Recent HIPAA Enforcement Cases: Lessons Learned
Post Summary
Major increases in ransomware attacks, phishing breaches, and access‑rights violations.
Solara Medical Supplies’ $3M phishing fine, seven ransomware‑related OCR actions, and OHSU’s $200K access‑rights penalty.
Weak risk analyses, outdated security controls, slow patching, and failing to meet the 60‑day breach notification rule.
Ransomware readiness, business associate oversight, and patient access rights.
Conduct annual risk analyses, implement MFA, maintain BAAs, and improve incident response.
Vendors handling PHI can trigger major breaches and fines if not properly vetted and monitored.
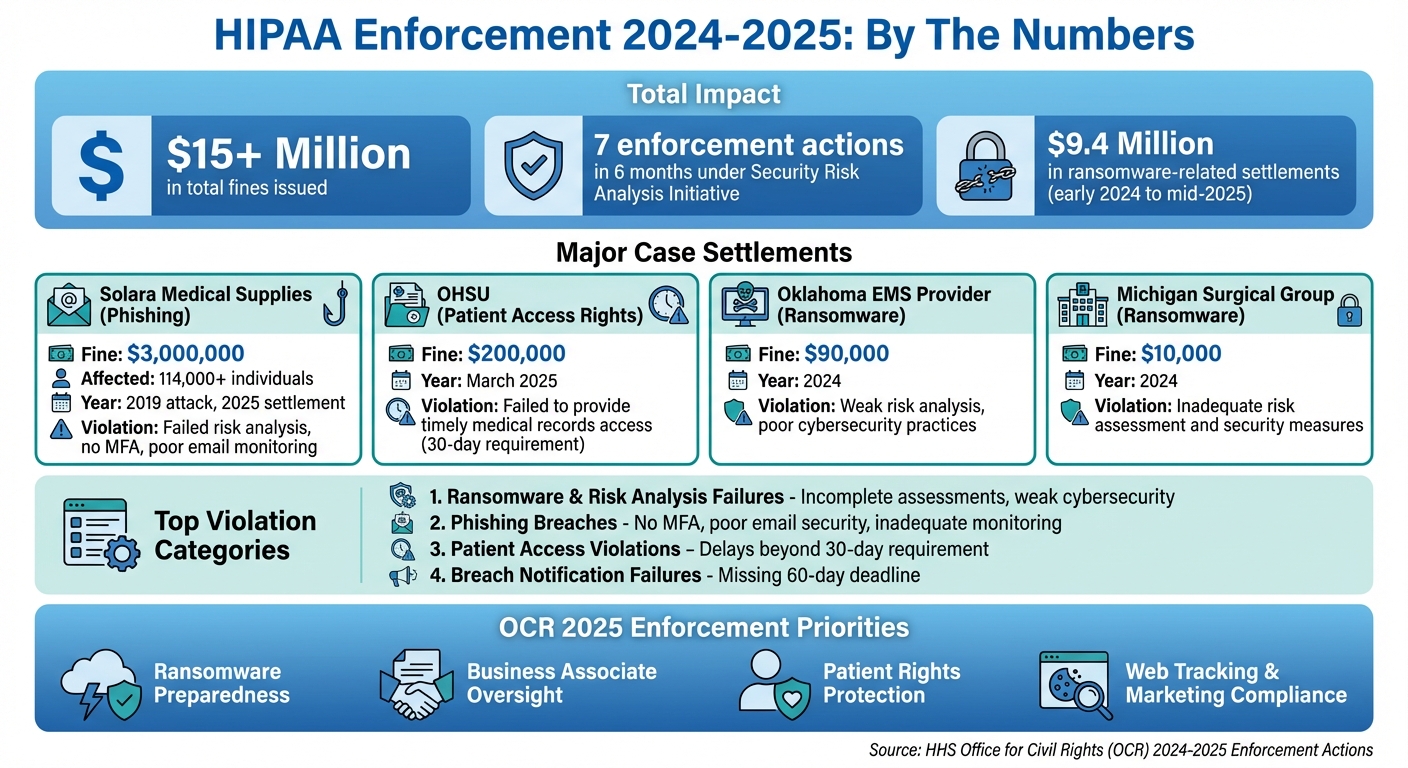
The U.S. Department of Health and Human Services (HHS) Office for Civil Rights (OCR) has intensified HIPAA enforcement, with over $15 million in fines issued across 2024 and 2025. Key issues include ransomware attacks, phishing breaches, and patient access rights violations. Here's what you need to know:
Key Takeaways:
Failure to address these areas risks steep penalties, reputational harm, and operational disruptions. Organizations must prioritize continuous improvement in risk management and cybersecurity to meet HIPAA standards effectively.
2024-2025 HIPAA Enforcement Cases: Fines, Violations and Key Statistics
Recent HIPAA Enforcement Cases (2024–2025)
Phishing Breach: Solara Medical Supplies
In January 2025, the Office for Civil Rights (OCR) announced a hefty $3 million settlement with Solara Medical Supplies, LLC. This penalty stemmed from a phishing attack in 2019 that exposed the protected health information (PHI) of over 114,000 individuals [1]. OCR's investigation revealed critical lapses in Solara's security measures. The company failed to conduct a thorough risk analysis, implement multi-factor authentication, monitor email accounts effectively, and audit email activity. As part of the settlement, Solara agreed to a Corrective Action Plan, which includes revising its risk analysis procedures, strengthening email security, providing workforce training, and submitting regular compliance reports to OCR [1]. This case highlights the importance of proactive cybersecurity measures, an issue OCR has sought to address through its Security Risk Analysis Initiative.
Ransomware Cases Under OCR's Risk Analysis Initiative
In late 2024, OCR launched the "Security Risk Analysis Initiative" to focus on organizations affected by ransomware or similar cyberattacks without conducting proper risk assessments. Within just six months, OCR had taken action against seven entities [3]. These included a $90,000 penalty for an Oklahoma emergency medical services provider, a Massachusetts cloud-based electronic health record (EHR) vendor, and a $10,000 fine for a Michigan surgical group. Common issues across these cases included weak risk analyses, poor risk management strategies, insecure system configurations, delays in applying security patches, and inadequate documentation of incident responses [3]. These enforcement actions emphasize HIPAA's requirement for strong cybersecurity practices, particularly in risk management and timely handling of incidents. OCR also made it clear that HIPAA violations extend beyond technical breaches, covering issues like patient access rights as well.
Right-of-Access Violations: OHSU Case
In March 2025, Oregon Health & Science University (OHSU) faced a $200,000 settlement with OCR for failing to provide patients with timely access to their medical records. The investigation found that OHSU did not have adequate policies or staff training to meet HIPAA’s 30-day access requirement. To address these shortcomings, OHSU has been tasked with standardizing its access procedures, training staff to handle patient and representative requests, and improving compliance monitoring. This case underscores OCR’s stance that access violations are taken as seriously as security breaches [1].
Common Compliance Failures and Enforcement Priorities
Recurring Violations
Recent enforcement actions by the OCR highlight several recurring compliance issues plaguing healthcare organizations. These include incomplete or outdated risk analyses, poor risk management practices, and weak technical safeguards. Many organizations fail to conduct thorough risk analyses when onboarding new vendors or adopting new technologies, leaving significant gaps in their compliance efforts.
Even when vulnerabilities are identified, OCR often finds a lack of follow-through - decisions go undocumented, responsibilities aren't assigned, and remediation efforts aren't tracked to completion. Common technical shortcomings include delayed security patching, inadequate multi-factor authentication, and ineffective logging practices, all of which weaken compliance and increase risk exposure.
Breach notification failures are another frequent problem. Many organizations miss the 60-day deadline to notify affected individuals and OCR, while others fail to update notifications when additional compromised records are discovered months - or even years - later. Violations of the Privacy Rule are also widespread. These include impermissible disclosures of patient information to media outlets, marketers, or third parties without proper authorization, and right-of-access violations where patients are denied timely access to their medical records. For instance, the March 2025 OHSU settlement, which resulted in a $200,000 penalty, emphasized that OCR treats delays in granting access to records as seriously as security breaches.
These repeated compliance failures have directly influenced OCR's enforcement priorities for 2025.
OCR Enforcement Priorities for 2025
In response to these ongoing issues, OCR's 2025 enforcement efforts have zeroed in on ransomware preparedness, business associate oversight, and the protection of patient rights. The Security Risk Analysis Initiative alone has led to seven enforcement actions within six months, all tied to ransomware attacks. These incidents revealed critical gaps, such as inadequate risk analyses, untested backups, and poorly executed incident response plans. From early 2024 to mid-2025, settlements related to these failures totaled approximately $9.4 million, underscoring the costly consequences of non-compliance.
Business associate oversight has also become a major focus. OCR is holding both vendors and the covered entities that fail to properly vet them accountable. Recent cases have involved cloud EHR providers, billing companies, and other business associates whose ransomware attacks or server misconfigurations exposed patient data for extended periods. To address this, organizations are required to maintain up-to-date Business Associate Agreements and conduct regular security assessments of high-risk vendors. Many healthcare entities are now leveraging tools like Censinet RiskOps™ to streamline third-party risk management across their supply chains.
Lastly, enforcement around patient rights remains a priority. OCR continues to advance its Right of Access Initiative, closely monitoring how organizations handle marketing content, web tracking technologies, and the use of identifiable patient information in public-facing materials. This emphasis reflects OCR's commitment to ensuring patients' rights are upheld alongside broader compliance measures.
sbb-itb-535baee
Lessons for Healthcare Organizations
Conduct Thorough Security Risk Analysis
A comprehensive risk analysis across the entire organization is the backbone of HIPAA compliance. The Office for Civil Rights (OCR) has consistently taken enforcement actions against organizations failing to conduct adequate risk assessments, as seen in its Security Risk Analysis Initiative [3][5]. To start, document every system that creates, receives, maintains, or transmits electronic protected health information (ePHI).
Risk analysis isn’t a one-and-done task. It needs to be an ongoing process, updated at least annually or whenever significant changes occur - like adopting a new EHR system, migrating to the cloud, expanding telehealth services, or signing a major vendor contract [3][4]. Your findings should directly inform your risk management plan, which must include specific remediation steps, assigned responsibilities, clear timelines, and budget allocations. When OCR investigates, they expect to see evidence of continuous improvement and executive involvement.
Healthcare-specific tools like Censinet RiskOps™ simplify this process by centralizing risk management activities. They offer standardized assessment templates designed to meet HIPAA Security Rule requirements.
Terry Grogan, CISO at Tower Health, shared that using the platform "allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required"
.
Once a solid risk analysis is in place, healthcare organizations must focus on strengthening defenses against cyber threats.
Strengthen Ransomware and Phishing Defenses
Identifying vulnerabilities through risk analysis is just the first step - addressing those gaps is equally critical. The $3 million settlement with Solara Medical Supplies after a phishing attack illustrates the financial and operational risks tied to weak security measures [1][2]. OCR investigations often reveal common issues such as missing multi-factor authentication (MFA), insufficient least-privilege controls, and untested incident response plans [3][5].
Here’s what to prioritize:
A well-documented incident response plan is equally important. This plan should clearly outline roles, containment procedures, and breach notification protocols. Test its effectiveness with annual tabletop exercises that simulate real-world scenarios. Security awareness training should also go beyond the usual annual presentations. Continuous, behavior-based training - such as simulated phishing campaigns with instant feedback - can significantly improve employee vigilance [5][6].
Improve Vendor and Supply Chain Risk Management
Managing internal risks is only part of the equation. Vendors and external partners must also meet stringent security standards. Recent OCR enforcement actions against business associates, from cloud EHR providers to billing companies, highlight that vendor oversight is a shared responsibility. Covered entities are held accountable when vendors are not properly vetted or when known risks remain unaddressed [3][4][5].
Start by maintaining an up-to-date inventory of all business associates and subcontractors that handle PHI. Perform risk-based due diligence before finalizing contracts.
Business Associate Agreements (BAAs) should clearly outline security expectations, including encryption requirements, multi-factor authentication, logging standards, incident reporting timelines, and subcontractor oversight. Regularly monitor vendor compliance through annual reassessments and independent audits [3][6].
Platforms like Censinet RiskOps™ can streamline vendor management by providing healthcare-specific assessment tools.
James Case, VP & CISO at Baptist Health, explained, "Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with"
.
Conclusion
The enforcement cases from 2024 and 2025 make one thing clear: HIPAA compliance is no simple "check-the-box" task. This year alone, the Office for Civil Rights (OCR) has imposed over $6.6 million in fines, with recent settlements highlighting the steep consequences of poor security practices [1]. Organizations that fail to conduct thorough risk assessments, maintain strong defenses, or honor patient access rights face not only financial penalties but also damage to their reputation.
To avoid these pitfalls, healthcare organizations must embrace a continuous, risk-based approach to management. This means going beyond one-time efforts and addressing vulnerabilities proactively. Key steps include conducting organization-wide risk assessments annually, implementing multi-factor authentication, using secure email filtering, maintaining tested incident response plans, and carefully vetting all vendors handling protected health information (PHI). OCR's seven enforcement actions within six months underline the importance of these strategies [3][5].
Effective risk management in healthcare requires tools designed specifically for the industry's unique challenges. Platforms like Censinet RiskOps™ offer centralized solutions for managing third-party and enterprise risks, automating vendor evaluations, and keeping detailed, auditable records that align with OCR's compliance standards.
As Matt Christensen, Sr. Director GRC at Intermountain Health, explains: "Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare"
.
Beyond avoiding fines, these measures play a critical role in protecting patient data, ensuring operational stability, and preserving trust. Ransomware attacks and breach notifications disrupt care and undermine confidence. By investing in strong risk management frameworks, advanced cyber defenses, and healthcare-specific platforms, organizations can turn compliance into a proactive strategy that safeguards both patients and their own operations.
FAQs
What are the most common cybersecurity issues that lead to HIPAA violations?
Healthcare organizations often face cybersecurity challenges that can lead to HIPAA violations. A big one? Weak access controls. Sharing login details or relying on simple, easily guessed passwords can open the door to unauthorized access. Another issue is inadequate employee training, leaving staff unprepared to handle patient data securely.
Unpatched software vulnerabilities are another major concern. When software isn't updated regularly, it creates gaps that hackers can exploit. Similarly, a lack of routine security assessments means potential risks go unnoticed and unaddressed.
On top of that, failing to monitor for or respond quickly to security incidents can result in breaches of protected health information (PHI). Tackling these issues head-on can help healthcare providers stay compliant and keep sensitive patient data safe.
What steps can healthcare organizations take to strengthen risk management and avoid HIPAA fines?
Healthcare organizations can bolster their risk management efforts by using specialized platforms tailored for ongoing risk assessment and compliance. Tools like Censinet RiskOps™ simplify workflows, minimize manual tasks, and help uncover potential vulnerabilities in critical areas such as patient data, clinical systems, and supply chains.
With these solutions, organizations can enhance their cybersecurity defenses, tackle risks proactively, and ensure adherence to HIPAA regulations. This approach not only strengthens overall security but also helps avoid costly penalties tied to non-compliance.
Why is it important to monitor vendors for HIPAA compliance?
Keeping a close eye on vendors is a critical part of staying HIPAA compliant. Why? Because it ensures that third-party partners handle protected health information (PHI) responsibly and follow strict regulatory guidelines. Without this oversight, healthcare organizations could unintentionally expose sensitive patient data, leading to breaches, hefty fines, and damage to their reputation.
Regularly reviewing and managing vendor practices allows organizations to spot potential weak points early and address them before they become serious issues. This hands-on approach not only protects patient data but also reinforces the organization's overall compliance strategy.
Related Blog Posts
- 8 Best Practices for Patient Data Protection
- HIPAA Cloud Violations: Penalties Explained
- “What 5 Years of OCR Breach Data Tells Us About Where HIPAA Fails”
- “The Hidden Costs of HIPAA Violations: Clinical Downtime and Lost Trust”
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"What are the most common cybersecurity issues that lead to HIPAA violations?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations often face <a href=\"https://www.censinet.com/resource/challenges-remain-for-healthcare-cybersecurity\">cybersecurity challenges</a> that can lead to HIPAA violations. A big one? <strong>Weak access controls.</strong> Sharing login details or relying on simple, easily guessed passwords can open the door to unauthorized access. Another issue is <strong>inadequate employee training</strong>, leaving staff unprepared to handle patient data securely.</p> <p><strong>Unpatched software vulnerabilities</strong> are another major concern. When software isn't updated regularly, it creates gaps that hackers can exploit. Similarly, a <strong>lack of routine security assessments</strong> means potential risks go unnoticed and unaddressed.</p> <p>On top of that, failing to monitor for or respond quickly to security incidents can result in breaches of protected health information (PHI). Tackling these issues head-on can help healthcare providers stay compliant and keep sensitive patient data safe.</p>"}},{"@type":"Question","name":"What steps can healthcare organizations take to strengthen risk management and avoid HIPAA fines?","acceptedAnswer":{"@type":"Answer","text":"<p>Healthcare organizations can bolster their risk management efforts by using <strong>specialized platforms</strong> tailored for ongoing risk assessment and compliance. Tools like Censinet RiskOps™ simplify workflows, minimize manual tasks, and help uncover potential vulnerabilities in critical areas such as patient data, clinical systems, and supply chains.</p> <p>With these solutions, organizations can enhance their cybersecurity defenses, tackle risks proactively, and ensure adherence to HIPAA regulations. This approach not only strengthens overall security but also helps avoid costly penalties tied to non-compliance.</p>"}},{"@type":"Question","name":"Why is it important to monitor vendors for HIPAA compliance?","acceptedAnswer":{"@type":"Answer","text":"<p>Keeping a close eye on vendors is a critical part of staying HIPAA compliant. Why? Because it ensures that third-party partners handle <strong>protected health information (PHI)</strong> responsibly and follow strict regulatory guidelines. Without this oversight, healthcare organizations could unintentionally expose sensitive patient data, leading to breaches, hefty fines, and damage to their reputation.</p> <p>Regularly reviewing and managing vendor practices allows organizations to spot potential weak points early and address them before they become serious issues. This hands-on approach not only protects patient data but also reinforces the organization's overall compliance strategy.</p>"}}]}
Key Points:
Why has HIPAA enforcement increased in 2024–2025?
- Growing ransomware and phishing attacks exposing PHI
- Repeated failures to meet access‑rights requirements
- Weak risk analyses linked to major operational gaps
- Growing regulatory pressure on cybersecurity readiness
What do the most recent OCR enforcement cases reveal?
- $3M Solara phishing settlement for poor email security and missing MFA
- Seven ransomware‑related OCR actions under the Security Risk Analysis Initiative
- OHSU’s $200K penalty for failing to provide timely patient access
- Gaps in documentation, monitoring, and incident response across cases
What recurring violations is OCR focused on?
- Incomplete or outdated risk assessments
- Delayed security patching and weak technical safeguards
- Breach notification delays beyond the 60‑day HIPAA requirement
- Impermissible disclosures and marketing-related Privacy Rule violations
What are OCR’s enforcement priorities for 2025?
- Ransomware preparedness and tested backups
- Stronger business associate oversight and updated BAAs
- Right‑of‑access compliance and faster record fulfillment
- Vendor risk management for cloud EHRs, billing firms, and IT partners
How can healthcare organizations reduce their HIPAA risk?
- Conduct comprehensive, annual risk analyses tied to major system changes
- Strengthen MFA, email filtering, and least‑privilege access controls
- Maintain tested incident response plans and conduct tabletop exercises
- Adopt healthcare‑specific platforms like Censinet RiskOps for visibility
Why is vendor and supply chain oversight essential for HIPAA?
- Vendors handle large volumes of PHI, expanding breach exposure
- Business Associates are increasingly targeted by cyber attackers
- OCR holds covered entities accountable for weak vendor oversight
- Regular assessments and BAAs help prevent compliance failures


