendor risks efficiently.
EMS agencies must prioritize vendor risk management to ensure uninterrupted operations and safeguard patient care.
EMS Vendor Risk Statistics: Third-Party Breach Impact and Costs
Cybersecurity Risks in EMS Vendor Ecosystems
The ecosystem of vendors supporting EMS operations faces three major cybersecurity challenges that could disrupt emergency response systems entirely. These challenges arise from the critical role vendors play - they often have extensive access to essential systems, manage sensitive patient data, and frequently operate with weaker security measures compared to the healthcare organizations they serve. Addressing these risks requires a focused approach to managing vendor security.
Ransomware and Data Extortion
Ransomware attackers have grown increasingly sophisticated, even creating specialized healthcare-targeted teams. They focus on critical vendor systems like CAD platforms, ePCR tools, and billing software, aiming to cause maximum disruption. By encrypting or stealing protected health information (PHI), these groups exploit vulnerabilities to pressure both vendors and the EMS agencies that rely on them. Often, these attacks are timed to coincide with periods when clinical operations are most vulnerable [1].
System Downtime and Continuity Risks
When vendor systems fail, the ripple effects are severe. Dispatch centers struggle to route ambulances effectively, paramedics lose access to patient histories and telemetry data, and telehealth services grind to a halt. These outages force EMS teams to revert to manual processes, leading to slower response times and lower care quality. In fact, operational risk has become the top concern in third-party risk management, as highlighted by an EY survey of 500 executives [5].
Third- and Fourth-Party Risk Concentration
EMS organizations also face risks from the interconnected nature of their vendor networks. Many vendors rely on the same cloud and SaaS providers, creating what’s known as "Nth party risk." This means that a breach or outage several layers down the supply chain can have a cascading effect across EMS networks [6][7]. For example, breaches involving third parties are estimated to cost $700,000 more on average than direct breaches [7]. Shockingly, nearly 75% of organizations fail to require their vendors to implement proper security measures [7]. This over-dependence on a small number of providers creates systemic vulnerabilities, leaving emergency response systems at risk of widespread failures [5].
How to Build a Vendor Management Framework for EMS
Creating a solid vendor management framework for EMS organizations starts with recognizing that not all vendors carry the same level of risk. In 2024, approximately 30% of data breaches involved third parties - double the rate from the previous year [8]. For EMS agencies, a structured approach to managing vendors is crucial for mitigating risks tied to critical operations.
Classify Vendors by Criticality
In emergency response, some vendors are far more critical than others. To prioritize effectively, categorize vendors into risk tiers by evaluating factors like data sensitivity, service importance, and the depth of system integration. For example, third-party billing companies and ePCR vendors often manage a significant portion of an EMS agency’s records, placing them in the highest-risk category [10]. Similarly, NG911 systems, dispatch platforms, and mobile telemetry services demand extra scrutiny because their failure directly impacts life-saving operations.
During the onboarding process, assess each vendor’s level of access and the potential operational impact of a breach [8]. The FBI recently reported at least 16 Conti ransomware attacks targeting U.S. healthcare and first responder networks, including EMS, law enforcement, and 9-1-1 dispatch centers [9]. Vendors supporting these critical functions need ongoing monitoring. On the other hand, vendors managing less essential tasks, like appointment scheduling, may require less intensive oversight [1].
Conduct Thorough Risk Assessments
A detailed risk assessment is key to evaluating a vendor’s cybersecurity readiness. Focus on their resilience to ransomware, compliance with HIPAA regulations, and overall incident response capabilities. Data shows that third-party breaches are increasingly common [11]. Ask vendors about their risk analysis processes, the specific measures they have in place to prevent cyberattacks, and their protocols for reporting "Cyber Events" - including how quickly they notify you [10].
Pay close attention to their cybersecurity testing, backup restoration processes, and incident response plans. With 80% of stolen patient records now linked to third-party breaches rather than direct attacks on hospitals [1], these evaluations are critical for safeguarding patient data and ensuring uninterrupted emergency services. Once risks are identified, it’s essential to address them through contractual agreements.
Set Security Requirements in Vendor Contracts
Vendor contracts should clearly outline security expectations, including baseline controls, incident notification timelines, and recovery objectives tailored to EMS operations. Business associates contribute to 30%-40% of HIPAA breaches [12], and the average cost of a healthcare data breach reached $9.77 million in 2024 [13]. These figures underscore the importance of robust contractual protections.
Contracts should include technical safeguards, strict SLAs, and clearly defined recovery objectives that reflect the critical nature of EMS operations [2][10][11][13]. Recovery time objectives (RTOs) and recovery point objectives (RPOs) must align with the urgency of EMS services, ensuring vendors can restore systems quickly to maintain patient care standards.
sbb-itb-535baee
How to Maintain EMS Operations During Vendor Outages
When vendors experience system failures, EMS agencies must keep their critical services running. In 2025, the average downtime caused by ransomware attacks in healthcare reached 22 days[1], with some facilities taking months to fully recover. Given the life-saving nature of emergency services, it's crucial for agencies to have solid plans to maintain dispatch, communication, and patient documentation - even when digital systems are down. Here’s how to stay operational during vendor outages.
Create Downtime Playbooks and Run Drills
Develop detailed downtime playbooks that include essential contact lists, notification procedures, and recovery steps to limit disruption and damage[2][14]. Clearly define roles, establish escalation pathways, and conduct joint drills with vendors to test how well your teams can coordinate across organizations. On average, vendor-related incidents affect seven different organizations[1], making clear communication protocols a must.
Train frontline staff on fallback solutions like paper-based protocols and offline communication tools. Regularly run drills to make sure everyone knows how to use these alternatives[4].
Peter Rizzo, IT manager at MedStar Mobile Healthcare, stresses the importance of practice: "Remember the human factors and treat training and repetition of cybersecurity just like you do safe driving!"[3]
Both discussion-based and hands-on drills are vital for spotting weaknesses and ensuring staff are ready to step into their roles during an outage[1][4].
Design Redundant and Resilient Systems
Beyond immediate response plans, building resilient systems is key to maintaining continuity. Use robust off-site data backups and regularly test your ability to restore them[2][14]. Offline backups are especially important to guard against ransomware attacks[2]. Network segmentation can also help contain the spread of a breach, preventing a single vendor issue from disrupting your entire operation.
The ripple effects of a single vendor breach, like the Change Healthcare incident, can impact large networks[1][15]. By adding redundant connectivity and offline communication options, you reduce dependence on any one system, ensuring critical functions stay up and running.
Coordinate with Regional and Federal Agencies
Strengthening EMS operations also means collaborating with external partners. Build relationships with organizations like HHS, CISA, and state EMS offices ahead of time. These partnerships can provide valuable resources, including threat intelligence, technical support, and mutual aid agreements, which are especially helpful during vendor-related disruptions. Incorporate both internal cyber incidents and external community attacks into your emergency response plans[4].
Nitin Natarajan, former Deputy Director of CISA, advises: "These plans should be routinely exercised (both discussion based and operational exercises) and updated to reflect changes to your operations"[4].
Working with regional and federal partners ensures you’re not tackling vendor outages alone. Shared resources and coordinated efforts can fill critical gaps when your primary systems go offline.
How to Monitor and Improve Vendor Risk Management
Vendor risk management is not a one-and-done task - it requires constant vigilance and improvement to stay ahead of emerging threats. With 80% of healthcare breaches tied to third-party vendors [1] and a staggering 400% increase in vendor attacks over the past two years [16], EMS organizations need tools that can keep pace. Automation plays a crucial role in ensuring effective oversight while adapting to these challenges.
Automate Vendor Risk Monitoring
Automation is key to maintaining seamless EMS operations while managing vendor risks. Relying on manual assessments is time-consuming and often inadequate for addressing the speed and complexity of modern cyber threats. Censinet RiskOps™ simplifies this process by automating workflows, enabling continuous monitoring, and using AI to validate evidence and visualize risks.
With Censinet AI, vendors can complete security questionnaires in seconds, quickly summarize documentation, and even identify fourth-party risk exposures. The platform generates risk summary reports from all assessment data, ensuring a comprehensive view. Additionally, configurable rules allow organizations to maintain oversight while reducing risk more efficiently. By integrating cyber threat intelligence and aligning controls with frameworks like ISO 27001, NIST, and GDPR, the platform provides a full-spectrum view of vendor risk across your network.
Share Risk Data Through Collaborative Networks
The ripple effects of vendor breaches can be massive - just consider the Change Healthcare breach, which impacted 192.7 million Americans, roughly 60% of the U.S. population [1]. Sharing threat intelligence and best practices is critical for mitigating these widespread risks.
Establish security information-sharing agreements to facilitate rapid exchange of threat intelligence when vendors detect potential compromises [1]. Centralizing this information among decision-makers across various healthcare organizations allows for better identification of red flags, whether they involve regulatory updates, vendor performance issues, or new threats [16]. By pooling resources and knowledge, EMS agencies can reduce redundant efforts and build stronger defenses against shared vulnerabilities.
This collaborative approach not only strengthens individual organizations but also fosters resilience across the entire healthcare ecosystem.
Track Success with Key Metrics
Tracking key metrics is essential for identifying weaknesses and ensuring accountability in your vendor risk management program. Focus on KPIs like inventory completeness, review frequency, and executive engagement [17]. These metrics provide actionable insights into how well your program is functioning and help justify investments in resources.
"Measure what matters. Track metrics like inventory completeness, review frequency, and executive engagement. Use these KPIs to drive continuous improvement and accountability." - American Hospital Association (AHA) Knowledge Exchange [17]
FAQs
What’s the best way for EMS agencies to assess and categorize vendor risks?
Emergency medical services (EMS) agencies can evaluate and categorize vendor risks by conducting detailed assessments that focus on key areas like cybersecurity practices, data protection protocols, regulatory compliance, and system reliability. This evaluation helps pinpoint which vendors may pose the greatest threat to operations or sensitive information.
Adopting a structured approach, such as quantitative risk analysis, allows agencies to measure both the likelihood and potential impact of these risks. Based on this analysis, vendors can be grouped into tiers according to their importance to EMS operations. To keep risk assessments accurate, agencies should implement regular monitoring and periodic audits. This ensures they can address potential issues early and maintain smooth, uninterrupted operations.
What are the key steps for developing effective downtime playbooks for EMS operations?
Creating a dependable downtime playbook for EMS operations requires thoughtful planning and consistent upkeep. Start by crafting detailed, step-by-step procedures that staff can follow during system outages. Make sure to establish clear communication protocols so that everyone - team members and stakeholders alike - stays informed without delay. Building in system redundancies is another key step to help reduce disruptions and speed up recovery.
It’s also important to run regular drills and simulations to evaluate how well the playbook works and to familiarize staff with emergency protocols. After any incident, take time to review and refine the playbook, addressing any weaknesses and accounting for evolving risks. A well-prepared playbook keeps operations running as smoothly as possible, even in the face of unexpected challenges.
How does automation enhance vendor risk management for emergency medical services?
Automation plays a key role in vendor risk management for emergency medical services by enabling real-time monitoring of vendor cybersecurity practices, streamlining risk assessments, and simplifying compliance tasks. This not only cuts down on human error but also boosts efficiency and precision.
With automation in place, organizations can react faster to potential threats, maintain system reliability, and protect sensitive healthcare data. These features are essential for ensuring smooth operations in high-stakes, life-saving scenarios.


