Healthcare Vendor Risk Management 2030: Emerging Threats and Future Strategies
Post Summary
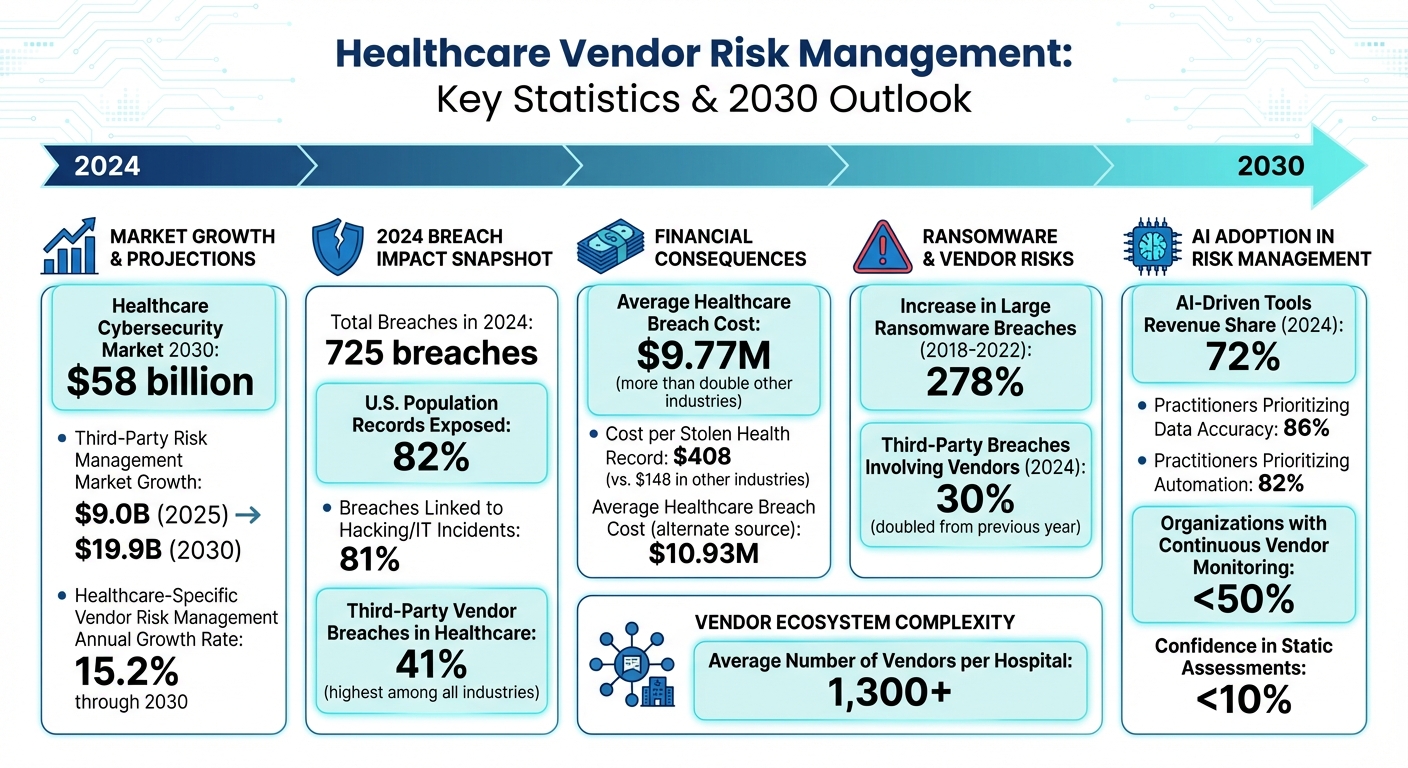
In healthcare, vendor risk management is becoming a top priority as cyber threats grow more sophisticated. By 2030, the healthcare cybersecurity market is forecasted to reach $58 billion, driven by increased digital transformation and stricter regulations like HIPAA updates targeting AI and quantum computing risks. Key challenges include ransomware attacks, software supply chain vulnerabilities, and outdated medical device security.
- 2024 Data: 725 breaches exposed 82% of U.S. population records; 81% were linked to hacking or IT incidents.
- Financial Impact: Healthcare breaches cost $9.77M on average, more than double other industries.
- Emerging Risks: AI vulnerabilities, IoMT devices, and decentralized health systems add complexity.
Solutions like continuous monitoring, AI-driven risk scoring, and platforms like Censinet RiskOps™ are helping organizations streamline vendor assessments, automate workflows, and maintain regulatory compliance. By adopting real-time monitoring and predictive analytics, healthcare providers can better safeguard patient data and ensure operational stability.
Action Steps for 2030:
- Shift from periodic to continuous vendor risk assessments.
- Use AI tools for predictive risk analysis and automation.
- Strengthen vendor governance models with tiering and lifecycle management.
- Integrate vendor risk strategies into enterprise resilience plans.
The future of healthcare vendor risk management hinges on proactive measures and investment in scalable, efficient solutions to combat evolving cyber threats.
Healthcare Vendor Risk Management Statistics and Projections 2024-2030
Emerging Cyber Threats in Healthcare Vendor Ecosystems
Cyber Threat Trends Impacting Third-Party Vendors
The healthcare sector is facing a growing wave of cyber threats, particularly within its vendor ecosystems. Ransomware attacks have seen a staggering increase, with large breaches involving ransomware jumping by 278% between 2018 and 2022 [1].
Another major concern is vulnerabilities in the software supply chain. Take the December 2021 ransomware attack on Eye Care Leaders, which compromised 3.7 million patient records. Or the April 2022 incident involving OneTouchPoint, where unauthorized access affected 2.6 million individuals, including patients from Anthem, Kaiser Permanente, and Blue Cross. The fallout has been severe - Eye Care Leaders paid over $4 million in settlements, while lawsuits related to the OneTouchPoint breach are still unresolved [6].
The data paints a grim picture. By 2024, nearly 30% of data breaches involved third-party vendors, doubling from the previous year [6]. And the financial toll is steep: the average cost to address a healthcare breach has reached $408 per stolen health record - almost three times the $148 average in other industries [5].
Risks from Emerging Technologies and AI
The rapid adoption of new technologies is creating fresh vulnerabilities in healthcare. By 2030, healthcare IT infrastructures are expected to be more complex, integrating Internet of Medical Things (IoMT) devices, remote consumer systems, AI tools, decentralized health networks, and countless third-party connections. This interconnected web makes managing vulnerabilities and exposures a daunting task [4].
Connected medical devices and telehealth platforms are particularly risky. Many of these devices operate on outdated software, lack strong security measures, and maintain constant network connections, making them prime targets for cyberattacks [6]. On top of that, AI-powered diagnostic tools and remote monitoring systems process massive amounts of sensitive patient data, introducing risks like algorithmic vulnerabilities that traditional security protocols may struggle to address.
Regulators are taking notice. Updates to HIPAA regulations now specifically target risks tied to AI and even quantum computing. These changes include mandatory controls and annual compliance audits to tackle the challenges posed by emerging technologies [6]. Additionally, new AI governance laws are expected to push compliance standards even higher for organizations managing these risks [7].
Regulatory Pressures Driving Vendor Risk Management
Regulatory frameworks are evolving quickly to keep up with the expanding threat landscape. Over the past two years, the U.S. Department of Health and Human Services Secretary's Breach of Unsecured Protected Health Information has documented 592 breaches, each affecting more than 500 individuals. These breaches are all under active investigation by the Office for Civil Rights [1].
"Regulatory bodies like the Health Insurance Portability and Accountability Act (HIPAA) in the U.S., the General Data Protection Regulation (GDPR) in the European Union, and various national regulations worldwide impose stringent requirements on healthcare organizations to safeguard patient data. This necessitates investments in cybersecurity solutions to ensure compliance, thereby driving market growth."
Laws like HIPAA, HITECH, and various state privacy regulations now require healthcare organizations to maintain strict oversight of their vendor relationships. These laws demand clear contractual terms outlining cybersecurity obligations, timelines for breach notifications, and financial accountability [3]. Without these safeguards, organizations not only face the direct costs of breaches - which average $9.77 million per incident - but also risk hefty regulatory fines that can climb into the millions [3].
The combination of evolving cyber threats and stricter regulations is pushing healthcare organizations toward advanced, data-driven strategies for managing vendor risks more effectively.
AI-Driven and Data-Driven Vendor Risk Assessment Strategies
Transitioning from Manual to Continuous Risk Assessments
Healthcare organizations are shifting away from outdated, periodic vendor assessments and embracing continuous, real-time monitoring. Why? Because traditional methods only provide fragmented snapshots of risk, leaving daily threats unchecked. The stats are telling: less than half of organizations actively monitor their vendors continuously, and confidence in static assessments is alarmingly low - below 10% [8].
The demand for daily monitoring and instant alerts is especially urgent in healthcare, where 41% of third-party breaches in 2024 targeted this sector, making it the most affected industry [10].
"Growth is anchored in the shift from periodic, compliance-driven checks to continuous oversight as supply-chain cyber attacks intensify and regulators demand broader third-party visibility." - Mordor Intelligence [7]
The market is catching up. Spending on third-party risk management solutions is expected to rise from $9.0 billion in 2025 to $19.9 billion by 2030, largely driven by the need for continuous monitoring capabilities [8]. Healthcare-specific vendor risk management is projected to grow at a 15.2% annual rate through 2030, fueled by the pressing need to combat ransomware and safeguard patient data from breaches involving business associates [7].
This shift sets the stage for incorporating AI and predictive analytics to streamline and prioritize risk management efforts.
Using Predictive Risk Scoring and Automation
Predictive analytics and machine learning are reshaping how healthcare organizations assess and prioritize vendor risks. These tools focus on vulnerabilities by analyzing factors like exploitability, exposure, and criticality, helping teams concentrate on the most pressing threats [2].
This approach eliminates much of the noise. Traditional systems often overwhelm security teams with endless alerts, many lacking context. AI-driven systems, on the other hand, analyze historical data and exposure metrics to predict which vulnerabilities are likeliest to cause real harm. By doing so, organizations can allocate resources more effectively, addressing critical risks rather than wasting time on low-priority issues.
The impact is clear. In 2024, AI-driven tools like automated document parsing and evidence gathering accounted for 72% of vendor risk management revenue [7]. These capabilities are in high demand - 86% of practitioners see data accuracy as essential, and 82% prioritize automation to close risk gaps [8]. Beyond improving efficiency, AI-powered monitoring adds to cost savings, contributing a modest 1.5% market growth [7].
"AI-native entrants automate document extraction, control mapping, and predictive scoring, lowering analyst workloads amid a widening talent gap." - Mordor Intelligence [7]
Automation also addresses a major challenge: security teams are managing an ever-expanding vendor landscape without comparable increases in staffing. By automating routine tasks like compliance updates, evidence collection, and control mapping, these systems free up analysts to focus on more strategic decisions and complex investigations.
How Censinet RiskOps™ Enables Scalable Vendor Risk Management
Building on advancements in AI, Censinet RiskOps™ and Censinet AI™ offer healthcare organizations tools to manage vendor risk efficiently at scale. In January 2025, Censinet introduced continuous monitoring and controls validation modules designed specifically for healthcare vendors. These features streamline assessments, automate workflows, and leverage AI for faster, more precise evaluations [7].
Censinet AI™ speeds up the third-party risk assessment process by allowing vendors to complete security questionnaires in seconds. The platform summarizes vendor evidence, captures integration details, identifies fourth-party risks, and generates comprehensive risk reports from all relevant data. This significantly reduces the time it takes to mitigate risks.
The platform also adopts a human-in-the-loop approach, balancing automation with expert oversight. Risk teams maintain control through customizable rules and review mechanisms, ensuring automation complements rather than replaces critical decision-making. Key findings and tasks are routed to stakeholders for review, making it easier to address high-priority risks. With real-time data presented via an intuitive dashboard, Censinet RiskOps™ acts as a central hub for managing vendor-related policies, risks, and tasks, seamlessly integrating with broader enterprise risk strategies.
This approach answers a critical need. Censinet RiskOps™ equips healthcare organizations to tackle evolving challenges by providing the continuous oversight, automated workflows, and predictive insights required to stay ahead of emerging threats - all while managing hundreds or even thousands of vendor relationships at once.
Building a Future-Proof Vendor Risk Governance Model
Key Components of a 2030-Ready Governance Model
A governance model designed for the future must bring together all organizational functions - spanning IT, legal, and beyond - to ensure a seamless approach to vendor risk management, covering everything from risk identification to response [9][11].
The involvement of executive leadership is crucial, as it provides the authority and resources needed to support the program. In addition, cross-functional risk committees play a vital role by offering diverse perspectives and establishing clear accountability [11].
To manage multiple vendor relationships, tools like real-time tracking, automated compliance updates, and guided risk assessments can simplify processes. However, relying solely on technology won't suffice. It's equally important to invest in continuous employee training and build a workplace culture where everyone understands their responsibility in managing vendor risks [9][11].
This integrated framework lays the groundwork for systematically categorizing vendors based on their importance, which is discussed in the next section.
Tiering Vendors Based on Criticality
Hospitals, for instance, often juggle relationships with over 1,300 vendors [10]. To manage this effectively, vendors must be categorized based on their impact on patient safety, the security of Protected Health Information (PHI), and overall operational stability.
Vendors critical to patient care, revenue streams, or data security demand heightened scrutiny. These relationships require stringent onboarding processes, ongoing monitoring, and well-defined contractual protections. Contracts and Business Associate Agreements (BAAs) should clearly outline security obligations aligned with each vendor's criticality level [10]. Additionally, critical vendors should be integrated into incident response plans, disaster recovery drills, and business continuity strategies, complete with communication protocols for emergencies [10].
While lower-tier vendors also need oversight, the level of management can be adjusted based on their relative risk.
Once vendors are prioritized by their criticality, the next step is managing their risks effectively throughout the entire lifecycle.
Lifecycle Management for Vendor Risk
Managing vendor risks effectively requires attention throughout the entire lifecycle of the relationship - from initial evaluation to final offboarding. Before bringing a vendor on board, organizations must conduct thorough due diligence to uncover potential risks. This includes assessing the vendor's security measures against regulatory requirements like HIPAA and industry standards [10][12].
After onboarding, regular audits and assessments should be conducted at key points in the relationship. Maintaining a Plan of Action and Milestones (POA&M) helps track and resolve any identified issues over time [10].
Offboarding is just as critical. Contracts should include clear instructions for returning or securely destroying data, revoking access, and performing final security audits to ensure no loose ends remain when the partnership ends [10][12].
Platforms like Censinet RiskOps™ can streamline and standardize these lifecycle processes. By offering a centralized hub for managing policies, risks, and tasks, along with configurable workflows and real-time dashboards, the platform ensures no essential steps are missed as vendor relationships evolve.
sbb-itb-535baee
Strategies for Resilience and Incident Response
Continuous Control Monitoring for Vendors
Healthcare organizations face tremendous risks when it comes to data breaches, with the average cost per breach reaching a staggering $10.93 million [12]. Even more alarming, 41% of third-party breaches in 2024 are expected to impact healthcare organizations [10]. Given these stakes, relying on annual or periodic vendor reviews is no longer practical. The answer? Continuous monitoring.
Continuous monitoring involves keeping a real-time pulse on vendor security postures - not just during onboarding, but throughout the entire partnership. This approach tracks performance metrics, incident reports, and the effectiveness of controls as they happen. To avoid drowning in alerts, focus on actionable insights by prioritizing exploitability, exposure, and criticality [2]. Modern compliance dashboards can provide a clear, real-time view of vendor status, open incidents, and remediation progress. Tools like a Plan of Action and Milestones (POA&M) can help organizations keep track of identified risks [10].
This real-time visibility is a game-changer, offering the groundwork needed to weave vendor risk into broader enterprise resilience strategies.
Integrating Vendor Risk with Enterprise Resilience
Data gathered through continuous monitoring doesn’t just sit in a silo - it plays a vital role in shaping enterprise resilience plans. By integrating vendor risk management into overall business continuity and disaster recovery strategies, healthcare organizations can respond to incidents more effectively. With hundreds or even thousands of vendor relationships, a single weak link can cause major disruptions. That’s why it’s critical to include key vendors in response plans and drills, ensuring communication protocols are clear and rehearsed [10][12].
For scenarios like ransomware attacks or data breaches, organizations should develop vendor-specific incident response plans. This also means having redundancy and failover strategies in place for services that are crucial to patient care. The stakes are high, with the healthcare cybersecurity market projected to grow to $58 billion by 2030 [2]. Adopting a Zero Trust Architecture, which continuously validates the security of devices and users, can help organizations sustain operations - even when vendor relationships are compromised [12].
Using Censinet RiskOps™ as a Resilience Command Center
Censinet RiskOps™ takes continuous monitoring and resilience planning to the next level, acting as a centralized hub for managing vendor risk data. This platform consolidates risk information into a real-time, comprehensive view of third-party risks [13]. When a vendor security incident occurs, every second counts. Censinet RiskOps™ enables healthcare organizations to quickly assess which systems, patient data, or clinical operations might be affected. From there, findings can be routed to the right stakeholders for immediate action.
The platform’s configurable workflows and real-time dashboards ensure no critical steps are overlooked during incident response. At the same time, it maintains the human oversight needed for making complex, high-stakes decisions. By streamlining processes and providing actionable insights, Censinet RiskOps™ empowers healthcare organizations to respond swiftly and effectively when it matters most.
Conclusion: Your Roadmap to 2030
Key Milestones for Vendor Risk Program Maturity
To build a robust vendor risk management program by 2030, healthcare organizations should take a phased approach with clear milestones. In the short term, the focus should be on laying the groundwork. Start by identifying critical vendors - those whose services directly impact patient care or revenue. Conduct thorough due diligence before onboarding new partners, and ensure contracts and Business Associate Agreements (BAAs) include well-defined cybersecurity requirements [10].
Medium-term goals involve refining operations and fostering continuous improvement. Move beyond static questionnaires and annual audits to adopt continuous vendor monitoring [8]. Introduce a Plan of Action and Milestones (POA&M) to oversee remediation efforts and integrate vendors into broader security initiatives like incident response and business continuity plans [10]. With 86% of professionals emphasizing the importance of data accuracy and 82% highlighting automation as key to bridging risk gaps, leveraging real-time tracking technology becomes indispensable [8].
Long-term objectives aim for advanced capabilities powered by AI and predictive analytics. By 2030, healthcare organizations should strive for fully automated, AI-driven risk assessments. These systems would offer predictive insights, enabling proactive threat mitigation across the entire vendor network.
This roadmap ties together earlier strategies, such as continuous monitoring and AI-driven tools, to create a cohesive, forward-looking approach to vendor risk management. These milestones outline a clear path to adopting advanced technologies and strategies that ensure resilience and adaptability.
The Role of Censinet in Future-Ready Vendor Risk Management
Censinet RiskOps™ plays a pivotal role in turning this roadmap into reality. With the Third-Party Risk Management market expected to grow from $9.0 billion in 2025 to $19.9 billion by 2030 [8], investing in the right technology is essential. Censinet RiskOps™ provides a centralized platform that streamlines risk management by consolidating data, automating workflows, and offering real-time dashboards - an essential feature for hospitals that typically manage relationships with over 1,300 vendors [10].
The platform’s AI-driven capabilities transform risk assessments, reducing the time required from weeks to mere seconds while maintaining human oversight. This blend of automation and expert input allows healthcare organizations to manage vendor risks at scale without compromising accuracy or safety. As the healthcare cybersecurity market is projected to hit $58 billion by 2030 [2], organizations equipped with scalable and resilient vendor risk frameworks will be better prepared to safeguard patient data, maintain care continuity, and navigate evolving regulatory landscapes.
FAQs
What are the top cybersecurity threats facing healthcare vendors by 2030?
By 2030, healthcare vendors will grapple with increasingly advanced cyber threats. Among these are supply chain attacks, where weaknesses in third-party systems become entry points for cybercriminals, and AI-driven cyberattacks that continuously adapt to evade security measures. Ransomware will continue to target interconnected healthcare networks, while legacy systems with outdated security measures will remain a persistent vulnerability.
On top of that, the emergence of disinformation campaigns and attacks exploiting data from smart medical devices will introduce new layers of complexity to managing vendor risks. To stay protected, vendors will need to adopt forward-thinking strategies, including the use of predictive risk assessment tools and AI-driven monitoring technologies to secure sensitive healthcare data effectively.
How do AI-powered tools improve vendor risk management in healthcare?
AI tools are transforming how healthcare organizations handle vendor risk management. These tools provide real-time risk assessments, helping identify and rank vulnerabilities based on factors like how easily they could be exploited, the importance of the systems at risk, and their level of exposure. This allows healthcare providers to address threats more quickly, focus on the most pressing issues, and continuously monitor vendor systems for potential risks.
By integrating AI into their processes, healthcare organizations can simplify risk management, cut down on manual tasks, and stay aligned with ever-changing regulatory requirements. This is especially crucial in today’s complex digital ecosystems, where third-party and supply chain risks continue to grow more advanced.
What are the best practices for ongoing vendor risk monitoring in healthcare?
To keep vendor risks under control, healthcare organizations need to embrace ongoing and forward-thinking strategies. This means using AI-driven tools to spot threats as they happen, conducting frequent and detailed risk evaluations, and including cybersecurity clauses in vendor agreements.
It's equally important to maintain up-to-the-minute visibility across the supply chain and align vendors with your overall cybersecurity efforts. These steps make it easier to catch and mitigate vulnerabilities early, helping your organization stay prepared against ever-changing cyber risks.


