FDA Cybersecurity Guidance: Impact on Incident Response Plans
Post Summary
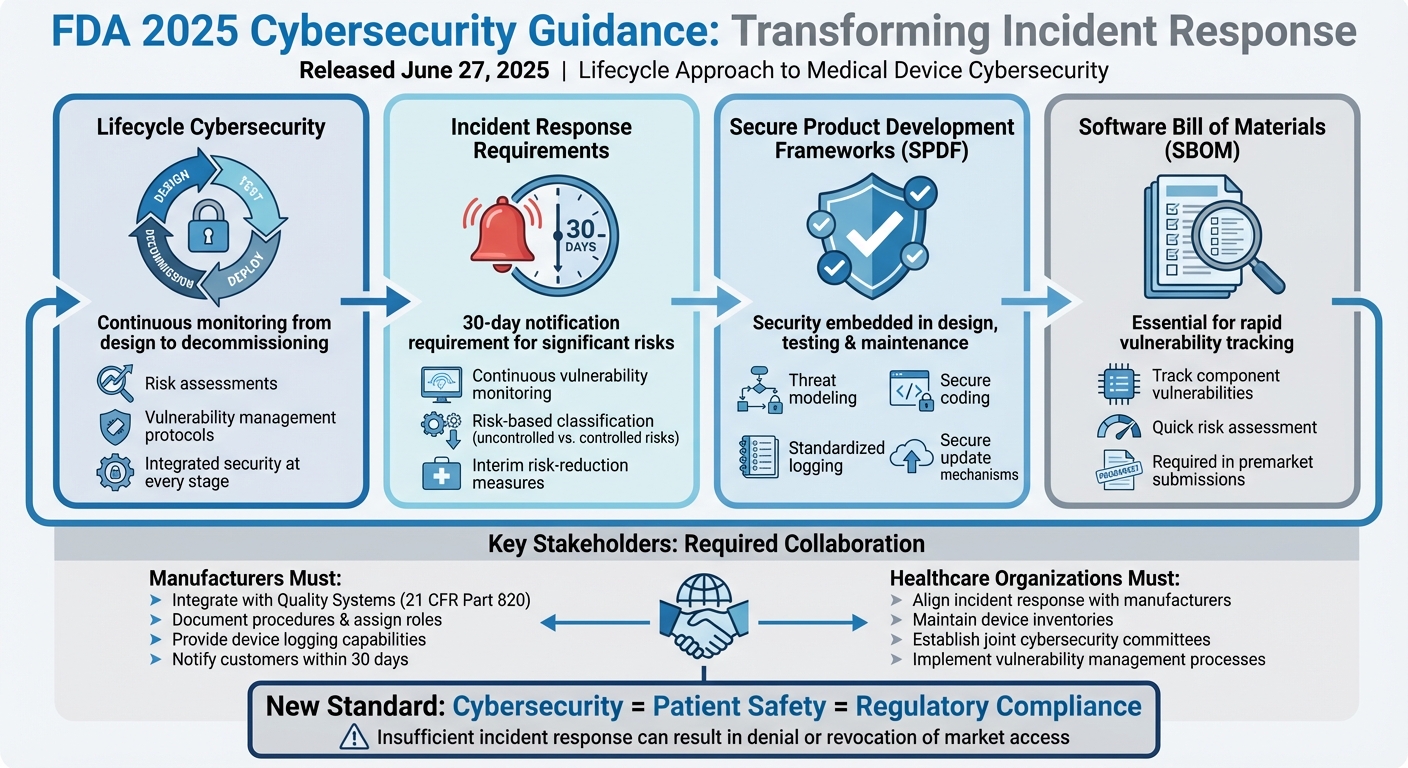
The FDA's updated 2025 cybersecurity guidance has transformed how medical device manufacturers and healthcare organizations handle incident response. Released on June 27, 2025, this framework mandates a lifecycle approach to cybersecurity, tying it directly to patient safety and regulatory compliance. Key changes include:
- Lifecycle Cybersecurity: Continuous monitoring, risk assessments, and clear protocols for managing vulnerabilities from design to decommissioning.
- Incident Response Requirements: Manufacturers must notify customers of significant risks within 30 days and provide interim risk-reduction measures.
- Secure Product Development Frameworks (SPDFs): Embedding security into design, testing, and maintenance to reduce vulnerabilities.
- SBOMs (Software Bill of Materials): Essential for tracking vulnerabilities and assessing device risks quickly.
This guidance redefines incident response as a regulated quality and safety responsibility, requiring detailed procedures, defined roles, and collaboration between manufacturers and healthcare providers. It also emphasizes robust logging, timely communication, and regulatory compliance in handling cybersecurity threats.
Takeaway: To meet these requirements, organizations must integrate cybersecurity into their quality systems, use SBOMs for rapid scoping, and create detailed playbooks that align with FDA expectations. These changes aim to improve preparedness and coordination for addressing cyber risks in healthcare.
FDA 2025 Cybersecurity Guidance: Key Requirements for Medical Device Incident Response
FDA Guidance Components That Affect Incident Response
Lifecycle Cybersecurity Obligations
The FDA's June 27, 2025 guidance reshapes how cybersecurity is approached, making it a continuous responsibility throughout a device's lifecycle[1][5][7]. For manufacturers, this means integrating processes for detecting, assessing, and addressing security issues right from the design phase. During development, incident response workflows must be embedded into design controls and risk management plans. Once devices are deployed in hospitals, continuous monitoring is essential, and clear protocols need to be in place for managing incidents, even as devices near the end of their lifecycle.
Healthcare delivery organizations (HDOs) are equally impacted by this shift. They must align their incident response strategies with the commitments manufacturers make, particularly in areas like patch management, vulnerability disclosures, and device decommissioning. For instance, when a connected medical device - such as an infusion pump or imaging system - faces a security event, both the manufacturer and the hospital need to work together. Their processes must be synchronized to reflect the device's lifecycle stage and the manufacturer’s ongoing support responsibilities.
Incident Response Requirements
The 2025 guidance outlines clear expectations for how manufacturers should manage vulnerabilities after discovery. A key requirement is continuous vulnerability monitoring, which involves tracking threats that could affect the device or its components, including third-party software libraries[1][7]. Manufacturers are expected to use a risk-based framework to classify vulnerabilities. This framework distinguishes between "uncontrolled risks", which demand immediate action, and "controlled risks", which can be addressed during routine maintenance[1].
For significant uncontrolled risks, the FDA advises manufacturers to notify customers within 30 days of discovery, even if a complete fix isn't available yet[1]. During this period, manufacturers should provide hospitals with interim measures, such as network segmentation or disabling vulnerable features, to reduce risks immediately. Incident response plans need to include detailed decision trees and timelines that align with these FDA guidelines. This ensures that response activities meet the "reasonable assurance of cybersecurity" now required under Section 524B[2][4].
Secure Product Development Frameworks (SPDF)
The FDA also emphasizes the importance of a Secure Product Development Framework (SPDF) - a structured approach to embedding security into every phase of device development and maintenance[1][3][7]. By incorporating practices like threat modeling, secure coding, and rigorous security testing into design controls, SPDFs help reduce the number of vulnerabilities that could lead to incidents post-deployment.
From an incident response standpoint, SPDFs provide essential tools. Devices designed with SPDF principles include standardized logging features, secure update mechanisms, and robust access controls - key elements that enable quick detection and resolution of anomalies[1][3]. SPDFs also ensure that patches are thoroughly tested and validated, minimizing the risk of introducing new problems[1][7]. Over time, adopting SPDFs not only decreases the frequency and severity of critical incidents but also provides consistent technical documentation that helps incident responders effectively address emerging threats. These frameworks play a crucial role in shaping how incident response evolves over time.
How FDA Guidance Changes Incident Response Planning
The FDA's June 27, 2025, guidance has reshaped incident response, transforming it from a technical IT task into a regulated quality and patient-safety priority. This new framework compels manufacturers and healthcare delivery organizations to overhaul how they handle security events. Below, we break down the updated expectations for governance, detection, and remediation.
Governance and Accountability
Incident response is now firmly embedded within the Quality System (21 C.F.R. Part 820). This means manufacturers must have documented procedures, clearly defined roles, and management oversight similar to Corrective and Preventive Action (CAPA) processes. Key roles - like a cybersecurity program owner or product security officer - must be assigned to oversee vulnerability monitoring, initiate investigations, and ensure timely corrective actions. These responsibilities will also be scrutinized in premarket submissions and inspections.
Healthcare delivery organizations are expected to establish joint cybersecurity and clinical risk committees. These committees work with manufacturers to manage triage, risk assessments, and remediation efforts. Both manufacturers and healthcare organizations must maintain detailed audit trails of incident-related decisions, document input from various teams, and set clear criteria for escalating issues to the FDA or other regulators.
Incident response now requires collaboration across multiple teams. For manufacturers, this involves product security, quality/regulatory affairs, clinical, IT/OT, legal, and communications teams. Healthcare delivery organizations must include clinical engineering/biomed, information security, IT operations, supply chain/vendor management, and clinical leadership. Together, these teams decide whether to remove devices from service, implement compensating controls, or wait for manufacturer patches. Tools like Censinet RiskOps™ can simplify this process by offering a centralized view of device risk, third-party risk data, SBOMs (Software Bill of Materials), and communication workflows.
Detection and Vulnerability Management
The guidance emphasizes that manufacturers must design devices with robust logging and telemetry capabilities to detect, investigate, and respond to cybersecurity incidents. Devices must log critical events like authentication attempts, configuration changes, updates, and communication failures. These logging capabilities should be outlined in premarket submissions. Incident response playbooks should explain how logs will be accessed and exported during an event, correlated with network or EHR logs, and used for forensic analysis and regulatory review.
Both manufacturers and healthcare organizations are required to establish risk-based vulnerability management processes that meet regulatory expectations. Manufacturers need to define how they assess vulnerability severity and exploitability, connect these assessments to patient safety risks, and classify vulnerabilities as "uncontrolled" (requiring immediate action) or "controlled" (manageable through scheduled updates or other measures).
For healthcare delivery organizations, vulnerability management involves integrating vendor advisories into a risk register, mapping them to the device inventory, and prioritizing actions based on clinical importance, network exposure, and available mitigations. Platforms like Censinet RiskOps™ can streamline this by centralizing SBOMs, advisories, and vulnerability data, mapping them to installed devices, and providing dashboards for managing risks effectively.
Remediation and Communication Processes
Manufacturers must take a risk-based approach to remediation, balancing cybersecurity needs with the clinical availability of devices. Clear criteria should be established to differentiate between routine patches and more extensive design changes. Incident response playbooks should outline remediation strategies, including rapid software or firmware updates for high-risk vulnerabilities, secure configuration changes or feature restrictions when immediate patches are unavailable, and temporary technical or administrative controls to reduce risk.
Manufacturers are required to notify customers within 30 days of identifying significant risks, provide interim risk-reduction measures, and use standardized templates for clear communication. Healthcare delivery organizations should incorporate manufacturer guidance into their runbooks, detailing safe patch deployment windows, necessary testing, fallback procedures, and coordination with clinical leadership to avoid disruptions to critical devices.
Joint exercises between manufacturers and healthcare organizations are highly recommended. These simulations can help validate remediation playbooks, identify weaknesses in change control and rollback procedures, and improve communication channels before a real incident occurs.
sbb-itb-535baee
How to Adjust Your Incident Response Plan
Adapting your incident response plan to meet the FDA's June 27, 2025, guidance involves weaving cybersecurity measures into regulated quality processes, using device inventories and SBOMs (Software Bill of Materials) for quick impact assessments, and creating playbooks that satisfy both operational needs and regulatory requirements. Here’s how manufacturers and healthcare delivery organizations can translate these requirements into actionable steps.
Integrating Incident Response with Quality Systems
The FDA's 2025 guidance emphasizes the need to embed incident response processes into Quality System documentation. This means connecting it with design controls, CAPA (Corrective and Preventive Actions), and complaint handling. When a cybersecurity event occurs, evaluate whether it qualifies as a reportable device malfunction or safety issue under FDA rules. If it does, escalate the event into CAPA for root-cause analysis and broader corrective measures.
Design controls should include features for detecting, logging, and investigating incidents, while risk management files must account for cybersecurity threats. Regular reviews and audits are essential to ensure that these processes provide what the FDA refers to as "reasonable assurance of cybersecurity."
Healthcare organizations, on the other hand, should align their internal incident response protocols with manufacturers' practices. This includes maintaining current device inventories, standardizing incident workflows, and syncing severity classifications. Security bulletins and vulnerability disclosures should be integrated into change-management systems to ensure compliance. Tools like Censinet RiskOps™ can simplify these tasks by centralizing device risk data, SBOMs, and communication workflows.
These quality system integrations lay the foundation for leveraging SBOMs to quickly assess the scope of incidents.
Using SBOMs for Incident Scoping
Manufacturers are now required to include SBOMs in premarket submissions. When a vulnerability is identified, security teams should immediately query the SBOM repository to pinpoint affected devices and prioritize remediation efforts. This allows incident response teams to quickly identify which devices in specific clinical settings are at risk, implement compensating controls (like isolating devices from the network or disabling certain features), and decide which devices require patching or removal.
Platforms like Censinet RiskOps™ can accelerate this process by cross-referencing SBOM data with CVEs (Common Vulnerabilities and Exposures) and live asset information, helping teams make faster, well-documented risk decisions.
To streamline these efforts, incorporate SBOM and inventory checks directly into incident response playbooks. For instance, a standardized "CVE intake" workflow could begin with an SBOM lookup and asset mapping. Additionally, collaborating with healthcare delivery organizations to exchange up-to-date device inventories reduces blind spots during incident scoping. Including SBOM and vulnerability disclosures in procurement processes can also strengthen internal risk management.
Once incident scoping is clearly defined, the next step is to develop playbooks that align with regulatory requirements.
Creating Regulatory-Compliant Playbooks
The FDA’s guidance highlights the importance of playbooks as a bridge between technical response actions and regulatory obligations. Develop device-specific playbooks that categorize incidents by risk level and outline specific response actions and reporting requirements.
Incorporate Medical Device Reporting (MDR) triggers into your processes. For example, incidents that result in death, serious injury, or significant risk must be reported under 21 CFR Part 803. Similarly, actions like disabling a vulnerable feature may need to be reported under 21 CFR Part 806. Document how your organization maintains "reasonable assurance of cybersecurity", including timelines for patches, updates, and vulnerability communications.
Establish clear communication protocols for both internal and external stakeholders. Internally, define roles - such as the PSIRT (Product Security Incident Response Team) lead, CISO, and Regulatory Affairs - and outline approval processes and team responsibilities (e.g., quality, clinical, legal, product teams). Externally, decide when and how to notify the FDA, healthcare delivery organizations, patients (if applicable), and groups like H-ISAC. For healthcare delivery organizations, ensure collaboration among clinical staff, biomedical/clinical engineering, and IT to evaluate risks and determine actions like using alternative devices, applying compensating controls, or removing devices from service.
Regular tabletop exercises can help refine your playbooks. Simulate scenarios such as a remote interface being exploited, a compromised update server, or ransomware impacting device connectivity. Use lessons learned from these exercises to improve CAPA processes and Secure Product Development Framework practices. Platforms like Censinet RiskOps™ can support these efforts by tracking vulnerabilities, remediation progress, and vendor communications, ensuring seamless coordination between manufacturers and healthcare organizations.
Conclusion
Main Takeaways from FDA Guidance
The FDA's 2025 cybersecurity guidance significantly shifts how medical device manufacturers and healthcare delivery organizations handle incident response. This guidance emphasizes a lifecycle approach, embedding incident response into every phase - from design to postmarket monitoring. It links cybersecurity directly to safety and effectiveness, making insufficient incident response not just a technical oversight but a regulatory risk. Under Section 524B, such gaps could lead to denial or revocation of market access for cyber devices.[2][4]
To comply, manufacturers must integrate incident response into their Quality Systems, complete with documented procedures, defined roles, record-keeping, and feedback mechanisms similar to Corrective and Preventive Actions (CAPA). Cybersecurity management plans and Software Bills of Materials (SBOMs) are now essential tools for quickly detecting, assessing, and containing threats.[2][3] The FDA also calls for timely communication, with risk-based vulnerability classifications and prompt notifications to customers.[1][6] Secure Product Development Frameworks are the new standard, ensuring lessons learned from incidents are used to refine design controls, threat modeling, and patching processes.[1][7]
Future Trends and Challenges
As new technologies and care models emerge, incident response becomes more complex. For instance, AI- and ML-enabled devices introduce unique risks - cyber incidents might corrupt models or training data in subtle ways rather than triggering obvious code execution. This demands advanced detection techniques, integrity checks, and tailored response playbooks.[5][7] Similarly, cloud-connected and API-driven ecosystems blur the lines between on-premises hardware, vendor cloud platforms, and third-party services, requiring seamless coordination and shared logging practices.[1][6]
Programs like hospital-at-home and remote monitoring add further challenges by relying on consumer networks and home-based devices. Containment and verification in these environments are tricky, as they often involve patients and caregivers, raising questions about how to coordinate during an incident. Additionally, the increasing use of software updates and feature flags speeds up innovation but also amplifies the risks of flawed releases. To address this, incident response must work hand-in-hand with DevSecOps and Secure Product Development Frameworks, ensuring safe rollbacks and hotfixes when necessary.[1][3] With growing regulatory scrutiny and litigation risks, cybersecurity failures are increasingly viewed as safety issues, making robust, well-documented incident response processes essential to meet FDA expectations.[4][5]
These evolving challenges highlight the need for flexible and forward-thinking solutions that can adapt to the changing landscape of cybersecurity risks.
How Censinet RiskOps™ Can Help

Censinet RiskOps™ offers a powerful way to tackle these challenges. By centralizing cyber risk data, the platform helps healthcare organizations quickly identify affected vendors and devices. It also manages SBOM details tied to specific products and environments, streamlining the process of pinpointing at-risk assets when new vulnerabilities arise.
The platform supports collaborative workflows between healthcare providers and vendors, ensuring that vulnerability notifications, remediation efforts, and compensating controls are tracked in a shared, auditable system. This alignment with Quality System documentation requirements makes compliance more manageable. Additionally, Censinet RiskOps™ provides benchmarking and analytics, allowing organizations to compare their cybersecurity readiness with peers and prioritize investments accordingly.
FAQs
How will the FDA's 2025 cybersecurity guidance impact healthcare incident response plans?
The FDA's 2025 cybersecurity guidance focuses on a forward-thinking approach to handling cybersecurity incidents within healthcare organizations. It highlights the importance of continuous risk management, encourages leveraging advanced technologies like AI for real-time threat detection, and mandates the development of flexible response plans that keep pace with shifting cybersecurity standards.
The goal is to strengthen the defenses of healthcare systems by tackling weaknesses in medical devices, safeguarding patient data, and securing other critical areas. By implementing these strategies, healthcare organizations can better shield sensitive information and uphold patient safety amidst an ever-evolving landscape of threats.
How do SBOMs fit into the FDA’s updated cybersecurity guidelines?
SBOMs, or Software Bill of Materials, are essential for aligning with the FDA's updated cybersecurity guidelines. They serve as a comprehensive list of software components and dependencies within medical devices, offering a clear view of potential vulnerabilities.
With SBOMs, manufacturers and healthcare providers can swiftly pinpoint and address security risks, simplify vulnerability management, and enhance their incident response strategies. This forward-thinking method not only supports FDA compliance but also prioritizes patient safety and the protection of sensitive data.
How can healthcare organizations update their incident response plans to meet the FDA's new cybersecurity guidelines?
To meet the FDA's updated cybersecurity guidelines, healthcare organizations need to work hand-in-hand with medical device manufacturers. This collaboration ensures that incident response plans are in sync. Key steps include setting up clear communication protocols, incorporating the FDA's recommendations into internal processes, and routinely exchanging threat intelligence and response strategies with manufacturers.
Using specialized tools for healthcare cybersecurity and risk management can make this process smoother. These tools help simplify risk assessments and encourage better teamwork, enabling organizations to handle incidents more efficiently while adhering to FDA regulations.


