How to Enforce Least Privilege in Healthcare IT Systems
Post Summary
The Principle of Least Privilege (PoLP) ensures that users, systems, and applications in healthcare IT only access the minimum data necessary for their roles. This approach reduces risks like data breaches, insider threats, and compliance violations. Here's how to implement it effectively:
- Review Access: Inventory all users, systems, and permissions. Identify inactive accounts, excessive access, and gaps.
- Create Role-Based Models: Define access roles by job functions (e.g., nurse, billing clerk) and align them with HIPAA standards.
- Use Access Controls: Implement Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) for precise permissions.
- Secure Privileged Access: Use Privileged Access Management (PAM) tools to restrict administrative accounts and enforce session monitoring.
- Monitor and Adjust: Conduct regular access reviews, track metrics (e.g., excessive permissions, inactive accounts), and manage vendor access.
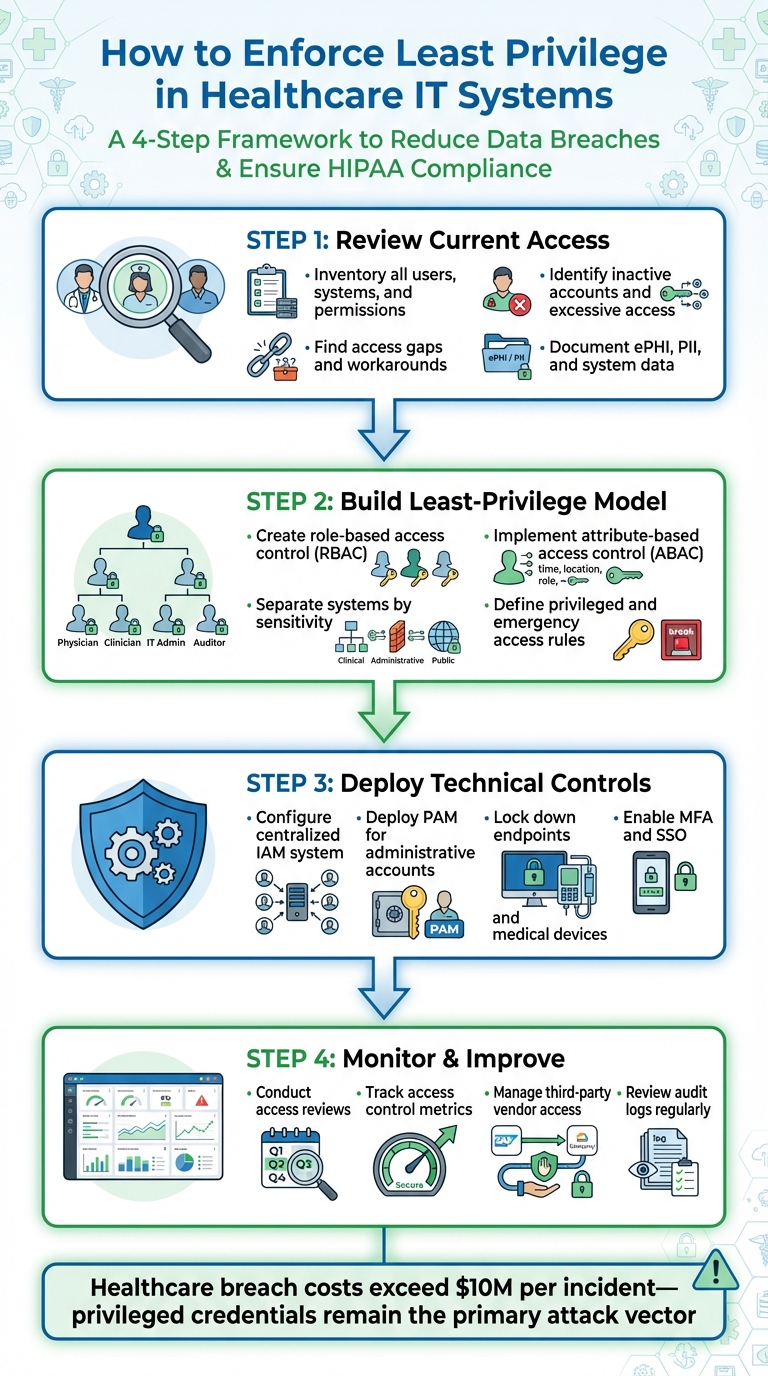
4-Step Framework for Implementing Least Privilege in Healthcare IT Systems
Step 1: Review Current Access and Permissions
To ensure secure and efficient operations in healthcare IT, start by enforcing the principle of least privilege. This involves mapping out who has access to what across your system and comparing those permissions to what each role actually needs to perform their job. Without a clear picture of current access, implementing effective controls becomes nearly impossible.
Document All Users, Systems, and Data
Begin by building a centralized inventory that includes every user and system in your environment. For human users, this means listing employees, contractors, residents, volunteers, students, and others, along with their roles, departments, managers, work locations, and employment statuses. Don’t forget non-human identities like service accounts, application accounts, robotic process automation IDs, and device identities, ensuring each is linked to its corresponding system and function.
Next, catalog critical systems and applications such as EHR/EMR platforms, PACS, billing and RCM systems, patient portals, imaging devices, biomedical/IoT equipment, directory services, VPNs, and cloud-based tools. For each system, note the type of data it handles. Finally, identify major data types - ePHI/PHI, PII, payment data, clinical research data, logs, and backups - and map them to their storage locations.
Pull data from sources like HR systems, IAM/Active Directory, EHR admin consoles, CMDBs, and medical device management tools. Make sure the inventory is exportable for audits and HIPAA documentation. This comprehensive overview is crucial for spotting where permissions are excessive or missing.
Find Excessive Permissions and Access Gaps
With your inventory complete, analyze current permissions to uncover inactive accounts, shared credentials, or roles with more access than necessary. IT risk assessments frequently reveal "zombie accounts" - inactive accounts that can be exploited by attackers. Look for mismatched access, such as employees who’ve changed roles but still retain permissions from their previous positions (e.g., a staff member moving from ICU to billing but keeping ICU EHR access).
Simultaneously, identify access gaps where users lack the permissions they need. Speak with frontline staff - clinicians, nurses, billing teams, schedulers - and ask about recurring issues like shared logins, frequent help desk overrides, or other workarounds. Help desk ticket data can also highlight patterns, such as roles that repeatedly request emergency access or additional permissions. These trends signal that certain roles may be under-provisioned. Tools like Censinet RiskOps™ can help centralize cybersecurity and risk data, making it easier to document and track these issues collaboratively.
This step lays the groundwork for creating accurate, role-based access templates.
Create Standard Roles Based on Job Functions
After identifying access issues, the next step is to develop standardized access roles tailored to specific job functions, such as clinicians, technical staff, or vendors. Use job descriptions and workflow information from HR and department leaders to define each role. For every role, document the systems required, the type of access (e.g., read, write, approve), the scope of patient or departmental access, and any constraints like time or location.
These role definitions should be reviewed by compliance and privacy officers to ensure they align with HIPAA's minimum necessary standard and verified by department heads to confirm they support actual workflows. Align each task (e.g., ordering labs or accessing imaging) with the precise data access needed, excluding any unnecessary permissions.
Once finalized, encode these templates into IAM or RBAC tools to ensure consistent provisioning and deprovisioning. Start with minimal access and only add privileges as needed. This approach helps prevent unauthorized administrative access while ensuring staff can perform their duties efficiently.
Step 2: Build a Least-Privilege Access Model
After documenting users, systems, and data, the next step is to organize this inventory into a structured least-privilege model. This means matching every user and system to specific job roles and data domains. Then, define the applications, data types (like EHR, PACS, and billing), and actions (view, edit, prescribe, administer) that each role requires to perform its duties. Any permissions that don’t serve a clear business or clinical purpose should be removed. It’s also crucial to ensure that workflows for patient care remain intact. Start with a pilot program, gather feedback, make adjustments, and then implement it across the system. This model becomes the backbone for applying precise technical controls.
Use Role-Based and Attribute-Based Access Control
Begin by implementing Role-Based Access Control (RBAC) as your foundation. Design roles around stable job functions and care settings - examples include inpatient nurse, ED nurse, attending physician, resident, pharmacist, front-desk registrar, and revenue-cycle analyst - rather than assigning permissions to individuals. For each role, grant only the minimum access necessary to perform tasks. Standardize these roles in your IAM and EHR systems so that access is automatically updated when employees are hired, transferred, or leave the organization. For instance, a billing specialist might have access to insurance and encounter data but wouldn’t be able to edit clinical notes.
Next, layer Attribute-Based Access Control (ABAC) on top of RBAC to account for dynamic, context-specific needs. In U.S. healthcare, useful attributes include location (such as ICU or outpatient clinic), employment type (staff versus contractor), current shift (on-duty or off-duty), relationship to the patient (assigned provider or unrelated), and the risk level of the action. For example, a nurse’s RBAC role might allow general access to EHR charts, but ABAC could limit detailed viewing or editing to patients currently assigned to that nurse during their scheduled shift. This would prevent unauthorized access from home or outside regular hours unless an elevated process is followed. Combining RBAC and ABAC ensures both consistency and adaptability.
Separate Systems and Data by Sensitivity
Segmenting your network is essential to limit lateral movement in case of a security breach. Separate clinical networks (like EHR, PACS, and lab interfaces), administrative systems (billing, HR, email), medical devices and IoT (infusion pumps, imaging equipment), and vendor or third-party access. Use firewalls and access lists to control traffic between these zones.
Within each zone, classify data based on sensitivity and apply the appropriate access controls. For example, ePHI and clinical data require the strongest protections, such as encryption (both at rest and in transit), multi-factor authentication, and detailed audit logs. Other sensitive data, like payment card information and personally identifiable information, also needs strict safeguards. Meanwhile, less sensitive data, such as public-facing marketing materials or anonymized reports, can have broader access. Align these classifications with HIPAA’s minimum necessary standard and document them in your security policies.
Set Rules for Privileged and Emergency Access
Privileged accounts, such as those used by domain administrators, EHR administrators, or medical device managers, need extra oversight. Enforce separation of duties so no single person can both approve and execute high-risk changes, such as those in clinical billing or EHR security settings. Use a centralized Privileged Access Management (PAM) solution to manage these accounts. This should include multi-factor authentication, session recording, and just-in-time access, where administrative rights are granted only for specific tasks and then revoked afterward. Privileged accounts should never be used for routine activities like checking email or browsing the web.
For emergency access scenarios, create time-limited roles with strong authentication. Log and audit all instances of emergency access. Periodically review these logs, allowing compliance or privacy officers to verify that each instance met the policy’s emergency criteria. Follow up on any access that seems unnecessary or misused. This ensures emergency access remains a rare exception and not a workaround for poorly designed access roles.
Step 3: Deploy Technical Controls and Processes
Set up technical systems that ensure the principle of least privilege is applied across your healthcare IT environment. By using the role-based and attribute-based models discussed earlier, these controls help enforce access policies effectively. This includes configuring your identity and access management (IAM) platform to automate role assignments, introducing privileged access management (PAM) tools to secure administrative accounts, and limiting endpoints and medical devices to their intended functions. These measures align with the access models we've covered, ensuring consistent operations across the board.
Configure Identity and Access Management (IAM)
A centralized IAM system is key to connecting all your applications - like electronic health records (EHR), picture archiving and communication systems (PACS), pharmacy systems, billing platforms, cloud services, and on-premises directories. This unified system ensures that role-based access control is applied consistently, whether someone is logging into medical records at a nursing station or accessing lab results remotely via a VPN. Automate tasks like provisioning and de-provisioning based on HR updates, such as when a nurse moves to a different department.
Get rid of shared accounts completely. Every user - whether a clinician, administrator, or vendor - should have their own unique login tied to their role. Use multi-factor authentication (MFA) for all users, especially for remote access or tasks like prescribing medications or reviewing billing data. To make things smoother, integrate single sign-on (SSO), allowing users to switch between applications easily while still enforcing least privilege access for each system they use.
Deploy Privileged Access Management (PAM)
While IAM handles everyday user access, PAM is all about securing high-risk administrative privileges. Store privileged accounts - like those for domain administrators, EHR superusers, database admins, and biomedical engineers - in a centralized PAM vault. This helps prevent routine use of these accounts. Add layers of security like MFA, regular password updates, and just-in-time access, where administrative rights are granted only for specific tasks and then quickly revoked.
Enable session recording for high-risk actions, such as changes to EHR security settings, domain controllers, or databases containing sensitive health information. These recordings provide an audit trail that compliance officers can review to ensure privileged access is used appropriately. For emergency situations, implement time-limited roles with strong authentication and automatic logging. Follow up on all such access to confirm it aligns with your policies.
Lock Down Endpoints, Servers, and Medical Devices
IAM and PAM controls are only part of the picture - securing endpoints, servers, and medical devices is equally critical. Remove local administrator rights from standard user accounts on clinical workstations and laptops using group policies or endpoint management tools. This prevents unauthorized software installations and changes to security settings. Use application allowlisting on clinical devices to ensure only approved software - like EHR clients, imaging tools, and dictation programs - can run. Any exceptions should go through a formal IT approval process.
For shared devices like workstations on wheels or nursing station computers, set up fast user switching with SSO badges or short PINs. This allows clinicians to access patient records quickly without compromising security. Keep the operating system locked down under IT-managed profiles. Apply similar measures to servers, such as disabling unnecessary services and ports, enforcing full-disk encryption, and enabling automatic screen locking after short periods of inactivity that align with clinical workflows. For medical devices like infusion pumps and imaging systems, restrict access to only the functions needed for patient care and place these devices on segmented networks with strict firewall rules to limit exposure.
sbb-itb-535baee
Step 4: Monitor Access and Improve Over Time
Once you've implemented strong IAM and PAM controls, the work doesn't stop there. Continuous oversight is critical to keep these measures effective and responsive. Maintaining a least privilege approach is an ongoing effort - it requires regular monitoring and timely updates. This aligns with NIST's Zero Trust guidance, which emphasizes proactive access management. In healthcare, regulations now mandate regular reviews and auditable logs to ensure compliance and security[1][4].
Conduct Regular Access Reviews
Schedule quarterly access reviews with department managers to ensure employees’ access permissions align with their current job responsibilities. These reviews help prevent "privilege creep", which can happen when staff change roles or take on temporary assignments. During these sessions, look for red flags like excessive permissions, unnecessary cross-department access, or emergency privileges that were never revoked[1][2].
Inactive or "zombie" accounts are another risk to watch out for. These accounts can linger long after an employee has left the organization, posing a significant security threat. To combat this, integrate your HR and identity management systems so that terminations and role changes automatically trigger de-provisioning or access adjustments.
Track Access Control Metrics
To measure how well your least-privilege model is working, establish clear metrics. Track data like:
- The percentage of users with excessive permissions.
- The number and age of inactive accounts that have been removed.
- The frequency of privileged access violations flagged by monitoring tools[1][2].
Additionally, keep an eye on administrative activities, failed login attempts, and unusual off-hours access to sensitive systems. Use these insights to populate security dashboards and compliance reports, demonstrating adherence to HIPAA and NIST standards. Regularly reviewing logs and integrating your system with a SIEM can help you detect and respond to suspicious activity more effectively[4].
These metrics also play a key role in overseeing third-party access, which is discussed in the next section.
Manage Third-Party and Vendor Access
Vendor access introduces unique risks, so it’s crucial to manage it carefully. Use time-limited accounts, enforce multi-factor authentication (MFA), and log all vendor sessions. Maintain an up-to-date inventory of vendors and assess the risks they pose. Tools like Censinet RiskOps™ can help healthcare organizations evaluate third-party risks. This platform allows for secure sharing of cybersecurity and risk data with over 50,000 vendors and products, covering areas like PHI, clinical applications, devices, and supply chains[3].
To further strengthen your program, integrate access reviews into your HR processes. This ensures that access is immediately revoked upon termination and that managers receive consistent training on access management best practices[1].
Conclusion
Implementing least privilege in healthcare IT is an ongoing effort to safeguard patient data and meet compliance requirements. To achieve this, focus on documenting current access, creating a role- and attribute-based model, deploying IAM/PAM controls, securing all endpoints and devices, and conducting regular access reviews with measurable metrics. These steps are essential, especially considering the steep costs and consequences of data breaches.
Healthcare organizations face staggering breach expenses - exceeding $10 million per incident[1][2] - with privileged credentials and excessive access remaining the primary attack vectors. This highlights the importance of proactive and effective access management strategies.
As previously discussed, maintaining least privilege is not a one-time task but a continuous process. Regular access reviews, automated notifications, and HR system integration ensure that controls remain aligned with evolving roles and workflows. Metrics such as excessive permission rates and the number of deactivated accounts provide valuable insights into the program’s effectiveness.
Managing external vendor access is another critical piece of the puzzle. Healthcare’s intricate vendor ecosystem makes third-party access management especially challenging. Tools like Censinet RiskOps™ simplify risk assessments across sensitive areas such as PHI, clinical applications, medical devices, and supply chains[3], ensuring robust access control measures that prioritize patient safety.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health[3]
FAQs
What’s the difference between Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) in healthcare IT?
RBAC, or Role-Based Access Control, assigns permissions based on specific roles, making it easier to manage access for users who have consistent responsibilities. This system works particularly well in healthcare environments where access needs are stable and predictable, such as for administrative or clinical staff.
In contrast, ABAC, or Attribute-Based Access Control, relies on attributes like user details, environmental conditions, or resource characteristics to determine access. This approach enables more precise and adaptable control, making it a better fit for complex healthcare scenarios where access requirements might shift depending on the situation - like during emergencies or when working across various systems.
While both methods strengthen security, ABAC provides more flexibility to meet the changing demands of healthcare IT systems.
What are the best practices for managing and monitoring third-party vendor access in healthcare IT?
To keep third-party vendor access in healthcare IT secure and under control, organizations should rely on a mix of strict access policies, regular audits, and automated monitoring systems. One key approach is to apply the principle of least privilege, which limits vendors to only the access they need to complete their tasks. This minimizes potential security vulnerabilities.
Solutions like Censinet RiskOps™ simplify managing third-party risks by offering continuous assessments, real-time insights into vendor compliance, and tools to track risks tied to patient data, clinical apps, and medical devices. When paired with clear policies and consistent oversight, these strategies help create a safer, more compliant healthcare IT environment.
What are the biggest challenges in maintaining a least privilege model in healthcare IT?
Maintaining a least privilege model in healthcare IT comes with its fair share of challenges. One major obstacle is dealing with complex access controls. Healthcare environments often involve a mix of systems and user roles, making it tricky to ensure everyone has just the right level of access without overcomplicating the process.
Then there’s the balancing act between security and usability. Healthcare professionals need quick and seamless access to do their jobs efficiently. If permissions are too restrictive, it can slow them down and disrupt critical workflows - something no one wants in a high-stakes environment like healthcare.
Another challenge is keeping up with staff compliance. Roles and responsibilities often shift, and ensuring permissions stay current can feel like a never-ending task. On top of that, integrating least privilege tools into existing systems without causing disruptions is no small feat.
Ultimately, overcoming these hurdles requires a thoughtful mix of well-defined policies, reliable tools, and consistent training to ensure everyone understands and adheres to access protocols.


