Emerging Privacy Laws: Audit Challenges Explained
Post Summary
Healthcare organizations face mounting challenges in 2025 as privacy regulations evolve at both federal and state levels. Here's what you need to know:
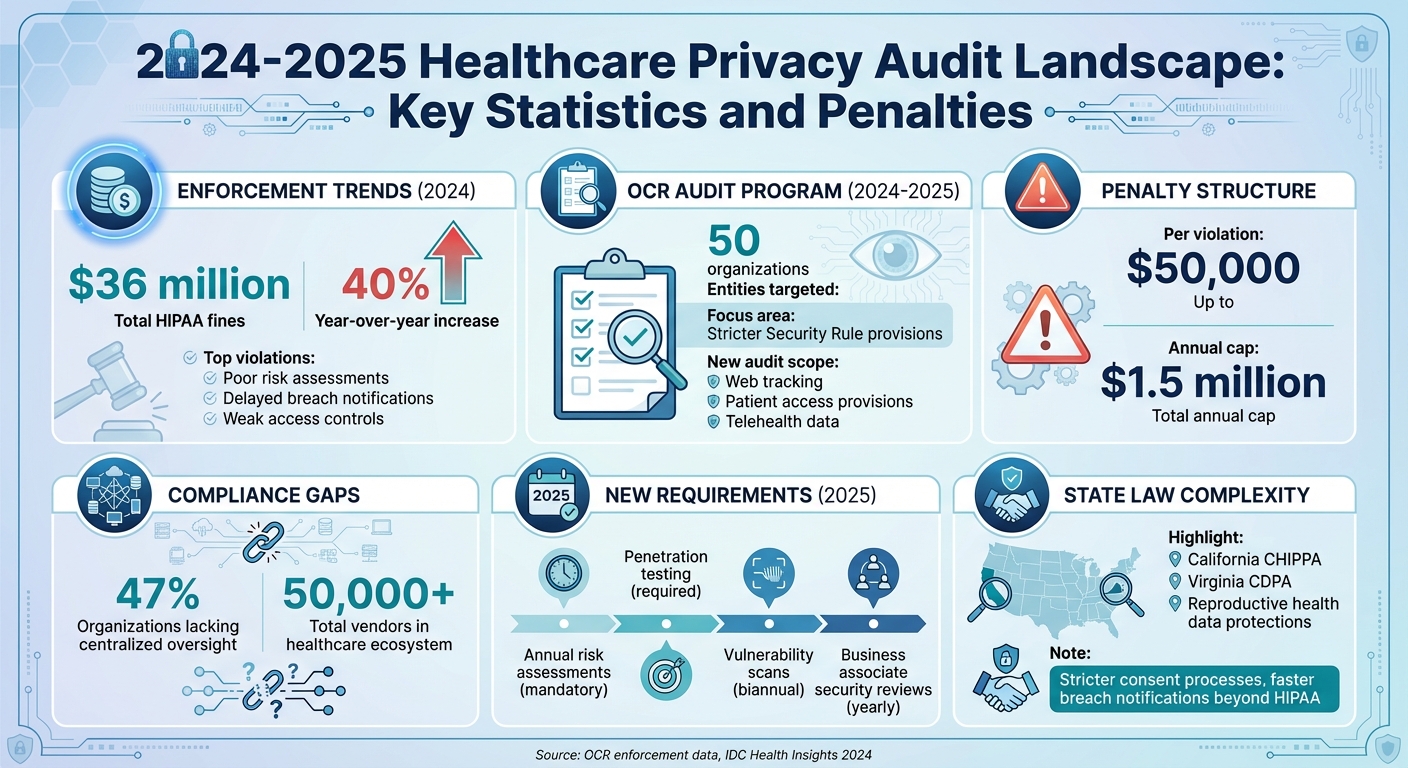
- OCR HIPAA Audits Are Back: The Office for Civil Rights (OCR) resumed its HIPAA Audit Program, targeting 50 entities and focusing on stricter Security Rule provisions.
- Fines Are Rising: HIPAA fines surged 40% in 2024, totaling $36 million, with most tied to poor risk assessments and delayed breach notifications.
- New Privacy Rule Proposals: Updates may soon allow patients to transfer medical records to personal health apps, requiring policy and data management overhauls.
- State Laws Add Complexity: Laws like California’s Privacy Rights Act impose stricter consent and faster breach reporting, creating conflicts with federal HIPAA standards.
- Expanded Audit Scope: More entities, including health tech vendors and apps, may fall under HIPAA-like protections, increasing vendor management challenges.
To prepare, healthcare organizations must prioritize risk assessments, vendor oversight, and centralized compliance systems. The stakes are high - penalties can reach $50,000 per violation, with annual caps of $1.5 million.
2024-2025 Healthcare Privacy Audit Landscape: Key Statistics and Penalties
How New Privacy Laws Are Changing Audit Requirements
Healthcare organizations are now navigating a complex web of federal and state compliance requirements. In April 2024, the Office for Civil Rights (OCR) issued a Final Rule that imposes stricter guidelines on how reproductive health Protected Health Information (PHI) can be used and shared. This rule demands updates to Notices of Privacy Practices, introduces new attestation processes for specific data requests, and requires revisions to organizational policies and training materials. These changes also add fresh layers of audit checkpoints, marking a departure from the more traditional HIPAA compliance reviews.
Simultaneously, proposed updates to the Security Rule call for more rigorous measures, including annual risk assessments, penetration testing, biannual vulnerability scans, and yearly security reviews of business associates. The HHS Office of Inspector General has also recommended expanding audits to cover additional HIPAA standards, highlighting gaps in enforcement within earlier audit programs.
Federal Updates: HIPAA and Proposed Rule Changes
Recent changes to HIPAA auditing practices have broadened their scope to include web tracking and patient access provisions. OCR’s updated guidance on tracking technologies - first introduced in 2022 and revised in 2024 - emphasizes that tools like tracking pixels on patient portals often involve PHI. For instance, OCR clarifies that an IP address linked to a visit on a health-related webpage can qualify as PHI if it identifies an individual seeking medical information. This effectively brings basic web data under HIPAA’s compliance umbrella.
Proposed Privacy Rule updates introduce several patient-centric changes. Patients may soon have the right to inspect and photograph their PHI, while third-party data transfers could be limited to electronic health record systems. Additionally, disclosures may be permitted for health or safety threats deemed "seriously and reasonably foreseeable." These updates will require organizations to revise their policies, privacy notices, and documentation to ensure compliance. On the technical side, federal regulators are tightening expectations by treating the absence of multi-factor authentication and encryption as significant risk management failures. These controls are now considered baseline requirements in Security Rule audits, no longer optional safeguards.
State Privacy Laws and Their Audit Requirements
State regulations, such as California's Confidentiality of Health Information Privacy Act (CHIPPA) and new reproductive health data protections, are raising the bar for PHI security. These laws often go beyond HIPAA standards, mandating stricter consent processes, faster breach notification timelines, and more comprehensive vendor oversight. For healthcare systems operating in multiple states, this creates a patchwork of compliance challenges. Organizations must juggle varying consent rules, documentation standards, and data definitions across jurisdictions.
The post-Dobbs legal landscape has also introduced additional protections for reproductive health PHI, which sometimes overlap with HIPAA but often extend further. For example, state attorney generals now have the authority to pursue civil actions and injunctions under these laws. This has made audits more complex, as organizations must demonstrate compliance with both federal HIPAA requirements and state-specific mandates. Without federal preemption, conducting risk assessments tailored to individual states becomes a significant operational hurdle.
Expanded Scope of Protected Data and Covered Entities
New privacy laws are also redefining the scope of audits by expanding both the types of data and the entities subject to compliance. For instance, the proposed Health Infrastructure and Privacy Reinforcement Act (HIPRA) seeks to extend HIPAA-like protections to non-traditional entities, such as health tech vendors, wellness apps, and consumer health platforms that handle PHI. If passed, this legislation would bring telehealth platforms, wearables, and interconnected health devices under the umbrella of "covered entities", adding complexity to vendor management and risk assessments.
Additionally, the definition of protected data has grown to include reproductive health records, telehealth data, and information from personal health applications. Proposed HIPAA updates now require organizations to evaluate risks when patients direct their records to personal health apps, which could heighten privacy concerns and audit scrutiny. To meet these expanding requirements, organizations will need robust data mapping processes. Upcoming OCR audit programs are expected to focus on these newer provisions alongside traditional Security Rule compliance, making comprehensive preparation essential for healthcare entities.
Common Audit Challenges for Healthcare Organizations
With audit requirements constantly evolving, healthcare organizations are grappling with real-world challenges in producing evidence, managing vendors, and handling sensitive data. According to a 2024 IDC Health Insights report, nearly half (47%) of healthcare organizations lack centralized compliance oversight across both cloud and on-premises systems. This gap makes it difficult to provide consistent and complete audit evidence [3]. Adding to the pressure, enforcement trends are intensifying. For instance, in 2024, the Office for Civil Rights (OCR) issued $36 million in HIPAA fines - a 40% increase from the previous year. The most common violations included inadequate risk assessments, delayed breach notifications, and weak access controls [3][6].
Conflicting Regulatory Requirements
One of the toughest hurdles healthcare organizations face is navigating conflicting federal and state regulations. HIPAA defines protected health information (PHI) as identifiable health data managed by covered entities and business associates. However, state laws like the California Privacy Rights Act (CPRA) and Virginia's Consumer Data Protection Act take a broader view, covering personal and sensitive information beyond HIPAA’s scope. This mismatch creates gaps in audits, as data not classified as PHI under HIPAA may still fall under state regulations. Organizations often struggle to log, document, or obtain proper consent for this additional data, complicating compliance efforts. These regulatory inconsistencies become even more challenging when managing the complex web of vendors and subcontractors.
Data Tracking and Vendor Management
The rise of telehealth and digital health tools has introduced intricate data flows involving video platforms, messaging apps, mobile devices, and remote monitoring technologies. Many of these rely on third-party cloud services or communication providers. As enforcement discretion phases out, stricter security requirements are set to roll out in 2025, making compliance even trickier. Audits frequently uncover issues such as incomplete asset inventories for telehealth tools and outdated or missing business associate agreements (BAAs). Limited visibility into fourth-party integrations - vendors that your vendors rely on - further complicates matters.
Healthcare organizations now oversee risks across a sprawling network of more than 50,000 vendors and products. Managing this ecosystem is a major HIPAA compliance obstacle, requiring organizations to ensure that all business associates and subcontractors meet stringent privacy and security standards. Common audit findings include:
- Missing or outdated vendor inventories
- Inconsistent third-party risk assessments
- BAAs and security addenda that are incomplete or out of date
- Limited oversight of fourth-party tools embedded within vendor systems
Manual processes, like vendor questionnaires, often fall short in providing the efficiency and depth required for robust oversight. Auditors expect evidence such as a detailed vendor inventory linked to systems and data types, standardized risk assessments, incident and breach notification timelines, and documentation of remediation efforts.
Sensitive Data Categories and Documentation Requirements
Handling sensitive data adds another layer of complexity to audits. Emerging privacy frameworks classify reproductive, sexual, and specific behavioral health information as highly sensitive, requiring stricter protections and explicit consent protocols. Many organizations struggle with tagging and tracking these records, making it difficult to demonstrate differentiated access controls, retention policies, or additional safeguards during audits.
Adding to the challenge, HIPAA’s rules for PHI often conflict with stricter state laws that limit how reproductive health data can be shared with third parties, law enforcement, or out-of-state entities. This requires organizations to meticulously document exceptions, legal holds, and case-by-case decisions. For example, state laws increasingly designate precise geolocation data as sensitive. Enforcement actions have targeted practices like geofencing around clinics, such as reproductive health or substance use facilities, for advertising or tracking purposes. Audits demand detailed evidence, including:
- How geolocation data is collected and its purpose
- Vendors or SDKs involved in the process
- Documentation of geofencing-based profiling, if applicable
Privacy regulations are also raising the bar for consent. Organizations must provide clear, specific consent flows, updated privacy notices, and sometimes formal attestations for data use, non-discrimination, or access restrictions. During audits, they’re expected to produce version-controlled copies of privacy notices, logs or screenshots of consent events (including withdrawals), and training records for staff on these protocols. A recurring issue is the disconnect between front-end consent processes - like app interfaces or portal screens - and back-end practices for data processing and retention. This misalignment often results in findings when marketing, research, or analytics rely on ambiguous or bundled consents.
Strategies for Improving Audit Readiness
Healthcare organizations face growing challenges in keeping up with privacy regulations. To stay ahead, they need to move beyond reactive compliance and embrace continuous risk management. This shift is crucial - not just to avoid penalties, but to ensure they're always prepared for audits.
Risk-Based Privacy and Security Governance
One of the most effective ways to strengthen audit readiness is by implementing policies that focus on prioritizing threats based on their likelihood and potential impact. This means conducting annual HIPAA risk assessments and holding quarterly reviews to fine-tune controls. Using a centralized dashboard to map HIPAA and state law requirements can streamline this process [3][5]. Why is this so important? In 2024 alone, insufficient risk assessments were a leading factor in $36 million worth of OCR fines [3].
Having a centralized governance framework also helps organizations keep tabs on federal changes, such as updates to patient access rights, and state-specific breach notification rules. This approach not only reduces the risk of hefty penalties - up to $1.5 million annually - but also ensures compliance with the OCR's 2024-2025 audit program, which plans to examine 50 entities for specific provisions [2][5]. Additionally, creating clear data inventories to track PHI (protected health information) flows and vendor exchanges is a must for maintaining compliance.
Data Mapping and Standardized Frameworks
Understanding how PHI moves within an organization is another key step. Automated tools can help map these flows, from initial collection to vendor sharing, aligning them with the NIST Privacy Framework. This alignment is particularly important as organizations prepare for the 2025 HIPAA updates [3][4].
A 2024 IDC Health Insights report revealed that 47% of organizations struggle with oversight in cloud systems [3]. By adopting NIST's structured controls - such as standardizing encryption for data in transit and at rest, and monitoring access - organizations can address these gaps. These measures have proven effective in avoiding penalties, especially in cases where patient records must be delivered within 30 days. Integrating data mapping with risk assessments also helps prevent issues like delayed breach notifications, which contributed to higher fines in 2024 [3].
Once data flows are clearly mapped and standardized, the focus shifts to managing audit evidence effectively.
Centralized Documentation and Evidence Management
Managing audit trails can be a nightmare without the right tools. Instead of relying on spreadsheets, organizations should use centralized repositories to handle access logs, training records, and policy updates. This approach not only simplifies the process but ensures quick production of audit trails when needed [5].
Terry Grogan, CISO at Tower Health, shared, "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required" [1].
James Case, VP & CISO at Baptist Health, added, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with" [1].
Organizations that adopted centralized systems in 2024 enforcement actions avoided costly corrective action plans by quickly providing the required audit trails. Key strategies include role-based access controls, automated tagging of sensitive telehealth data, and quarterly reviews of evidence tied to risk assessments. These efforts not only enhance compliance but also prepare organizations to tackle the growing complexities of audits head-on.
sbb-itb-535baee
Technology Solutions for Privacy Regulation Audits
Healthcare organizations often face challenges with fragmented data sources, making it tough to demonstrate compliance with HIPAA, HITECH, and various state regulations. Without a unified system, real-time oversight of vendor risks, access controls, and incident response evidence becomes nearly impossible. Adding to the pressure, OCR enforcement actions frequently focus on inadequate risk assessments and delays in breach notifications. Below, we explore how technology is reshaping the audit process through centralized platforms, automated assessments, and collaborative tools.
Centralized Risk and Compliance Platforms
Centralized platforms tailored for healthcare bring together policies, risk registers, assessments, business associate agreements (BAAs), and PHI data flows into one unified system. For example, Censinet RiskOps™ connects controls, assessments, and evidence to frameworks like HIPAA, HITECH, NIST, and state laws. This integration allows organizations to generate instant, customized reports for auditors and regulators.
When it comes to vendor management, these platforms consolidate third-party inventories, risk assessments, security questionnaires, BAAs, and remediation plans. This approach creates a clear, standardized process that auditors can easily follow - from initial assessments and risk scoring to mitigation actions and ongoing monitoring. Vendors handling PHI, clinical applications, medical devices, and supply chains are all managed within this streamlined system.
Automation and AI for Risk Assessments
Centralized systems become even more effective with automation. Tools like Censinet AI™ simplify evidence collection by analyzing policy libraries, system logs, tickets, and previous assessments. The AI can auto-complete assessment forms, propose control mappings, draft risk narratives, and flag missing evidence - such as MFA logs, encryption settings, or vendor attestations.
These platforms also integrate with identity management systems, EHRs, and security tools to continuously monitor key controls like MFA status, encryption coverage, and access logs. Automated alerts notify teams of potential issues, such as expiring vendor certificates or BAAs, well before they become audit problems. This approach combines automated efficiency with human oversight, cutting assessment times from hours to minutes while preserving critical decision-making.
Collaborative Risk Management in Healthcare
Collaboration is another key advantage of these platforms. Shared workspaces enable privacy officers, CISOs, compliance managers, legal teams, and clinical leaders to work together on risks, controls, and corrective actions. This replaces the inefficiency of spreadsheets and email chains. Role-based access ensures stakeholders only see what’s relevant to their role, safeguarding sensitive PHI details. Task management tools assign responsibilities, deadlines, and progress updates for remediation efforts, showing auditors that findings are actively addressed.
Matt Christensen, Sr. Director GRC at Intermountain Health, remarked: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." [1]
These platforms also streamline external audits. Vendors can securely complete standardized questionnaires and upload certifications without exposing unrelated data. For auditors, organizations can set up read-only "audit rooms" with limited-time access to necessary policies, assessments, and evidence. Encryption (both in transit and at rest), granular permissions, and detailed access logs maintain security while ensuring smoother, more transparent audits. By replacing last-minute chaos with a structured, documented process, these tools help healthcare organizations stay on top of compliance challenges.
Conclusion
Healthcare organizations can no longer afford to approach privacy laws with a reactive, checkbox mindset. Changes like federal HIPAA updates, evolving state privacy regulations, and broader definitions of protected data have reshaped audit expectations. Today, continuous, risk-based oversight is the new standard. Delaying investments in proper controls only increases the risk of penalties, corrective actions, and damage to an organization’s reputation.
Adopting proactive governance means leveraging technology to streamline compliance efforts. Centralized platforms, such as Censinet RiskOps™, bring together policies, risk assessments, vendor management, and supporting documentation into a single system. These tools replace outdated manual processes like spreadsheets and email chains with automated workflows, AI-driven questionnaires, and real-time monitoring. This approach not only simplifies assessments but also ensures human oversight remains a key part of the process. It’s a strategic shift that strengthens vendor oversight and fosters ongoing process improvements.
Third-party risk management plays a critical role in staying audit-ready. Regulators increasingly hold healthcare entities responsible for the practices of their business associates. To meet these expectations, organizations must implement systematic vendor oversight through annual verifications, standardized questionnaires, and continuous monitoring. Collaborative platforms make it easier to manage vendor inventories, risk ratings, and remediation efforts across areas like patient health information, clinical applications, medical devices, and supply chains.
To stay ahead, audit readiness should become an ongoing practice. By embedding privacy and security into strategic planning, incorporating continuous risk assessments into every new technology deployment, and maintaining centralized documentation, healthcare organizations can demonstrate compliance effectively and transparently.
Brian Sterud, CIO at Faith Regional Health, noted: "Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters." [1]
FAQs
What challenges do healthcare organizations face with new privacy laws?
New privacy laws are driving healthcare organizations to reevaluate how they handle compliance. These regulations require stronger safeguards for sensitive information, more detailed and frequent audits, and continuous updates to internal policies to stay aligned with legal standards.
To tackle these demands, organizations need to adopt solid risk management practices and utilize tools that simplify compliance processes, minimize third-party risks, and protect patient data. Taking a forward-thinking approach and staying flexible will be crucial to meeting these shifting requirements.
What challenges do healthcare organizations face in managing vendor risks under new privacy laws?
Healthcare organizations today grapple with the tough task of managing vendor risks, driven by the ever-expanding complexity of supply chains and the mounting pressures of privacy regulations. Keeping third-party vendors in line with these laws isn’t a one-and-done effort - it demands ongoing monitoring and strong risk management practices.
To tackle these issues effectively, organizations need tools that work in real time. These solutions should simplify risk assessments, allow for efficient comparisons, and encourage collaboration across teams. By leveraging such tools, healthcare providers can protect sensitive patient information more effectively while staying aligned with the constantly changing regulatory landscape.
What steps can healthcare organizations take to prepare for broader audit requirements?
Healthcare organizations can better navigate expanding audit requirements by taking proactive steps to align with evolving privacy regulations. Key strategies include performing ongoing risk assessments, leveraging advanced tools like AI-driven risk management platforms, and maintaining thorough documentation of compliance efforts.
Staying ahead also means measuring performance against industry benchmarks, automating data collection to save time, and encouraging cooperation among internal teams and external partners. By addressing potential weaknesses early, organizations can minimize unexpected challenges during audits and maintain compliance with emerging privacy laws.


