Healthcare Metaverse Vendors: Risk Management for Virtual Medical Environments
Post Summary
The healthcare metaverse is reshaping patient care by integrating VR, AR, AI, and blockchain into virtual medical spaces. While 75% of providers already use these technologies, they bring major risks: sensitive data collection, cybersecurity threats, and regulatory challenges. Key concerns include identity spoofing, privacy breaches, and device vulnerabilities like hacking or immersive attacks. To address these, healthcare organizations need strong vendor risk assessments using frameworks like NIST and STRIDE. Tools like Censinet RiskOps™ streamline these processes with automation, AI, and compliance tracking to protect patient data and maintain trust in virtual healthcare environments.
Cybersecurity Risks from Metaverse Vendors
Healthcare organizations working with metaverse vendors encounter cybersecurity risks that go beyond traditional IT concerns. The immersive nature of virtual medical environments and the vast amounts of sensitive data they collect create vulnerabilities that threaten both patient safety and data security. Understanding these risks is a key step in developing strong defenses. Below, we explore the major areas of concern.
Identity and Access Management Challenges
Verifying identity in virtual medical environments presents unique challenges. The metaverse's decentralized structure and the use of multiple virtual avatars make it hard to confirm who is accessing sensitive medical data. This opens the door to identity spoofing and unauthorized access through fake identities or account takeovers.
The risks are amplified by the ability of VR motion data to identify users with alarming precision. Studies show that just 100 seconds of motion data can identify a user with 94.33% accuracy from a pool of over 50,000 individuals [6]. This data can also reveal personal details like height, wingspan, age, gender, country of origin, and even mental or physical disabilities [6]. Solving these identity challenges is essential to secure virtual medical environments.
Data Privacy and Information Disclosure Threats
AR/VR devices gather vast amounts of personal data using sensors and tracking technologies [5][6]. If vendors fail to protect this data, healthcare organizations could face severe privacy breaches and legal repercussions.
One of the most concerning risks is deanonymization and profiling. As Sikandar Ali et al. explain:
Metaverse systems have greater potential for sensitive data collection than conventional systems, which poses a serious threat to user privacy [4].
When data from various sources is combined in virtual medical environments, it can lead to detailed profiling. This profiling could expose sensitive health conditions, treatment histories, and behavioral patterns. Managing these risks is critical to safeguarding user privacy.
AR/VR and Device-Specific Vulnerabilities
AR/VR devices introduce new avenues for cyberattacks. These platforms are vulnerable to hacking, malware, and other threats, especially since users often input personal information during setup and operation [7][3]. Such vulnerabilities provide entry points for bad actors to compromise data and disrupt device functionality.
Immersive attacks are a particularly concerning threat. In a "chaperone attack", hackers manipulate device outputs to trick users into colliding with physical objects, potentially causing injuries during medical procedures or therapy. "Overlay attacks" can display harmful or distressing content to patients, triggering psychological distress or cybersickness [6]. Denial-of-service attacks, meanwhile, can render AR/VR devices inoperable, disrupting essential healthcare operations and directly impacting patient care [3][6]. Addressing these vulnerabilities is essential to protect both patients and medical systems in virtual environments.
Vendor Risk Assessment Frameworks for the Metaverse
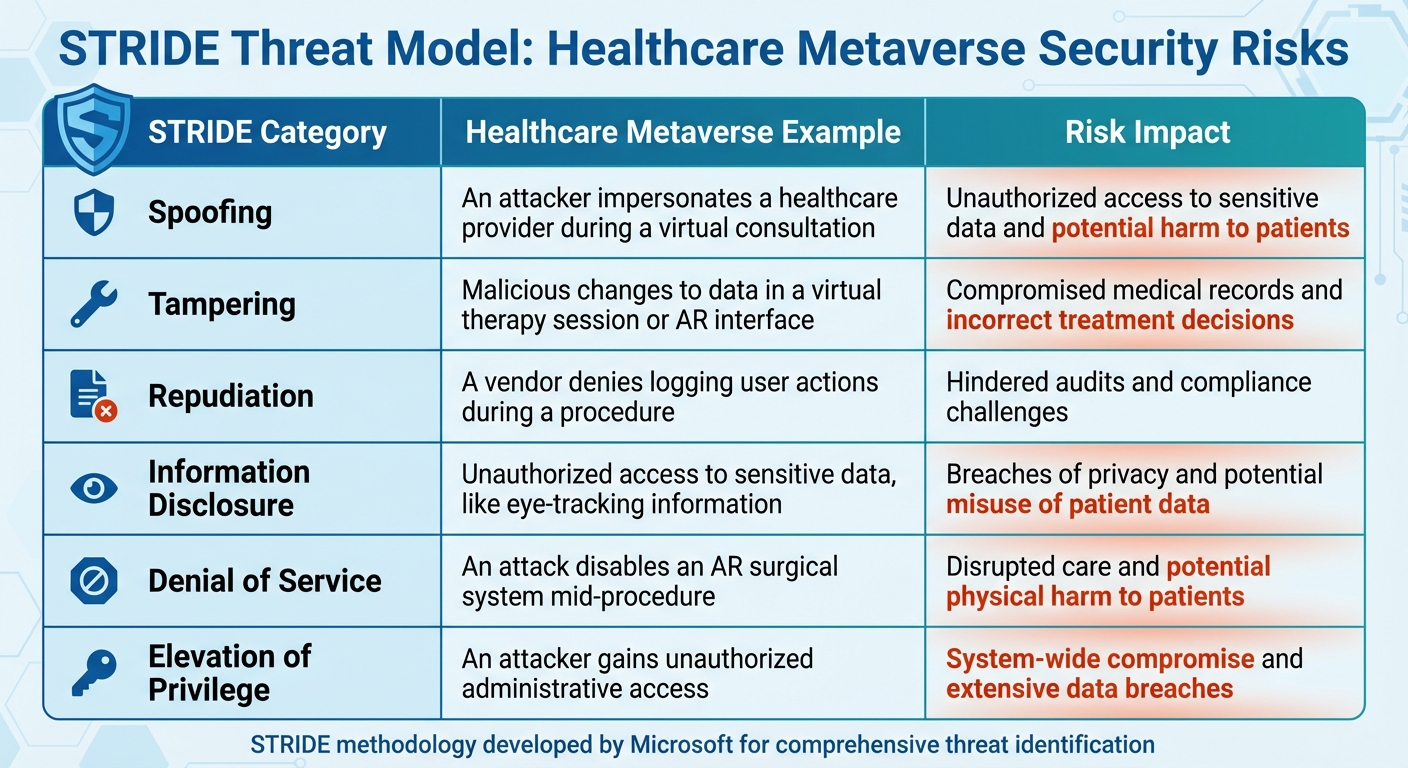
STRIDE Threat Model for Healthcare Metaverse Security Risks
Healthcare organizations face unique challenges when it comes to evaluating vendors operating in the metaverse. Virtual environments demand a structured approach to ensure vendor practices align with healthcare's stringent compliance requirements. A well-designed assessment framework not only identifies potential vulnerabilities before they escalate but also ensures vendors meet the industry's high standards for data security and patient privacy.
Applying the NIST Cybersecurity Framework

The NIST Cybersecurity Framework provides a solid foundation for assessing risks in the metaverse. Its core functions - Identify, Protect, Detect, Respond, and Recover - guide organizations through a comprehensive evaluation process:
- Identify: Start by cataloging all vendor relationships and understanding the flow of sensitive data, such as patient health information, within virtual environments.
- Protect: Ensure vendors implement robust security measures, including multi-factor authentication, biometric verification, and advanced encryption. Vendors should also provide detailed privacy controls, allowing users to decide what data is collected, how it's used, and who can access it. Regular ethical hacking tests and security audits should be a standard part of vendor protocols.
- Detect: Vendors must have systems in place to continuously monitor for breaches or suspicious activity.
- Respond and Recover: Evaluate how vendors address vulnerabilities and their ability to restore services quickly after disruptions.
This structured approach ensures that vendors are equipped to handle the unique challenges of the metaverse while safeguarding patient data and maintaining operational integrity.
Using STRIDE for Threat Modeling in Virtual Environments
The STRIDE methodology, developed by Microsoft, offers a detailed way to identify specific threats in the metaverse. This model categorizes risks into six areas: Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, and Elevation of Privilege. Here's how these threats might manifest in a healthcare metaverse setting:
| STRIDE Category | Healthcare Metaverse Example | Risk Impact |
|---|---|---|
| Spoofing | An attacker impersonates a healthcare provider during a virtual consultation. | Unauthorized access to sensitive data and potential harm to patients. |
| Tampering | Malicious changes to data in a virtual therapy session or AR interface. | Compromised medical records and incorrect treatment decisions. |
| Repudiation | A vendor denies logging user actions during a procedure. | Hindered audits and compliance challenges. |
| Information Disclosure | Unauthorized access to sensitive data, like eye-tracking information. | Breaches of privacy and potential misuse of patient data. |
| Denial of Service | An attack disables an AR surgical system mid-procedure. | Disrupted care and potential physical harm to patients. |
| Elevation of Privilege | An attacker gains unauthorized administrative access. | System-wide compromise and extensive data breaches. |
By mapping these threat categories against a vendor's security measures, healthcare organizations can better anticipate and address the unique risks of immersive virtual environments.
Evaluating Compliance and Third-Party Risk
Compliance in the metaverse extends beyond traditional regulations like HIPAA. Vendors operating in these virtual spaces must navigate challenges posed by jurisdictional ambiguity and rapidly evolving technology. This often results in gaps between existing laws and the realities of metaverse operations.
Third-party and fourth-party relationships add another layer of complexity. For instance, a metaverse vendor collaborating with AR/VR hardware providers or cloud services significantly broadens the potential attack surface. To address these risks, organizations should:
- Work with legal experts to establish clear contracts defining data ownership, breach notification responsibilities, and liability.
- Require vendors to conduct regular third-party audits, penetration tests, and maintain documented incident response plans.
Additionally, staying informed about emerging standards and regulations specific to virtual environments is critical. This ensures healthcare organizations can protect patient data and maintain trust, even as the metaverse evolves. By integrating vendor risk assessments into broader cybersecurity strategies, healthcare providers can uphold patient safety and data integrity in these cutting-edge spaces.
Mitigation Strategies with Censinet RiskOps™
Healthcare organizations face constant challenges in managing vendor risks, especially as digital health solutions grow more complex. Censinet RiskOps™ offers a powerful platform designed to simplify third-party risk assessments and strengthen overall risk management processes.
Simplifying Vendor Risk Assessments
Traditional vendor assessments often slow things down and leave room for vulnerabilities. Censinet RiskOps™ tackles these issues with automated workflows and AI-driven tools. Features like Censinet AITM and Connect™ automate tedious tasks, such as filling out security questionnaires, and consolidate risk data into one central hub. This makes it faster to evaluate vendors and pinpoint critical risks. The platform also provides a central dashboard that visualizes risk data across all vendor relationships, helping organizations spot trends and prioritize fixes. These efficiencies are crucial for safeguarding patient data and securing connected devices.
Protecting Patient Data and Devices
Censinet RiskOps™ ensures healthcare providers can monitor vendor security measures effectively. The platform checks for compliance with key standards, like encryption, access controls, and data retention policies. Customizable frameworks allow organizations to set their own risk thresholds, triggering alerts when a vendor falls short. This approach helps maintain compliance while addressing potential vulnerabilities proactively.
Leveraging AI for Smarter Risk Management
Censinet takes risk management a step further by integrating AI to enhance oversight. With Censinet AITM, the platform automates the assessment process while still involving human expertise. AI tools quickly generate risk summary reports based on collected data, allowing healthcare organizations to evaluate vendors more efficiently. Meanwhile, the platform’s human-in-the-loop approach ensures that risk teams stay in control, with configurable rules and review processes.
Critical findings are routed to the right stakeholders through advanced workflows, ensuring timely action and approvals. This balanced approach enables healthcare organizations to scale their risk management efforts without compromising on oversight or compliance. By combining automation with human judgment, Censinet RiskOps™ helps healthcare providers stay ahead of vendor risks in a rapidly evolving digital landscape.
sbb-itb-535baee
Implementing Censinet for Metaverse Risk Management
As healthcare organizations explore partnerships within the metaverse, having a clear strategy for managing risks is essential. Censinet RiskOps™ provides adaptable solutions that cater to different organizational needs and resource levels, addressing the specific vulnerabilities found in virtual medical environments. Let’s break down the deployment models, collaborative frameworks, and AI governance tools that make Censinet a strong choice for managing risks in this evolving space.
Deploying a Customized Censinet Plan
Censinet offers three deployment options to suit varying organizational structures:
- Platform Model: Ideal if your organization has a dedicated cybersecurity team capable of managing daily operations. This option provides full internal control over risk management processes.
- Hybrid Mix: Perfect for organizations that want a balance of internal management and external expertise. Your team handles routine risk assessments, while Censinet experts step in to address more complex challenges, such as vulnerabilities in AR/VR devices and virtual data flows.
- Managed Services: A fully outsourced approach where Censinet oversees everything from assessments to monitoring and reporting, freeing up internal resources entirely.
These tailored options ensure healthcare organizations can implement a risk management strategy that aligns with their capabilities and priorities.
Building Collaborative Risk Networks
The metaverse introduces unique challenges that require collective efforts from platforms, users, and regulatory bodies to establish secure practices [2]. Censinet’s collaborative risk network capabilities enable healthcare organizations to work seamlessly with metaverse vendors. Using Censinet Connect™, organizations can streamline communication, ensuring that security and compliance requirements are clearly defined and upheld. This approach promotes accountability across the virtual healthcare ecosystem, reinforcing the importance of secure and transparent interactions between stakeholders.
AI Governance with Human Oversight
Effective vendor risk management in virtual environments demands both automation and human expertise. Censinet AITM handles routine tasks, while human experts validate critical findings to maintain accuracy. Risk teams set clear boundaries between automated processes and those requiring manual review. For example, issues like health data governance in virtual environments [1][8] are flagged and routed to designated stakeholders for further evaluation. A centralized AI risk dashboard provides real-time insights, giving leadership a clear view of vendor risks while ensuring complex challenges are addressed with human judgment.
Conclusion
Virtual healthcare environments bring exciting possibilities, but they also introduce a host of cybersecurity challenges that demand a nimble approach to risk management. The healthcare metaverse, in particular, presents new risks like digital identity theft, massive data collection, and unclear legal guidelines surrounding health data ownership. These issues push healthcare organizations to rethink and adapt their traditional security strategies.
Earlier, we discussed how Censinet RiskOps™ provides a structured framework that aligns with best practices for vendor risk assessments. Its adaptable deployment options allow healthcare providers to address vulnerabilities unique to the metaverse. By combining automated workflows with expert human oversight, the platform ensures that critical risks are carefully reviewed and managed.
Building secure virtual healthcare ecosystems requires collaboration across multiple stakeholders - technology providers, regulators, and healthcare organizations. Censinet Connect™ supports this effort by streamlining communication and ensuring accountability within the vendor network.
As the metaverse continues to evolve, healthcare organizations must prioritize patient safety and regulatory compliance without stifling innovation. This means implementing strong digital authentication methods, precise data controls, and advanced cybersecurity measures. With the right tools and strategies in place, healthcare providers can confidently engage with the metaverse, protecting patient data and maintaining the trust that is central to delivering quality care. These strategies reinforce the importance of integrating frameworks and fostering collaboration across the vendor landscape.
FAQs
What are the main cybersecurity risks when working with healthcare metaverse vendors?
Healthcare metaverse vendors encounter a variety of serious cybersecurity threats that could jeopardize virtual medical environments. These threats include data breaches, identity theft, hacking attempts, malware infections, and unauthorized access to confidential patient information.
Because healthcare data is extremely sensitive, these risks carry severe repercussions. They can undermine patient privacy, result in violations of regulatory requirements, and cause financial damage. To address these challenges, it's crucial to establish strong security protocols, perform routine risk assessments, and ensure all vendors strictly follow compliance regulations.
What steps can healthcare organizations take to manage vendor risks in virtual medical environments?
Healthcare organizations can tackle vendor risks in virtual medical settings by implementing a solid risk management approach. This involves consistently monitoring cybersecurity protocols, analyzing the root causes of any incidents, and maintaining ongoing oversight of vendor operations.
A crucial part of this process is ensuring vendors comply with HIPAA and other applicable regulations. Organizations should confirm vendor credentials and evaluate the security measures they employ, such as multi-factor authentication and encryption, to protect digital identities. Developing clear data governance policies with vendors and performing regular security audits are additional steps that can bolster these efforts. Open collaboration and proactive communication with vendors play a key role in safeguarding the integrity of virtual healthcare systems.
How does AI help manage risks in virtual healthcare environments?
AI has become a key player in reducing risks in virtual healthcare settings, particularly when it comes to data security and cyber defenses. By using advanced anomaly detection, AI can spot unusual activity, helping to identify potential threats early and minimize damage. It also aids in making ethical decisions by leveraging frameworks that align with established healthcare standards.
Another important contribution of AI is its role in predictive analytics. This technology helps organizations foresee potential risks and address them before they grow into bigger issues. It also ensures compliance with regulatory requirements and protects sensitive patient information, creating a safer and more reliable environment for virtual healthcare.


