HIPAA Compliance for Application Vulnerabilities
Post Summary
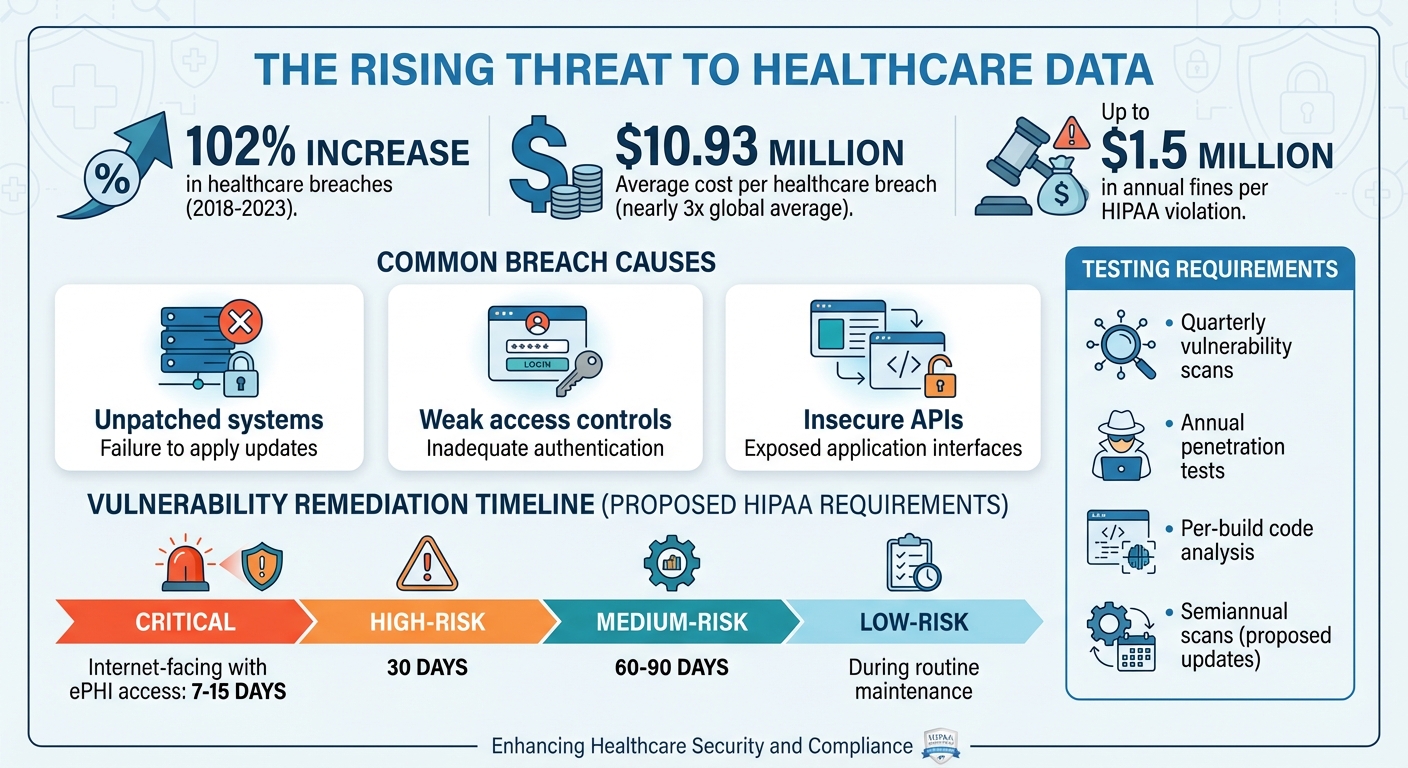
Healthcare organizations face a rising challenge: protecting patient data while managing software vulnerabilities. Over 102% more healthcare breaches were reported from 2018 to 2023, exposing millions of records. These breaches often result from unpatched systems, weak access controls, and insecure APIs, violating HIPAA's Security Rule. Non-compliance can lead to fines up to $1.5 million annually per violation and loss of patient trust.
To comply with HIPAA, organizations must:
- Conduct regular risk assessments for applications handling ePHI.
- Prioritize fixes for high-risk vulnerabilities, especially in patient portals, APIs, and cloud services.
- Implement safeguards like encryption, multi-factor authentication, and robust logging.
- Follow proposed 2024–2025 updates, including stricter timelines for fixing vulnerabilities and annual audits.
A structured vulnerability management program helps prevent breaches, ensures compliance, and protects patient data. Tools like Censinet RiskOps™ simplify tracking, remediation, and reporting, helping healthcare organizations meet evolving security demands.
HIPAA Compliance Statistics and Vulnerability Management Requirements for Healthcare
HIPAA Requirements for Application Vulnerability Management
HIPAA outlines specific expectations for managing vulnerabilities to safeguard electronic protected health information (ePHI). While the HIPAA Security Rule doesn’t explicitly mention terms like "vulnerability scans" or "penetration tests", it does require covered entities and business associates to identify and address risks to ePHI. As a result, routine scanning and testing have become widely accepted practices for mitigating application security risks.
Administrative and Technical Safeguards
Under the Security Management Process (§164.308(a)(1)), HIPAA requires a documented risk analysis and an active risk management program. This includes cataloging all applications - such as web portals, mobile apps, APIs, cloud services, and medical device software - and addressing their vulnerabilities. A designated security official (Assigned Security Responsibility, §164.308(a)(2)) is tasked with overseeing these processes. Additionally, regular reviews of logs and audit trails (§164.308(a)(1)(ii)(D)) ensure that mitigation measures are functioning as intended.
Access Control (§164.312(a)) provisions call for measures like unique user IDs, strong multi-factor authentication, automatic logoff, and encryption to protect ePHI. Other safeguards, including Audit Controls (§164.312(b)), Integrity Controls (§164.312(c)), and Person or Entity Authentication (§164.312(d)), further enhance security by tracking activities, preventing unauthorized changes, and verifying user identities[7].
Together, these administrative and technical safeguards create a framework for proactive risk management and compliance.
OCR Enforcement Actions and Common Violations
The Office for Civil Rights (OCR) has frequently penalized organizations for failing to conduct comprehensive risk analyses and address known vulnerabilities. Common violations include using default credentials, leaving remote access open, and neglecting to patch systems. These missteps have resulted in hefty penalties, with fines reaching up to $1.5 million annually per violation, along with mandatory corrective action plans[2].
Risk Analysis and Remediation Requirements
To remain compliant, organizations must implement a dynamic risk analysis process that evolves with new applications, integrations, and security incidents. While the HIPAA Security Rule doesn’t prescribe specific testing intervals, industry standards now lean toward quarterly or monthly vulnerability scans and annual or post-change penetration tests. Proposed updates suggest requiring at least annual penetration tests and semiannual vulnerability scans, with high-risk vulnerabilities addressed within 15–30 days. Organizations should maintain thorough documentation of testing schedules, link them to risk assessments, and confirm remediation efforts through follow-up scans or tests[6][9].
How to Build a HIPAA-Compliant Vulnerability Management Program
Creating a vulnerability management program that aligns with HIPAA requirements involves defining a clear scope, establishing governance, conducting thorough risk analysis, and implementing ongoing testing and remediation measures. While the HIPAA Security Rule doesn’t explicitly call for a “vulnerability management program,” it does require covered entities and business associates to perform an "accurate and thorough assessment of the potential risks and vulnerabilities" to electronic protected health information (ePHI). This includes implementing continuous risk management, evaluation, and audit controls.
Setting Up Scope and Governance
Start by compiling a comprehensive inventory of all systems that handle ePHI. This includes everything from electronic health record (EHR) systems and patient portals to telehealth platforms, mobile health apps, APIs, cloud services, medical device software, and third-party vendor applications. To ensure no asset is missed, leverage data from tools like configuration management databases (CMDBs), asset discovery utilities, cloud provider dashboards, EHR inventories, and procurement records.
For each asset, document key details such as whether it handles ePHI, its hosting environment, ownership, vendor, and criticality. This information helps guide risk analysis and remediation efforts. The Department of Health and Human Services (HHS) recommends documenting every location where ePHI is stored, transmitted, or maintained - including mobile apps and third-party services.
Many healthcare organizations in the U.S. rely on specialized risk management platforms like Censinet RiskOps™ to centralize their application inventories, third-party risk data, and security assessments. These tools make it easier to keep inventories up to date and integrate them into HIPAA-compliant risk analysis and remediation workflows.
Next, establish governance structures and assign clear responsibilities. Designate a vulnerability management lead - often the Chief Information Security Officer (CISO) or security officer - and outline roles for security teams, IT operations, application owners, compliance staff, and vendors. Form a cross-functional committee that meets regularly (e.g., monthly) to review risk metrics, overdue remediation tasks, exceptions, and upcoming high-impact changes. Written policies and procedures are essential, detailing how vulnerabilities are identified, assessed, remediated, documented, and reviewed. The Office for Civil Rights (OCR) has cited the absence of such policies in past enforcement actions, so this step is critical.
Conducting Risk Analysis and Setting Priorities
Once you’ve established an asset inventory, the next step is to evaluate risks based on how each asset impacts patient care. A thorough risk analysis should identify where ePHI resides, assess threats and existing controls, assign risk levels, and outline a remediation plan. For vulnerabilities in applications, prioritize them using factors like severity (CVSS scores), exploitability (e.g., known exploits or active attacks in healthcare), system exposure (internet-facing vs. internal), and existing compensating controls (such as web application firewalls or multi-factor authentication).
Special attention should be given to vulnerabilities in clinical applications that directly affect patient safety and ePHI availability. For example, vulnerabilities in EHRs, telehealth platforms, and APIs that support patient care should be addressed as a top priority. Critical vulnerabilities on internet-facing systems with direct access to ePHI should ideally be remediated within 7–15 days, while high-risk issues might be addressed within 30 days, medium-risk issues within 60–90 days, and low-risk items during routine maintenance.
If remediation of high- or critical-risk vulnerabilities is delayed due to clinical or operational constraints, formal documentation and approval from both security and business stakeholders are necessary. Integrating risk acceptance processes into ticketing systems or risk management platforms ensures consistency and auditability. Additionally, risk analyses should be revisited periodically or whenever significant operational changes occur.
After risks are prioritized, establish targeted testing protocols to validate and address vulnerabilities effectively.
Testing and Remediation Controls
Regular testing is a cornerstone of a robust vulnerability management program. Best practices include conducting quarterly automated scans, per-build code analysis, and annual penetration tests to simulate real-world attack scenarios and validate controls. While HIPAA doesn’t specify tools or testing frequencies, quarterly authenticated vulnerability scans in ePHI production environments are generally recommended, along with continuous or per-build code analysis for in-house applications and annual penetration testing - especially after major system changes.
For web and mobile healthcare applications, dynamic testing should focus on issues like injection flaws, authentication weaknesses, and insecure direct object references. API testing should verify access control, input validation, and encryption requirements specific to ePHI.
To manage remediation, classify systems by their importance to patient care and the sensitivity of the data they handle. For high-risk vulnerabilities in systems managing ePHI, fast-track patches through an accelerated change control process. This process should include non-production testing, input from clinical teams when needed, and clear communication with affected users. HIPAA requires measures to protect the confidentiality, integrity, and availability of ePHI, so patching strategies must strike a balance between robust security and uninterrupted patient care.
Change management records should document every step, including risk assessments, approvals, test results, and post-implementation reviews. These records provide a clear audit trail for OCR inspections. If immediate patching isn’t feasible, temporary compensating controls - such as enhanced access restrictions or network segmentation - can mitigate risks. However, these measures should be reviewed periodically, along with any risk acceptance decisions. Centralizing all test results into a unified tracking and remediation workflow ensures that evidence of due diligence is readily available for audits or investigations by OCR.
Managing High-Risk Vulnerabilities in Healthcare Applications
Securing high-risk healthcare applications requires building on established HIPAA risk analysis and testing practices. Applications that directly interact with electronic protected health information (ePHI) or manage large volumes of patient data are particularly vulnerable. Systems like patient portals, telehealth platforms, mobile health apps, FHIR and REST APIs, and cloud-hosted services significantly expand the attack surface. This increases the chances that a single vulnerability could compromise numerous records. Data from U.S. breach reports frequently highlights web application attacks and stolen credentials as leading causes of large HIPAA reportable breaches, making these systems a top focus for OCR (Office for Civil Rights) oversight. Below, we explore specific controls for web and mobile applications, APIs, and cloud services to address these risks.
Web and Mobile Healthcare Applications
Patient portals and telehealth platforms often face threats like weak access controls, insecure session management, unpatched frameworks, SQL injection, cross-site scripting, and improperly configured TLS. To mitigate these threats:
- Enforce strong, risk-based authentication measures, such as multifactor authentication (MFA) for both user and administrative access.
- Encrypt all portal traffic using up-to-date TLS configurations.
- Use role-based access controls to limit users to only their authorized records.
- Establish a formal patch management program with clear service-level agreements for addressing high-risk vulnerabilities.
Mobile healthcare apps present additional risks, including lost or stolen devices, local data storage, weak device security, and insecure third-party SDKs that may transmit ePHI without proper agreements. To counter these issues:
- Require device-level security measures like PINs, biometrics, and screen locks, and enforce them through mobile device management (MDM) or mobile application management (MAM) tools.
- Encrypt all ePHI stored on devices and minimize local storage by using secure server-side sessions.
- Implement app-level authentication with short session timeouts and require re-authentication for sensitive actions.
- Remove or thoroughly vet third-party SDKs, especially those not covered by business associate agreements or that transmit data to non-HIPAA-compliant environments.
APIs and Health Data Exchange Standards
FHIR and REST APIs, commonly used for health data exchange, pose significant risks due to vulnerabilities like broken object-level authorization (BOLA), overly broad token scopes, inadequate input validation, and weak transport security. These flaws can lead to unauthorized data access. To address these risks:
- Use granular authentication and strict token scopes that adhere to the "minimum necessary" standard.
- Conduct comprehensive input validation to prevent unauthorized queries.
- Encrypt all API traffic involving ePHI with current TLS configurations.
- Implement API gateways to segment traffic, enforce rate limits, validate schemas, log activity, and detect anomalies.
Regular API-focused security testing should be part of your HIPAA risk analysis. This includes scanning for vulnerabilities like BOLA, insecure direct object references, misconfigured CORS, and weak token handling.
Cloud and Third-Party Application Risks
Cloud deployments introduce a shared responsibility model: while cloud providers secure the infrastructure, organizations must secure configurations, applications, identities, and data. Common missteps include publicly accessible storage buckets containing ePHI, overly permissive IAM roles, unencrypted data at rest, exposed administrative interfaces, and insufficient network segmentation between internet-facing components and those processing ePHI.
To address these challenges:
- Ensure business associate agreements (BAAs) clearly designate the cloud or SaaS provider as a business associate, outline permitted uses of ePHI, and require compliance with the Security Rule, including breach notification obligations.
- Map the shared responsibility model explicitly, detailing which controls (e.g., virtual network configurations, access management, encryption key handling) are managed by the provider versus the organization or its vendors.
- Verify the provider’s security claims through due diligence, risk questionnaires, and independent attestations or certifications.
- Require BAAs to include provisions for timely vulnerability remediation, support for security assessments, and incident response collaboration.
Healthcare organizations can streamline vendor security assessments and BAA management using platforms like Censinet RiskOps™, which helps track cybersecurity benchmarks, manage remediation efforts, and oversee agreements with cloud and application providers handling ePHI.
sbb-itb-535baee
Maintaining Continuous HIPAA Compliance
Staying HIPAA-compliant isn’t a one-and-done task - it demands constant effort and vigilance. The Security Rule mandates ongoing activities like risk analysis, risk management, monitoring, and regular reviews of safeguards to protect electronic protected health information (ePHI) [7]. For application vulnerabilities, this means moving away from annual audits and adopting repeatable workflows with clear responsibilities, service-level agreements (SLAs) for remediation, and documented proof that controls are regularly reviewed and adjusted. Any changes to your environment - like new patient portals, updated APIs, or added cloud services - require an updated risk analysis to ensure compliance. Organizations that treat HIPAA as a one-time project put themselves at greater risk for findings from the Office for Civil Rights (OCR) and may struggle to adapt as new threats emerge.
The stakes are high: data from the Department of Health and Human Services (HHS) shows a 102% increase in large breaches from 2018 to 2023, impacting millions of patients [6]. Many of these breaches stem from issues like unpatched systems, misconfigurations, and weak access controls - problems that continuous vulnerability management is designed to address. As discussed in earlier sections on risk analysis and governance, maintaining compliance requires a dynamic, ongoing approach. The following sections delve into strategies for measuring, responding to, and continuously improving your HIPAA compliance efforts.
Tracking Metrics and Reporting
To prove continuous HIPAA compliance, it's crucial to establish and monitor key performance indicators (KPIs). These might include metrics like the time it takes to remediate high-risk vulnerabilities, patch coverage rates, and the percentage of critical vulnerabilities resolved within defined SLAs. Other valuable indicators include the recurrence of issues flagged in audits, security incidents tied to unresolved vulnerabilities, and the proportion of third-party applications that have undergone risk assessments and remediation planning.
For executives and compliance committees, aggregate this data into concise, risk-focused reports. These reports should connect technical vulnerabilities to their potential impact on patient safety and financial exposure. Effective reporting might include quarterly scorecards highlighting trends in high-risk vulnerabilities and SLA performance, red-amber-green (RAG) status for critical applications handling ePHI, and narratives that outline material risks, root causes, and planned remediation steps. Linking these reports to potential financial penalties - such as the fact that civil penalties for willful neglect can reach up to $1.5 million annually per violated provision - can help drive better oversight and resource allocation [2].
Incident Response and Breach Notification
Application vulnerabilities are a common entry point for security incidents, so your incident response (IR) plan should explicitly address scenarios like exploited web-app flaws or insecure APIs. Each phase of your IR process - preparation, detection, analysis, containment, eradication, recovery, and post-incident review - should be mapped to these types of application-layer threats. Preparation steps might include creating playbooks for specific vulnerabilities, keeping contact lists up to date, and ensuring access to logs and monitoring data. During detection and analysis, alerts from tools like web application firewalls, endpoint detection systems, and SIEMs should trigger investigations into possible ePHI breaches.
If an application vulnerability leads to unauthorized access or disclosure of ePHI, a risk assessment must evaluate the likelihood of PHI compromise. Factors to consider include the sensitivity of the data, the identity of the unauthorized recipient, and any mitigation efforts. If a breach is confirmed, the HIPAA Breach Notification Rule requires timely notification: affected individuals must be informed without unreasonable delay and no later than 60 days after discovery. Additionally, breaches must be reported to the HHS OCR, and if 500 or more individuals in a state or jurisdiction are affected, notification must also be made to prominent media outlets.
After an incident, conduct a structured post-incident review to identify root causes and map them to specific HIPAA Security Rule safeguards and internal controls. These reviews should inform updates to risk ratings, SLAs, and escalation paths if remediation delays contributed to the incident. They should also lead to improved secure coding practices and refined monitoring rules to detect similar threats earlier. Integrating these findings into your ongoing risk analysis and management plan ensures a continuous cycle of improvement. Centralizing these insights in risk management platforms helps streamline remediation workflows and demonstrates a commitment to ongoing compliance.
Using Risk Management Platforms
Maintaining HIPAA compliance at scale often requires centralized tools that automate routine tasks and provide actionable insights. A strong risk management platform can automate the ingestion of vulnerability scan results, threat intelligence, and configuration assessments. It should also streamline workflows for triage, remediation tracking, and reporting. Dashboards aligned with HIPAA requirements, along with integration into ticketing systems, CI/CD pipelines, and incident response tools, embed risk management into daily operations.
Platforms like Censinet RiskOps™ are specifically designed to support continuous HIPAA compliance across applications, third-party vendors, and assets containing PHI. This tool can standardize and automate security questionnaires, link vendor responses to risk scores, track remediation plans, and provide audit-ready reports. With features like up-to-date inventories of vendors and applications, monitoring of changes over time, and centralized dashboards, Censinet RiskOps™ enables organizations to demonstrate compliance with HIPAA's administrative and technical safeguards. Additionally, its integration with internal workflows ensures that vulnerabilities in vendor-hosted or cloud applications are addressed collaboratively and documented for oversight [2].
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required." - Terry Grogan, CISO, Tower Health
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with." - James Case, VP & CISO, Baptist Health [1]
Conclusion
Application vulnerabilities pose serious risks to patient data, disrupt care delivery, and challenge HIPAA compliance. The Security Rule emphasizes the need for "an accurate and thorough assessment of the potential risks and vulnerabilities" to electronic protected health information (ePHI), requiring ongoing evaluations and safeguards to mitigate these risks [8][7]. With the Department of Health and Human Services (HHS) reporting a 102% increase in large breaches from 2018 to 2023, and healthcare breaches costing an average of $10.93 million per incident - nearly triple the global average - the stakes are clear [6][10]. Many of these breaches stem from preventable security gaps that continuous vulnerability management can address.
Evolving regulations now demand a more dynamic approach to risk management. Recent updates call for regular penetration testing, vulnerability scanning, and strict remediation timelines for Common Vulnerabilities and Exposures (CVEs) [5][6]. This shift underscores that one-off compliance efforts are no longer enough. Instead, healthcare organizations need structured, repeatable processes that integrate vulnerability identification, prioritization, and remediation into their everyday workflows. These efforts should cover web and mobile applications, APIs, cloud environments, and third-party vendors.
A strong vulnerability management program not only enhances patient trust but also ensures operational stability and clinical continuity - especially in the face of ransomware attacks and other cyber threats that can jeopardize care delivery [2][3][4]. Organizations that treat HIPAA as an ongoing commitment, supported by governance frameworks, thorough risk analysis, and swift remediation cycles, are better equipped to adapt to evolving threats and demonstrate compliance during OCR investigations [9][10]. This continuous approach, as emphasized earlier, is critical for maintaining HIPAA compliance and safeguarding patient care.
Healthcare-specific platforms like Censinet RiskOps™ streamline this process by centralizing risk assessments, tracking remediation efforts, and providing audit-ready documentation aligned with HIPAA requirements [2]. As Matt Christensen, Sr. Director GRC at Intermountain Health, explains:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare" [1].
Tailored solutions like these allow healthcare organizations to scale their risk management efforts without compromising the precision and oversight needed to ensure patient safety.
Together, these measures create a strong compliance framework. Proactive vulnerability management is not just a regulatory necessity - it’s a critical step to protect ePHI, maintain compliance, and uphold the quality of patient care.
FAQs
How can healthcare organizations manage application vulnerabilities while staying HIPAA compliant?
Healthcare organizations must take proactive steps to protect systems that handle Protected Health Information (PHI) and meet HIPAA standards. Here's how they can bolster their defenses:
- Perform regular risk assessments: Identify potential weak spots in systems managing PHI and clinical applications.
- Leverage automated tools: Use tools for continuous monitoring and vulnerability scanning to detect risks as they emerge.
- Address vulnerabilities based on priority: Focus on issues with the highest potential impact and resolve critical ones quickly.
- Apply security patches and updates promptly: Regular updates help mitigate risks and keep systems secure.
- Establish clear incident response policies: Ensure there are well-defined procedures to address and remediate vulnerabilities.
- Invest in cybersecurity training for staff: Educate employees on HIPAA requirements and reinforce best practices to reduce human errors.
- Maintain detailed documentation: Keep records of risk assessments, corrective actions, and compliance efforts to demonstrate accountability.
Platforms like Censinet can play a vital role by streamlining risk management processes and simplifying compliance, ensuring both patient data and systems stay protected.
What are the best ways for healthcare organizations to address high-risk application vulnerabilities while staying HIPAA compliant?
Healthcare organizations can tackle high-risk application vulnerabilities more effectively by focusing on a risk-based strategy. This means prioritizing vulnerabilities based on how they might impact patient data security and compliance with HIPAA regulations. To stay ahead, it's crucial to conduct regular risk assessments, perform consistent vulnerability scans, and use automated alerts to address threats as they emerge.
Leveraging advanced tools, such as AI-powered risk management platforms, can simplify this process by organizing and monitoring vulnerabilities more efficiently. Team collaboration plays a key role in speeding up remediation efforts, while comparing practices to industry standards helps ensure resources are directed to the areas that need them most. By embedding risk management into their broader cybersecurity framework, healthcare organizations can better safeguard sensitive patient data and maintain compliance.
Why is continuous monitoring important for ensuring HIPAA compliance when addressing application vulnerabilities?
Continuous monitoring plays a crucial role in maintaining HIPAA compliance by allowing healthcare organizations to spot and address security threats as they happen. With real-time detection of vulnerabilities, organizations can act quickly to secure sensitive patient data and reduce the risk of breaches.
This ongoing vigilance ensures that any necessary fixes are implemented effectively while keeping security protocols in line with HIPAA's standards for protecting protected health information (PHI). It also enables organizations to stay ahead of emerging cyber threats, ensuring their security measures remain robust and compliant over time.


