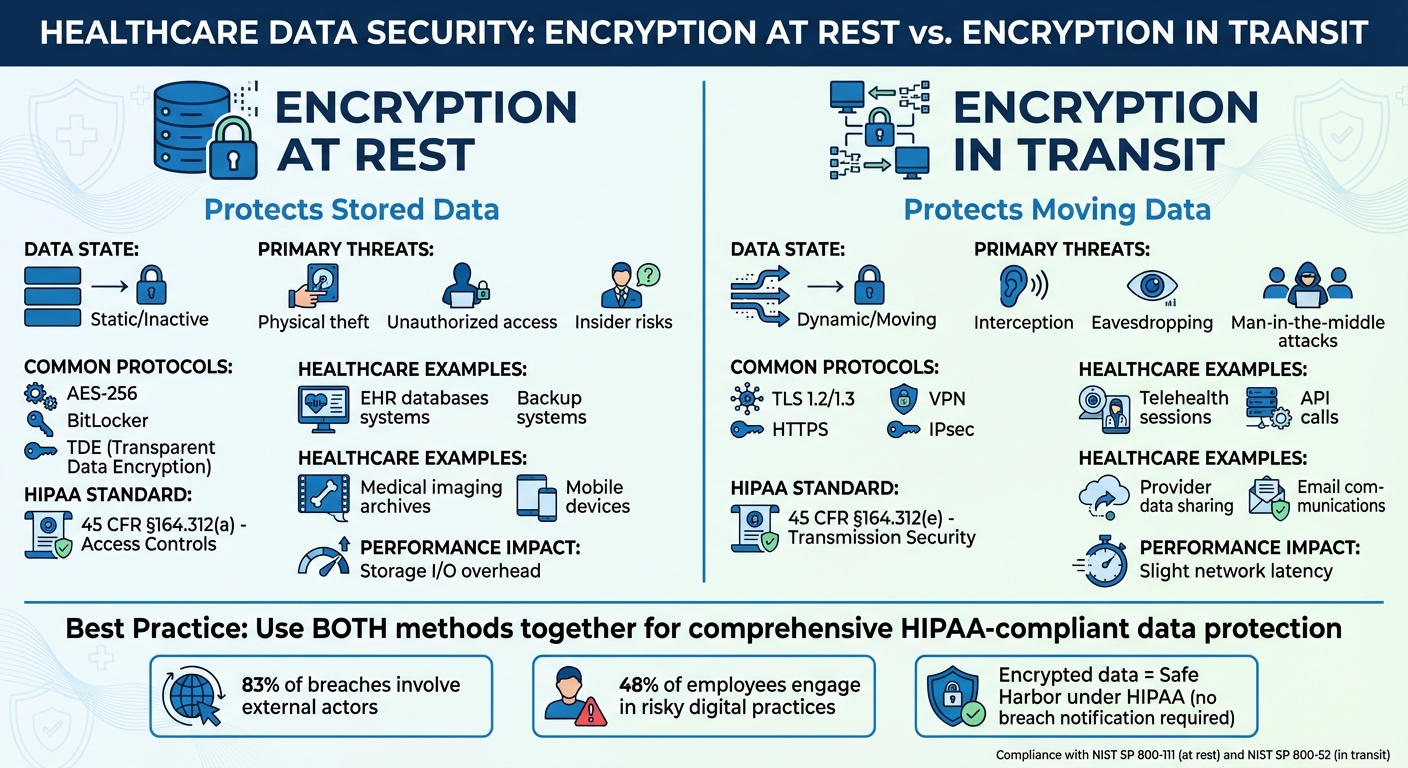
Encryption at Rest vs. Encryption in Transit: Differences
Post Summary
Protecting sensitive data is non-negotiable, especially in healthcare. Encryption ensures data remains secure, whether it's stored or being transferred. Here's the key takeaway:
- Encryption at Rest: Secures stored data (e.g., in databases, cloud storage, or devices). It protects against risks like theft or unauthorized access.
- Encryption in Transit: Safeguards data as it moves across networks, ensuring privacy during transfers like emails, telehealth sessions, or API calls.
Both methods are essential for HIPAA compliance and data security. Encryption at rest uses techniques like AES-256 and full-disk encryption, while encryption in transit relies on protocols like TLS and VPNs. Together, they create a robust defense against breaches.
Quick Comparison
| Feature | Encryption at Rest | Encryption in Transit |
|---|---|---|
| Data State | Stored/static | Moving/transferred |
| Primary Threats | Physical theft, unauthorized access | Interception, eavesdropping |
| Common Protocols | AES-256, BitLocker, database encryption | TLS, HTTPS, VPN |
| HIPAA Standard | 45 CFR §164.312(a) | 45 CFR §164.312(e) |
| Healthcare Examples | Protects EHRs, backups, imaging files | Secures telehealth, APIs, data sharing |
Bottom Line: Use both methods together for comprehensive data security.
Encryption at Rest vs Encryption in Transit: Key Differences for Healthcare Data Security
🔒 Encryption Explained Simply Data in Transit vs. Data at Rest
What is Encryption at Rest?
Encryption at rest transforms inactive data stored on physical media - like hard drives, cloud storage, or databases - into ciphertext. This ensures the data remains protected even if the storage devices are compromised. For healthcare organizations, this is a critical safeguard for protecting sensitive information, such as Protected Health Information (PHI). It also helps clarify the distinction between encryption at rest and its counterpart, encryption in transit.
In practical terms, encryption at rest shields PHI stored on devices like stolen laptops or breached servers. Under the HITECH Act and HIPAA Breach Notification Rule, encrypted data that is accessed without authorization is considered non-reportable. Steve Alder, Editor-in-Chief of The HIPAA Journal, explains:
"If data acquired without authorization is unreadable, undecipherable, and unusable, the loss of data is not a notifiable breach of unsecured ePHI."[9]
The Advanced Encryption Standard (AES) with 256-bit keys (AES-256) is widely recognized as the go-to standard for encryption at rest. Many modern systems also employ envelope encryption. In this approach, Data Encryption Keys (DEKs) protect the data, while Key Encryption Keys (KEKs) secure the DEKs. These KEKs are stored in secure environments like Hardware Security Modules (HSMs) or cloud-based key vaults.
Key Features of Encryption at Rest
Encryption at rest is implemented through multiple technical layers, each addressing specific storage scenarios:
- Full-Disk Encryption (FDE): Encrypts the entire storage device at the hardware level. This ensures that if a laptop or tablet is lost or stolen, the data remains inaccessible.
- File-Level Encryption: Targets specific files or directories. This is particularly useful for sensitive files like medical imaging or lab reports.
- Database Encryption (TDE): Secures entire databases or specific columns containing sensitive data. For instance, Microsoft Azure began enabling Transparent Data Encryption (TDE) by default for new SQL databases in June 2017.
- Key Management: Focuses on securely managing encryption keys, including their creation, rotation, and deletion. Many systems adhere to standards like FIPS 140-2 to ensure the security of key management modules.
Healthcare Applications
Encryption at rest is indispensable for safeguarding PHI in healthcare settings. For example, Electronic Health Record (EHR) systems store structured patient data - like diagnoses, medications, and treatment plans - in databases that must remain secure even during a network breach. Encryption at rest ensures this data is protected from unauthorized access.
Cloud storage is another area where encryption at rest is critical. A notable case occurred in 2021 when Florida-based 20/20 Eye Care Network exposed the PHI of over 3.2 million individuals due to a misconfigured Amazon Web Services (AWS) S3 bucket[10]. Proper encryption at rest would have rendered the exposed data unreadable, minimizing the breach's impact.
Additionally, encryption at rest is vital for securing large-scale medical imaging archives, such as DICOM files from X-rays, MRIs, and CT scans. Even if storage devices are compromised, the encrypted data remains protected. Another key benefit is crypto-shredding, a process where encryption keys are deleted, permanently rendering the data unrecoverable. This approach is particularly useful for securely decommissioning old storage systems or complying with data retention policies.
What is Encryption in Transit?
Encryption in transit, also known as data in motion encryption, protects information as it moves between locations - whether that's over the internet or within internal networks. Unlike encryption at rest, which secures stored data, this process focuses on safeguarding data as it travels from sender to receiver.
This protection relies on three main components: authentication (confirming the identities of the sender and receiver), integrity (ensuring the data remains unaltered during transfer), and encryption (keeping the content private). The process begins with endpoints performing a handshake to agree on encryption protocols and exchange keys. This creates a secure pathway that prevents interception. Even if data is intercepted, encryption ensures it's indecipherable, thwarting eavesdropping and man-in-the-middle attacks.
Google Cloud provides a clear explanation:
"Encryption in transit authenticates the endpoints and encrypts the data before transmission. On arrival, the receiver decrypts the data and verifies that it was not modified during transit." [11]
Modern encryption methods, such as RSA-2048, deliver strong security. In healthcare, encryption in transit is particularly critical under HIPAA regulations. If encrypted electronic protected health information (ePHI) is intercepted or lost during transfer, it is typically not classified as a "notifiable breach" because the data remains unreadable. As Steve Alder, Editor-in-Chief of The HIPAA Journal, puts it:
"Encrypting ePHI in transit ensures that, if a hacker accesses a router or intercepts a communication, the ePHI contained in the communication is unreadable, indecipherable, and unusable." [12]
This security framework underpins the technologies used to protect data in transit.
Key Features of Encryption in Transit
Several protocols and tools work together to ensure data remains secure during transfer:
- TLS (Transport Layer Security): TLS is the standard for securing HTTPS connections, web applications, and API calls. As the modern replacement for SSL, TLS is the backbone of secure online communication.
- VPNs (Virtual Private Networks): VPNs use IPsec to create encrypted private connections, often between corporate networks and cloud environments. This is especially helpful for remote healthcare workers accessing hospital systems.
- mTLS (Mutual TLS): Adds a layer of security by requiring both the client and server to authenticate each other’s identities during service-to-service communications.
Major cloud providers also embed encryption into their infrastructure. For example, Google uses its BoringCrypto core for TLS, validated to FIPS 140-3 level 1 standards, while AWS encrypts all network traffic between its data centers at the physical layer before it exits secure facilities.
Healthcare Applications
Encryption in transit plays a critical role in healthcare. It ensures the protection of ePHI in various scenarios, including:
- Telehealth visits: Whether video or audio, virtual consultations rely on encryption to prevent unauthorized listening or viewing of sensitive patient discussions.
- API calls: Data exchanged between systems, such as a pharmacy system and a hospital's electronic health record (EHR), remains private and secure through encryption.
- Third-party data sharing: When patient records are shared with billing vendors, insurance companies, or diagnostic services, encryption ensures privacy throughout the transfer.
For HIPAA compliance, healthcare organizations must also sign Business Associate Agreements (BAAs) with cloud service providers, acknowledging the access these providers may have to data during transmission.
While AES 128-bit encryption meets the minimum HIPAA standards, the National Institute of Standards and Technology (NIST) advises upgrading to AES 192-bit or 256-bit for stronger protection. To simplify encryption management, solutions like AWS Certificate Manager can automate the generation, distribution, and rotation of digital certificates, making it easier to maintain security at scale.
Encryption in transit is just as critical as encryption at rest for protecting the confidentiality and integrity of protected health information (PHI) throughout its lifecycle.
Key Differences Between Encryption at Rest and Encryption in Transit
Encryption at rest and encryption in transit address different aspects of data security. Encryption at rest focuses on protecting static data stored on physical media like hard drives, databases, or cloud storage. On the other hand, encryption in transit secures data as it moves between locations, such as during email exchanges, web traffic, or file transfers.
The security challenges they address also differ. Data at rest is susceptible to risks like physical theft, unauthorized access, and insider threats. Meanwhile, data in transit is vulnerable to network-based attacks, including interception, eavesdropping, and man-in-the-middle exploits. As Daniel Argintaru from Mimecast puts it:
"Data encryption is a core component of modern data protection strategy, helping businesses protect data in transit, in use and at rest." [2]
When it comes to implementation, encrypting data at rest can be more complex and may impact database performance. FileCloud notes:
"A simple TLS certificate for a website is often considered a far less complex undertaking than a full database encryption project." [8]
From a compliance perspective, these methods are governed by different standards. For HIPAA, encryption at rest falls under the Access Controls standard (45 CFR §164.312(a)), while encryption in transit aligns with Transmission Security (45 CFR §164.312(e)). Additionally, NIST provides specific guidelines: SP 800-111 for data at rest and SP 800-52 for data in transit.
Comparison Table
| Feature | Encryption at Rest | Encryption in Transit |
|---|---|---|
| Data State | Static/inactive data stored on physical or digital media | Dynamic data moving between networks |
| Primary Threats | Physical theft, unauthorized access, insider risks | Interception, eavesdropping, man-in-the-middle attacks |
| Common Protocols | AES-256, full-disk encryption, BitLocker, Transparent Data Encryption (TDE) | TLS 1.2/1.3, HTTPS, IPsec, VPN, SSH, SFTP |
| Performance Impact | Storage I/O overhead; complex key management | Slight network latency during connection handshakes |
| HIPAA Standard | 45 CFR §164.312(a) – Access Controls | 45 CFR §164.312(e) – Transmission Security |
| NIST Guidance | NIST SP 800-111 | NIST SP 800-52 |
| Healthcare Applications | Protects ePHI on servers, mobile devices, USB drives, and backups | Protects ePHI during exchanges between providers, patients, or cloud services |
Understanding these distinctions is essential for choosing the right encryption strategy, as discussed further in the next section.
sbb-itb-535baee
Use Cases and Implementation Guidelines
Encryption at Rest Use Cases
Healthcare organizations rely on encryption at rest to secure patient data across various storage environments, protecting it from physical theft and unauthorized access. For example, databases storing patient medical records often use AES-256 encryption to safeguard electronic protected health information (ePHI) on servers. Similarly, sensitive medical imaging files, like X-rays and MRI scans stored in object storage, should also be encrypted to prevent unauthorized exposure in the event of a system breach.
Portable devices and media - such as laptops, tablets, smartphones, and USB drives - pose additional risks when they contain ePHI. Encrypting these devices is essential to meet HIPAA’s Access Controls standard (45 CFR §164.312(a)). Backup systems and archives must also be encrypted to ensure consistent data security. As Kurt Kumar from Amazon Web Services explains, "Data encryption can help protect your business data even after a breach occurs. It provides a layer of defense against unintended disclosure." [14]
Encryption in Transit Use Cases
Telehealth communications are a prime example of why encryption in transit is critical. Video consultations, API calls between telehealth platforms, and real-time patient monitoring data transmitted from medical devices to cloud services require TLS 1.2 or higher to guard against interception. Beyond encryption, these tools must also include integrity controls to prevent unauthorized modifications. For instance, apps like WhatsApp, while encrypted, may lack the necessary controls or Business Associate Agreements (BAAs) required for HIPAA compliance.
Secure data exchanges between healthcare providers, insurers, and third-party vendors are another key area where encryption in transit is vital. The AWS Business Associate Addendum mandates "the encryption of protected health information (PHI) as defined by HIPAA at rest and in transit." [15] This requirement also applies to microservices communication within healthcare IT systems, where service meshes can streamline secure TLS session negotiations without requiring changes to application code.
Implementation Guidelines
Healthcare organizations should prioritize encryption by default, starting with cloud storage systems. Configuring these systems to automatically encrypt new volumes using AES-256 with customer-managed keys (CMKs) helps maintain a secure baseline. For data in transit, enforcing bucket policies that deny access over HTTP and blocking insecure protocols at the network level ensures secure communication.
Effective key management is another essential component. Decryption keys should be stored separately from the encrypted data to reduce the risk of a single point of failure. The Department of Health and Human Services (HHS) advises, "To avoid a breach of the confidential process or key, these decryption tools should be stored on a device or at a location separate from the data they are used to encrypt or decrypt." [16] Automated tools like AWS Config can help detect unencrypted resources and trigger remediation processes.
Regular audits are crucial for maintaining security. Logging systems should track when encryption keys are accessed and by whom, providing a clear audit trail. Separating health data from non-health data by using distinct accounts or organizational units can simplify the implementation of least-privilege access controls. By aligning with NIST standards, organizations can gain a “safe harbor” under HIPAA, meaning encrypted data breaches don’t require the same notification protocols as unencrypted breaches.
To strengthen their cybersecurity strategy, healthcare organizations can integrate these encryption practices with broader risk management tools like Censinet RiskOps™, which address complex cyber risks unique to the healthcare industry.
When to Use Each Encryption Method
Choosing between encryption at rest and encryption in transit depends on whether the data is being stored or actively transferred.
When to Prioritize Encryption at Rest
Encryption at rest is essential for healthcare organizations when Protected Health Information (PHI) is stored in cloud databases, on-premises drives, mobile devices, or backups [5]. This type of encryption is especially important to reduce risks from lost or stolen devices [5].
It also protects against insider threats and hackers who bypass perimeter defenses, often through phishing attacks. Even if an attacker gains access to the system, encrypted data remains unreadable to unauthorized users [5]. Although HIPAA lists encryption as an "addressable" safeguard rather than a "required" one, it has effectively become a standard since no alternative offers the same level of security for PHI [5]. Any data labeled as "confidential" or "highly confidential" should always be encrypted at rest [6].
When to Prioritize Encryption in Transit
Encryption in transit becomes critical when data is being transferred between systems, devices, or cloud environments [3]. This is particularly important for Voice-over-IP (VoIP) and video conferencing during live patient consultations, where the risk of eavesdropping is high [3]. For remote access scenarios, such as healthcare providers accessing Electronic Health Records (EHRs) from home or mobile devices, using TLS 1.2 or higher is essential [3].
Modern healthcare systems also require encryption for API interactions and communications between microservices [3]. With about 83% of data breaches involving external actors driven by financial motives, securing data during transmission is a must [3]. Additionally, encryption is critical in hybrid and multi-cloud setups where data moves between on-premises systems and cloud platforms via VPNs or dedicated connections [6]. These measures ensure data security while in motion and strengthen overall protection.
Using Both Methods Together
The most effective approach combines both encryption methods in a layered defense strategy [3]. End-to-end encryption is a key part of this, ensuring data is encrypted on the sender’s device and only decrypted by the intended recipient. This process prevents even service providers from accessing plaintext patient information [4].
Since nearly half of employees engage in risky digital practices [2], healthcare organizations should automate encryption protocols wherever possible. For example, telehealth sessions should use TLS/SRTP for live communication and AES-256 to secure any recordings [3]. Proper key management is equally vital - decryption keys must be stored separately from encrypted data to avoid creating a single point of failure [3].
For organizations with complex vendor networks, tools like Censinet RiskOps™ can simplify the coordination of encryption requirements across multiple stakeholders. This ensures that both vendors and business associates adhere to strict encryption standards for PHI, supporting comprehensive risk management and regulatory compliance.
Conclusion
Encryption plays a critical role in safeguarding sensitive healthcare data. Encryption at rest shields stored PHI from physical threats, while encryption in transit ensures data remains secure during network transfers [7]. Together, these methods create a layered defense, addressing different vulnerabilities to protect data throughout its lifecycle [7].
For healthcare organizations, adopting both encryption methods isn't just a technical choice - it's a necessity. While encryption is technically "addressable" under 45 CFR §164.312 of HIPAA, it has become the standard because no other measure offers comparable protection [13]. Additionally, encrypted PHI benefits from a "safe harbor" provision, meaning breaches involving properly encrypted data do not trigger notification requirements if the data is "unusable, unreadable, or indecipherable" to unauthorized individuals [1]. This makes encryption a dual-purpose tool: it strengthens security and simplifies compliance.
The stakes are high. Studies show that 48% of employees engage in risky behaviors, and 83% of breaches are driven by external attacks [2][3]. For healthcare organizations managing complex vendor networks and third-party relationships, platforms like Censinet RiskOps™ streamline encryption protocols, ensuring PHI remains protected across all stakeholders.
Following NIST standards - like AES-256 for encryption at rest and TLS 1.2 or higher for data in transit - lays the groundwork for strong data security [13]. Pairing this with automated key management, regular risk assessments, and multi-factor authentication creates a comprehensive approach to protecting patient data. By implementing these strategies, healthcare organizations can secure sensitive information, maintain trust, and achieve full HIPAA compliance. Encryption isn't just a safeguard - it's the cornerstone of modern healthcare data security.
FAQs
What types of threats does encryption at rest protect against?
Encryption at rest protects stored data by making it unreadable without the proper decryption key. This layer of security helps guard against risks such as unauthorized access, data breaches, and insider threats. It becomes especially critical in cases where storage devices are lost, stolen, or compromised. By encrypting data at its storage location, organizations can lower the chances of exposure and ensure they meet data security regulations.
How does encryption in transit protect sensitive data during telehealth sessions?
Encryption in transit secures sensitive data during telehealth sessions by employing secure protocols like TLS 1.2 or 1.3. These protocols work by encrypting electronic protected health information (ePHI) as it moves between devices, rendering the data unreadable to anyone attempting to intercept it without proper authorization.
This method not only preserves patient confidentiality but also ensures compliance with security standards required in healthcare communication.
Why is it essential to use both encryption at rest and encryption in transit to protect healthcare data?
Using both encryption at rest and encryption in transit plays a key role in keeping sensitive healthcare data secure. Encryption at rest protects stored data - like patient records or medical images - by ensuring it remains safe from unauthorized access, even if the storage system is breached. On the other hand, encryption in transit safeguards data as it travels across networks, preventing interception or tampering during transmission.
When combined, these methods create a strong, layered defense that protects data at every stage - whether it's being stored, transmitted, or accessed. This approach is especially important in healthcare, where safeguarding patient information and meeting regulations such as HIPAA are non-negotiable priorities.


