HIPAA Compliance in Cloud Forensics
Post Summary
HIPAA compliance in cloud forensics is all about protecting patient data while investigating security incidents. Healthcare organizations must follow strict rules to ensure that investigations involving Protected Health Information (PHI) meet legal standards. This includes safeguarding sensitive data, maintaining clear documentation, and working closely with cloud vendors to meet HIPAA requirements.
Key challenges include:
- Role confusion with cloud providers: The shared-responsibility model can blur lines on who handles what during investigations.
- Over-collection of PHI: Gathering more data than necessary violates HIPAA's "minimum necessary" standard.
- Log and evidence issues: Short log retention periods and scattered data make it hard to track breaches and maintain a reliable chain of custody.
To stay compliant:
- Establish clear policies for accessing and handling PHI during investigations.
- Strengthen vendor contracts to include forensic support, like log retention and breach notifications.
- Use privacy-by-design architectures to limit PHI exposure, such as encryption and tokenization.
- Maintain detailed documentation of forensic activities to meet regulatory requirements.
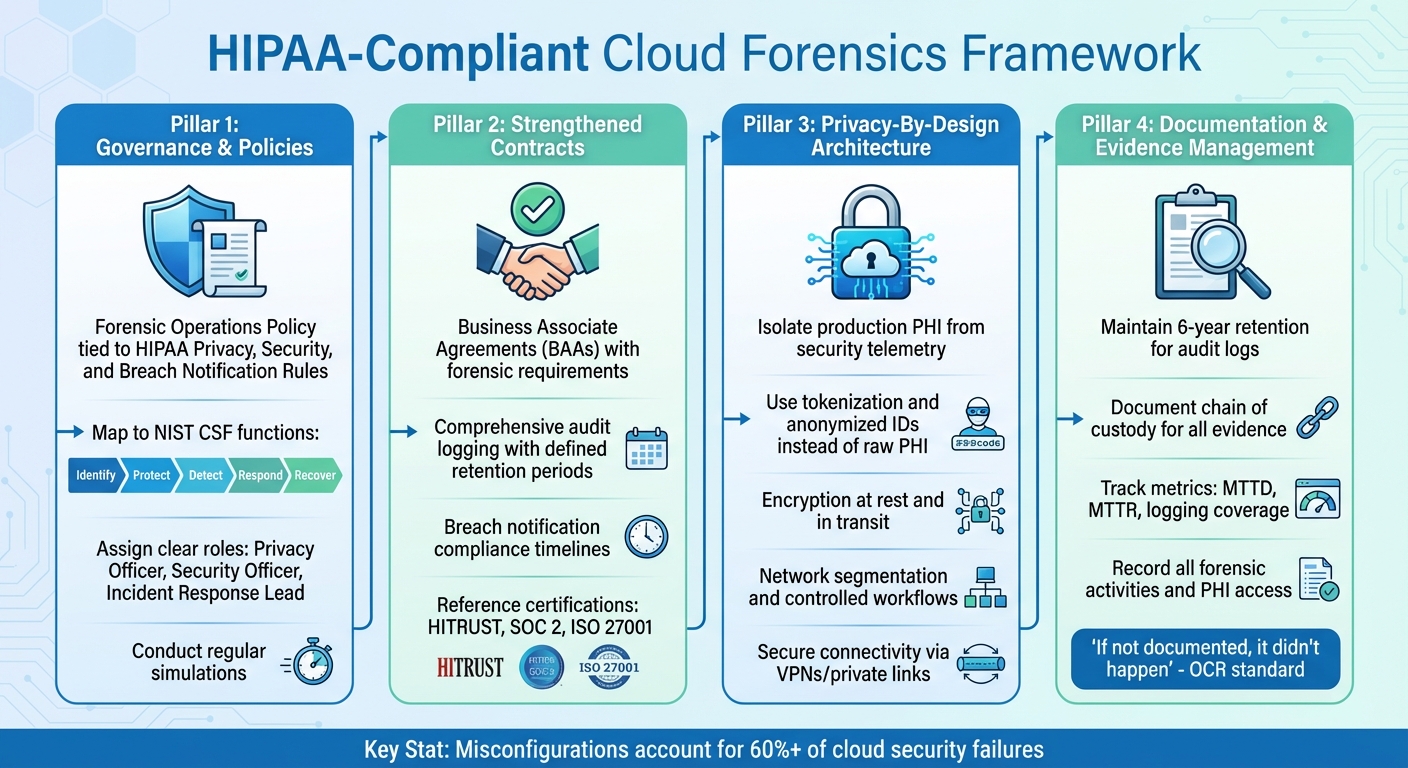
HIPAA-Compliant Cloud Forensics Framework: 4 Essential Pillars
HIPAA Risks in Cloud Forensics
This section focuses on the specific risks tied to HIPAA compliance during cloud forensic investigations, expanding on the earlier discussion of compliance challenges.
Unclear Roles and Responsibilities
The shared-responsibility model in cloud computing often leads to confusion during forensic investigations. Cloud service providers typically handle the security of the infrastructure, but healthcare organizations are responsible for safeguarding their data, applications, and configurations. When an incident occurs, it’s not always clear who should handle tasks like preserving logs, retaining snapshots, or exporting evidence containing electronic protected health information (ePHI). Without a Business Associate Agreement (BAA) that clearly outlines forensic responsibilities - such as logging, data retention, and evidence export - crucial cloud artifacts may be overwritten or lost. This lack of clarity can slow down investigations and leave organizations vulnerable to scrutiny under the HIPAA Security Rule.
Excessive PHI Collection During Investigations
Forensic investigations in cloud environments can sometimes result in collecting far more PHI than necessary, which conflicts with HIPAA's minimum necessary standard. For instance, capturing a full disk image or a broad snapshot in a multi-tenant environment might unintentionally include sensitive data like medical records, imaging files, or patient identifiers from unrelated departments. This over-collection not only increases the workload required to secure and track unnecessary PHI but also broadens the scope of compliance reviews. Misconfigurations, which account for more than 60% of cloud security failures[3], further complicate the process. These issues make it challenging to adhere to HIPAA’s stringent guidelines while conducting forensic investigations.
Chain of Custody and Audit Trail Problems
Preserving forensic evidence in the cloud is especially difficult due to the transient nature of cloud resources. Virtual machines, containers, and serverless functions can be created and terminated within minutes, making it easy for evidence to disappear if logging isn’t configured to capture and centralize data quickly. Short log retention periods, missing object-level logging, and inconsistent timestamps across services can make it nearly impossible to reconstruct a reliable timeline of PHI access or potential exfiltration. Without comprehensive, tamper-proof logs that detail who accessed data and when, proving the integrity of evidence becomes a challenge. Additionally, demonstrating that "reasonable and appropriate" monitoring safeguards were in place is difficult. Reports from the Office for Civil Rights (OCR) frequently highlight deficiencies in risk analyses and access controls as leading causes of HIPAA violations[4].
Building a HIPAA-Compliant Forensic Framework
Healthcare organizations need a forensic framework that not only complies with HIPAA regulations but also integrates governance, contracts, and technical architecture. According to HHS guidelines, any cloud provider managing Protected Health Information (PHI) is considered a business associate and must sign a Business Associate Agreement (BAA) [6]. Below, we’ll break down the key elements - governance policies, contractual agreements, and architectural safeguards - necessary to create a solid HIPAA-compliant forensic framework. This structure ensures accountability, protects evidence, and enforces privacy at every level, from internal policies to vendor contracts.
HIPAA-Aware Governance and Policies
To align forensic processes with HIPAA requirements, healthcare organizations should incorporate forensic procedures into their existing privacy and security policies. Start by creating a Forensic Operations Policy that ties directly to the HIPAA Privacy, Security, and Breach Notification Rules, while also following guidance from the NIST Cybersecurity Framework and NIST SP 800-66 [4][8]. This policy should outline how PHI is accessed during investigations and require thorough documentation of every action taken.
Map forensic activities to the NIST CSF functions to ensure a structured approach:
- Identify: Maintain detailed inventories of assets and PHI.
- Protect: Implement access controls and encryption to safeguard data.
- Detect: Enable forensic-ready logging to monitor and capture activity.
- Respond: Develop formal investigation playbooks for handling incidents.
- Recover: Focus on restoring data and learning from incidents.
Assign clear roles and responsibilities to key personnel, such as the HIPAA Privacy Officer, Security Officer, and incident response lead. These individuals should oversee forensic procedures, approve access to high-risk evidence, and review actions taken during investigations [4][6]. Regular simulations are essential to test and refine these policies, ensuring they balance PHI protection with effective evidence collection.
Strengthened BAAs and Vendor Contracts
Business Associate Agreements (BAAs) and Service Level Agreements (SLAs) must explicitly require cloud providers to support forensic efforts. This includes preserving, producing, and securely transferring logs and forensic data in compliance with encryption and key management standards [2][6][9][10]. Contracts should also mandate:
- Comprehensive audit logging: Track administrator actions, PHI access, and configuration changes, with retention periods tailored to your regulatory and investigative needs.
- Performance targets: Define expectations for log search speed, system uptime, and availability of ePHI-related systems.
- Breach notification compliance: Ensure providers notify you promptly of subpoenas, law enforcement requests, or breaches, adhering to HIPAA Breach Notification Rule timelines [6].
To confirm a provider’s forensic and security capabilities meet industry standards, reference certifications like HITRUST, SOC 2, or ISO 27001 in agreements [2][3]. Tools such as Censinet RiskOps™ can help continuously assess cloud vendors’ compliance with HIPAA-related security and forensic requirements, including logging, incident response readiness, and evidence-handling practices. This proactive approach helps identify and address gaps before any incidents occur [2][9].
Privacy-By-Design Cloud Architectures
Implementing privacy-by-design principles is crucial for securing PHI while ensuring forensic readiness. Start by isolating production PHI from security telemetry. Use dedicated logging services that store metadata - such as hashes, anonymized IDs, or tokens - rather than raw PHI [2][3][9]. Configure logs to avoid recording sensitive identifiers, like patient names or Social Security numbers, in clear text. Instead, maintain mappings between tokens and real identifiers in tightly controlled clinical systems [9].
Additional architectural safeguards include:
- Network segmentation: Separate logging infrastructure from other systems using distinct accounts or projects.
- Controlled workflows: Require higher-level approvals for investigators to pivot from minimal PHI logs to clinical records, ensuring access is documented and justified [3][4].
- Encryption: Enforce encryption at rest and in transit using modern algorithms, ideally with customer-managed keys or hardware security modules [2][9][10].
- Secure connectivity: Use private links or VPNs to transfer logs securely to forensic tools. Ensure cloud services provide APIs or interfaces for exporting logs and snapshots without granting broad access to production systems [3][9].
HIPAA-Compliant Methods for Cloud Forensic Investigations
Preparation and Forensic Readiness
Getting your cloud systems ready for secure, HIPAA-compliant investigations starts with proactive planning. First, enable tamper-proof, encrypted audit logging with standardized timestamps (like NTP) to meet HIPAA’s six-year retention rule. Make sure essential systems are set up to log access events, API calls, and admin actions, storing this data in immutable repositories with strict access controls.
Develop clear forensic playbooks that outline who can authorize access to logs, what Protected Health Information (PHI) can be viewed, and which tools are approved for investigations. Use strong authentication measures and role-based access controls for both administrative and forensic tools. Tools like Censinet RiskOps™ can simplify this process by centralizing third-party risk data and monitoring logs, access permissions, and cloud configurations for systems handling PHI. With this groundwork in place, you’ll be better prepared for secure and focused evidence collection when incidents occur.
Evidence Collection with Minimal PHI Exposure
To remain HIPAA-compliant while minimizing risk, collect only the data that’s absolutely necessary. Avoid full-disk images and focus on specific log segments or metadata tied to the incident. For example, narrow your scope to defined timeframes, particular user accounts, storage buckets, or API calls.
Start by gathering metadata-level artifacts - such as user IDs, timestamps, IP addresses, roles, resource identifiers, and action types. Avoid collecting full clinical content like medical notes, images, or other free-text PHI unless it’s critical to the investigation. Design your logging systems to capture security-relevant metadata rather than sensitive medical information. Use cloud-native tools like granular export filters, column-level encryption, and object-level access logs to isolate only the impacted data segments. If disk or snapshot collection is unavoidable, separate investigations by environment to ensure PHI in production systems doesn’t mix with non-PHI data.
Chain of Custody and Investigator Access Controls
Once evidence is collected, maintaining a secure and documented chain of custody is essential. Keep detailed records of every step - who requested and gathered the evidence, the specific data sources involved (like cloud accounts or storage buckets), timestamps for all actions, tools and commands used, integrity checks (e.g., hash values), and where the evidence is stored. These records should be part of your HIPAA compliance documentation and retained for the required period.
Treat forensic tools and evidence repositories containing PHI as high-risk systems. Limit access to a small, thoroughly vetted group of investigators, privacy officers, and legal personnel. Enforce multi-factor authentication for any accounts with access to evidence. Protect storage locations with network-level safeguards like private subnets, VPNs, or zero-trust frameworks, and use IP allowlists for added security. Encrypt all evidence, both at rest and in transit, using strictly managed encryption keys. Enable detailed audit logging to track all access, exports, or modifications of evidence. Regularly review and update permissions to ensure only authorized users have access, and disable third-party accounts as soon as their involvement ends.
sbb-itb-535baee
Implementing HIPAA-Compliant Forensics in Healthcare
Integrating Forensics into Incident Response Plans
Clearly define the triggers for initiating forensic activities in your incident response plan. These could include suspected exfiltration of PHI, unauthorized system access, or issues like cloud misconfigurations. For each phase of incident response - preparation, detection, analysis, containment, eradication, and recovery - assign specific forensic tasks. Examples include preserving volatile cloud logs, capturing system snapshots, and meticulously documenting every instance of access to systems containing PHI [7][4].
To ensure patient safety, prioritize keeping systems available for direct care. Instead of analyzing live production systems like EHR or PACS, work with read-only forensic copies. Establish clear guidelines for when systems might need to be taken offline, especially in situations where patient safety is at stake [7]. A RACI model (Responsible, Accountable, Consulted, Informed) can help clarify when to involve compliance, privacy, legal, and clinical leadership. This approach ensures your forensic actions align with OCR’s expectations for timely breach investigations, risk assessments, and notifications [4][6]. To maintain readiness, conduct annual tabletop exercises to test forensic procedures in cloud-based environments [3][5].
By linking forensic activities to specific incident triggers and practicing these steps, you can strengthen your response capabilities while staying compliant with HIPAA regulations.
Continuous Monitoring and Risk Prioritization
HIPAA's Security Rule mandates ongoing monitoring of systems that handle ePHI to safeguard confidentiality, integrity, and availability [3][5]. Centralize logs from EHRs, clinical applications, cloud infrastructure (such as API calls, IAM changes, and storage access), network devices, and identity providers into a SIEM. Ensure these logs meet HIPAA's retention and documentation requirements. Use the SIEM to monitor for anomalies, like unexpected PHI access, irregular login patterns, or unusual data transfers [3][5].
Tools like Censinet RiskOps™ can work alongside SIEM systems to prioritize risks tied to PHI-bearing systems and third parties. This platform centralizes risk assessments for vendors and internal systems, helping you identify where PHI exposure is highest. With this insight, you can focus on implementing stronger forensic and logging controls for high-risk areas. For example, you might enforce stricter BAAs, demand detailed audit logs, or prioritize specific systems for forensic testing during tabletop exercises. Additionally, integrated workflows allow you to collaborate with vendors on critical response elements like log retention policies, evidence export formats, and response SLAs. This ensures you have access to the forensic data you need during real incidents.
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare." - Matt Christensen, Sr. Director GRC, Intermountain Health [1]
Regularly validate your SIEM logs through completeness checks and mock investigations to confirm their accuracy and reliability [4][6]. Also, perform ongoing risk analysis and configuration reviews for cloud services handling PHI. Focus on areas like logging capabilities, retention periods, MFA, network segmentation, and least-privilege access [3][4][6].
Pair these monitoring efforts with meticulous documentation of forensic activities and evidence management processes.
Documentation and Evidence Management
The OCR requires covered entities to maintain detailed documentation related to policies, procedures, training, risk analyses, BAAs, breach notifications, and digital forensic activities [4]. Keep a centralized repository for all forensic records, including timelines, evidence catalogs, investigative conclusions, and decisions related to PHI access and containment [4][6].
During an investigation, document every detail of the evidence chain of custody. Record who collected the evidence, when it was collected, how it was stored, and every transfer. This ensures the data remains admissible and meets OCR review standards [7]. Breach investigations should also align with the Breach Notification Rule. Document risk assessments for potential compromises, explain the rationale for notification decisions, and keep detailed timelines of notifications issued [6]. From OCR's perspective, if it's not documented, it didn’t happen - so ensure every forensic action and remediation effort is thoroughly recorded [4][6].
Track metrics to measure and improve your forensic processes over time. Key metrics include the mean time to detect (MTTD) and respond (MTTR) to PHI-related incidents, the percentage of PHI-bearing systems with centralized logging, the number of incidents where forensic data was incomplete, and the frequency of forensic tabletop exercises. Use these metrics to identify gaps, justify investments, and demonstrate progress to boards and regulators [3][7][4]. When tracked within a risk platform, these metrics can also help correlate forensic readiness with broader risk trends and resource allocation, ensuring better long-term outcomes.
Conclusion
Navigating HIPAA-compliant cloud forensics is a continuous effort that hinges on strong governance, well-defined contracts, and the use of integrated tools. Healthcare organizations must ensure their forensic activities align with the HIPAA Privacy, Security, and Breach Notification Rules by incorporating clear policies and detailed forensic playbooks into their incident response strategies. This governance framework enforces strict access controls, establishes robust logging standards, and supports ongoing risk management efforts - all essential for maintaining HIPAA compliance [3][4].
Having well-drafted BAAs (Business Associate Agreements) and vendor contracts is equally critical. HIPAA mandates that covered entities establish BAAs with cloud service providers and other vendors handling PHI. These agreements should clearly outline forensic collaboration requirements, such as log retention policies, evidence export procedures, and breach notification responsibilities [2][3][6]. Rather than treating BAAs as static legal documents, leaders should view them as dynamic tools that adapt to evolving forensic needs.
Cloud architectures designed with privacy in mind enhance forensic readiness through techniques like tokenization, pseudonymization, encryption, and comprehensive audit logging [2][5]. These measures not only meet HIPAA's "minimum necessary" standard but also streamline investigations, making them faster and more secure. Tools such as Censinet RiskOps™ can assist organizations in identifying HIPAA-compliant cloud and forensic vendors, addressing any gaps, and prioritizing improvements across patient data systems, clinical applications, medical devices, and supply chains.
Ultimately, success in this area requires collaboration across legal, compliance, security, IT, clinical, and risk management teams. By operationalizing governance, refining contracts, embedding privacy into cloud systems, and leveraging advanced risk tools, healthcare organizations can respond to incidents swiftly and effectively without compromising compliance. Each investigation becomes an opportunity to bolster cloud security and forensic preparedness while showcasing due diligence to regulators.
FAQs
What challenges do healthcare organizations face in maintaining HIPAA compliance during cloud forensic investigations?
Healthcare organizations encounter a range of hurdles when striving to maintain HIPAA compliance during cloud forensic investigations. These challenges include preserving data integrity and ensuring a reliable chain of custody in the ever-changing landscape of cloud environments. They must also adhere to stringent HIPAA privacy and security standards throughout the investigative process. Adding to the complexity is the nature of multi-tenant cloud infrastructures, where shared resources among multiple organizations can complicate compliance efforts.
Overcoming these obstacles demands the use of strong protocols and advanced tools designed to protect sensitive patient information while meeting all regulatory obligations.
How can healthcare organizations define clear responsibilities with cloud providers?
Healthcare organizations can define responsibilities with cloud providers by drafting detailed agreements that specify the roles and obligations of each party. These agreements should cover critical areas like data security, HIPAA compliance, and incident response protocols to ensure clarity and accountability.
Conducting regular risk assessments is equally important to maintain compliance and uncover potential vulnerabilities. Tools like Censinet RiskOps™ simplify this process by offering a collaborative platform for documenting and overseeing risk management activities. This centralized approach helps organizations manage risks associated with patient data and other sensitive assets more effectively.
How can healthcare organizations protect PHI during cloud forensic investigations?
To protect Protected Health Information (PHI) during cloud forensic investigations, it’s crucial to establish robust measures from the start. Begin by enforcing strict access controls so that only authorized individuals can access sensitive information. Make sure PHI is encrypted both during transmission and while stored to block unauthorized access. Use isolated forensic copies of the data to reduce exposure risks, and always conduct analysis within secure, HIPAA-compliant environments.
Don’t overlook the importance of regular training for your team on HIPAA guidelines and proper handling of PHI during investigations. Tools like Censinet RiskOps™ can also be invaluable for monitoring risks and addressing vulnerabilities, ensuring compliance while keeping patient information secure throughout the investigation.


