Healthcare TPRM Governance: Essential Board Reporting and Executive Oversight Strategies
Post Summary
Healthcare organizations rely heavily on third-party vendors for critical services like electronic health records and medical devices. But these partnerships carry risks - data breaches, vendor failures, and regulatory violations can disrupt patient care and lead to significant financial and legal consequences.
Key points to know:
- Third-Party Risk Management (TPRM) focuses on identifying, evaluating, and reducing risks tied to external vendors, especially those handling Protected Health Information (PHI).
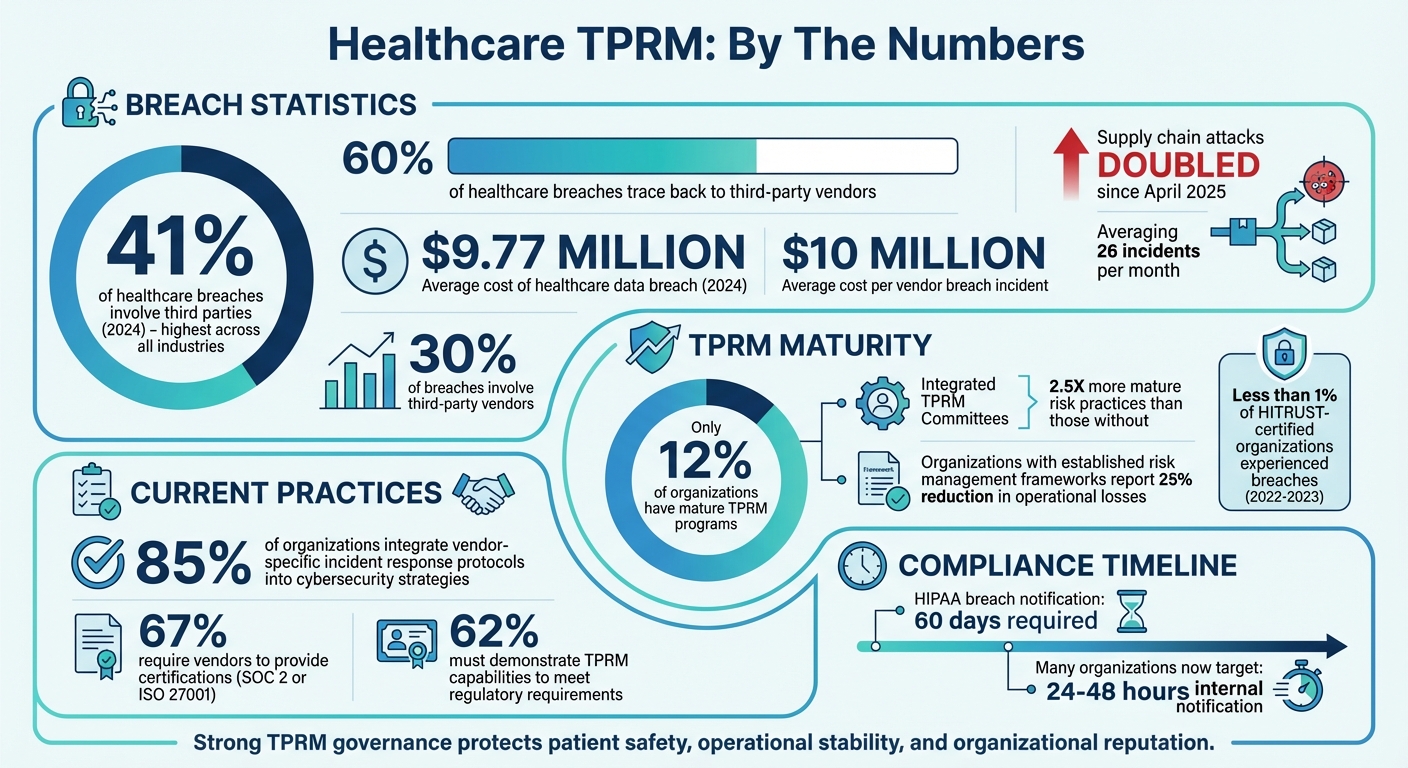
- Only 12% of organizations have mature TPRM programs, despite 41% of healthcare breaches involving third parties in 2024.
- Boards and executives play a central role in setting risk policies, monitoring vendor risks, and ensuring compliance with laws like HIPAA and HITECH.
- Tools like Censinet RiskOps™ simplify vendor risk management with real-time monitoring, automated assessments, and centralized dashboards.
Why it matters: Strong TPRM governance isn't just about compliance - it's about protecting patient safety, operational stability, and organizational reputation. Boards and executives must prioritize vendor oversight and integrate risk management into broader strategies for healthcare resilience.
Healthcare Third-Party Risk Management Statistics and Impact
Building a TPRM Governance Framework
Core Components of TPRM Governance
Creating a governance framework for third-party risk management (TPRM) in healthcare means addressing vulnerabilities unique to the industry. At its core, this involves systematically identifying and categorizing vendor risks, such as cybersecurity, privacy, reputational, financial, legal, operational, geopolitical, and ESG concerns. This ensures a consistent evaluation process for all vendors, whether they manage electronic health records or manufacture medical devices.
Risk remediation is another critical piece. Clear protocols must be in place for working with vendors to improve security, manage liability through contracts and Business Associate Agreements, and safely terminate relationships when necessary. Embedding security requirements into supplier contracts is essential - these should include incident reporting procedures and remedial action plans. For organizations working with third-party medical device manufacturers or software vendors, frameworks like ISO 14971 provide a structured way to address supplier risks that could compromise device safety.
The financial impact of these risks is significant. In 2024, the average cost of a healthcare data breach reached $9.77 million [3]. Even more alarming, 41% of breaches in the healthcare sector originated from third parties - the highest percentage across all industries [3]. On the flip side, organizations with well-established risk management frameworks reported a 25% reduction in operational losses [4], and fewer than 1% of HITRUST-certified organizations experienced breaches between 2022 and 2023 [5].
To strengthen these efforts, organizations must integrate vendor risk management into broader enterprise and patient safety metrics.
Integrating TPRM with Patient Safety and Enterprise Risk
TPRM frameworks shouldn’t operate in isolation. Effective governance integrates vendor risks into overall enterprise risk strategies. This involves categorizing vendors based on their access to critical systems and setting acceptable risk thresholds. The NIST Cybersecurity Framework 2.0 supports this approach by emphasizing the importance of understanding business contexts, identifying resources tied to critical functions, and assessing risks across the vendor ecosystem.
Incident response plans within TPRM frameworks are directly tied to patient safety. These plans should outline clear steps for communicating with vendors during security events, cutting off access for compromised third parties, minimizing exposure to patient data and critical systems, and meeting HIPAA breach notification requirements. Since breaches are an unavoidable reality, healthcare organizations must prioritize response planning for vendors with significant access to systems and protected health information (PHI). This proactive approach underscores that cybersecurity is a shared responsibility, with vendor oversight playing a direct role in patient outcomes and overall accountability.
Role of Technology in Streamlining Governance
Managing integrated risks and maintaining oversight is nearly impossible without technology. Manual TPRM processes simply can’t keep up with today’s fast-changing threat landscape. Technology platforms offer continuous monitoring by tracking real-time security, financial, and operational risks throughout the vendor lifecycle. This shift from periodic assessments to constant oversight is crucial, as vendors can experience risk changes multiple times a year due to breaches, acquisitions, or infrastructure updates - factors that one-time evaluations often miss.
For example, Censinet RiskOps™ simplifies governance with automation, standardized assessments, and real-time risk reporting. Its Censinet AI™ accelerates risk assessments by enabling vendors to quickly complete security questionnaires, automatically summarizing evidence, and generating detailed risk reports. This combination of human-guided and automated processes allows risk teams to scale their efforts and respond to complex vendor risks more effectively. Advanced routing and orchestration tools ensure that critical findings reach the right stakeholders, much like air traffic control, with real-time data displayed on intuitive dashboards. These dashboards act as centralized hubs, consolidating policies, risks, and tasks to support informed decision-making at every level.
Board-Level TPRM Oversight and Reporting Strategies
Board Roles in TPRM Governance
Healthcare boards carry the ultimate responsibility for overseeing Third-Party Risk Management (TPRM). Their role involves setting the strategic direction, shaping policies, and ensuring the organization remains committed to effective risk management practices [6][7][8].
Boards are tasked with approving the TPRM policy and regularly reviewing its effectiveness [9]. They also establish the organization's risk appetite and tolerance levels, which serve as a guide for all vendor-related decisions [10]. Beyond policy-setting, boards need to ensure that the TPRM team is equipped with the necessary resources - whether that’s skilled personnel, adequate funding, or cutting-edge technology - to address evolving risks. Additionally, they play a direct role in oversight and approvals for significant or complex third-party arrangements [2].
A critical aspect of effective oversight is asking the right questions. Boards need to verify that management comprehends the full scope of third-party risks, maintains a comprehensive and prioritized inventory of essential services (including those provided by subcontractors), and determines where oversight responsibilities should reside - whether with the full board, a dedicated risk committee, or another specialized group [2].
By clearly defining their responsibilities, boards can lay the groundwork for effective reporting mechanisms that enhance decision-making.
Designing TPRM Board Reports
Good reporting translates oversight into actionable insights. Reports to the board should distill complex information into clear, concise updates, focusing on critical areas such as third-party cybersecurity, data privacy, risks associated with emerging AI technologies, and ESG (Environmental, Social, and Governance) concerns. These reports should also outline management’s efforts in remediation and compliance [2].
Technology plays a pivotal role in this process. Real-time dashboards and automated reporting tools allow leadership to make informed decisions without waiting for periodic updates [10][11]. These tools should track key performance indicators (KPIs) and risk metrics on an ongoing basis [11]. Effective reports incorporate data from vendor risk assessments, contractual compliance, and ongoing monitoring efforts. Adding objective risk scoring systems helps compare vendors' security postures and prioritize remediation efforts effectively [5].
Incident response is another area that requires careful attention. Reports should detail compliance with breach notification requirements, such as those under HIPAA, and illustrate how TPRM integrates into the organization’s broader risk management and compliance strategies [5][2].
Best Practices for Board Engagement
Active engagement from the board is essential to strengthen the TPRM framework. Many organizations see better outcomes when they establish a TPRM Oversight Committee that provides regular updates to senior management and the board. Research shows that companies with such integrated committees have risk management practices that are 2.5 times more advanced than those without [11].
"The most important aspects of developing an effective committee is to have support from both C-suite executives and the board." – Risk Ledger [11]
Boards must define clear escalation procedures, risk thresholds, and communication channels to ensure timely involvement from senior management or the full board when necessary [11]. Determining the right frequency and format for third-party risk updates - whether through scheduled reports or real-time data access - also plays a key role in informed decision-making [2].
Continuous monitoring systems help boards stay on top of vendor performance and quickly identify new risks [11]. When combined with clearly assigned roles across teams like Risk, IT, Legal, Procurement, and Clinical [10], this approach fosters a collaborative environment where vendor-related risks are shared responsibilities. By aligning TPRM strategies with the organization’s broader goals and objectives, boards can turn vendor oversight into a strategic advantage rather than just a compliance requirement [11].
Executive Oversight of TPRM in Healthcare
Executive Leadership Responsibilities in TPRM
While board oversight sets the strategic direction for Third-Party Risk Management (TPRM), it's up to healthcare executives to translate those strategies into action. The C-suite - particularly roles like the CIO, CISO, and CFO - plays a critical role in implementing and maintaining TPRM programs across the organization.
"The success of your TPRM program depends on the support you receive from your C-Suite, as well as your Board." – TPRA Team & Practitioner Focus Group [12]
Executives shape the organization's risk appetite by making key decisions on managing and mitigating vendor risks [12]. They establish thresholds to identify when risks need escalation and regularly review reports on vendor risk ratings and mitigation efforts for high-risk partnerships [12]. Budgeting is another major responsibility; executives must ensure there are sufficient resources - whether personnel, tools, or training - to support the TPRM program [12].
Another crucial task is to quantify the value of TPRM. Demonstrating the financial benefits or cost savings from risk mitigation can help justify ongoing investments and secure broader organizational buy-in [12]. Executives must also ensure that TPRM is consistently implemented across all departments. Without this enterprise-wide commitment, even the most well-designed programs can fall short [12]. This operational work complements the governance framework established by the board.
"Senior leadership, as well as Board support, are essential to ensuring your TPRM program is successful by setting the right 'tone from the top.' Absent that support, an organization is unlikely to achieve consistent and timely adoption across all business and risk functions." – TPRA Team & Practitioner Focus Group [12]
Cross-Functional TPRM Operating Models
Effective TPRM doesn’t happen in isolation - it requires collaboration across departments. Procurement, legal, IT, and security teams each bring unique expertise to the table. Procurement manages vendor selection and contracts, legal ensures compliance, IT evaluates technical capabilities, and information security assesses cyber risks [1].
To avoid confusion, organizations benefit from clear operating procedures that define each department’s responsibilities, particularly during contract reviews [1]. This clarity helps ensure that no critical tasks are overlooked. For example, 85% of organizations now integrate vendor-specific incident response protocols into their broader cybersecurity strategies. Meanwhile, 67% require vendors to provide certifications like SOC 2 or ISO 27001, and 62% must demonstrate TPRM capabilities to meet regulatory requirements [1]. These statistics highlight why cross-functional collaboration is essential - not just for operational success, but also for meeting regulatory expectations.
Executive-Level TPRM Metrics and Dashboards
Executives need tools that provide real-time insights into vendor risks without overwhelming them with technical details. Consolidated dashboards and monthly reports that track vulnerabilities and enterprise-wide risks allow leaders to make informed, risk-based decisions and address issues promptly [13]. A monthly high-risk summary for the CIO, CISO, and senior management should include data on open, reopened, and remediated vulnerabilities, as well as compliance with critical vulnerability directives [13].
Beyond summary reports, early-warning alerts are key for proactive risk management. Dashboards that flag breaches of risk thresholds enable swift executive action. For instance, an Ongoing Authorization dashboard can monitor risk metrics and immediately notify leaders when risk tolerance levels are exceeded [13]. This kind of visibility is critical, especially as supply chain attacks have doubled since April 2025, now averaging 26 incidents per month, with 30% of breaches involving third-party vendors [14].
Requesting Software Bills of Materials (SBOMs) from vendors is another proactive step. SBOMs provide insight into software components and dependencies, helping organizations spot vulnerabilities before they escalate [14].
"You can't protect what you can't see, and knowing your software supply chain is the first step to securing it." – Idan Dardikman, CTO of Koi Security [14]
Centralized governance models for TPRM improve data aggregation and program oversight. Platforms like Censinet RiskOps™ serve as a central hub for managing risk-related policies, tasks, and data. These tools provide real-time dashboards that enhance accountability and ensure continuous monitoring across the organization.
sbb-itb-535baee
Integrating TPRM Governance with Incident Response
Vendor-Related Incident Scenarios
When a third-party vendor suffers a security breach, the fallout for healthcare organizations can be immediate and severe. From ransomware attacks that paralyze critical systems to data breaches exposing Protected Health Information (PHI) or service disruptions that interrupt patient care, these incidents demand swift action from boards and executives. The stakes are high - patient safety, regulatory compliance, and organizational reputation hang in the balance.
The NIST Cybersecurity Framework (CSF) 2.0 highlights this urgency through its Govern function (GV.SC-08). It underscores the need for healthcare organizations to quickly respond to, report, and mitigate vendor security incidents as part of a broader incident management strategy [15]. Treating vendor-related breaches with the same urgency as internal ones is essential. This means establishing clear communication protocols and assigning defined roles for both internal teams and vendor representatives during crises [16]. Timely action is especially critical given the strict regulatory timelines healthcare organizations must follow.
Regulatory and Legal Reporting Obligations
When vendor incidents involve PHI, healthcare organizations face strict reporting requirements. Under HIPAA breach notification rules, affected individuals must be notified within 60 days of breach discovery. However, many organizations now aim for even tighter internal deadlines, often requiring breach notifications within 24-48 hours of discovery [16]. These accelerated timelines help ensure compliance while demonstrating transparency to both patients and regulatory authorities.
In addition to HIPAA, vendor contracts often include clauses outlining cooperation during investigations. This can involve granting access to forensic data or sharing incident documentation. To streamline these efforts, organizations should create standardized communication templates tailored to different vendor incident scenarios [16]. Pre-approved templates can significantly reduce response time and help maintain clarity during high-pressure situations.
Improving Incident Response with TPRM Integration
Regulatory frameworks provide the foundation, but integrating Third-Party Risk Management (TPRM) tools can elevate incident response to a new level. Platforms like Censinet RiskOps™ act as centralized hubs for vendor risk data, enabling faster and more coordinated responses when incidents occur. These systems give risk teams instant access to critical information - such as vendor security assessments, contract terms, and contact details - eliminating delays caused by disorganized documentation or scattered communication channels.
Beyond immediate response efforts, these platforms also enhance long-term accountability. For example, after a vendor-related incident, organizations can use real-time dashboards to track remediation efforts, review vendor relationships, update risk profiles, and document corrective actions [16]. Tools like Censinet RiskOps™ ensure these activities are recorded systematically, providing clear oversight for executives. This approach aligns with the 85% of organizations that have already integrated vendor-specific incident response protocols into their overall cybersecurity strategies [1].
Post-incident reviews gain even more value when TPRM platforms aggregate insights across the entire vendor portfolio. By identifying recurring vulnerabilities among specific vendor types, organizations can refine their risk assessment criteria and strengthen their defenses. This continuous improvement loop not only enhances incident response capabilities but also fortifies the broader TPRM governance framework, making it a vital part of enterprise security.
Conclusion and Key Takeaways
Summary of TPRM Governance Practices
Did you know that 60% of healthcare breaches trace back to third-party vendors, with each incident costing an average of $10 million? [10] These numbers highlight the critical need for strong oversight at the highest levels of leadership. To tackle this, healthcare organizations must establish a structured framework for Third-Party Risk Management (TPRM), aligning with standards like NIST CSF 2.0 or HITRUST CSF. A dedicated TPRM Oversight Committee - comprising representatives from Risk, IT, Legal, Procurement, and Clinical teams - serves as the backbone of these efforts [10][11]. By weaving TPRM into broader enterprise risk management and patient safety strategies, healthcare systems can better safeguard both sensitive data and patient care.
Benefits of Technology in TPRM Governance
Governance sets the foundation, but technology takes it to the next level. Centralized platforms are revolutionizing how healthcare organizations approach third-party risks. For instance, tools like Censinet RiskOps™ streamline workflows, making risk remediation faster and more efficient [5][10]. When paired with IT service management and procurement systems, these platforms automate key processes, ensuring consistent communication with vendors and maintaining thorough documentation for future needs [5][10]. Organizations with integrated TPRM committees see their risk practices reach maturity levels 2.5 times higher than those without [11]. These technological advancements empower healthcare leaders to act decisively and comprehensively.
Final Thoughts on Strengthening Healthcare TPRM
Third-Party Risk Management is not just a cybersecurity measure; it’s a lifeline for protecting patients, reputations, and operations. With 41.2% of healthcare breaches involving vendors, the call to action is urgent [10]. To meet this challenge, healthcare leaders must define clear risk appetite statements, secure buy-in from executives, and enforce robust policies that cover vendor assessments, contract management, and incident response plans [10][11]. Strengthening TPRM governance is no longer optional - it’s a necessity for ensuring the resilience of healthcare organizations in an increasingly complex digital landscape [10][11].
FAQs
What are the essential elements of an effective TPRM governance framework in healthcare?
An effective healthcare Third-Party Risk Management (TPRM) governance framework relies on several critical components to operate smoothly. At its core, it should include a centralized or federated governance structure to streamline decision-making and oversight. Clearly defining the roles and responsibilities of board members and executives is equally important, ensuring accountability and clarity in managing third-party risks.
A solid process for vendor risk assessment and classification is another cornerstone. This helps identify and prioritize potential risks associated with different third-party vendors. Beyond assessment, continuous monitoring and reassessment of vendors is essential to keep up with evolving risks and maintain a proactive stance.
Comprehensive contract management is also vital. Contracts should include safeguards that address potential risks, reducing vulnerabilities from the outset. To prepare for unexpected challenges, a detailed incident response plan should be in place, ready to tackle any security breaches or compliance issues that arise.
Finally, aligning your framework with established industry standards - such as NIST, ISO 27001, or VRMMM - can strengthen its reliability and ensure adherence to regulatory requirements. This alignment not only enhances the framework's effectiveness but also helps build trust with stakeholders.
How does technology improve third-party risk management (TPRM) governance in healthcare?
Technology has become a cornerstone in refining TPRM (Third-Party Risk Management) governance, simplifying critical tasks like vendor onboarding, conducting risk assessments, and maintaining continuous monitoring. Tools powered by AI, for example, automate these processes, making them quicker and more precise.
With real-time insights into potential risks, technology boosts oversight while ensuring adherence to regulatory standards. This dual benefit not only fortifies governance but also equips organizations to address new threats proactively, protecting both patient data and operational stability.
What is the role of healthcare executives in ensuring the success of TPRM programs?
Healthcare executives play a key role in shaping the success of Third-Party Risk Management (TPRM) programs. They guide the overall strategy, turn board-level priorities into actionable policies, and establish clear boundaries for acceptable risk. By distributing resources wisely and ensuring ongoing monitoring, they help the organization stay compliant while addressing potential risks effectively.
Their leadership not only reinforces accountability but also cultivates a culture that prioritizes risk awareness throughout the organization. This alignment of TPRM initiatives with broader organizational objectives ensures that risk management becomes a seamless part of daily operations, supporting both security measures and operational efficiency.
Related Blog Posts
- Healthcare TPRM Governance: Essential Board Reporting and Executive Oversight Strategies
- Healthcare Third-Party Risk Management Trends 2025: What's Changing and Why It Matters
- Healthcare Third-Party Risk Management Maturity Model: Where Does Your Organization Stand?
- Healthcare TPRM Stakeholder Management: Board Reporting and Executive Engagement


