HIPAA Compliance in Clinical Software Development
Post Summary
Developing clinical software requires balancing innovation with strict HIPAA regulations to protect patient data. Here's the bottom line: if your software handles Protected Health Information (PHI), compliance isn't optional. Violating HIPAA can lead to fines up to $2,134,831 per year, reputational damage, and even criminal charges.
Key points to consider:
- Core HIPAA Rules: Privacy, Security, and Breach Notification Rules define how PHI must be handled.
- Technical Safeguards: Encryption, access controls, and audit logs are critical.
- Challenges: Legacy systems, cloud vulnerabilities, and balancing security with usability.
- Solutions: Build compliance into the design phase, use tools like Censinet RiskOps™ for risk assessments, and automate testing with AI.
With cybersecurity threats rising, embedding compliance into every development stage ensures patient trust, minimizes risks, and prepares for stricter regulations expected in 2025.
For HIPAA compliance, you need DevSecOps
sbb-itb-535baee
HIPAA Requirements for Clinical Applications
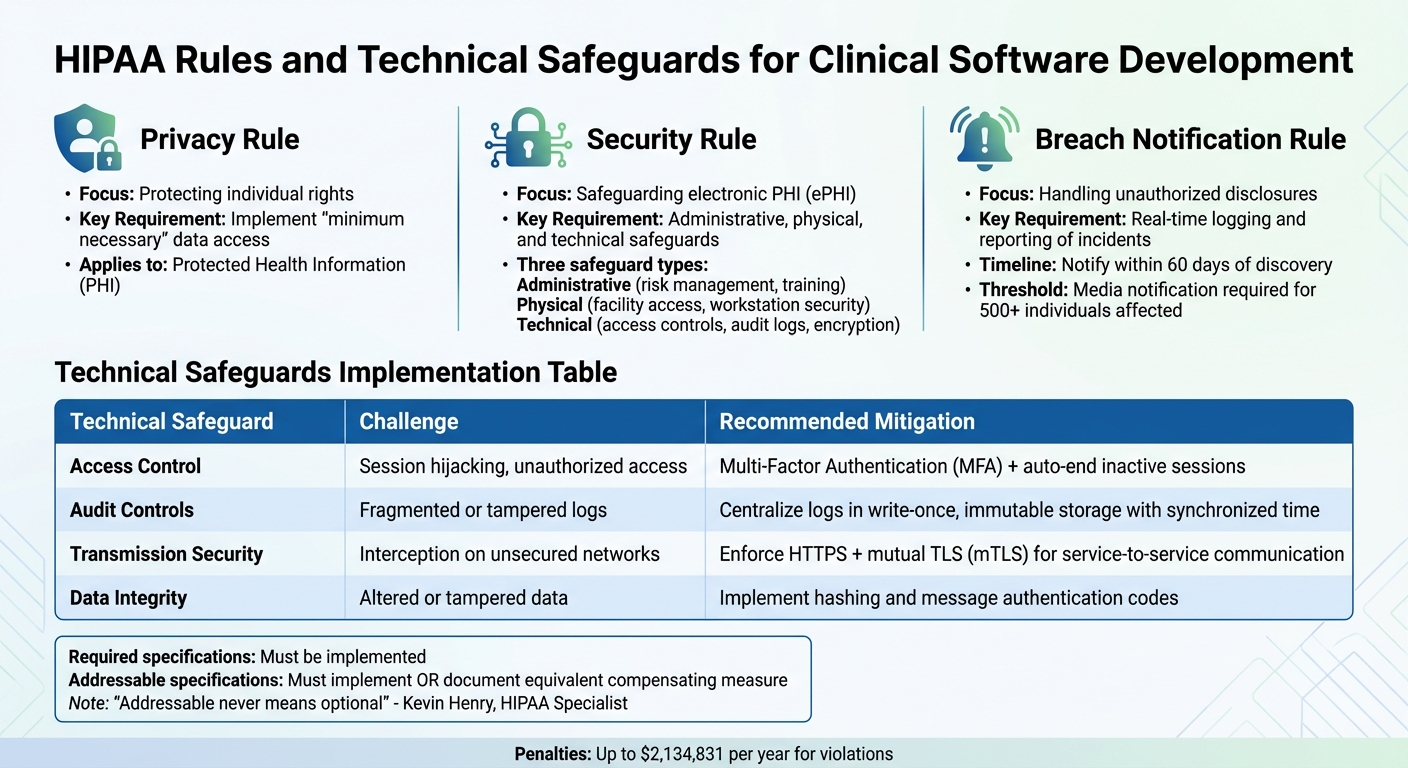
HIPAA Core Rules and Technical Safeguards Requirements for Clinical Software
Core HIPAA Rules and How They Apply to Software Development
HIPAA compliance revolves around three key rules that shape the way clinical software is designed and maintained. Here's a breakdown:
- The Privacy Rule: This sets national guidelines for safeguarding individually identifiable health information, known as Protected Health Information (PHI). It ensures that PHI is only accessed or shared when necessary for a specific task, and even then, only the minimum required data should be used[9].
-
The Security Rule: Focused on electronic PHI (ePHI), this rule mandates three types of safeguards:
- Administrative: Includes risk management and staff training.
- Physical: Covers facility access controls and workstation security.
- Technical: Involves access controls, audit logs, encryption, and authentication. Unlike prescribing specific technologies, the Security Rule allows flexibility, requiring measures that are reasonable based on the entity's size and risk profile[9].
"The Security Rule establishes a national set of security standards to protect certain health information that is maintained or transmitted in electronic form." - HHS[9]
- The Breach Notification Rule: This requires that individuals, the HHS Secretary, and in some cases, the media, are informed when unsecured PHI is accessed or disclosed without authorization. For developers, this means building systems with automated logging and real-time reporting to identify and document security incidents.
Most clinical software developers are classified as business associates under HIPAA. Following the HITECH Act of 2009 and the 2013 Omnibus Final Rule, these associates became directly accountable for HIPAA violations. This includes adhering to the Security Rule, signing Business Associate Agreements (BAAs) with clients, and ensuring subcontractors do the same. Documentation of policies, procedures, and assessments must be maintained for at least six years[9]. Adopting secure coding practices not only ensures compliance but also reduces liability risks.
| Rule | Primary Focus | Key Requirement for Software |
|---|---|---|
| Privacy Rule | Protecting individual rights | Implement "minimum necessary" data access. |
| Security Rule | Safeguarding electronic PHI (ePHI) | Administrative, physical, and technical safeguards. |
| Breach Notification | Handling unauthorized disclosures | Real-time logging and reporting of incidents. |
These rules form the backbone of HIPAA compliance. Next, let’s look at what qualifies as PHI.
What Qualifies as Protected Health Information (PHI)
PHI includes any identifiable health information tied to a person's past, current, or future physical or mental health, healthcare services, or payment for care[9][10]. When this data exists electronically - whether stored in databases, transmitted over networks, or displayed in software - it becomes ePHI and falls under the Security Rule's requirements.
Clinical software often processes various types of PHI, such as medical records, diagnostic results, prescriptions, billing details, insurance information, appointment schedules, and clinical notes. The HHS has recently highlighted risks posed by online tracking technologies, like pixels in clinical portals, which could unintentionally expose PHI to third parties, potentially breaching HIPAA[10].
To remove HIPAA protections, PHI can be de-identified using one of two methods:
- Safe Harbor: Eliminating 18 specific identifiers.
- Expert Determination: Using statistical analysis to ensure a low risk of re-identification.
Once de-identified, this data can be used for analytics or research without HIPAA restrictions[10].
Now, let’s explore the consequences of non-compliance.
Penalties and Risks of Non-Compliance
Failing to comply with HIPAA can lead to severe financial, reputational, and legal repercussions. Under the HITECH Act, business associates, including software developers, are directly accountable for Security Rule violations[9]. The Enforcement Rule governs investigations and penalties for such breaches[12].
When a breach occurs, it is presumed to have compromised PHI unless the entity can prove otherwise through a detailed four-factor risk assessment. Notifications must be sent promptly - no later than 60 days after discovery. Breaches impacting over 500 individuals in a state or jurisdiction also require media notification and reporting to the HHS Secretary, which can further damage reputations[13].
To mitigate risks:
- Follow recognized security practices, such as those recommended by NIST, for at least 12 months before an incident. This can influence penalties and audit outcomes[11].
- Encrypt PHI and use proper destruction methods to make it inaccessible to unauthorized users. If done correctly, this can exempt the entity from breach notification requirements[13].
"The HITECH Act provides the Department with the ability to take direct enforcement action against business associates for violating the Security Rule." - HHS[9]
Developers should enforce compliance through formal sanction policies and workforce training. Regular risk analyses, which assess potential threats to ePHI's confidentiality, integrity, and availability, are not optional - they’re mandatory[9].
Common Challenges in Achieving HIPAA Compliance During Development
Building HIPAA-compliant clinical software is no walk in the park. It’s not just about ticking off a checklist - it’s about tackling technical, operational, and integration challenges head-on. Below, we’ll dig into the key issues: technical security obstacles, the struggle to integrate with legacy systems, and finding the right balance between security and usability.
Technical Security Challenges
Today’s tech landscape introduces a host of new security risks. Cloud environments, for instance, can be a double-edged sword. Misconfigured setups, abandoned workloads, or misplaced electronic Protected Health Information (ePHI) can lead to compliance violations [1]. Many healthcare devices, including mobile and IoT devices, also lack basic security features, making it tough to enforce consistent authentication and logging across diverse hardware [1].
Artificial intelligence (AI) adds another layer of complexity. Sensitive data can inadvertently leak through AI training pipelines, and de-identifying unstructured data while keeping it clinically useful is a major challenge [1]. Even the healthcare supply chain security isn’t safe - vulnerabilities in third-party tools like billing systems or Electronic Health Record (EHR) platforms can compromise patient data, demanding constant vigilance [1].
"It's best to consider HIPAA requirements at the design stage of software development. This way, you can create a solution with top-notch security in mind."
– Stanislav, Security Testing Team Software Developer, Apriorit [1]
Testing environments present additional challenges. Developers need automated pipelines for tokenization or synthetic data generation to create realistic test data without exposing real patient records [6]. Managing encryption keys, implementing envelope encryption, and phasing out weak protocols without sacrificing performance requires expert handling [7][8]. API security also demands strict schemas, validated inputs and outputs, and error messages that don’t unintentionally expose ePHI [7].
| Technical Safeguard | Challenge | Recommended Mitigation |
|---|---|---|
| Access Control | Risks like session hijacking or unauthorized access | Use Multi-Factor Authentication (MFA) and auto-end inactive sessions [1] |
| Audit Controls | Fragmented or tampered logs | Centralize logs in write-once, immutable storage with synchronized time sources [6][7] |
| Transmission | Interception on unsecured networks | Enforce HTTPS and use mutual TLS (mTLS) for service-to-service communication [8] |
| Integrity | Altered or tampered data | Implement hashing and message authentication codes [7] |
While technical safeguards are essential, many organizations face an even bigger challenge: outdated systems. Let’s explore how these legacy systems complicate compliance efforts.
Connecting Modern Software to Legacy Systems
Healthcare organizations often rely on legacy infrastructure that wasn’t built with today’s security standards in mind. Shockingly, up to 75% of healthcare IT budgets are spent maintaining these outdated systems, and 74% of hospitals using them experienced cybersecurity incidents in the past year [14]. With healthcare breaches costing an average of $9.77 million per incident - almost double the global average - this is a critical issue [14].
One of the biggest hurdles is bridging old protocols like HL7 v2, which lack modern security measures, into FHIR or REST standards used by new applications [14]. Legacy systems often can’t meet requirements like MFA or AES-256 encryption, so developers must implement these safeguards at the API gateway or middleware layers [14].
Real-world examples highlight possible solutions. A regional healthcare payer successfully modernized six disconnected legacy systems into an AWS data lake in just 10 weeks. By using a de-identification pipeline with tokenization and machine learning-based Named Entity Recognition, they passed a HIPAA audit on the first try and cut manual compliance work by 40% [14].
"The best engineers spend 50% of their time maintaining legacy pipelines instead of building AI features because nobody wants to work on 15-year-old Perl scripts."
– Torsion.ai [14]
To ensure a smooth transition, organizations often use database virtualization and a parallel-run approach. Running both modern and legacy systems side-by-side for 2–8 weeks allows for validation of data parity and compliance without disrupting clinical operations [14]. Additionally, creating copy-on-write clones of masked datasets for testing avoids exposing raw PHI in development environments [6].
Balancing Security Requirements with User Experience
Security measures, while necessary, can sometimes feel like roadblocks to users. The challenge is to integrate protections for ePHI without slowing down essential healthcare workflows. Building security into the software from the start ensures it feels seamless rather than tacked on later [3].
Single Sign-On (SSO) is one way to streamline the user experience. It reduces login fatigue while maintaining centralized control over identity management [7]. Step-up verification is another smart approach - it triggers MFA only for high-risk actions, like exporting PHI, rather than for every interaction [7]. Just-in-time (JIT) access, also known as “break-glass” access, provides temporary, task-specific permissions that expire automatically once the task is complete [6].
"Security works better when it mirrors how developers already work."
– Yash Gautam, Bright Security [15]
Role-based access is another effective strategy. By redacting unnecessary PHI from standard views, clinicians see only what’s relevant to their role, reducing data exposure without complicating workflows [6]. Embedding HIPAA requirements directly into user stories during the design phase ensures that security features feel intuitive and natural [7].
| Strategy | Security Benefit | UX Benefit |
|---|---|---|
| Single Sign-On (SSO) | Simplifies identity management | Reduces login fatigue and password resets [7] |
| Step-up Auth | Protects high-risk actions | Minimizes friction for routine tasks [7] |
| JIT Access | Limits permanent high-level access | Speeds up emergency responses [6] |
| View Redaction | Enforces "minimum necessary" access | Simplifies the interface by hiding irrelevant data [6] |
Overly rigid security can stifle innovation and scalability. By prioritizing flexibility during the design phase, developers can build systems that meet current security needs while remaining adaptable for future demands.
How to Integrate HIPAA Compliance into Software Development
The challenges of HIPAA compliance aren't impossible to overcome - they just need a structured approach. Instead of tacking compliance on at the end, successful development teams incorporate it into every stage of the software lifecycle, from initial planning to ongoing monitoring. Here's how to make HIPAA compliance a seamless part of your process.
Building Security into the Design Phase
The ideal time to address HIPAA requirements is before any code is written. This "shift-left" strategy ensures compliance is baked into user stories and acceptance criteria during the planning phase. By making security a priority from the start, you set a strong foundation for the entire project [7]. When brainstorming new features, HIPAA considerations should be part of the discussion - not an afterthought.
Threat modeling is a key step during design reviews. For every feature, ask questions like: What protected health information (PHI) will this involve? Who needs access? What could go wrong? Document potential risks and their solutions alongside your feature specifications. This proactive approach helps you avoid costly rework and ensures your architecture supports compliance without major changes later [7].
Another crucial principle is data minimization. Design systems to collect and store only the PHI necessary for a specific function. For instance, if a dashboard only needs to show appointment times, avoid pulling a patient’s full medical history. This reduces your risk exposure and simplifies compliance.
"HIPAA compliance for software development is an important consideration for vendors... however, software HIPAA compliance is rarely the only consideration."
– Steve Alder, Editor-in-Chief, The HIPAA Journal [2]
Before handling any PHI, establish Business Associate Agreements (BAAs) with healthcare clients and subcontractors, including cloud providers like AWS [7]. Addressing these requirements during the design phase minimizes future issues and helps secure patient data from the outset.
Once you’ve established a compliant design, your next focus should be implementing robust technical safeguards.
Required Technical Safeguards
With a strong design in place, adding the right technical safeguards becomes more straightforward. Encryption is fundamental: use AES-256 for data at rest and TLS 1.2 or 1.3 for data in transit [7][5]. Employ envelope encryption with Key Management Services (KMS) or Hardware Security Modules (HSM) to enable secure key rotation [5].
Access control is another must-have, and it involves three layers: unique user identification, role-based access (RBAC), and multi-factor authentication (MFA) for anyone accessing electronic PHI (ePHI) [7]. For administrative access, adopt just-in-time (JIT) methods, which grant temporary permissions with full session recording and automatic expiration [6].
Audit controls are essential for tracking every interaction with PHI. Logs should record details like user identity, access time, location, and action outcome [6]. Stream these logs to a centralized Security Information and Event Management (SIEM) platform using immutable storage. Set up alerts for unusual activities, such as failed logins, large data exports, or access outside normal hours [6][17].
| Safeguard Category | Implementation Specification | HIPAA Status |
|---|---|---|
| Access Control | Unique User Identification | Required |
| Access Control | Emergency Access Procedures | Required |
| Access Control | Automatic Logoff | Addressable |
| Audit Controls | Audit Logging and Review | Required |
| Integrity | Mechanism to Authenticate ePHI | Addressable |
| Transmission | Encryption | Addressable |
It’s important to note that "addressable" doesn’t mean optional. As Kevin Henry, a HIPAA Specialist, clarifies:
"Addressable never means optional. It means you must implement the control as reasonable and appropriate, or document a compensating measure that achieves an equivalent level of protection based on risk" [16].
When creating testing environments, avoid using real PHI. Instead, rely on deterministic tokenization and salted hashing to generate realistic synthetic data. Automated pipelines for this purpose can mimic clinical patterns while protecting patient privacy [6].
Risk Management and Continuous Monitoring
HIPAA compliance doesn’t stop at deployment - ongoing monitoring is critical. The Office for Civil Rights (OCR) emphasizes:
"Risk analysis is an ongoing process that should provide the organization with a detailed understanding of the risks to the confidentiality, integrity, and availability of e-PHI" [18].
Conduct quarterly risk assessments and re-evaluate after any significant changes [7].
Incorporate automated security scans into your CI/CD pipeline. Tools like Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Infrastructure-as-Code (IaC) scanning can identify vulnerabilities before they reach production, reducing both costs and risks [7].
Schedule regular penetration tests and vulnerability scans for applications, APIs, and infrastructure. Complement these with tabletop exercises to rehearse incident response plans, document lessons learned, and strengthen controls [6].
Regularly test your backup systems. Perform recovery drills and verify data integrity using checksums. Test your Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) on a consistent schedule - don’t wait for a disaster to discover your backups aren’t reliable [7].
Finally, remember that HIPAA requires documentation - such as risk analyses, remediation plans, and training records - to be retained for at least six years [2]. Organizations must also be able to provide this documentation within 30 days if requested for audits or complaints [2]. Treat documentation as a priority, not an afterthought, to ensure you’re always prepared.
Using Technology to Simplify Compliance
Handling HIPAA compliance manually can be overwhelming and prone to mistakes. Fortunately, modern platforms are stepping in to take over much of the grunt work. From keeping tabs on vendor agreements to monitoring security controls in real time, these tools help cut down on administrative headaches while also bolstering your security measures. This shift builds on the importance of thorough risk assessments and ongoing monitoring, as previously discussed.
Faster Risk Assessments with Censinet RiskOps™
Traditional risk assessments often slow things down, creating bottlenecks in critical workflows. Censinet RiskOps™ tackles this problem by consolidating risk management into one streamlined platform. It keeps a detailed risk register that connects specific threats to the controls that mitigate them, assigns ownership, and tracks remediation timelines. This ensures no gaps in compliance with administrative safeguard requirements.
One standout feature is Censinet AITM™, which drastically speeds up third-party risk assessments. Vendors can complete security questionnaires in seconds, while the system automatically compiles evidence, captures integration details, and generates summary reports based on all relevant data [7][17]. This allows healthcare organizations to address risks faster without compromising the thoroughness needed for HIPAA compliance.
The platform also includes a centralized BAA registry, which manages Business Associate Agreements with machine-readable metadata. This registry links BAAs to specific systems, data types, renewal dates, and compliance requirements like data retention and logging. By maintaining this digital record, organizations can quickly respond to audits and prevent "compliance drift" - a gradual weakening of standards when new vendors or services are added without proper oversight [6][17].
Automating Compliance Checks with AI
Automation is transforming complex HIPAA tasks into efficient, ongoing processes. As Mike Bruns from UDX puts it:
"Automation, with its ability to streamline processes, reduce human error, and increase efficiency, plays a pivotal role in HIPAA compliance." [19]
Shift-left integration embeds compliance checks directly into development pipelines. This includes tools like Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Infrastructure-as-Code (IaC) scanning [7]. For instance, automated systems can block infrastructure templates that attempt to use services without valid BAAs, enforcing compliance at the configuration level [6][17].
AI also excels in continuous risk monitoring, replacing periodic manual reviews with real-time alerts and reports. This ensures vulnerabilities are addressed immediately, aligning with guidance from the Office for Civil Rights (OCR), which emphasizes integrating risk analysis into new technology deployments [18][19].
Another innovative use of AI is synthetic data generation for testing environments. Instead of manually de-identifying production data or using unrealistic "dummy" records, AI can create statistically accurate datasets that mimic real patient information without exposing sensitive data [6].
| Compliance Task | Manual Approach | Automated/AI Approach |
|---|---|---|
| Risk Assessment | Annual or periodic reviews [18] | Continuous monitoring with real-time alerts [19] |
| Audit Trails | Manual log collection and review | Centralized, immutable logging [6][19] |
| Test Data | Manual de-identification or dummy data | AI-generated synthetic data [6] |
| Access Control | Manual permission audits | Automated access and revocation [6][19] |
| Vendor Risk | Manual BAA tracking | Automated metadata and service blocking [6] |
These tools not only streamline internal processes but also improve collaboration between healthcare organizations and their vendors.
Coordinated Risk Management for Vendors and Healthcare Organizations
Effective HIPAA compliance requires collaboration across the healthcare ecosystem. The HITECH Act holds business associates, such as software vendors, directly accountable for violations [4]. This shared responsibility highlights the need for coordinated risk management between healthcare providers and their partners.
Platforms like Censinet RiskOps™ act as centralized hubs for this collaboration. A command center aggregates various risk metrics into one dashboard, providing clear, actionable insights. This shared visibility helps both healthcare organizations and vendors identify gaps, track remediation progress, and ensure security requirements are aligned [6].
For vendors, this approach offers benefits beyond compliance. Automated evidence collection can speed up sales by providing ready-to-share proof of compliance, while standardized audit processes simplify demonstrating adherence during software updates. Healthcare organizations, on the other hand, save time on audit preparation and gain ongoing oversight of third-party relationships.
The platform's routing and orchestration capabilities ensure that risk management tasks are handled efficiently. Think of it as "air traffic control" for compliance - it directs findings and remediation tasks to the right teams at the right time, ensuring nothing slips through the cracks. This accountability strengthens both compliance efforts and overall security.
Conclusion
Integrating HIPAA compliance into every phase of clinical software development - right from initial design to ongoing post-launch monitoring - is non-negotiable. It’s not something you can simply tack on later. Instead, it must be built into the foundation of your process. This approach ensures your software protects patient data, maintains trust, and withstands the scrutiny of audits.
The stakes are high. Civil monetary penalties for HIPAA violations range from $141 per violation to as much as $2,134,831 annually [1]. Beyond financial penalties, non-compliance can severely harm your reputation and limit future business opportunities in a trust-driven industry.
"As HIPAA regulations evolve, having certified HIPAA compliance for software can make it easier for vendors and service providers to adapt to new legal requirements and streamline the due diligence process during sales negotiations."
– Steve Alder, Editor-in-Chief, The HIPAA Journal [2]
Fortunately, you don’t have to navigate compliance challenges alone. Tools like Censinet RiskOps™ simplify the process by automating risk assessments, maintaining up-to-date documentation, and keeping vendor relationships audit-ready. By embedding compliance checks directly into your CI/CD pipelines and leveraging AI for continuous risk monitoring, you can shift from reactive problem-solving to proactive risk management.
Automated vulnerability scanning and immutable audit trails ensure you stay ahead of emerging threats and regulatory updates. With the proposed January 2025 HIPAA Security Rule changes potentially making all specifications "required" instead of "addressable" [1], now is the time to strengthen your compliance strategy.
FAQs
Is my app a HIPAA business associate?
Apps are considered HIPAA business associates if they create, receive, maintain, or transmit protected health information (PHI) on behalf of a covered entity. However, if your app doesn’t handle PHI for a covered entity, it doesn’t automatically fall under this classification.
What security controls are 'required' vs 'addressable'?
Under HIPAA, "required" controls are non-negotiable and must be put in place. These include measures like access control policies and risk management procedures. On the other hand, "addressable" controls offer some leeway. Organizations need to assess whether these controls are relevant to their operations. If a control isn’t deemed suitable, they must document their reasoning and implement an alternative solution. For instance, encryption and automatic logoff fall into the addressable category, meaning their implementation depends on the specific needs and risks of the organization.
How do we test with realistic data without using PHI?
To work with realistic data while steering clear of Protected Health Information (PHI), you can rely on synthetic data. This type of data replicates real patient information but adheres to HIPAA regulations. Common methods include:
- Generating synthetic patient records: These are entirely fabricated but designed to reflect real-world patterns and scenarios.
- Anonymizing or masking data: This involves removing or altering identifiable information to ensure privacy.
- Creating scenario-specific mock data: Tailored datasets are developed to simulate specific use cases or testing needs.
These strategies allow for effective testing in realistic environments without compromising privacy or compliance standards.


