Study: Impact of Cloud Vendor Breaches on Healthcare
Post Summary
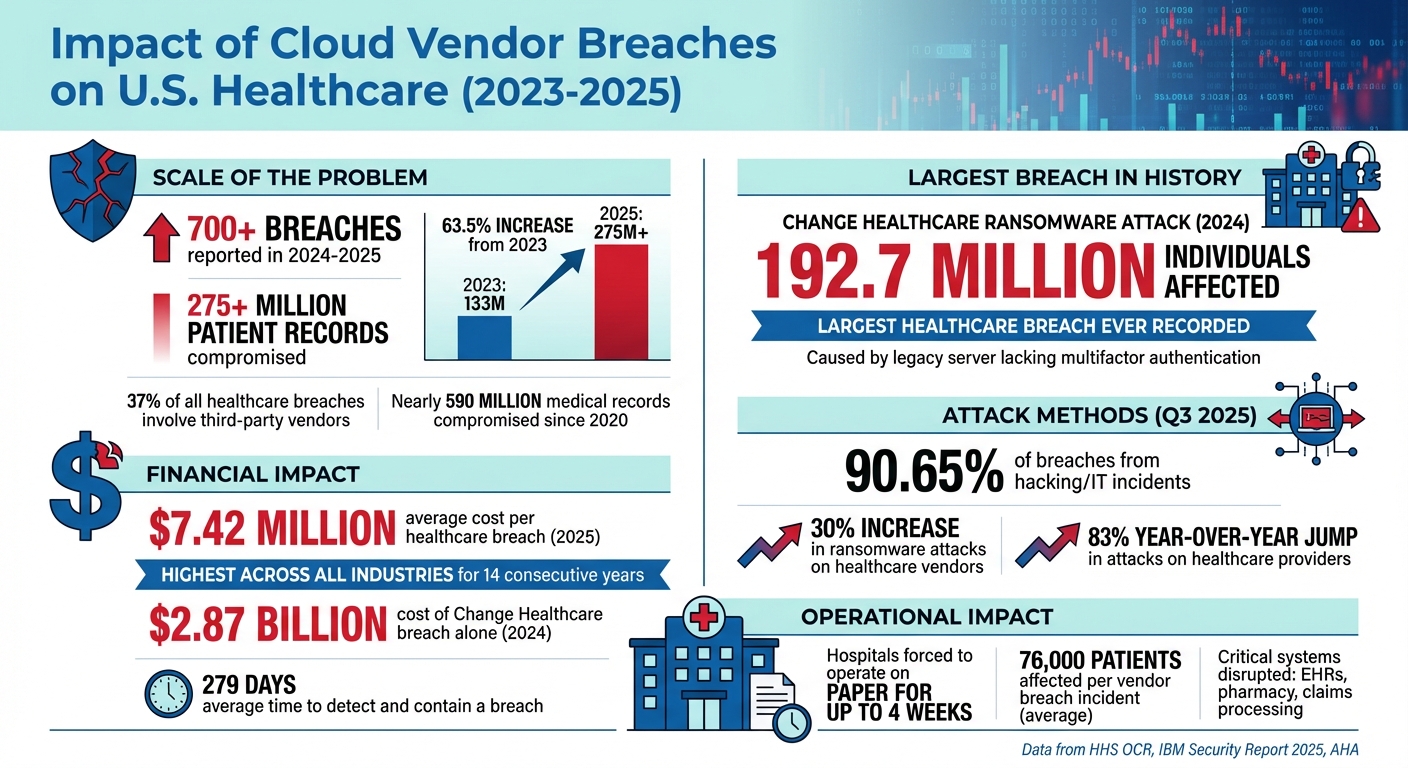
Cloud vendor breaches are shaking the U.S. healthcare system, exposing patient data, disrupting critical operations, and costing billions. Between 2024 and 2025, over 275 million patient records were compromised in more than 700 breaches - a 63.5% jump from 2023. These incidents, often involving third-party vendors, have caused service outages, delayed care, and increased risks to patient safety. The financial toll is equally alarming, with healthcare breaches averaging $7.42 million per incident in 2025, the highest across all industries for 14 consecutive years.
Key Takeaways:
- Scale of Breaches: 37% of healthcare breaches now involve third-party vendors, exposing millions of records annually.
- Operational Disruptions: Outages force hospitals to revert to manual processes, delaying treatments and increasing risks of errors.
- Financial Costs: Breaches like the 2024 Change Healthcare ransomware attack cost up to $2.87 billion.
- Root Causes: Common vulnerabilities include unpatched systems, weak access controls, and misconfigured cloud storage.
- Mitigation Strategies: Pre-contract risk assessments, continuous vendor monitoring, and tools like Censinet RiskOps™ can help reduce risks.
Cloud vendor breaches are more than data leaks - they disrupt care, compromise safety, and erode trust. Addressing these risks demands rigorous vendor oversight, robust security measures, and investment in advanced risk management tools.
Healthcare Cloud Vendor Breach Statistics 2023-2025: Impact on Patient Records and Costs
How Often Cloud Vendor Breaches Occur in Healthcare
Third-Party Vendor Breach Statistics
Healthcare organizations are increasingly vulnerable to threats from third-party vendors. In 2023, 725 data breaches were reported to the HHS Office for Civil Rights (OCR), exposing over 133 million records. By 2024-2025, this number grew to more than 700 breaches, impacting over 275 million patient records - a staggering 63.5% increase[2][6].
Business associates and cloud vendors represent a particularly concerning risk. In 2025 so far, business associates were involved in 37% of all reported breaches, despite making up only a small portion of entities handling protected health information (PHI)[4]. During the third quarter of 2025 alone, these associates were linked to 30 breaches (21.58% of incidents), affecting 796,552 patients[3]. These numbers highlight the critical vulnerabilities posed by third-party vendors in healthcare cybersecurity, showing both the frequency and the far-reaching consequences of such breaches.
Patient Records Compromised
The scale of patient data exposure through vendor breaches is overwhelming. As of 2025, nearly 500 breaches involving unsecured PHI have been reported, impacting more than 37.5 million individuals[4]. Since 2020, over 590 million medical records have been compromised in the U.S., according to the American Hospital Association. This means nearly every U.S. citizen has been affected - often multiple times[2].
One of the most devastating incidents was the ransomware attack on Change Healthcare, a UnitedHealth Group subsidiary, reported in 2024. This breach exposed the protected health information of approximately 192.7 million people, making it the largest healthcare breach in history[4]. The attackers exploited a legacy server that lacked multifactor authentication, demonstrating how a single vulnerability in a widely used vendor can ripple across the entire healthcare system. The financial toll of this breach was immense, with costs reaching $2.87 billion in 2024 and continuing to rise[4]. Events like this underscore the urgency of addressing vulnerabilities in vendor systems to safeguard patient data.
How Breaches Happen in Cloud Systems
With the sheer volume of breaches and compromised data, it’s crucial to examine how these incidents occur in cloud environments. In the third quarter of 2025, hacking and IT incidents targeting network servers and cloud-hosted resources accounted for 126 out of 139 breaches (90.65%), impacting 9,342,576 patients (98.15%)[3]. The most common attack methods include ransomware campaigns, credential theft, and exploiting unpatched vulnerabilities in external systems[3][4].
Ransomware attacks on healthcare vendors have surged dramatically, increasing by 30% in 2025, with attacks on healthcare providers specifically jumping 83% year-over-year[5]. Threat groups like Nova and BianLian have repeatedly targeted U.S. healthcare companies and their service providers, knowing that breaching a single vendor can disrupt multiple downstream organizations at once[5]. Beyond ransomware, breaches often result from misconfigured external storage systems and unauthorized tracking technologies. For example, the Kaiser Foundation Health Plan breach in 2024 exposed the data of 13.4 million individuals due to such vulnerabilities[4]. These examples highlight the need for stricter security measures to prevent similar incidents in the future.
How Cloud Vendor Breaches Affect Healthcare Operations and Patient Safety
Interruptions to Clinical Systems
When cloud vendors are breached, clinicians lose access to critical systems, often forcing hospitals to take essential tools offline for investigation due to ransomware or hacking incidents [3][4]. During these outages, healthcare providers must rely on paper charts, manual order entries, and phone calls to coordinate lab results, radiology reports, and medication orders [2].
Major health systems have reported enduring weeks of electronic health record (EHR) downtime following cyberattacks. For instance, during significant breaches in 2024 and 2025, some hospitals operated on paper for nearly four weeks. This led to ambulance diversions, postponed elective surgeries, and a reliance on manual processes that slowed every aspect of patient care [2]. These disruptions extended beyond clinical workflows, affecting scheduling, claims submission, and revenue cycle operations [3][4]. The impact on patient care, as outlined below, can be severe.
Risks to Patient Care
When systems go offline, healthcare providers are forced into manual workflows, which increase risks to patient safety. Without real-time access to patient data, clinicians must make decisions based on incomplete information [2][4]. Emergency departments and inpatient units face greater chances of duplicate tests, delays in diagnostic decisions, missed critical results, and errors when re-entering data later [2].
A stark example is the 2024 Change Healthcare ransomware breach, which compromised the protected health information of approximately 192.7 million individuals. This incident disrupted electronic claims processing, eligibility checks, and pharmacy benefit transactions nationwide [4]. Providers and pharmacies were unable to transmit electronic prescriptions or verify coverage, causing treatment delays. Some patients had to postpone care or pay out of pocket [4]. For high-risk individuals - such as those undergoing chemotherapy, complex imaging follow-ups, or staged surgical procedures - these outages delayed critical appointments and care planning, sometimes pushing follow-ups weeks or even months later [2][4].
Financial and Trust Costs
Healthcare organizations incur steep financial losses when cloud vendors are breached. According to IBM's 2025 report, the average cost of a healthcare breach in the United States reached $7.42 million per incident [4][7]. These costs include incident response, forensic investigations, system restoration, regulatory actions, legal fees, credit monitoring, and lost productivity [7].
The Change Healthcare breach alone resulted in an estimated $2.87 billion in damages during 2024, with additional costs likely from regulatory penalties and class-action lawsuits [4]. Beyond these direct expenses, providers face delayed or lost revenue when claims submission and billing systems are offline. Breaches also attract negative media attention, damaging the reputations of both the vendor and associated healthcare providers [2][3][4]. Patient surveys conducted after major incidents reveal growing concerns about the privacy of protected health information (PHI). Many patients express hesitation to share sensitive data through patient portals, mobile apps, or virtual care platforms, which can hinder the adoption of new digital health technologies [4].
Risk Factors and System Weaknesses
Problems in Healthcare Vendor Networks
Healthcare organizations in the U.S. often depend on hundreds, sometimes thousands, of third-party vendors. This reliance increases their vulnerability to cyberattacks, as it broadens the potential points of entry for bad actors [3][4]. Issues like fragmented contracting processes, inconsistent security standards, and limited visibility into downstream vendors weaken the overall security framework. In fact, business associates are linked to 37% of reported breaches [4]. Without a clear understanding of who handles protected health information (PHI) or how systems interconnect, these organizations face significant challenges in identifying and mitigating risks. These vulnerabilities directly contribute to the operational disruptions mentioned earlier.
The situation becomes even riskier with the widespread use of cloud-hosted clinical, billing, and claims systems. A single breach at a vendor supporting nationwide health IT or revenue cycle platforms can ripple across multiple hospitals and physician groups simultaneously [4]. This interconnectedness creates systemic weaknesses, amplifying the impact of breaches when they occur.
Factors That Lead to Worse Breaches
Certain factors make breaches more severe, especially when critical services are concentrated among a small number of vendors. For instance, if one cloud provider fails, it can disrupt key functions like revenue cycles, prior authorizations, e-prescribing, or eligibility checks across numerous facilities [4]. A notable example is the ransomware attack on Change Healthcare, where the absence of multifactor authentication (MFA) on a legacy server allowed attackers to exploit weak vendor security controls, significantly amplifying the damage [4].
Other high-risk scenarios involve vendors managing mission-critical clinical or financial workflows, such as claims clearinghouses, managed electronic health record (EHR) hosting, or imaging archives [2][4]. These vendors often integrate deeply with on-premise systems, and their downtime plans may not have been adequately tested. Additionally, vendors that host vast amounts of PHI across multiple clients are particularly vulnerable. A single compromise can lead to widespread service disruptions [2][4].
Hacking and IT incidents are responsible for about 90% of large healthcare breaches. Common vulnerabilities include compromised credentials, misconfigured cloud storage, exposed remote access systems, and unpatched software in vendor-facing systems [3][4]. These weaknesses not only disrupt operations but also increase the risk of regulatory scrutiny under federal mandates.
HIPAA and Regulatory Requirements
Federal regulations, particularly HIPAA and HITECH, require healthcare organizations to manage vendor risks effectively. Covered entities must establish Business Associate Agreements (BAAs) with vendors handling PHI. These agreements outline acceptable uses, security expectations, subcontractor oversight, and breach notification timelines [6][7]. When organizations fail to enforce adequate vendor oversight, the Office for Civil Rights (OCR) has imposed substantial penalties [6][7].
Major breaches often lead to federal investigations, corrective action plans, and civil monetary fines. For example, in 2023 alone, 725 healthcare data breaches affected over 133 million records, according to reports submitted to the Department of Health and Human Services (HHS) OCR [6]. By mid-2025, nearly 500 breaches involving unsecured PHI had already impacted more than 37.5 million individuals [4]. These alarming statistics highlight how poor third-party risk management can extend breach durations, inflate costs, and increase the likelihood of regulatory action [4][7].
sbb-itb-535baee
How to Manage Cloud Vendor Risks
Thorough Vendor Risk Assessments
Healthcare organizations must take a structured approach when evaluating cloud vendors, especially before allowing access to sensitive data like PHI or clinical systems. The first step is understanding what type of data the vendor will handle - how many patient records are involved, whether PHI is being stored or simply transmitted, and how critical the service is to clinical operations. With numerous breaches reported, this kind of diligence is non-negotiable.
Part of this evaluation involves scrutinizing the vendor's security measures. Organizations should verify that vendors use multifactor authentication (MFA) across all access points, properly encrypt data both in transit and at rest, and implement network segmentation in shared environments. For example, a breach tied to a legacy server without MFA resulted in severe financial consequences[4]. Additionally, organizations should request independent certifications like SOC 2 Type II, HITRUST, or ISO 27001, along with evidence of regular penetration tests and vulnerability scans. Reviewing a vendor’s incident history is also critical, as business associates account for 37% of reported breaches[4]. Once a vendor passes this initial assessment, ongoing monitoring is essential to ensure their security measures remain effective.
Ongoing Monitoring and Comparison
Even after a vendor is approved, the work doesn’t stop. Continuous monitoring ensures that vendors maintain a strong security posture over time. This involves regularly reviewing OCR data and threat intelligence feeds to detect incidents involving current vendors or their subcontractors. Staying updated on trends, such as the 30% increase in ransomware attacks targeting healthcare vendors, is also vital[5].
Benchmarking provides another layer of oversight. Comparing a vendor's performance and risk profile against industry standards can help identify potential vulnerabilities that require immediate attention[1]. For vendors supporting critical systems like EHRs, imaging, or revenue cycle management, reassessments should be conducted annually - or even more frequently - to ensure their defenses keep pace with emerging threats.
Using Censinet RiskOps™ for Healthcare Vendor Management
Managing vendor risks manually can quickly become overwhelming, especially with the sheer number of vendor relationships in healthcare. This is where Censinet RiskOps™ comes in. The platform centralizes vendor risk data across PHI, clinical applications, medical devices, and supply chains, streamlining the entire process[1][2]. It automates security questionnaires aligned with frameworks like HIPAA, NIST CSF, and HITRUST, significantly reducing the workload for risk management teams.
Terry Grogan, CISO at Tower Health, highlighted the benefits: "Censinet RiskOps allowed 3 FTEs to go back to their real jobs! Now we do a lot more risk assessments with only 2 FTEs required."[1]
Censinet RiskOps™ also features a collaborative risk network that connects healthcare organizations with more than 50,000 vendors and products[1]. Its real-time dashboards provide instant visibility into vendor risks, enabling faster responses to potential issues. When one hospital completes a detailed evaluation of a cloud vendor, others in the network can use that information, avoiding duplicated efforts. Additionally, Censinet AI™ speeds up the process by helping vendors complete questionnaires in seconds, summarizing evidence, and drafting risk reports while ensuring critical decisions still involve human oversight[1]. By combining automation, benchmarking, and shared data, healthcare organizations can scale their risk management efforts effectively without compromising on quality or patient safety.
Conclusion
Cloud vendor breaches pose a significant threat to U.S. healthcare, impacting 37% of all breaches and affecting an average of 76,000 patients per incident[4]. When a single vendor or service provider is compromised, the consequences ripple through the system - disrupting clinical workflows, delaying care, and exposing massive amounts of sensitive data. A striking example is the Change Healthcare ransomware attack, which affected nearly 193 million individuals and resulted in an estimated $2.87 billion in damages[4]. These incidents are far more than technical glitches; they are crises that jeopardize patient safety and operational continuity, requiring immediate and focused attention from healthcare leaders.
The financial toll is equally alarming. Healthcare breaches cost an average of $7.42 million per incident - the highest among all industries for 14 straight years - and take approximately 279 days to detect and contain[4][7]. When a key vendor fails, hospitals are often forced to revert to paper-based processes, delay critical pharmacy approvals, and divert emergency care. These disruptions create an environment where diagnostic errors and medication mistakes are more likely to occur[2][4]. Beyond the direct impact, such breaches erode trust, undermining the adoption of digital health tools and patient engagement platforms that are essential for modern healthcare delivery.
To combat these risks, healthcare organizations must adopt comprehensive, data-driven vendor risk management programs. This includes conducting thorough pre-contract evaluations, maintaining ongoing monitoring, and benchmarking vendor performance in real time[4][7]. Key measures, such as enforcing multifactor authentication, encrypting data both in transit and at rest, maintaining tested backups, and participating in coordinated incident response exercises, should be implemented proactively - before breaches happen.
Technology can play a pivotal role in streamlining vendor oversight. Censinet RiskOps™ offers a robust platform to operationalize these efforts at scale. By centralizing third-party risk assessments, automating security questionnaires aligned with HIPAA and HITRUST, and connecting healthcare delivery organizations (HDOs) with a network of over 50,000 vendors and products, the platform helps identify and mitigate vulnerabilities before they escalate into major incidents[1][2]. In a healthcare landscape where cloud vendors are integral to everything from electronic health records to revenue cycle management, investing in advanced risk management tools safeguards patient care, ensures operational stability, and strengthens the healthcare system's overall resilience.
FAQs
How do cloud vendor breaches affect patient safety in healthcare?
Cloud vendor breaches pose a serious risk to patient safety by exposing sensitive health data and interrupting access to vital systems. When patient records are altered, lost, or become inaccessible, the consequences can be severe - ranging from delayed care to incorrect treatments or even misdiagnoses.
Beyond the immediate clinical impact, these breaches can also undermine trust in healthcare providers. Patients may feel reluctant to share critical information, fearing their privacy could be compromised. Safeguarding patient data and ensuring seamless access to clinical systems are essential to upholding both the safety and quality of care.
How can healthcare organizations protect themselves from risks caused by cloud vendor data breaches?
Healthcare organizations can better protect themselves from cloud vendor breaches by using continuous risk assessment and employing AI-powered platforms tailored to healthcare cybersecurity. These tools simplify third-party risk evaluations, pinpoint weaknesses, and improve coordination with vendors.
Additional steps include comparing security measures to industry benchmarks, performing detailed vendor assessments, and automating detection systems to respond swiftly to threats. Clear and robust contractual agreements outlining security obligations, along with transparent communication with vendors, are essential to protecting patient data and maintaining smooth operations.
Why do third-party vendors increase the risk of data breaches in healthcare?
Third-party vendors frequently interact with sensitive patient data and access crucial healthcare systems. However, their security protocols don't always align with the stringent measures upheld by healthcare organizations. This mismatch can open the door to vulnerabilities, making it easier for cybercriminals to target and potentially jeopardize both patient safety and data privacy.
To tackle these challenges, healthcare organizations need to focus on continuous risk assessments and work closely with their vendors. By staying proactive, they can better protect patient information, uphold security standards, and reduce the fallout from potential breaches.


