HIPAA-Compliant File Transfer Protocols
Post Summary
Transferring sensitive health data? Here's what you need to know: HIPAA-compliant file transfer protocols protect electronic protected health information (ePHI) during transmission. The three most secure options are SFTP, FTPS, and HTTPS. Each offers encryption, authentication, and logging to meet HIPAA's strict security standards. Here's a quick breakdown:
- SFTP: Encrypts data and commands using SSH. Ideal for automated transfers with strong key-based authentication and single-port simplicity.
- FTPS: Adds TLS encryption to FTP but requires more complex configurations, especially for firewall settings.
- HTTPS: Secures web-based transfers with TLS, making it user-friendly for patient portals and APIs.
Choosing the right protocol depends on your needs. Use SFTP for back-end automation, HTTPS for user-facing tools, and FTPS for legacy systems. Always ensure strong encryption, detailed logging, and proper authentication to maintain compliance.
1. SFTP
SFTP (SSH File Transfer Protocol) stands out as a secure method for transmitting ePHI (electronic protected health information), aligning with HIPAA requirements. Operating over SSH on port 22, SFTP encrypts both commands and data by default, ensuring that sensitive credentials and PHI are never sent in plain text. Unlike older FTP protocols that leave data exposed, SFTP encrypts the entire session, making it a reliable choice for securely transferring ePHI.
Encryption Strength
SFTP leverages SSH for encryption, commonly using AES‑128 or AES‑256 to protect data confidentiality and HMAC‑SHA2 for ensuring integrity. While HIPAA doesn’t prescribe specific encryption standards, industry norms recommend AES‑256 for safeguarding data both in transit and at rest. To maintain compliance, it’s critical to disable outdated algorithms like 3DES and MD5‑based MACs and enforce RSA keys with a minimum length of 2,048 bits. Many platforms designed for HIPAA compliance rely on AES‑256 encryption paired with FIPS 140‑2 validated cryptographic modules, providing a solid security foundation that integrates seamlessly with advanced authentication methods.
Authentication Options
For HIPAA-compliant environments, key‑based authentication using SSH public keys is often preferred. This approach, combined with strong passphrases and multi‑factor authentication (MFA) where possible, enhances security for accounts handling ePHI. While SFTP supports various authentication methods, it’s best practice to disable password‑only authentication for sensitive accounts and enforce unique user IDs with least‑privilege permissions. Many HIPAA-focused SFTP platforms also incorporate features like role‑based access control (RBAC), IP allowlisting, and directory service integration (e.g., Active Directory or SSO) to meet access control requirements under the HIPAA Security Rule. Comprehensive logging further bolsters these authentication measures, ensuring a complete audit trail.
Logging and Auditability
HIPAA mandates robust audit controls, and SFTP implementations should log all key activities, such as authentication attempts, file uploads, downloads, deletions, and permission changes. These logs should be retained in accordance with organizational policies and include detailed information like user identity, timestamps, file paths, IP addresses, and action types. Many HIPAA-ready file transfer solutions can forward logs to a SIEM for continuous monitoring. To meet compliance standards, ensure logs are tamper-evident, access-controlled, and regularly reviewed.
Operational Fit
SFTP simplifies firewall management by operating through a single port, unlike FTPS, which requires separate channels for control and data, often leading to complex configurations. This simplicity, combined with its compatibility with scripting languages and integration tools, makes SFTP ideal for automated workflows like nightly EHR exports, lab result transfers, or claims submissions. For healthcare organizations looking to reduce on-premises infrastructure, cloud-native managed file transfer platforms offer features such as AES‑256 encryption, detailed audit trails, and scalable performance. When outsourcing SFTP services to third-party providers, it’s essential to secure a Business Associate Agreement (BAA) and clearly outline responsibilities for encryption, logging, and data retention. SFTP’s security features and ease of integration make it a strong choice for HIPAA-compliant data transmission.
2. FTPS
FTPS (FTP over SSL/TLS) builds upon the traditional FTP protocol by adding SSL/TLS encryption, transforming the otherwise insecure FTP into a safer option for transmitting ePHI - provided it's properly configured. Unlike plain FTP, which transmits credentials and data in cleartext, FTPS secures both the control and data channels. To meet HIPAA requirements, organizations must enforce TLS 1.2 or TLS 1.3, disable outdated SSL/TLS versions, and use strong cipher suites like AES-128 or AES-256 with GCM and ECDHE key exchange. These measures ensure both confidentiality and forward secrecy [2]. Below, we’ll explore FTPS’s encryption, authentication, logging, and operational requirements for HIPAA compliance.
Encryption Strength
FTPS uses the same TLS infrastructure as HTTPS, allowing administrators to implement strict certificate validation processes. This includes verifying CN/SAN fields, checking certificate validity dates, and confirming revocation status through OCSP or CRL. Weak ciphers can be disabled, and encrypted transfers are enforced using the PROT P command [2]. Many HIPAA-compliant file transfer solutions rely on FIPS 140-2 validated encryption modules and default to AES-256 encryption to meet industry standards. To stay compliant, administrators must disable anonymous FTP access, enforce TLS for all connections, and regularly rotate both certificates and credentials.
Authentication Options
FTPS supports several authentication methods, including username/password combinations, TLS client certificates, and integration with directory services like Active Directory or LDAP. Multi-factor authentication (MFA) is also supported [2] [5]. Best practices for HIPAA environments include assigning unique user IDs with strong passwords, implementing MFA for privileged or remote access, and using certificate-based service accounts to mitigate credential theft risks. Additionally, many managed file transfer servers offer features like role-based access control (RBAC), IP allowlisting, and session timeouts to enforce least-privilege principles [1] [5].
Logging and Auditability
For HIPAA compliance, FTPS must log all control and data channel activities. This includes logons, logoffs, authentication failures, file transfers (uploads, downloads, renames, deletions), and administrative actions. These logs should capture user identities, actions, timestamps, and source IP addresses [2] [5]. To support audits and investigations, logs should be forwarded to a SIEM or centralized logging platform and retained according to organizational policies - often for six years or more.
Operational Fit
FTPS is commonly used by healthcare organizations that need to work with legacy FTP-based systems or partners unable to transition to SFTP [2]. It’s particularly effective for batch or large-file transfers between enterprises, HIS/EMR vendors, or payers, provided both parties support FTPS. However, its reliance on separate control and data channels adds complexity. For instance, in passive mode, the server opens a range of high-numbered ports for data connections, which must be allowed through firewalls and inspected by TLS-aware devices. This makes FTPS more challenging to manage compared to SFTP’s single-port design.
For example, a U.S. hospital might deploy an Explicit FTPS endpoint in a DMZ, restrict passive port ranges, integrate Active Directory with MFA, and enforce certificate-based authentication - all while maintaining centralized logs in line with policy. When outsourcing FTPS services to third-party providers, it’s critical to secure a Business Associate Agreement (BAA) and clearly define responsibilities related to encryption, logging, and data retention to ensure HIPAA compliance. While FTPS can meet HIPAA standards, it requires careful configuration and ongoing management to do so effectively.
3. HTTPS
HTTPS secures standard web traffic by using an encrypted tunnel, making it a preferred protocol for patient portals, clinician dashboards, and application-to-application exchanges that handle electronic Protected Health Information (ePHI) [2]. Unlike SFTP and FTPS, which require specialized software, HTTPS works seamlessly with all browsers and mobile apps. This compatibility allows secure ePHI exchanges without additional tools. When configured with strong TLS settings, HTTPS satisfies HIPAA's transmission security requirements just as effectively as SFTP or FTPS [2]. Its widespread adoption also simplifies the enforcement of robust encryption standards.
Encryption Strength
HTTPS relies on TLS (Transport Layer Security) to safeguard data as it travels. For HIPAA compliance, organizations must implement TLS 1.2 or TLS 1.3 and disable outdated protocols like SSL, TLS 1.0, and TLS 1.1 [2]. Server configurations should enable strong cipher suites, such as AES-128 or AES-256 with GCM mode, and use elliptic-curve key exchange while disabling weak ciphers [2]. Many platforms designed for HIPAA compliance use TLS 1.2+ for data in transit and AES-256 for data at rest [5]. Additional security measures include enabling HSTS (HTTP Strict Transport Security) to prevent protocol downgrades and using OCSP stapling to ensure reliable certificate validation [2].
Authentication Options
HTTPS supports multiple layers of authentication to secure access to ePHI. At the application level, healthcare systems often require username-password combinations with enforced complexity, supplemented by multi-factor authentication (MFA) to reduce the risk of credential theft [1][3][6]. Larger health systems frequently integrate single sign-on (SSO) using protocols like SAML or OpenID Connect, tied to identity providers such as Azure AD. This centralizes management of user onboarding, offboarding, and access policies [5][6]. For higher-security scenarios, such as administrative access or server-to-server communication, mutual TLS (mTLS) with client certificates can cryptographically verify identities [5]. Additionally, role-based access controls (RBAC) add another layer of restriction, defining what each user can do with PHI [1][3][5].
Logging and Auditability
The HIPAA Security Rule mandates detailed audit controls, and HTTPS-based systems must log key events such as logins, file uploads and downloads, link sharing, permission changes, and administrative actions [1][5][6]. These logs should capture information like user IDs, IP addresses, device details, timestamps, and success or failure codes [2]. Many HIPAA-compliant platforms offer detailed audit trails that track every file action and can be integrated with SIEM tools for centralized monitoring and alerts [5][4]. Logs must be stored in tamper-evident, centralized systems and retained based on organizational policies - often for six years or more - to support investigations and compliance audits [2][4].
Operational Fit
HTTPS operates over TCP port 443, which is already open in most hospital and clinic networks, simplifying deployment without requiring major firewall adjustments [5][6]. Its native browser compatibility makes it easy for clinicians and patients to use [6][4]. HTTPS is particularly well-suited for patient portals, clinician dashboards, and application-to-application exchanges, including handling large-object uploads through chunked transfers or pre-authorized URLs [2]. It also integrates naturally with workflows like telehealth, remote monitoring, and interoperability APIs. To enhance security, organizations should deploy a Web Application Firewall (WAF) and implement rate limiting to protect HTTPS endpoints handling PHI. Regular testing for large files and high-traffic scenarios is also crucial [2]. When outsourcing HTTPS-based file transfer services, it’s essential to secure a Business Associate Agreement (BAA) and clearly define responsibilities for encryption, logging, and data retention to ensure HIPAA compliance.
sbb-itb-535baee
Strengths and Weaknesses
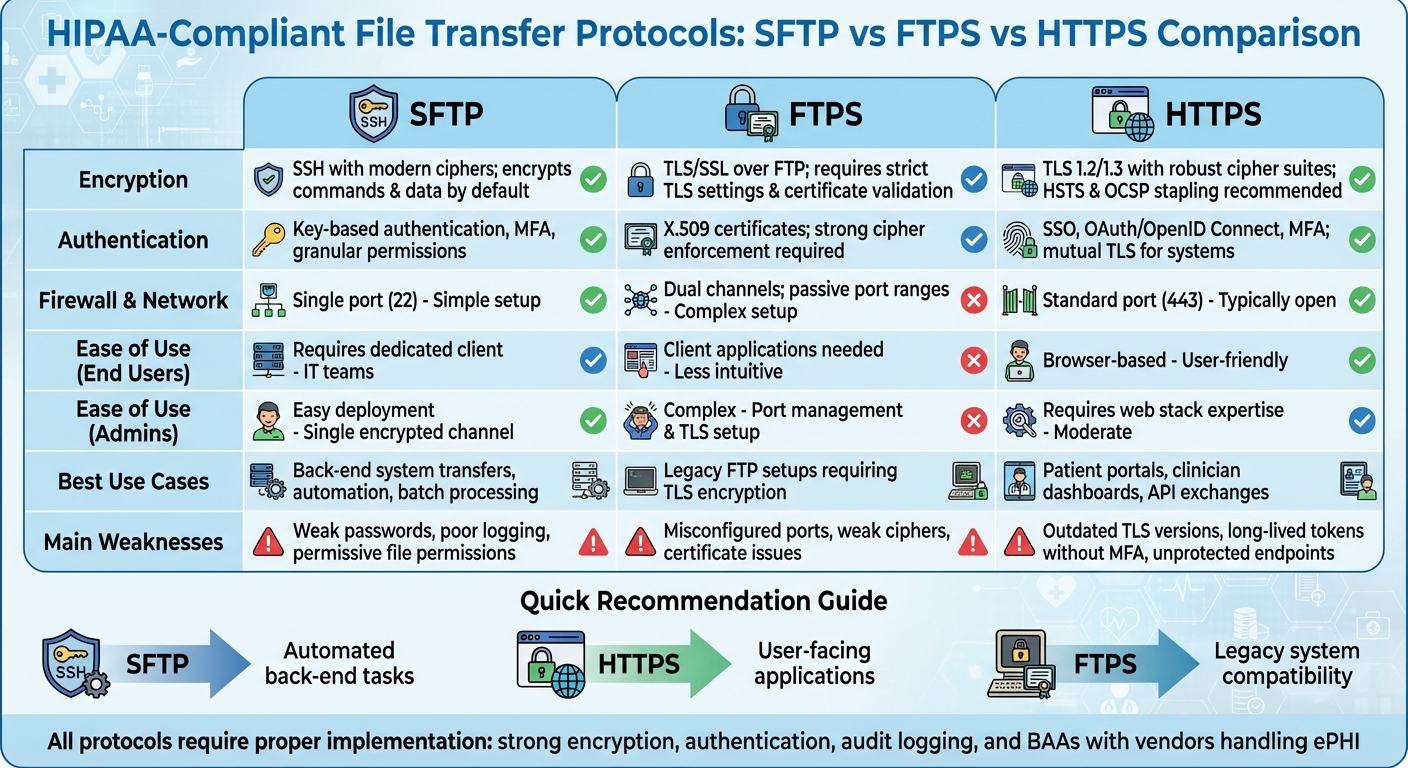
HIPAA-Compliant File Transfer Protocols Comparison: SFTP vs FTPS vs HTTPS
Based on our protocol reviews, here's a detailed look at how these protocols stack up in securing electronic Protected Health Information (ePHI).
Each protocol has its own set of trade-offs when it comes to protecting ePHI during transfers. SFTP operates through a single port (usually 22), making it easier to manage firewall rules and automate processes. It encrypts both commands and data by default using modern SSH ciphers and supports robust security features like key-based authentication, multi-factor authentication (MFA), and granular permissions (e.g., chrooted directories). However, weak operational practices - such as poor password management, insufficient logging, or overly permissive file permissions - can undermine its HIPAA compliance.
FTPS, on the other hand, uses TLS encryption layered over FTP but comes with a dual-channel design for control and data, which complicates configuration. Administrators need to carefully set up explicit or implicit FTPS modes, define passive port ranges, and align these settings across firewalls and NAT devices. Missteps like misconfigured passive ports, fallback to unencrypted FTP, or skipping certificate validation can expose sensitive data. While FTPS is often used to accommodate legacy FTP workflows, it can lead to higher troubleshooting demands and greater risks of configuration errors that could threaten HIPAA compliance.
HTTPS shines in ease of use, as it works natively in any browser, making it a go-to for patient portals, clinician dashboards, and REST APIs. It benefits from advanced web security tools like web application firewalls (WAFs), content delivery networks (CDNs), and support for SSO and MFA. However, risks include using outdated TLS versions, long-lived tokens without MFA, and unprotected endpoints. To safeguard ePHI, HTTPS deployments require strong input validation, secure session management, and well-designed APIs.
Here’s a side-by-side comparison of SFTP, FTPS, and HTTPS in the context of HIPAA compliance:
| Aspect | SFTP | FTPS | HTTPS |
|---|---|---|---|
| Encryption | Employs SSH with modern ciphers; encrypts commands and data by default | Utilizes TLS/SSL over FTP; demands strict TLS settings and certificate validation | Relies on TLS 1.2/1.3 with robust cipher suites; HSTS and OCSP stapling recommended |
| Authentication | Offers key-based authentication, MFA, and granular permissions (e.g., chrooted directories) | Depends on X.509 certificates; requires strong cipher enforcement and disabling of non-encrypted FTP | Supports SSO, OAuth/OpenID Connect, and MFA; can use mutual TLS for system authentication |
| Firewall & Network | Operates on a single port (22), simplifying firewall and automation setups | Uses separate control and data channels; passive port ranges complicate firewall/NAT configurations | Uses the standard port (443), which is typically open in most networks |
| Ease of Use (End Users) | Requires a dedicated client, making it better suited for IT teams | Relies on client applications and can be less intuitive due to explicit/implicit modes | Browser-based and user-friendly, ideal for clinicians and patients |
| Ease of Use (Admins) | Easier to deploy and maintain with a single encrypted channel | More complex due to port management and TLS setup | Demands web stack expertise (e.g., TLS hardening, WAF setup, session management) |
| Logging & Auditing | Supports centralized logging for connections, authentication, file operations, and admin changes | Offers detailed logging across control/data channels; proper setup is critical | Logs all HTTPS requests, often with structured audit trails |
| Best Use Cases | Perfect for back-end system-to-system transfers, automation, and batch processing | Common in legacy FTP setups requiring TLS encryption | Best for patient portals, clinician dashboards, and API-based data exchanges |
| Main Weaknesses | Can be compromised by weak passwords, poor logging, or overly permissive file permissions | Prone to errors from misconfigured ports, weak ciphers, or certificate issues | Risks include outdated TLS versions, long-lived tokens without MFA, or unprotected endpoints |
This breakdown highlights the strengths and vulnerabilities of each protocol, helping organizations choose the right tool for their specific ePHI transfer needs.
Conclusion
The discussion highlights the importance of aligning your choice of file transfer protocols with specific workflows and security requirements. Here’s a quick breakdown: SFTP is ideal for automated back-end tasks thanks to its single-port operation, simplified firewall configurations, key-based authentication for scripting, and built-in encryption and audit logging. HTTPS is perfect for patient portals, clinician dashboards, and API-driven data exchanges, offering browser-based access, Single Sign-On (SSO), Multi-Factor Authentication (MFA), and user-friendly interfaces. Meanwhile, FTPS is still relevant for legacy FTP workflows or when external partners require FTP compatibility, but it demands extra care with passive port configurations, TLS settings, and certificate validation to avoid security missteps.
Maintaining HIPAA compliance hinges on proper implementation. This means using robust encryption, strong authentication, and detailed audit logging. Key and certificate management, data integrity checks, and signed Business Associate Agreements (BAAs) with any Managed File Transfer (MFT) or cloud file-sharing vendor handling ePHI are equally critical.
Tools like Censinet RiskOps™ can simplify the process for healthcare organizations. By standardizing risk assessments and evaluating critical factors like encryption, authentication, logging, and BAA status, Censinet centralizes these efforts. It also facilitates collaboration with vendors to resolve risks, ensuring your protocols are secure, well-documented, and continuously monitored to meet HIPAA requirements and organizational risk thresholds.
To apply these best practices, start by cataloging all file transfers involving PHI and map each one to the most suitable protocol based on its risk profile and operational needs. Update your policies, validate configurations through security assessments or penetration testing, and set up ongoing monitoring with tools like SIEMs or Censinet RiskOps™. As systems evolve and new workflows emerge, regularly revisit your protocol choices to ensure they continue to support both your operational goals and compliance obligations.
FAQs
What should I consider when deciding between SFTP, FTPS, and HTTPS for HIPAA-compliant file transfers?
When choosing a file transfer protocol to ensure HIPAA compliance, prioritize security, encryption, and how well it integrates with your existing systems. Both SFTP and FTPS provide robust encryption methods. SFTP is generally simpler to configure when dealing with firewalls, while FTPS might involve more complex setup. If you're looking for secure, browser-based file transfers, HTTPS is a solid choice.
It's essential to evaluate the sensitivity of the data you handle, your organization's network setup, and whether the protocol meets HIPAA's encryption and security standards. Select the protocol that not only complies with HIPAA but also fits seamlessly into your operational processes.
What steps can I take to ensure my organization's file transfer protocols comply with HIPAA regulations?
To keep your file transfer protocols aligned with HIPAA regulations, it's essential to use secure methods like SFTP, FTPS, and HTTPS. These protocols are designed to encrypt data and ensure safe transmission. Beyond that, you should put safeguards in place, such as access controls to restrict unauthorized entry, audit logs to monitor activity, and regular system updates to keep security measures current.
Another key step is performing regular risk assessments. These evaluations help pinpoint vulnerabilities so you can address them before they become issues. Using specialized cybersecurity platforms can simplify this process, making it easier to manage risks and maintain compliance with HIPAA standards.
What mistakes should I avoid when setting up FTPS for secure ePHI transfers?
When setting up FTPS for transferring secure electronic protected health information (ePHI), there are a few critical steps to ensure your data remains protected. Start with strong encryption protocols to shield data while it's being transmitted. Weak or default credentials should be avoided at all costs, as they are a common target for attackers.
It's also important to validate SSL/TLS certificates to ensure the connection is authentic and secure. Adding session timeouts is another layer of protection, as it limits the risk of unauthorized access during periods of inactivity. Finally, make regular security audits a priority. These audits can uncover potential vulnerabilities and allow you to address them proactively. By following these practices, you can better protect sensitive patient data and stay compliant with regulatory requirements.


