Healthcare Payroll and HR Vendor Risk Management: Employee Data Protection
Post Summary
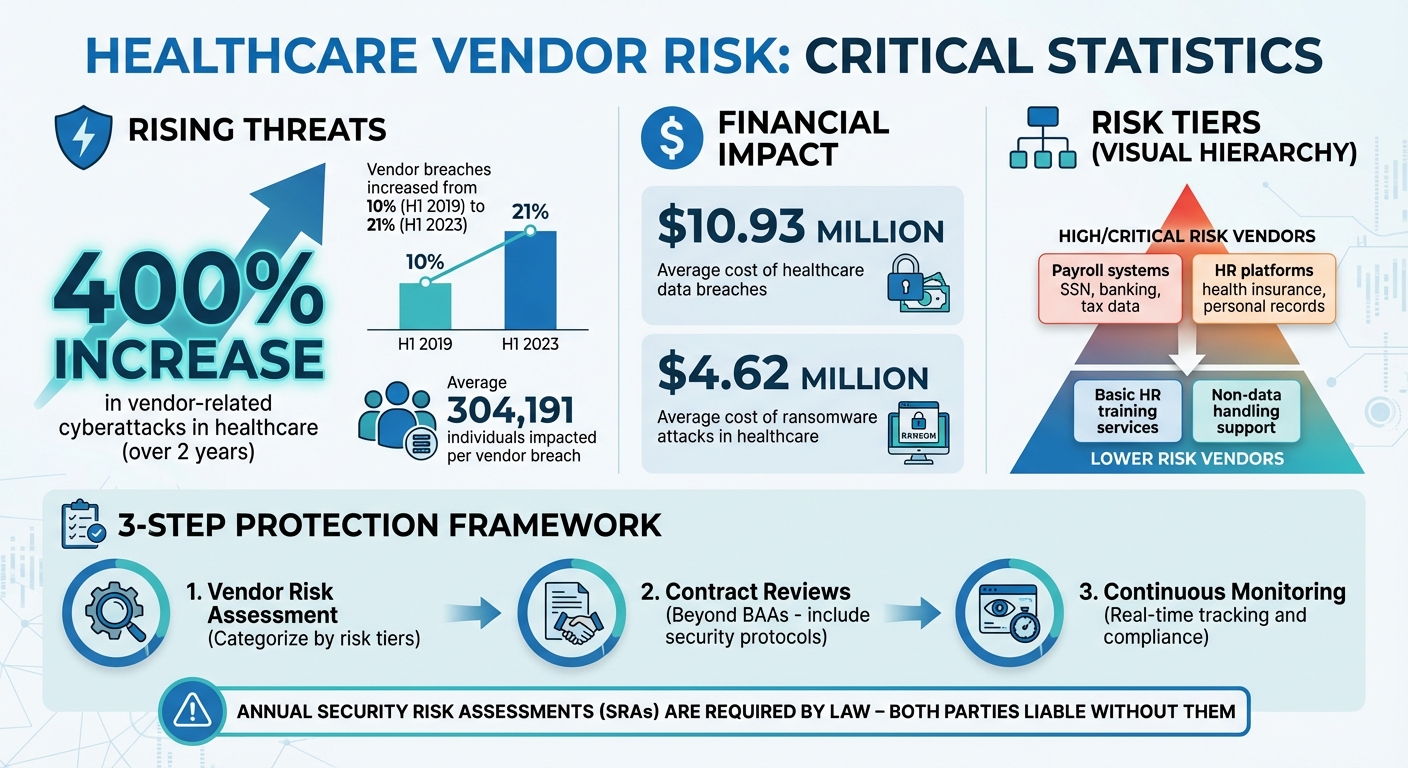
Outsourcing payroll and HR functions in healthcare comes with serious risks to employee data security. Vendors gain access to sensitive information like Social Security numbers, banking details, and health insurance data - making them prime targets for cyberattacks. Alarmingly, vendor-related cyberattacks in healthcare have surged by 400% in just two years, exposing organizations to breaches, fines, and reputational damage.
Key Takeaways:
- Relying on a signed Business Associate Agreement (BAA) is not enough to ensure data protection.
- Poor vendor management is a leading cause of data breaches in healthcare.
- Risks include ransomware attacks, weak encryption, and regulatory non-compliance.
- Annual Security Risk Assessments (SRAs) are required by law but often overlooked.
Solutions:
- Vendor Risk Assessment: Categorize vendors by risk tiers (e.g., payroll vendors as high-risk) and evaluate their security measures.
- Contract Reviews: Go beyond BAAs - include detailed security protocols, breach timelines, and subcontractor responsibilities.
- Continuous Monitoring: Use tools to track vendor compliance, security incidents, and vulnerabilities in real time.
Platforms like Censinet RiskOps™ simplify vendor risk management by automating assessments, providing real-time monitoring, and combining AI with human oversight. This ensures healthcare organizations can protect employee data, maintain compliance, and avoid costly breaches.
Healthcare Vendor Risk Statistics and Key Data Protection Metrics
Risks from Third-Party Payroll and HR Vendors
Third-party payroll and HR vendors handle some of the most sensitive data, including Social Security numbers, direct deposit information, and tax details. Unfortunately, these vendors can become prime targets for cyberattacks. Outdated systems, weak passwords, and unencrypted data can leave the door wide open for hackers, exposing organizations to theft, fraud, and a host of other risks. These vulnerabilities can have serious consequences for security, compliance, and even day-to-day operations.
Data Security Threats and Breach Vulnerabilities
Ransomware attacks, data breaches, and unauthorized access are among the most common threats tied to payroll and HR vendors. If encryption is weak or credentials are compromised, attackers can easily infiltrate systems and steal sensitive records. When this happens, healthcare organizations are often held legally accountable for the fallout.
The repercussions of a breach can be far-reaching. Beyond the immediate costs of responding to an incident, organizations may face regulatory fines, legal settlements, and long-term damage to their reputation.
Regulatory Compliance Challenges
Technical vulnerabilities aren’t the only concern - regulatory compliance can also be a minefield. Many healthcare organizations mistakenly think that having a signed Business Associate Agreement (BAA) with a vendor is enough to ensure compliance. However, the Department of Health and Human Services (HHS) requires much more. As Compliancy Group highlights:
"Having a signed business associate agreement (BAA) is not enough. The Department of Health and Human Services (HHS) mandates that healthcare organizations do their 'technical due diligence' when choosing a vendor to work with. If an organization fails to send out an SRA to their vendors, they are not satisfying the law. In the event of a vendor breach, both parties would be considered liable without an annual SRA." [2]
If vendors skip annual HIPAA Security Risk Assessments, fail to follow the "minimum necessary rule" for data access, or rely on shared login credentials, they create compliance risks for their clients. Poor offboarding practices, such as not fully revoking access or verifying data destruction, can make matters even worse.
Operational Risks and Vendor Oversight
A lack of proper oversight can disrupt critical operations. Without clear roles or centralized management for monitoring vendor risks, serious security issues can slip through the cracks. Superficial assessments - especially those that don’t involve input from multiple stakeholders - may miss major vulnerabilities. And when cost takes priority over security during vendor selection, organizations often find themselves paying a much higher price down the line.
How to Assess and Manage Vendor Risks
Managing vendor risks isn’t just about ticking boxes - it’s an ongoing process that starts before signing a contract and continues throughout the partnership. Healthcare organizations need a structured approach to evaluate vendors, considering the sensitivity of the data they handle, their security practices, and their potential impact on operations. This means going beyond basic questionnaires and demanding solid proof of compliance and strong security measures. By doing so, organizations can strengthen their overall risk management strategy and address vendor vulnerabilities more effectively.
Creating a Vendor Risk Assessment Framework
To tackle vendor risks, start by categorizing vendors into risk tiers based on factors like data sensitivity, operational impact, integration level, and potential breach costs. Vendors handling sensitive information - such as Social Security numbers, direct deposit details, or health records - should be classified as high or critical risk. It’s essential to conduct separate assessments for information security and compliance risks, as each requires a unique evaluation method.
A clear scoring system can help prioritize which vendors need deeper scrutiny. For example, a payroll vendor with access to banking and tax records poses a much higher risk than a vendor offering basic HR training services. Documenting these risk levels ensures you know how much due diligence is needed and how often vendors should be reviewed.
Performing Due Diligence and Contract Reviews
Once vendors are categorized, the next step is to verify their compliance. Request documented proof such as audit reports, metrics, and logs. Ask about their audit schedules, anti-phishing training, and endpoint device policies. Neutral third-party certifications like SOC, HITRUST, ISO, or UL are invaluable for validating their claims.
Contracts should go beyond standard Business Associate Agreements (BAAs). While BAAs are mandatory for HIPAA-covered entities, they need to spell out security measures, data handling protocols, breach notification timelines, and subcontractor responsibilities. Considering that healthcare data breaches cost an average of $10.93 million per incident [3] and vendor-related attacks have surged by over 400% in two years [1], these detailed contract provisions are more critical than ever.
Setting Up Continuous Monitoring and Audits
Vendor risks can change over time, which makes continuous monitoring essential. High-risk vendors, like those managing payroll data, might need quarterly or semi-annual reviews, while lower-risk vendors could be reviewed annually. Real-time monitoring tools can help track security incidents, compliance changes, and new vulnerabilities as they arise.
It’s equally important to have clear protocols in place for vendors that fail to meet security standards or experience breaches. With ransomware attacks in healthcare averaging $4.62 million per incident [4], predefined response plans can significantly reduce financial and operational fallout. Regular audits should confirm that vendors maintain their certifications, conduct internal risk assessments, and follow proper data handling practices.
sbb-itb-535baee
Using Censinet RiskOps™ for Vendor Risk Management
Managing vendor risks manually can be a daunting task, especially when juggling multiple payroll and HR vendors. Censinet RiskOps™ simplifies this process by bringing all risk management activities into one centralized platform tailored for healthcare organizations. It streamlines vendor assessments, provides ongoing monitoring of security measures, and supports informed decision-making about third-party partnerships. With features like automated assessments, real-time monitoring, and expert-guided tools, it offers a comprehensive solution for vendor risk management.
Automating Risk Assessments
Traditional vendor evaluations often involve repetitive and time-consuming tasks. Censinet RiskOps™ eliminates much of this manual effort with automated workflows that guide vendors through security questionnaires and documentation submissions. The platform ensures a consistent and structured assessment process for all vendors, cutting down on administrative work.
With the help of Censinet AI™, vendors can complete security questionnaires in seconds. The AI summarizes evidence, identifies key integration details, and highlights fourth-party risk exposures, generating detailed risk reports. This level of efficiency is especially important when dealing with vendors who handle sensitive employee information.
Real-Time Monitoring with Cybersecurity Dashboards
Beyond automating evaluations, Censinet RiskOps™ provides continuous, real-time oversight through integrated cybersecurity dashboards. Unlike static annual reviews that might miss new threats or compliance gaps, these dashboards offer up-to-the-minute insights into vendor security and compliance status. Risk teams can quickly pinpoint vendors that require immediate attention.
The platform’s command center acts as a central hub, allowing risk managers to oversee all vendor relationships, track assessment progress, and monitor compliance across the entire vendor network. This real-time visibility is crucial for addressing emerging security concerns, particularly with vendors managing sensitive data.
Human-Guided AI for Better Risk Decisions
Censinet AI™ takes a balanced approach, combining automation with human oversight to enhance decision-making. While the AI validates evidence, drafts policies, and flags potential risks, risk teams retain control through configurable rules and review processes. This ensures that automation complements, rather than replaces, human judgment.
Key findings from assessments are routed to the appropriate stakeholders for review and approval. Workflows can be set up to escalate high-risk issues to leadership or compliance officers automatically. By coordinating efforts across Governance, Risk, and Compliance teams, the platform promotes accountability and ensures that critical issues are addressed promptly and effectively.
Conclusion
Key Takeaways for Healthcare Organizations
Safeguarding payroll and HR data hinges on taking a proactive approach to vendor risk management. Alarmingly, third-party vendor breaches have surged from 10% in the first half of 2019 to 21% in the first half of 2023, impacting an average of 304,191 individuals per breach [5]. In healthcare, these vendor attacks have skyrocketed by over 400% in just two years [1], making vendor security an urgent priority.
Effective risk management starts with a deep evaluation of a vendor’s security measures, compliance standards, and operational reliability - before any contracts are signed. When choosing vendors, factors like cybersecurity credentials and adherence to regulations should weigh as heavily as cost considerations [1].
The 2023 MOVEit zero-day vulnerability revealed how a single vendor’s security gap can trigger widespread consequences. This highlights the importance of healthcare organizations having real-time visibility into vendor security and the agility to respond swiftly to emerging threats. These lessons underline the need for a structured and informed approach to vendor risk management.
Next Steps for Vendor Risk Management
To build on these insights, healthcare organizations need to take decisive action. Setting well-defined security requirements in contracts is essential. By embedding data protection expectations directly into agreements, organizations ensure vendors are held accountable from the outset [1].
Censinet RiskOps™ offers a centralized platform designed to handle vendor risks efficiently and at scale. With tools like automated assessments, continuous monitoring, and human-guided AI, this platform empowers healthcare organizations to minimize risk while maintaining operational efficiency. Its command center provides risk managers with real-time data, helping to safeguard sensitive employee information and meet regulatory standards across their entire vendor network.
FAQs
What security measures should healthcare organizations expect from HR and payroll vendors to protect employee data?
Healthcare organizations must prioritize the security of sensitive employee data by ensuring their HR and payroll vendors adhere to rigorous protection measures. This includes enforcing strict access controls, performing regular security audits based on established frameworks like NIST or HITRUST, and signing Business Associate Agreements (BAAs) to meet regulatory requirements.
Vendors should also offer continuous monitoring of their security systems, keep incident response plans current, and implement proactive measures to prevent breaches. These practices are essential for reducing cyber risks and safeguarding employee information.
How does continuous monitoring strengthen vendor risk management in healthcare?
Continuous monitoring plays a crucial role in improving vendor risk management within the healthcare industry by providing real-time updates on a vendor's security measures. It enables organizations to spot potential weaknesses or breaches early, ensuring they can respond quickly to protect sensitive employee information.
This forward-thinking method not only lowers the chances of data breaches but also helps maintain compliance with healthcare regulations. By anticipating and addressing new threats, healthcare organizations can safeguard their payroll and HR systems from risks tied to vendor vulnerabilities.
Why isn’t a Business Associate Agreement enough to ensure data protection compliance?
A Business Associate Agreement (BAA) plays an important role in compliance, but relying on it alone isn't enough to fully safeguard sensitive employee data. While it lays out the responsibilities of both parties, it often falls short in addressing newer challenges like advanced technologies, unauthorized data use, or evolving cyber threats.
To truly protect data, healthcare organizations need to take additional steps. This includes conducting regular vendor assessments, enforcing strong encryption standards, and continuously monitoring vendor security practices. These proactive measures not only reduce risks but also strengthen compliance efforts and help keep employee information secure.


