HITRUST CSF vs. Other Cybersecurity Frameworks
Post Summary
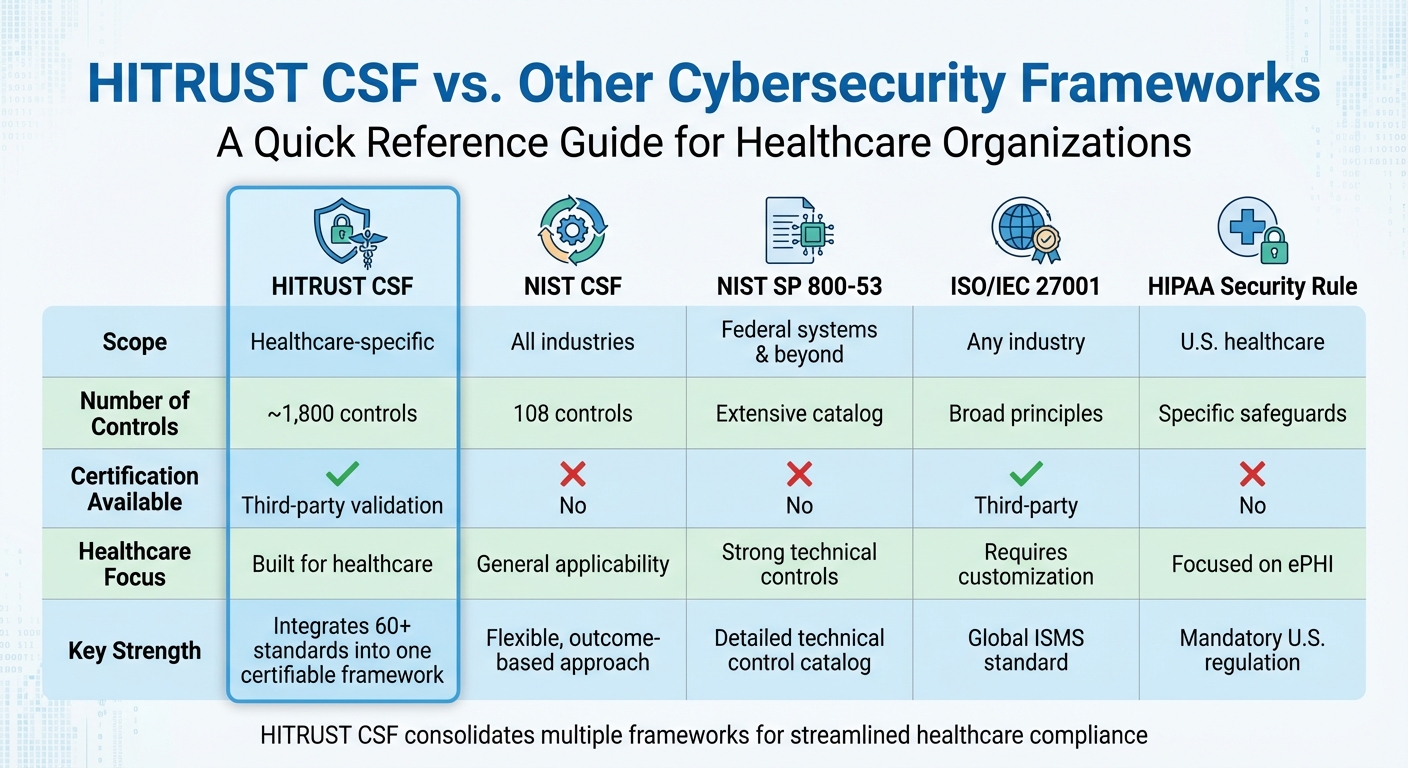
HITRUST CSF integrates 60+ standards into one healthcare‑specific, certifiable framework with ~1,800 controls.
NIST provides flexible, outcome‑based guidance, while HITRUST offers prescriptive controls, maturity scoring, and certification tailored for healthcare.
HITRUST builds on ISO governance principles and HIPAA safeguards, creating a unified framework that simplifies compliance across both.
Certification reduces redundant audits, streamlines contracting, and provides validated assurance of strong security controls.
Scope, maturity level, resources, regulatory needs, system complexity, and alignment with existing frameworks like NIST or ISO.
Censinet centralizes assessments, maps controls, automates evidence tracking, highlights vendor risks, and accelerates HITRUST readiness.
HITRUST CSF is a cybersecurity framework specifically designed for the healthcare industry to address its complex regulatory and privacy requirements. It consolidates over 60 standards, including HIPAA, NIST, and ISO/IEC 27001, into one certifiable framework. With around 1,800 controls tailored for healthcare, HITRUST simplifies compliance, protects sensitive patient data, and ensures security for clinical workflows and medical devices.
Here’s how HITRUST CSF compares to other frameworks:
Quick Comparison
Healthcare-specific
All industries
Federal systems & beyond
Any industry
U.S. healthcare
~1,800
108
Extensive catalog
Broad principles
Specific safeguards
Third-party validation
No
No
Third-party
No
Built for healthcare
General applicability
Strong technical controls
Requires customization
Focused on ePHI
HITRUST CSF is often used alongside other frameworks, combining NIST’s flexibility, ISO’s governance, and HIPAA’s safeguards with HITRUST’s detailed, certifiable approach. For healthcare organizations, HITRUST certification can streamline compliance, reduce audit fatigue, and demonstrate strong security practices to partners and regulators.
HITRUST CSF vs NIST CSF vs ISO 27001 vs HIPAA Security Rule Comparison Chart
What is HITRUST CSF for Healthcare Organizations

The HITRUST Common Security Framework (CSF) is a certifiable, risk-based framework designed to help healthcare organizations tackle security, privacy, and regulatory challenges [3]. It has become a go-to standard in the healthcare sector because it specifically addresses the industry's unique requirements.
HITRUST CSF stands out by consolidating over 60 authoritative sources - like HIPAA, NIST, ISO/IEC 27001, and PCI DSS - into one unified control set. This approach allows healthcare organizations to handle multiple compliance needs with a single framework. By doing so, it helps minimize redundancy, simplifies evidence collection, and creates a shared language for discussing risk among health systems, vendors, and regulators. Its focus on healthcare-specific needs makes it particularly valuable for organizations in this field.
Key Features of HITRUST CSF
HITRUST CSF goes beyond general security frameworks by offering detailed, flexible controls tailored for healthcare. It includes around 1,800 controls, organized into 14 categories, 75 objectives, and 19 domains. This comprehensive structure addresses the complexities of protecting patient data, clinical workflows, and medical devices.
The framework adjusts its controls based on factors like organizational size, data sensitivity (e.g., PHI), system complexity, and regulatory requirements [3]. This flexibility ensures that each organization can implement controls suited to its specific risks, rather than following a one-size-fits-all approach.
HITRUST also evaluates controls through a five-level maturity model, ranging from basic policy creation to fully managed processes [3]. This model not only ensures that controls are in place but also evaluates their consistent application, monitoring, and ongoing improvement.
HITRUST Certification and Assurance Programs
Unlike frameworks that only provide guidance, HITRUST offers certifiable assessments with third-party validation. Its tiered assessment model - e1, i1, and r2 - aligns the level of assurance with the organization's business and clinical risks. For instance, a cloud-based EHR vendor with HITRUST r2 certification can use a single assessment report to meet the requirements of multiple hospital clients. This reduces the need for repetitive questionnaires, on-site audits, and streamlines contract negotiations, making risk management more efficient.
These certifiable assessments are a cornerstone of HITRUST’s ability to meet the complex security demands of healthcare organizations.
Healthcare-Specific Security and Compliance Requirements
HITRUST CSF includes controls specifically designed to protect PHI and ePHI, addressing critical areas like access control, encryption, audit logging, breach detection, and incident response, all aligned with HIPAA requirements [3]. But it doesn’t stop at generic security measures. The framework also tackles the operational challenges unique to healthcare, such as securing clinical applications, EHRs, networked medical devices, and IoT systems in clinical environments.
Key areas covered include secure configurations, robust identity and access management, continuity planning, asset tracking, network segmentation, patch management, vulnerability assessments, and vendor oversight.
Additionally, HITRUST emphasizes business continuity, disaster recovery, change management, and third-party risk controls - essential for ensuring patient safety in the event of downtime or data loss. By regularly updating its controls to align with evolving standards from sources like NIST, ISO, and HIPAA, HITRUST CSF helps healthcare organizations stay ahead of regulatory changes while maintaining strong security practices.
HITRUST CSF vs. NIST Frameworks
NIST Frameworks Overview
Healthcare's cybersecurity challenges require more than just generic solutions, and this is where HITRUST CSF sets itself apart from NIST frameworks.
The NIST Cybersecurity Framework (NIST CSF), originally designed for U.S. critical infrastructure, has become a widely used standard across industries [3]. It breaks cybersecurity into five core Functions: Identify, Protect, Detect, Respond, and Recover. Each Function is further divided into Categories (like asset management or access control) and Subcategories that define specific outcomes, such as maintaining an asset inventory or logging security events.
To complement the CSF, NIST SP 800-53 provides a detailed catalog of security and privacy controls grouped into families like Access Control, Incident Response, and System and Communications Protection. In healthcare, organizations often use the NIST CSF to guide their overall risk strategies while turning to SP 800-53 for technical details to safeguard PHI and clinical systems. Together, these frameworks provide a foundation for comparing how HITRUST CSF and NIST frameworks address the unique needs of healthcare.
Key Differences Between HITRUST CSF and NIST Frameworks
NIST frameworks are flexible and outcome-focused, allowing organizations to tailor their approach. In contrast, HITRUST CSF takes a more structured, implementation-based approach tailored specifically for healthcare [3]. NIST CSF outlines what outcomes to aim for but doesn’t dictate how to achieve them. HITRUST, on the other hand, provides detailed requirements, scoping factors (based on organizational size and data sensitivity), and a maturity scoring system - Policy, Process, Implemented, Measured, Managed - adapted from NIST's PRISMA model [3].
This difference is particularly important for healthcare organizations managing PHI, clinical systems, and medical devices. While NIST frameworks offer a versatile foundation for risk management across industries, HITRUST CSF integrates healthcare-specific requirements from regulations like HIPAA, PCI DSS, and ISO/IEC 27001 into a comprehensive framework of about 1,800 controls across 19 domains [2][3]. HITRUST also stands out by offering third-party certification, providing a standardized way for healthcare vendors and systems to demonstrate compliance.
Voluntary, risk-based framework for any industry
Detailed control catalog for federal systems and beyond
Healthcare-specific framework integrating multiple standards
5 Functions, Categories, Subcategories, Implementation Tiers (1–4)
Control families with baselines (Low, Moderate, High)
~1,800 controls; 19 domains; 14 categories; 75 objectives; maturity scoring
Flexible guidance - defines outcomes, not implementation
Specific controls with tailoring options
Detailed requirements with scoping and maturity scoring system
No formal certification
No formal certification
Third-party certification
General applicability; requires customization for PHI/HIPAA
Strong technical controls; requires mapping to HIPAA
Built for healthcare; integrates HIPAA, PCI, ISO, and more
Given these distinctions, many healthcare organizations choose to leverage both frameworks for a well-rounded approach to risk management.
Using HITRUST CSF and NIST Frameworks Together in Healthcare
Many U.S. health systems begin their cybersecurity strategies with the NIST CSF's five Functions to organize risks across clinical, business, and research environments [3]. As third-party risks grow with cloud-hosted EHR extensions, telehealth platforms, and medical device vendors, these organizations often adopt HITRUST CSF as their standard for vendor assessments and compliance validation. This dual approach allows organizations to use NIST Tiers to communicate cybersecurity maturity to boards while leveraging HITRUST certification to meet healthcare-specific regulatory demands.
Platforms like Censinet RiskOps™ make it easier to integrate HITRUST CSF and NIST frameworks into both enterprise and third-party risk assessments. By mapping NIST CSF profiles to HITRUST domains and requirements, organizations can ensure that all desired outcomes are backed by measurable, auditable controls. This approach simplifies evidence collection, reduces redundant assessments, and creates a common language for discussing risk with vendors, regulators, and business partners.
HITRUST CSF vs. ISO/IEC 27001 and HIPAA Security Rule
ISO/IEC 27001 and HIPAA Security Rule Overview
ISO/IEC 27001 is a globally acknowledged standard for setting up, implementing, and maintaining an Information Security Management System (ISMS). It’s often used to showcase systematic risk management through regular risk assessments. Certification under this standard is voluntary and conducted by accredited third-party auditors.
On the other hand, the HIPAA Security Rule is a U.S. federal regulation designed to enforce specific administrative, physical, and technical safeguards for protecting electronic protected health information (ePHI). It applies to covered entities like healthcare providers, health plans, and clearinghouses, as well as their business associates. The rule outlines mandatory and optional specifications, giving organizations some flexibility in meeting these requirements. However, enforcement by the U.S. Department of Health and Human Services Office for Civil Rights (HHS/OCR) is strict, with penalties reaching millions of dollars for issues like insufficient risk analysis, lack of encryption, or poor access controls. Compliance is evaluated based on documented, risk-based practices. [3][5]
Next, let’s explore how HITRUST CSF connects with these frameworks.
Comparing HITRUST CSF, ISO/IEC 27001, and HIPAA Security Rule
Now that we’ve defined these frameworks, let’s examine how they compare. HITRUST CSF combines elements of ISO/IEC 27001 and HIPAA to address healthcare-specific needs. While ISO/IEC 27001 provides a solid ISMS foundation, it often requires additional customization to address healthcare risks. Meanwhile, the HIPAA Security Rule, though focused on healthcare, allows organizations flexibility in implementation, which can lead to inconsistent interpretations.
HITRUST CSF bridges these gaps by offering detailed, prescriptive controls - around 1,800 requirements across 19 domains - that align directly with HIPAA safeguards while incorporating ISO/IEC 27001’s governance principles. Organizations achieving HITRUST certification can use their assessment reports to demonstrate compliance with HIPAA. As a result, many major U.S. health systems and insurers now prefer or require HITRUST certification from vendors to ensure strong security practices. [3][5]
Global ISMS standard for any industry
U.S. regulation focused on ePHI in healthcare
Framework tailored for healthcare, integrating multiple standards
Voluntary international standard
Mandatory U.S. federal regulation
Voluntary framework aiding regulatory compliance
Broad principles needing customization
Required and optional safeguards with flexibility
About 1,800 prescriptive controls with maturity levels
Third-party certification by auditors
No formal certification; compliance via documentation
Third-party HITRUST certification with validated assessments
General standards requiring mapping to healthcare risks
Healthcare-specific but open to interpretation
Designed for healthcare, directly aligned with HIPAA requirements
This table highlights how HITRUST CSF integrates aspects of both ISO/IEC 27001 and the HIPAA Security Rule, offering a more unified approach.
Combining HITRUST CSF with ISO/IEC 27001 and HIPAA Programs
Healthcare organizations can streamline their efforts and reduce audit fatigue by aligning ISO/IEC 27001’s ISMS governance practices with HITRUST CSF’s detailed controls. ISO/IEC 27001 focuses on governance through risk assessments, management reviews, and continuous improvement, while HITRUST CSF provides the specific controls needed for healthcare environments. This combination ensures robust protection for PHI, secure clinical applications, and better management of risks associated with medical devices. By integrating these frameworks, organizations can maintain a single set of policies and procedures that meet the requirements of both.
For HIPAA compliance, incorporating activities into a HITRUST CSF program simplifies redundant assessments. Since HITRUST is designed to demonstrate adherence to the HIPAA Security Rule (and related HITECH requirements), organizations can use HITRUST assessment reports to show regulators their commitment to mandated safeguards. This approach is particularly advantageous for healthcare vendors and business associates, as HITRUST certification is often a key differentiator in RFPs with major health systems and insurers. [3][5]
Censinet RiskOps™ further supports this alignment by centralizing third-party and enterprise risk assessments. It manages HITRUST-mapped questionnaires and benchmarks cybersecurity readiness across vendors handling PHI and clinical applications. By creating a shared evidence repository, the platform helps organizations streamline ISO/IEC 27001 audits, HITRUST assessments, and HIPAA compliance documentation simultaneously.
sbb-itb-535baee
How to Implement HITRUST CSF in Healthcare Organizations
Factors to Consider When Choosing HITRUST CSF
Before diving into HITRUST CSF, healthcare organizations need to weigh a few important considerations. Start by aligning the decision with your organization's goals and appetite for risk. For instance, if you're expanding into new payer networks, launching telehealth services, or navigating mergers and acquisitions, HITRUST certification can support growth while signaling that your cybersecurity and compliance risks are under control. This is particularly crucial when considering the high costs of potential PHI breaches and OCR fines [3][6].
Next, take a close look at your current security and compliance maturity. Compare your existing policies and controls to HITRUST's baseline requirements and maturity levels, which include stages like policy, procedure, implementation, measurement, and management. If you're relying solely on basic HIPAA checklists, the road to HITRUST certification may be longer. However, organizations already using frameworks like NIST CSF or ISO/IEC 27001 will likely find the transition smoother [3].
Budget and resource capacity are also key factors. HITRUST certification requires a significant investment, including licensing fees, external assessments, and remediation efforts. That said, this upfront investment can help streamline overlapping compliance activities and reduce the fatigue of repeated audits over time [2][3][6].
HITRUST's tailored approach to healthcare, incorporating HIPAA and industry-specific controls, directly addresses the unique challenges of protecting PHI and ensuring uninterrupted clinical operations [3][6][4].
Steps to Implement HITRUST CSF
To get started, define your business drivers and narrow the scope of implementation. Pinpoint the systems, data types (like PHI and PII), and business units that will be involved. Many organizations begin with high-risk areas such as EHR systems, patient portals, or critical clinical applications [3][6].
If you're already using frameworks like NIST CSF, leverage existing resources such as risk assessments, asset inventories, incident response plans, and governance structures. Align these with HITRUST's five maturity levels to save time and effort [2][3].
Break down the process into manageable phases to tackle the complexity. During the remediation phase, which can take anywhere from 3 to 12 months or more, prioritize closing gaps that pose the greatest risk to PHI and patient safety. Focus on critical systems where a breach would have significant clinical or regulatory consequences. Strengthen technical controls like identity and access management, network segmentation, and logging, while formalizing policies and procedures to meet HITRUST's maturity standards [3][4].
Establish a cross-functional governance structure by forming a HITRUST steering committee. This group should include representatives from IT, security, privacy, compliance, clinical operations, supply chain, and legal teams. Secure buy-in from a senior executive, such as the CIO, CISO, or Chief Compliance Officer, to ensure the necessary resources and alignment with broader risk management goals [3][6].
When you reach the evidence collection and validation phase, centralize documentation like policies, logs, reports, and screenshots to meet HITRUST's requirements. By integrating this into your existing risk management workflows, you can make HITRUST compliance part of your organization's routine operations rather than a one-time project [3][6].
A centralized platform can help simplify and sustain ongoing HITRUST compliance efforts.
How Censinet Supports HITRUST CSF Adoption
Censinet RiskOps™ serves as a powerful tool for healthcare organizations looking to streamline HITRUST compliance. This platform acts as a centralized hub for managing HITRUST-aligned risk assessments across vendors, clinical applications, medical devices, and the supply chain. It helps map controls, track remediation progress, and store evidence to meet HITRUST requirements [Censinet site].
Censinet's collaborative risk network connects healthcare organizations with over 50,000 vendors and products, cutting down on redundant questionnaires and speeding up the risk assessment process. Terry Grogan, CISO of Tower Health, shared the impact:
"Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."
– Terry Grogan, CISO, Tower Health
The platform also offers cybersecurity benchmarking, enabling organizations to measure their security posture against industry standards. This helps advocate for the resources needed to address gaps effectively. Brian Sterud, CIO at Faith Regional Health, explained:
"Benchmarking against industry standards helps us advocate for the right resources and ensures we are leading where it matters."
– Brian Sterud, CIO, Faith Regional Health
By moving away from manual, spreadsheet-based processes to continuous risk management, Censinet RiskOps™ supports the evidence collection and monitoring required for HITRUST's higher maturity levels. James Case, VP & CISO at Baptist Health, highlighted the benefits:
"Not only did we get rid of spreadsheets, but we have that larger community [of hospitals] to partner and work with."
– James Case, VP & CISO, Baptist Health
Censinet AI™ further enhances the process by automating third-party risk assessments. Vendors can complete security questionnaires quickly, while the platform generates detailed risk summary reports. This automation scales risk management operations while maintaining the oversight needed to meet HITRUST's stringent control requirements [Censinet site].
Conclusion
Selecting the right cybersecurity framework isn’t about finding a "one-size-fits-all" solution - it’s about aligning the framework’s strengths with your organization’s specific needs. For healthcare organizations, HITRUST CSF stands out as it was purpose-built for the industry. By integrating approximately 1,800 controls from standards like HIPAA, NIST, and ISO/IEC 27001 into one certifiable framework, it offers a streamlined, risk-based approach that evolves with the ever-changing demands of healthcare compliance[2].
Each framework has its own strengths. NIST CSF provides adaptable guidance with 108 controls, while ISO/IEC 27001 delivers a globally recognized standard for information security management systems (ISMS). What makes HITRUST particularly appealing to healthcare organizations is its ability to unify these compliance needs into a single, certifiable strategy. Instead of juggling multiple audits for HIPAA, NIST, and ISO, HITRUST simplifies the process, creating a more cohesive compliance pathway. Importantly, adopting HITRUST doesn’t mean abandoning other frameworks - it can complement NIST and ISO/IEC 27001 to enhance overall compliance efficiency.
For healthcare CISOs and compliance leaders, the benefits of HITRUST certification go beyond meeting regulatory requirements. It demonstrates to patients, partners, and regulators that protecting PHI is a top priority. Certification can also ease vendor relationships, support business expansion, and reduce the strain of repeated audits across various standards.
That said, implementing HITRUST CSF isn’t without its challenges. Success requires a strong infrastructure tailored to the unique demands of healthcare. This is where tools like Censinet RiskOps™ come into play. By offering a centralized platform for managing HITRUST-aligned assessments, tracking remediation efforts, and maintaining the evidence needed for certification, Censinet streamlines the process. Its collaborative risk network and AI-driven automation help healthcare organizations efficiently scale their compliance efforts while maintaining the oversight critical for patient safety. These elements together provide a practical path forward for organizations aiming to strengthen their cybersecurity posture.
FAQs
Why is HITRUST CSF a good fit for healthcare organizations?
HITRUST CSF is tailored for healthcare organizations, addressing the distinct challenges they face. This framework brings together regulatory compliance, risk management, and security practices into one cohesive system.
Designed with healthcare in mind, HITRUST CSF helps safeguard sensitive patient information, such as Protected Health Information (PHI), while ensuring adherence to regulations like HIPAA. It’s especially useful for managing risks tied to clinical applications, medical devices, and other essential healthcare systems. This makes it a valuable resource for navigating the intricate and highly regulated world of healthcare.
How does the HITRUST CSF work alongside frameworks like NIST and ISO/IEC 27001?
The HITRUST CSF works by aligning its controls with established frameworks like NIST and ISO/IEC 27001. By mapping to these standards, it enables organizations to tackle multiple compliance requirements using one unified system.
For healthcare organizations, this alignment streamlines the process of meeting diverse regulatory and security standards. It minimizes redundant efforts and enhances both risk management and compliance efficiency.
What are the main advantages of HITRUST certification for healthcare providers?
HITRUST certification brings a range of advantages for healthcare providers. First, it proves that an organization complies with rigorous industry standards, making it easier to meet regulatory requirements. This can streamline the process of audits and assessments, saving both time and resources.
On top of that, it strengthens cybersecurity by identifying potential risks and addressing them proactively. This helps protect sensitive patient information, such as PHI, and ensures the security of essential systems. By achieving HITRUST certification, organizations also demonstrate their dedication to upholding top-tier security and privacy standards, fostering trust among patients, partners, and stakeholders.
Related Blog Posts
- “Risk Management Under HIPAA: Why Framework Alignment Beats Compliance Alone”
- HITRUST vs. NIST: Cloud Security Frameworks Compared
- How HITRUST Certification Reduces Cloud Vendor Risks
- HITRUST Certification: Third-Party Risk Assessment Role
{"@context":"https://schema.org","@type":"FAQPage","mainEntity":[{"@type":"Question","name":"Why is HITRUST CSF a good fit for healthcare organizations?","acceptedAnswer":{"@type":"Answer","text":"<p>HITRUST CSF is tailored for healthcare organizations, addressing the distinct challenges they face. This framework brings together regulatory compliance, risk management, and security practices into one cohesive system.</p> <p>Designed with healthcare in mind, HITRUST CSF helps safeguard sensitive patient information, such as Protected Health Information (PHI), while ensuring adherence to regulations like HIPAA. It’s especially useful for managing risks tied to clinical applications, medical devices, and other essential healthcare systems. This makes it a valuable resource for navigating the intricate and highly regulated world of healthcare.</p>"}},{"@type":"Question","name":"How does the HITRUST CSF work alongside frameworks like NIST and ISO/IEC 27001?","acceptedAnswer":{"@type":"Answer","text":"<p>The HITRUST CSF works by aligning its controls with established frameworks like NIST and ISO/IEC 27001. By mapping to these standards, it enables organizations to tackle multiple compliance requirements using one unified system.</p> <p>For healthcare organizations, this alignment streamlines the process of meeting diverse regulatory and security standards. It minimizes redundant efforts and enhances both risk management and compliance efficiency.</p>"}},{"@type":"Question","name":"What are the main advantages of HITRUST certification for healthcare providers?","acceptedAnswer":{"@type":"Answer","text":"<p>HITRUST certification brings a range of advantages for healthcare providers. First, it proves that an organization complies with rigorous industry standards, making it easier to meet regulatory requirements. This can streamline the process of audits and assessments, saving both time and resources.</p> <p>On top of that, it strengthens cybersecurity by identifying potential risks and addressing them proactively. This helps protect sensitive patient information, such as PHI, and ensures the security of essential systems. By achieving HITRUST certification, organizations also demonstrate their dedication to upholding top-tier security and privacy standards, fostering trust among patients, partners, and stakeholders.</p>"}}]}
Key Points:
What makes HITRUST CSF uniquely suited for healthcare organizations?
- Consolidates 60+ standards including HIPAA, NIST, ISO, PCI, and more
- Offers ~1,800 prescriptive controls, tailored specifically for healthcare environments
- Integrates privacy, security, and compliance requirements into one framework
- Includes a five‑level maturity model that evaluates policy, process, implementation, measurement, and management
- Provides third‑party validated certification, unlike most other frameworks
How does HITRUST CSF differ from NIST CSF and NIST SP 800‑53?
- NIST CSF defines outcomes, while HITRUST defines detailed, prescriptive controls
- NIST is flexible and cross‑industry, whereas HITRUST is healthcare‑specific
- HITRUST includes scoping factors (organization size, data sensitivity)
- HITRUST certification gives formal assurance, which NIST lacks
- NIST SP 800‑53 provides control catalogs, but without a certifiable maturity model
How does HITRUST CSF integrate with ISO/IEC 27001 and HIPAA Security Rule requirements?
- ISO provides governance and ISMS structure, while HITRUST adds healthcare‑specific control depth
- HIPAA defines required safeguards, and HITRUST maps directly to them
- HITRUST controls reduce ambiguity in HIPAA’s flexible implementation guidance
- HITRUST assessments act as evidence of HIPAA compliance
- Combining ISO with HITRUST reduces audit duplication across multiple regulatory regimes
What are the benefits of HITRUST certification for healthcare providers and vendors?
- Streamlines third‑party risk assessments, reducing questionnaire fatigue
- Provides a unified control set, replacing multiple overlapping audits
- Improves vendor trust and contracting speed, especially for EHR and cloud vendors
- Strengthens PHI and ePHI protection across clinical, operational, and device environments
- Demonstrates defensible compliance, useful for regulators and partners
What challenges must organizations prepare for before implementing HITRUST?
- Significant time and resource investment (assessment, remediation, validation)
- Extensive documentation requirements, far beyond HIPAA checklists
- Need for cross‑functional governance across IT, security, compliance, and clinical teams
- Potential gaps in technical controls, requiring remediation prior to certification
- Ongoing maturity requirements, not a one‑time project
How does Censinet support HITRUST CSF adoption and readiness?
- Centralizes HITRUST‑aligned assessments across applications, vendors, and devices
- Maps HITRUST controls to NIST and ISO frameworks, reducing duplicate work
- Automates evidence tracking, versioning, and documentation for audits
- Identifies vendor risk gaps, including fourth‑party exposure
- Accelerates review cycles using Censinet AI™ for summarization and analysis


