GDPR Anonymization vs Pseudonymization: Key Differences
Post Summary
Anonymization and pseudonymization are two ways to protect personal data under GDPR, but they differ significantly. Here's the quick takeaway:
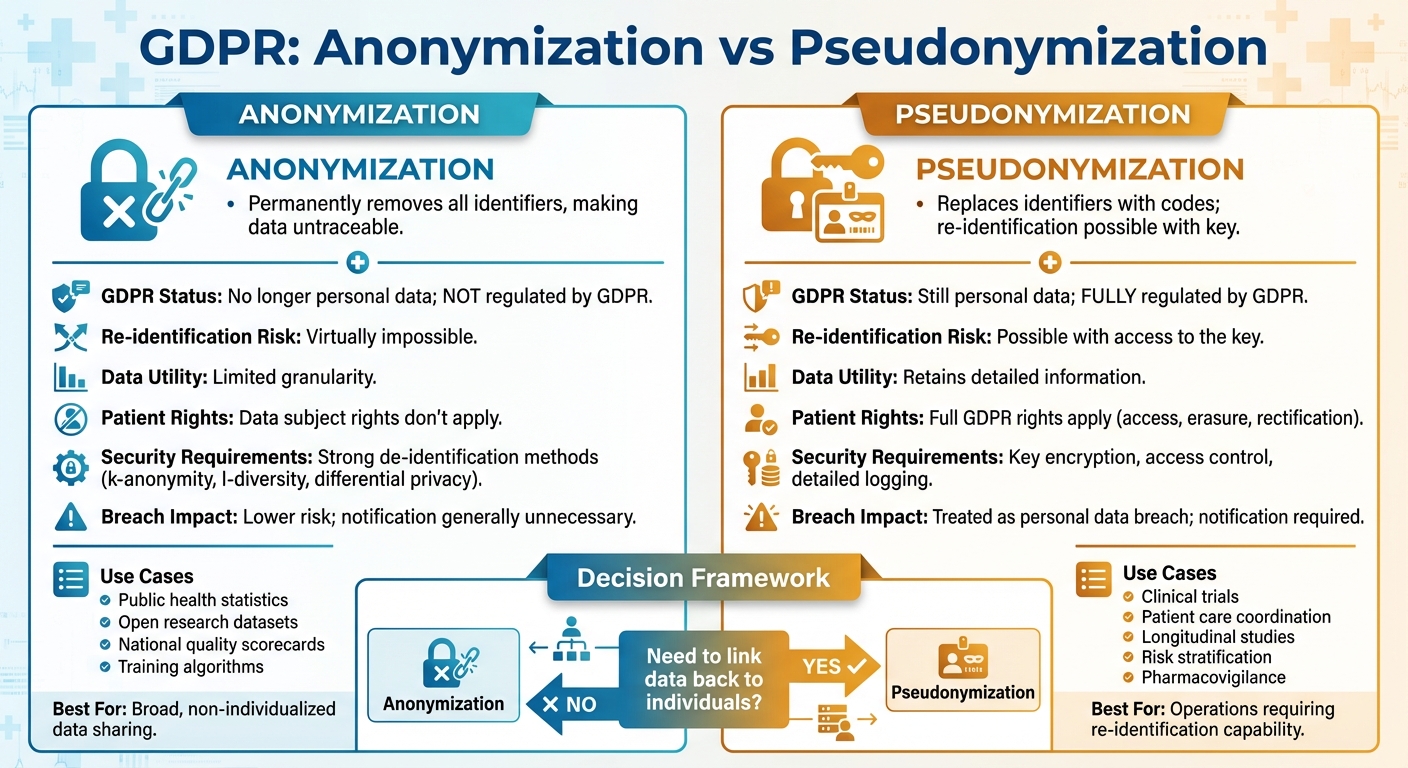
- Anonymization: Permanently removes all identifiers, making data untraceable to individuals. Once anonymized, data is no longer regulated by GDPR.
- Pseudonymization: Replaces identifiers with codes, allowing re-identification if needed. Pseudonymized data is still regulated under GDPR.
Key Points:
- Anonymization is ideal for sharing data in research or public health reporting where individual tracking isn't required.
- Pseudonymization works best for clinical research, patient monitoring, and other scenarios where linking data to individuals is necessary.
- GDPR compliance depends on understanding these methods and applying strong safeguards.
Quick Comparison:
| Aspect | Anonymization | Pseudonymization |
|---|---|---|
| GDPR Status | No longer personal data; not regulated. | Still personal data; fully regulated. |
| Re-identification Risk | Virtually impossible. | Possible with access to the key. |
| Use Cases | Public health stats, research datasets. | Clinical trials, patient care, analytics. |
| Data Utility | Limited granularity. | Retains detailed information. |
| Security Requirements | Strong de-identification methods. | Key encryption, access control. |
Choose anonymization for broad, non-individualized data sharing. Opt for pseudonymization when re-identification might be necessary in healthcare operations.
GDPR Anonymization vs Pseudonymization Comparison Chart
What Are GDPR Anonymization and Pseudonymization?
The GDPR (General Data Protection Regulation) distinguishes between two approaches to protecting personal data: anonymization and pseudonymization. The key difference lies in whether the data can be traced back to an individual. Anonymized data is altered so it can never be linked to a specific person, while pseudonymized data is masked but can still be identified if additional information is available. Let’s break down these concepts, particularly in the context of healthcare data.
Anonymization Under GDPR
Anonymization refers to permanently modifying data so that it can no longer be traced back to an individual - neither directly nor indirectly. According to GDPR Recital 26 [4], data protection rules don’t apply to information that cannot identify a natural person. This means that once data is genuinely anonymized - using techniques like removing, generalizing, or aggregating identifiers - it is no longer subject to GDPR regulations.
However, achieving true anonymization is no small feat. Regulators acknowledge the difficulty of making data completely untraceable. As a result, they recommend a risk-based approach, where organizations work to minimize the chances of re-identification as much as possible.
Pseudonymization Under GDPR
Pseudonymization, as defined in Article 4(5) of the GDPR [4], involves processing data in a way that separates identifying details from the rest of the dataset. For example, names or Social Security numbers might be replaced with unique codes, which are stored elsewhere. While this makes the data less directly identifiable, the possibility of re-identification remains if someone has access to the "key" that links the codes back to individuals. Because of this, pseudonymized data is still regulated under GDPR and requires organizations to comply with its rules, such as having a lawful basis for processing and respecting individuals' rights.
For U.S. healthcare organizations handling data from EU patients, this distinction is critical. Even if pseudonymized records are used - for instance, in clinical trials or research - they must still meet GDPR requirements, as re-identification is technically possible if another party holds the necessary mapping information.
How Anonymization Works in Healthcare
Main Features of Anonymization
Anonymization permanently modifies patient data so individuals cannot be identified - even by the entity collecting the data. Under GDPR, data is considered anonymized only if re-identification is impossible using any methods that are reasonably accessible, considering current technology, costs, and time constraints [1]. The defining feature of anonymization is its irreversibility: once data is anonymized, it is no longer subject to GDPR regulations.
Healthcare organizations rely on various techniques to achieve anonymization, such as:
- Data suppression: Removing key identifiers like names or Social Security numbers.
- Generalization: Replacing specific details with broader categories, such as using age ranges instead of exact ages or partial ZIP codes instead of full addresses.
- Aggregation: Summarizing data into groups, like reporting averages or totals instead of individual records.
- Perturbation: Slightly altering data values to prevent exact matches.
The European Data Protection Supervisor emphasizes that anonymization is a process shaped by context and risk. Organizations must evaluate whether any realistic actor - like a disgruntled employee, an insurance company, or a data broker - could combine the anonymized dataset with other information to re-identify individuals. If the data meets this strict standard, it is exempt from GDPR, reducing compliance burdens while ensuring the data cannot be traced back to specific patients.
Despite its benefits, anonymization poses challenges, particularly in scenarios requiring individual monitoring.
Limitations for Healthcare Data
While anonymization effectively removes re-identification risks and ensures compliance, it also significantly limits clinical applications. Its irreversible nature means that anonymized records cannot be linked back to individual patients, which complicates essential healthcare functions like monitoring chronic diseases, coordinating care across providers, or conducting safety follow-ups. For instance, if a medication recall occurs or a new adverse event pattern emerges, anonymized data cannot be used to contact affected patients.
This makes anonymized data unsuitable for patient-specific tasks, such as care coordination, quality improvement initiatives, or value-based care efforts. Instead, anonymized data is most useful for broader analyses, such as:
- Evaluating population health trends.
- Identifying regional disease patterns.
- Benchmarking hospital performance.
- Supporting public health reporting.
However, for research that requires tracking individual patient trajectories - like studies on medication adherence or developing precision medicine models - the inability to link data to specific individuals limits its usefulness. As a result, healthcare organizations typically reserve anonymization for secondary purposes, such as epidemiological studies, external quality metric reporting, and data sharing with academic researchers or policymakers, where individual identities are not needed.
How Pseudonymization Works in Healthcare
Main Features of Pseudonymization
Pseudonymization replaces direct identifiers - like names, Social Security numbers, medical record numbers, and full addresses - with codes or tokens. These codes are stored securely in an encrypted, access-controlled system, ensuring that only authorized personnel can re-identify the data when it's medically necessary. According to GDPR Article 4(5), this process ensures patient data cannot be linked to an individual without accessing additional, separately stored information under strict control [1][2].
Unlike anonymization, which permanently removes all links to a patient's identity, pseudonymization maintains the ability to reconnect the data to the individual when needed. This flexibility is vital in healthcare, where re-identification may occasionally be required for patient care. For example, a cardiology outcomes registry might assign each patient a unique study ID. This allows all related encounters and tests to share the same pseudonym, while the link to the patient's actual medical record remains securely accessible to authorized staff.
Techniques like tokenization, hashing, and deterministic coding are commonly used in pseudonymization. Importantly, clinical details - such as diagnoses, medications, dosages, lab results, and imaging findings - remain intact, which is essential for meaningful analysis and research.
The GDPR explicitly encourages pseudonymization in Recitals 28, 29, and 78 as part of a privacy-by-design approach. This method reduces risks to patient privacy while enabling valuable secondary uses of health data [4][3].
Advantages for Healthcare Operations
Pseudonymization offers significant benefits for healthcare organizations, particularly in research and clinical trials, while ensuring compliance with GDPR. Researchers can track pseudonymous patient cohorts over time to study outcomes like survival rates, medication adherence, and treatment effectiveness - all without exposing direct identifiers. In randomized clinical trials, sponsors and analysts use pseudonymous subject IDs, while only the investigative site retains the ability to re-identify participants if safety concerns or regulatory audits arise.
This method is especially helpful for real-world evidence registries. National or multi-center registries, such as those in oncology or cardiology, can use pseudonymized IDs to combine outcomes data from multiple hospitals. This allows for GDPR-compliant data sharing across borders while preserving the ability to update records or honor patient withdrawal requests. Medical imaging platforms have also adopted automated systems to replace DICOM identifiers at the source, enabling teleradiology and collaborative research across institutions.
Pseudonymization also facilitates ongoing patient care coordination without revealing full identities. For example, care coordinators or external analytics teams can work with pseudonymous IDs paired with clinical and utilization data, while treating physicians retain access to full identities through the electronic health record. Health information exchanges and accountable care organizations can share pseudonymized datasets for purposes like risk stratification and quality measurement. If an analytics model flags a high-risk patient, only an authorized clinical team can re-identify the individual for timely intervention. These capabilities not only enhance clinical research but also strengthen secure and efficient patient care coordination.
sbb-itb-535baee
Anonymization vs Pseudonymization: Side-by-Side Comparison
Comparison Table
In U.S. healthcare, navigating GDPR compliance, security, and operational needs often hinges on understanding the differences between anonymization and pseudonymization. The table below highlights their key distinctions:
| Dimension | Anonymization | Pseudonymization |
|---|---|---|
| Legal Status Under GDPR | No longer classified as personal data if re-identification is not reasonably possible, placing it outside GDPR's scope. | Still considered personal data since re-identification is possible with additional information (like a key or mapping table), meaning GDPR rules fully apply. |
| Re-identification Risk | Designed to make re-identification virtually impossible using current methods. | Reduces risk but doesn't eliminate it; re-identification is possible if security measures fail. |
| Typical Healthcare Use Cases | Commonly used for aggregate reporting, public health stats, open datasets, national quality scorecards, and training algorithms on non-traceable data. | Ideal for clinical research, EHR analytics, longitudinal studies, outcomes tracking, pharmacovigilance, risk stratification, and population health management. |
| Data Utility | Offers limited granularity, which can restrict patient-level analysis, longitudinal tracking, and detailed subgroup studies due to data suppression or generalization. | Retains high utility by allowing record linkage, individual-level statistics, and multi-time-point analysis, which are crucial for research and coordinated care. |
| Impact on Patient Rights & Consent | Reduces regulatory obligations since data subject rights (like access, erasure, and rectification) typically don’t apply. | Full GDPR rights remain, requiring organizations to honor access, erasure, and rectification requests. |
| Security & Control Requirements | Demands strong de-identification techniques - such as k-anonymity, l-diversity, and differential privacy - along with ongoing risk assessments to ensure anonymity over time. | Requires strict control over re-identification keys, including encryption, access controls, and detailed logging. |
| Incident Impact if Breached | Lower regulatory and reputational risk as the data isn’t considered personal; breach notification is generally unnecessary. | Treated as a personal data breach under GDPR, triggering notification, investigation, and remediation requirements. Attackers without the key face limited identification capability. |
| Examples in U.S. Healthcare | Used in multi-institution research datasets for open science or national quality scorecards. | Applied to pseudonymized EHR data sent to analytics vendors, internal risk models, or securely tied to patients via study IDs. |
This comparison underscores the core GDPR differences, helping organizations make informed decisions about risk management and compliance strategies.
Anonymization removes data from GDPR's reach, while pseudonymization keeps it regulated due to re-identification potential. Tools like Censinet RiskOps™ can assist by cataloging datasets, managing re-identification controls, and benchmarking cybersecurity across partners. Choosing the right approach depends on balancing risk with operational goals.
How to Choose Between Anonymization and Pseudonymization
Factors to Consider
Deciding between anonymization and pseudonymization starts with understanding how the data will be used. If you're dealing with patient care, clinical research, or safety monitoring - where linking records is essential - pseudonymization is the better fit. On the other hand, for public reporting or sharing data externally without the need for follow-up, full anonymization is the way to go. This aligns with earlier discussions about the importance of re-identification in clinical contexts.
Another key factor is your organization's risk tolerance. A breach involving pseudonymized data can trigger GDPR and U.S. breach notification requirements, while fully anonymized data minimizes regulatory and legal risks.
The level of detail you need from the data also matters. Anonymization often reduces data precision by coarsening dates, grouping age ranges, or aggregating diagnoses. While this protects privacy, it can limit advanced analytics or AI applications. Pseudonymization, however, keeps detailed information - like exact timestamps, rare disease codes, and longitudinal lab results - intact, making it a better choice for in-depth clinical or research insights. For cross-border data transfers from the EU to the U.S., pseudonymization paired with encryption and contractual safeguards can help meet compliance requirements. Meanwhile, anonymized data, since it falls outside GDPR transfer rules, can simplify these processes.
These decisions naturally lead to the need for robust operational safeguards.
Managing Risks with Censinet
Once you've chosen an approach, it's crucial to implement risk management measures tailored to your decision. For pseudonymization, this means securely storing re-identification keys with encryption, restricting access through role-based controls, and strictly limiting re-identification to specific circumstances, such as medical necessity or Institutional Review Board (IRB) approval. Additionally, all re-identification events should be logged for accountability. For anonymization, you’ll need to apply strong de-identification techniques and regularly assess risks to ensure the data remains non-identifiable, even as external data sources evolve.
To support these efforts, Censinet RiskOps™ offers tools to streamline and scale these safeguards. The platform helps healthcare organizations evaluate vendors' practices around pseudonymization and anonymization, including tokenization, encryption protocols, key management, and incident response plans. It ensures alignment with regulatory frameworks like GDPR and HIPAA, as well as cross-border transfer rules. By cataloging datasets, managing re-identification controls, and monitoring cybersecurity practices across partners, Censinet RiskOps™ provides a centralized solution for maintaining compliance and adapting to changing conditions. Whether you opt for pseudonymization to retain operational flexibility or anonymization for broader data sharing, this structured approach ensures your organization meets the technical and organizational safeguards required under GDPR.
Conclusion
Choosing between anonymization and pseudonymization in healthcare data governance comes down to a critical distinction: anonymization permanently removes data from the scope of GDPR, while pseudonymization, though it masks identifiers, remains subject to GDPR regulations. For U.S. healthcare organizations managing EU patient data, this difference significantly shapes how you approach your data governance framework.
Anonymization works well for large-scale research and public reporting but limits follow-ups and individualized care. On the other hand, pseudonymization retains clinical utility by enabling longitudinal tracking and re-identification when medically necessary. However, it also demands robust controls, including encryption, strict access management, and comprehensive audit trails. While anonymized data can be managed under internal ethics and security standards, pseudonymized data must be treated as regulated personal information, requiring readiness for breach notifications and compliance with GDPR mandates.
To navigate these complexities, consider this streamlined strategy: use pseudonymization for care delivery, quality improvement, and internal analytics where patient-level tracking is essential. Reserve anonymization for large-scale research, public reporting, and external data sharing where re-identification is unnecessary or prohibited. For every data initiative, evaluate whether re-identification is required. If it is, ensure pseudonymization keys are tightly controlled. If not, implement robust anonymization practices and document their application.
Specialized risk management platforms like Censinet RiskOps™ can simplify this process by standardizing how healthcare organizations assess third-party vendors' anonymization and pseudonymization practices. These platforms help ensure that controls for PHI and pseudonymized data meet both GDPR and U.S. healthcare security standards. By centralizing cybersecurity benchmarks and vendor risk assessments, privacy officers and CISOs can make informed decisions about when anonymized datasets are safe to share and when stricter controls are necessary for pseudonymized data.
Incorporating anonymization and pseudonymization into your data governance strategy as deliberate, policy-driven decisions - rather than reactive technical measures - ensures alignment with your clinical, research, and operational goals. This systematic approach allows U.S.-based healthcare organizations to uphold patient privacy, comply with regulatory requirements, and maximize the value of healthcare data.
FAQs
What steps can organizations take to ensure data stays anonymized over time?
To keep data anonymized over time, organizations need to implement strong measures like regular audits and continuous monitoring. These steps help identify and reduce the risk of re-identification. It's also crucial to update anonymization methods regularly to address new technologies and emerging threats, ensuring compliance with GDPR.
Leveraging specialized tools designed for healthcare data management can make this process easier. These tools can streamline risk assessments, highlight vulnerabilities, and support consistent adherence to privacy regulations. Beyond technology, promoting accountability and providing staff with training on best practices for data protection adds another layer of security for anonymized information.
What are the potential privacy risks of pseudonymization under GDPR?
Pseudonymization under GDPR helps lower privacy risks by disguising personal data, but it doesn’t completely remove them. One major issue is re-identification - this can happen when pseudonymized data is matched with other datasets or information, potentially revealing sensitive details and compromising privacy.
To address these risks, organizations working with pseudonymized data should adopt strong protections. This includes enforcing strict access controls and conducting regular risk assessments to minimize the chances of unauthorized data connections or misuse.
When should healthcare organizations use pseudonymization instead of anonymization?
Healthcare organizations should consider pseudonymization when it's necessary to keep the option of re-identifying data for specific purposes, like clinical research, patient follow-ups, or fixing errors in records. This method allows data to stay identifiable under strict conditions, while still reducing privacy risks.
This approach is especially helpful in situations where some level of traceability is crucial, but fully anonymizing the data would interfere with operational or research needs. By using pseudonymization, organizations can find a middle ground between maintaining data usability and protecting privacy, meeting GDPR standards while supporting essential healthcare activities.


