HITRUST Certification Audit Process Explained
Post Summary
The HITRUST certification audit process evaluates an organization’s security controls to ensure compliance with the HITRUST CSF framework, including readiness and validated assessments.
Steps include scoping, readiness assessments, validated assessments, corrective action plans (CAPs), and quality assurance reviews.
A readiness assessment identifies gaps and prepares for certification, while a validated assessment is a formal evaluation by an external assessor.
The process typically takes 9–12 months, including 2 months for readiness, 6 months for remediation, and 3 months for validation and QA.
It demonstrates compliance with multiple regulatory standards, protects PHI, and strengthens cybersecurity posture.
Tools like Censinet RiskOps™ automate evidence collection, track compliance, and simplify third-party risk management.
HITRUST certification is a framework that simplifies compliance for organizations managing protected health information (PHI) by unifying multiple regulatory standards like HIPAA and NIST. It’s especially relevant in cloud environments where responsibilities are shared between providers and customers. Achieving certification involves defining scope, preparing for assessments, and undergoing audits, all while addressing HITRUST’s rigorous control requirements.
Key points to know:
- HITRUST Assessments: Choose from e1 (basic), i1 (moderate), or r2 (advanced) based on your risk level.
- Scope Definition: Identify all systems handling PHI, including cloud services and third-party tools.
- Preparation: Conduct readiness assessments to identify and remediate gaps before validation.
- Audit Process: Includes control testing, evidence collection, scoring, and submission for QA review.
- Maintenance: Certification requires ongoing monitoring, evidence collection, and interim reviews.
Scoping and Preparing for a HITRUST Assessment

Defining Scope in Cloud-Based Healthcare Systems
Getting the scope right is critical for avoiding delays in HITRUST certification. When dealing with cloud-based healthcare systems, you need to include every system that creates, receives, maintains, or transmits PHI or ePHI. This often spans SaaS applications, PaaS components, IaaS resources, and any on-premises systems that interface with them.
Start by identifying all processes that interact with PHI. Think about patient portals, telehealth platforms, billing systems, EHR integrations, analytics tools, and mobile applications. Then, list all the supporting cloud services - this might include AWS accounts, Azure subscriptions, GCP projects, and any related SaaS tools. To make this clearer, create a data flow diagram that tracks how PHI moves between applications, cloud workloads, databases, APIs, and third-party systems. Any component or service involved in these paths should be part of your scope.
Don’t forget the shared responsibility model. Make sure your control mapping clearly distinguishes between what your cloud provider manages and what you, as the customer, are responsible for. Key areas to include in your HITRUST control mapping are identity platforms (like SSO and MFA), logging and SIEM services, vulnerability management tools, backup systems, and any third-party vendors or business associates that handle PHI.
Once your scope is defined, the next step is to close the gaps between your current controls and HITRUST’s requirements.
Preparation Activities for HITRUST Readiness
After locking down your scope, the next phase is a readiness or gap assessment. This step compares your existing cloud controls against HITRUST’s requirement statements. For HITRUST r2 certifications, expect to address more than 400 requirement statements, depending on your specific scope. Keep in mind that documentation maturity is just as important as technical controls - your controls might exist, but if they’re not formally documented, measured, or consistently applied, they won’t meet HITRUST standards.
To make progress, prioritize remediation based on risk and complexity. Start by tackling high-risk gaps like missing MFA, weak encryption, or insufficient logging. At the same time, focus on updating policies and centralizing documentation to achieve some quick wins. Remember, HITRUST requires a 90-day period after implementation before you can move into validation testing, so plan accordingly.
Begin collecting evidence early - things like screenshots, configuration exports, and logs - and assign clear responsibility for each control using a RACI matrix. Tools like Censinet RiskOps™ can help streamline third-party risk assessments and organize evidence collection in one place.
Many organizations now choose to partner with assessors for readiness assessments instead of relying solely on internal reviews. This approach can improve remediation efforts and minimize surprises during validation. If you’re working in a multi-cloud environment, standardize your baseline configurations using frameworks like CIS benchmarks, established encryption standards, and consistent logging practices. This not only simplifies evidence collection but also ensures your controls are applied uniformly across all platforms.
The HITRUST Certification Audit Process
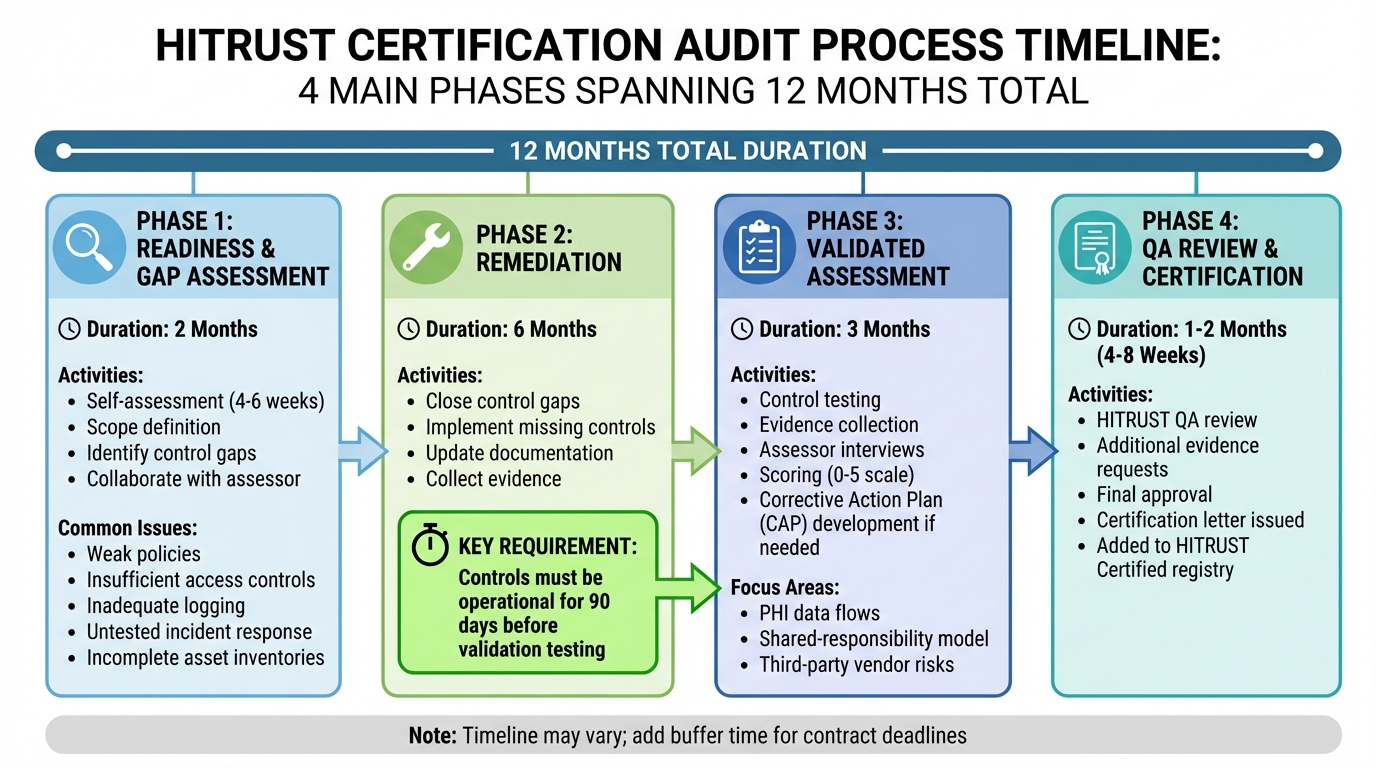
HITRUST Certification Timeline: 12-Month Process from Readiness to Certification
Readiness and Gap Assessment Phase
Although optional, skipping the readiness phase is generally not recommended. This phase is your chance to evaluate your current cloud controls against HITRUST's requirements and identify areas needing improvement. Typically, the self-assessment process takes about 4–6 weeks [1].
During this stage, collaborating with a HITRUST Authorized External Assessor experienced in cloud-based healthcare systems is invaluable. They can help define your scope, pinpoint control gaps, and outline a remediation plan. Common issues often include weak security and privacy policies, insufficient access controls (like missing role-based access for PHI), inadequate logging and monitoring of cloud resources, untested incident response plans, and incomplete asset inventories - especially in multi-cloud environments, where tracking PHI flows can be particularly challenging [1].
To stay on track, work backward from your target certification date. A typical HITRUST certification journey spans up to 12 months: around 2 months for readiness, 6 months for remediation, 3 months for the validated assessment, and 1–2 months for HITRUST's QA review [3]. It's also essential to note that HITRUST requires controls to be fully operational for at least 90 days before validation testing begins [4]. This readiness phase sets the foundation for the validated assessment, where your controls will undergo rigorous testing.
Validated Assessment and Control Testing
Once your remediation efforts are complete and your controls have been in place for the required 90 days, the validated assessment begins. During this phase, your assessor will test each control in scope and gather evidence - such as documentation, configuration files, screenshots, and logs - to confirm that your controls are functioning as intended. This phase typically takes about 3 months [3].
Assessors also conduct interviews with your teams, including security, IT, compliance, and operations, to review how controls are implemented and managed. For cloud-based healthcare systems, special attention is given to PHI data flows, the shared-responsibility model with cloud providers, and risks associated with third-party vendors [1].
Using a centralized evidence repository, like Censinet RiskOps™, can simplify the process of responding to assessor requests, especially in multi-cloud setups. Controls are evaluated across maturity levels - policy, procedure, implementation, measurement, and management - using a scoring scale of 0 to 5 for each requirement [1].
Scoring, Corrective Actions, and Certification Submission
After gathering evidence, your assessor will score each control and compile their findings. If any controls fall short of HITRUST standards, you'll need to develop a Corrective Action Plan (CAP) that outlines the steps and timelines for addressing these deficiencies. Once the CAP is approved, the assessor submits the full assessment report to HITRUST for QA review.
The QA review process typically lasts 4 to 8 weeks [3]. HITRUST reviewers will examine the assessment for consistency, completeness, and alignment with their methodology. They may request additional evidence or clarifications, so staying responsive during this time is crucial. Once the review is completed and approved, HITRUST will issue your certification letter and add your organization to the HITRUST Certified registry.
The entire process - from readiness to certification - requires detailed planning and realistic timelines. If you're working toward a specific contract deadline or board commitment, make sure to include extra buffer time for the remediation and QA review phases. With careful preparation and strong evidence management, you can navigate the audit process more efficiently and avoid unexpected delays.
sbb-itb-535baee
Maintaining HITRUST Certification in the Cloud
Achieving HITRUST certification is a significant milestone, but the real challenge lies in maintaining it. This requires constant monitoring and a proactive approach to governance to meet ongoing compliance needs.
Automating Evidence Collection and Compliance Monitoring
Getting HITRUST certified is just the first step. Keeping that certification active over its two-year cycle demands continuous monitoring and automated evidence collection. Relying on manual processes to track compliance across platforms like AWS, Azure, and Google Cloud can quickly overwhelm teams. Instead, cloud security tools - such as identity and access management (IAM), logging, vulnerability scanning, and encryption key management - can be directly aligned with HITRUST controls to simplify evidence collection tasks[6][2].
Using a centralized GRC platform tailored for healthcare, such as Censinet RiskOps™, can make this process even smoother. These platforms automate control mappings, allow for the reuse of evidence, and generate HITRUST-aligned reports. For instance, Terry Grogan, CISO at Tower Health, shared that adopting Censinet RiskOps™ enabled their team to reallocate three full-time employees to other tasks while still increasing the number of risk assessments conducted, with only two employees dedicated to the process[5]. Automation like this reduces the burden of manual log collection, allowing teams to focus more on proactive risk management.
To stay audit-ready, schedule evidence collection at regular intervals. For example:
- Conduct quarterly internal control reviews.
- Perform semiannual cloud configuration audits.
- Maintain continuous logging.
Store reports such as IAM user listings, encryption statuses, vulnerability scans, and backup logs in an organized repository[6][2]. This shift from point-in-time compliance to continuous monitoring aligns with modern HITRUST expectations and strengthens overall compliance efforts.
By automating these processes, organizations lay the groundwork for effective governance and ongoing risk management in the cloud.
Governance and Risk Management Best Practices
Once evidence collection is automated, the focus shifts to building strong governance practices. Embed HITRUST requirements into daily cloud operations by establishing a formal governance framework. Form a HITRUST governance committee that includes representatives from Security, Compliance, IT/Cloud Operations, Privacy, Clinical or Business Operations, and Vendor Management. This committee should oversee updates to the risk register, monitor Corrective Action Plan (CAP) deadlines, and ensure cloud configuration changes don’t compromise control effectiveness.
To manage third-party risk effectively, centralize the tracking of vendor SLAs, security incidents, and HITRUST certifications. A centralized platform simplifies vendor risk management while cutting down on manual effort. Additionally, document the shared responsibility model with each cloud provider. This involves linking specific HITRUST requirements to either customer- or provider-owned controls. Use infrastructure-as-code and configuration baselines to enforce compliant setups for critical areas like network segmentation, logging, encryption, and backups.
Preparing for Interim and Recertification Audits
Maintaining certification also means preparing for interim and recertification audits. HITRUST requires an interim review halfway through the two-year cycle, with recertification needed before the cycle concludes. In the 6–9 months leading up to these audits, ensure any major system implementations or migrations to new cloud services have been operational for at least 90 days. This "bake-in" period is crucial to demonstrating that controls are functioning as intended[4].
Re-train staff on HITRUST requirements, evidence standards, and updated policies - especially if processes have changed. In dynamic cloud environments, closely monitor configuration drift and new deployments to avoid any gaps in compliance. Benchmarking against industry standards can help secure the necessary resources for these efforts. By maintaining a HITRUST operating calendar and leveraging continuous monitoring tools, organizations can confidently approach interim and recertification audits without the stress of last-minute preparations.
Conclusion
The HITRUST certification audit process for cloud-based healthcare systems revolves around three key elements: precise scoping, cross-functional teamwork, and ongoing compliance. Many organizations underestimate the sheer effort involved - not because HITRUST is overly complex, but due to the scale of the assessment itself[1]. To simplify the process, start by clearly defining your in-scope cloud services, PHI data flows, and shared-responsibility boundaries. This upfront clarity can make the audit more manageable[1].
Building a lean, cross-functional team is equally important. Such a team ensures uniform control implementation and smooth evidence collection. As Matt Christensen, Sr. Director GRC at Intermountain Health, aptly said:
"Healthcare is the most complex industry... You can't just take a tool and apply it to healthcare if it wasn't built specifically for healthcare."[5]
Platforms like Censinet RiskOps™ are designed with healthcare's unique challenges in mind. They centralize third-party and enterprise risk assessments, automate control mappings, and facilitate collaborative risk management across the healthcare ecosystem.
Automation also plays a critical role in maintaining compliance. By automating control and evidence management, organizations can shift from treating HITRUST as a one-time checklist to embracing continuous monitoring. For example, automation allows teams to reallocate resources, improving efficiency in risk assessments while reducing the burden of manual tasks like log collection and spreadsheet management.
To begin, identify your in-scope cloud systems and PHI data flows, choose the appropriate HITRUST assessment type (e1, i1, or r2), and engage an authorized external assessor early. Assemble a cross-functional team and use healthcare-specific GRC platforms to centralize evidence collection and streamline risk management[1]. Starting with a readiness assessment can help establish your current posture and outline the remediation steps needed before undergoing a validated assessment[1]. For organizations managing extensive third-party ecosystems, tools like Censinet RiskOps™ can simplify these tasks and reduce manual workload.
HITRUST certification goes beyond just passing an audit. It’s about earning patient trust, improving vendor partnerships, and setting your organization up for growth in the U.S. healthcare market. By embedding HITRUST requirements into everyday operations and maintaining an operating calendar, your organization can confidently tackle interim and recertification audits while ensuring continuous compliance.
FAQs
What are the main differences between HITRUST e1, i1, and r2 assessments?
HITRUST provides three distinct assessments - e1, i1, and r2 - designed to meet varying organizational security and compliance needs.
- e1: Geared toward organizations at the beginning of their compliance journey, this assessment emphasizes foundational security controls, offering a straightforward starting point.
- i1: Built for organizations requiring a stronger level of assurance, the intermediate-level assessment includes more detailed security requirements and validations.
- r2: Aimed at mature organizations with complex systems, this advanced, risk-based assessment involves thorough validation and a broader scope to address stringent compliance demands.
These assessments are tailored to help organizations manage different levels of risk and compliance challenges effectively.
What is the shared responsibility model, and how does it affect HITRUST certification in cloud environments?
The shared responsibility model outlines how security duties are split between a cloud service provider and a healthcare organization utilizing the cloud. When it comes to HITRUST certification, this means clearly identifying which security and compliance elements are handled by the cloud provider and which fall under the healthcare organization's scope.
Healthcare organizations are responsible for safeguarding patient data, such as protected health information (PHI), and ensuring their internal processes align with HITRUST standards. Meanwhile, cloud providers typically handle the security of the underlying infrastructure. Accurately defining and addressing these responsibilities is essential for navigating audits and achieving certification successfully.
What are the best practices for staying compliant with HITRUST certification during its two-year cycle?
To maintain HITRUST certification throughout its two-year cycle, staying on top of routine maintenance and ongoing updates is essential. This includes regularly evaluating risks, revising policies and controls when necessary, and keeping a close eye on your systems for potential weaknesses.
Ensure you're ready for annual or interim audits by keeping all documentation current and making sure your team understands the compliance requirements. Tools like Censinet RiskOps™ can make this process easier by simplifying risk management, tracking compliance efforts, and aiding in continuous monitoring.
Related Blog Posts
Key Points:
What is the HITRUST certification audit process?
- Definition: The HITRUST certification audit process evaluates an organization’s security controls to ensure compliance with the HITRUST CSF framework. It includes readiness assessments, validated assessments, and ongoing compliance activities.
- Purpose: It ensures organizations meet rigorous security and privacy standards, particularly for managing PHI in healthcare environments.
What are the key steps in the HITRUST certification process?
- Scoping: Define the systems, processes, and data flows that handle PHI or sensitive information.
- Readiness Assessment: Identify gaps in controls and remediate issues before the validated assessment.
- Validated Assessment: Conducted by an external assessor to evaluate control implementation and maturity.
- Corrective Action Plans (CAPs): Address deficiencies identified during the validated assessment.
- Quality Assurance (QA): HITRUST reviews the assessment for consistency and completeness before issuing certification.
What is the difference between readiness and validated assessments?
- Readiness Assessment:
- Conducted internally or with an external assessor.
- Identifies gaps and prepares the organization for certification.
- Validated Assessment:
- A formal evaluation by a certified external assessor.
- Includes evidence collection, control testing, and scoring.
How long does the HITRUST certification process take?
- Timeline: The process typically spans 9–12 months:
- 2 months for readiness assessment.
- 6 months for remediation.
- 3 months for validated assessment and QA review.
- Ongoing Maintenance: Certification requires interim assessments and continuous monitoring.
Why is HITRUST certification important for healthcare organizations?
- Regulatory Compliance: Demonstrates adherence to multiple standards, including HIPAA, NIST, and GDPR.
- PHI Protection: Strengthens security controls to safeguard sensitive patient data.
- Trust and Credibility: Builds trust with partners, customers, and regulators.
What tools can streamline the HITRUST certification process?
- Censinet RiskOps™: Automates evidence collection, tracks compliance progress, and simplifies third-party risk management.
- Cloud Security Tools: Align controls with HITRUST requirements, such as IAM, logging, and encryption.
- Centralized GRC Platforms: Organize documentation and generate HITRUST-aligned reports.


