Integrated Delivery Network TPRM: Managing Vendor Risk Across Multiple Facilities
Post Summary
Integrated Delivery Networks (IDNs) face a growing challenge: managing third-party vendor risks across multiple healthcare facilities. With IDNs relying on thousands of vendors, the risks range from data breaches to operational disruptions. In 2024, healthcare organizations experienced 41% of third-party breaches, and the average breach affected over 300,000 individuals. These risks make a robust Third-Party Risk Management (TPRM) program essential for IDNs.
Key takeaways:
- Fragmented Vendor Ecosystems: Multiple facilities often use different vendors, creating inconsistencies and vulnerabilities.
- Regulatory Challenges: Compliance with HIPAA and state laws becomes harder with decentralized vendor management.
- Patient Safety Risks: Vendor failures can disrupt care and jeopardize lives.
A strong TPRM program includes centralized governance, risk-based vendor classification, continuous monitoring, and detailed incident response plans. Tools like Censinet RiskOps™ streamline these processes, offering centralized oversight, automated workflows, and compliance tracking. For IDNs, effective TPRM is not just about managing risks - it’s about protecting patients and ensuring uninterrupted care.
Key Challenges in Multi-Facility Vendor Risk Management
Managing vendor risk in an Integrated Delivery Network (IDN) is a whole different ballgame compared to handling it for a single facility. The sheer size and complexity of an IDN amplify risks, creating blind spots that can jeopardize the entire network. These challenges can lead to compliance issues and even put patient safety at risk.
Fragmented Vendor Ecosystems
In an IDN, each facility often has its own set of vendor relationships. One hospital might partner with a specific medical device supplier, while another chooses a completely different one for the same purpose. This lack of standardization leads to a chaotic vendor ecosystem with inconsistent security practices, redundant assessments, and significant gaps in visibility. These vulnerabilities make the network more susceptible to threats.
Research shows that the probability of a breach jumps from 22.7% with five technology providers to 40.1% when ten are involved[5]. A fragmented multi-vendor setup doesn’t just increase costs and operational headaches - it also broadens the attack surface while reducing the ability to monitor and secure the network effectively. This fragmentation not only complicates security measures but also makes regulatory compliance a tougher challenge.
Regulatory and Compliance Risks
For IDNs, staying compliant with regulations like HIPAA becomes more challenging when vendors are spread across multiple facilities and states. Each state may have stricter privacy laws than HIPAA, along with unique licensing and certification requirements[2]. A vendor contract that works in one state might fail to meet the legal standards of another, creating compliance gaps that put the entire network at risk.
Inconsistent vendor processes across different facilities only add fuel to the fire, leading to conflicts in multi-state compliance. The stakes couldn’t be higher. Steve Alder, Editor-in-Chief of The HIPAA Journal, underscores the importance of monitoring vendors:
"It is necessary to monitor business associate compliance because a covered entity can be held liable for a violation of HIPAA by a business associate if the covered entity 'knew, or by exercising reasonable diligence, should have known' of a pattern of activity or practice of the business associate that constituted a material breach or violation of the business associate's obligations under the HIPAA Business Associate Agreement."[2]
If Business Associate Agreements are invalid, Protected Health Information (PHI) can’t legally be shared with vendors, turning every data exchange into a potential HIPAA violation[2]. Even worse, a single facility’s compliance failure can ripple across the entire IDN, exposing the network to legal and financial risks.
Impact on Patient Safety and Care Delivery
Vendor failures don’t just compromise data - they can have a direct and devastating impact on patient safety and care. For instance, in 2020 and 2021, Trinity Health suffered third-party data breaches when ransomware attacks hit two of their software vendors, exposing millions of patient records and sensitive health information[7].
According to a 2024 Third-Party Risk Management Study, 61% of organizations reported experiencing a third-party data breach or cybersecurity incident - a 49% increase from the previous year[6]. Jaren Day from KLAS Research pointed out that despite increased spending on security, "early feedback from the market suggests that these investments might not be as effective as hoped"[6].
The consequences of vendor failures go beyond cybersecurity. They can disrupt hospital operations, delay critical treatments, and even endanger lives. This makes vendor risk management not just a technical or administrative concern but a fundamental issue of patient safety.
Core Components of an IDN TPRM Program
Building a strong IDN TPRM program requires structured governance, prioritization of risks, and collaboration across departments. Without these essential pillars, even well-funded programs can falter in safeguarding patient data and ensuring smooth operations. The stakes are high - one-third (30%) of data breaches in 2024 involved a third party, doubling the rate from the previous year[8].
Centralized Governance and Risk Visibility
The foundation of a successful TPRM program lies in creating a single source of truth for vendor risk across all facilities. Instead of allowing each hospital to maintain separate vendor lists and risk assessments, IDNs should adopt a centralized platform. This platform provides a clear, real-time view of all vendor relationships, tracking compliance, security posture, and performance metrics. A unified governance structure with clearly defined roles and a centralized risk register ensures that potential issues are identified and addressed before they escalate into system-wide problems.
Equally important is fostering a culture of security. Teams across all facilities should receive ongoing training in information security, data protection, and best practices for vendor risk management and incident reporting[1]. Education empowers staff to recognize threats and act proactively.
Risk-Based Vendor Classification
Not all vendors pose the same level of risk, so classifying them based on specific factors is critical. Factors include the type and sensitivity of data they handle, the extent of their access to critical systems, potential financial repercussions of a breach, and the operational impact if the vendor fails[4]. With the average healthcare data breach costing nearly $10 million[4] and vendor-related attacks surging by over 400% in just two years[4], accurate classification is essential.
High-risk vendors - those involved in areas like patient privacy, cybersecurity, data storage, or communications - demand thorough scrutiny. This includes detailed assessments, continuous monitoring, and certifications such as HITRUST, SOC 2 Type 2, or ISO 27001[4]. Best practices involve requiring vendors to complete detailed questionnaires with documentation, addressing identified risks for medium- and high-risk vendors, and conducting regular security reviews and scans[4].
Cross-Department Collaboration
Vendor risk management extends far beyond IT - it’s a patient safety concern that calls for input from various departments. Steve Ryan, Senior Manager of BARR's Attest Services Practice and Head of BARR's Healthcare Services, emphasizes this point:
"Vendor security isn't just an IT issue - it's a patient safety issue"[8]
Healthcare organizations face a range of vendor risks that require expertise from multiple areas. A multidisciplinary VRM team should include representatives from executive leadership, legal, compliance, IT, and procurement[4]. Effective collaboration hinges on centralized information sharing, allowing departments to discuss regulatory updates, vendor concerns, security risks, and policy changes. One department’s overlooked detail could be a critical red flag for another.
Clear role assignments are essential for swift, coordinated responses to threats. Additionally, integrating vendors into key security programs - like incident response plans and disaster recovery testing - ensures everyone knows their responsibilities during emergencies[3].
These components lay the groundwork for a structured, four-step TPRM framework tailored to streamline operations across multi-facility IDNs.
4-Step Framework for TPRM in IDNs
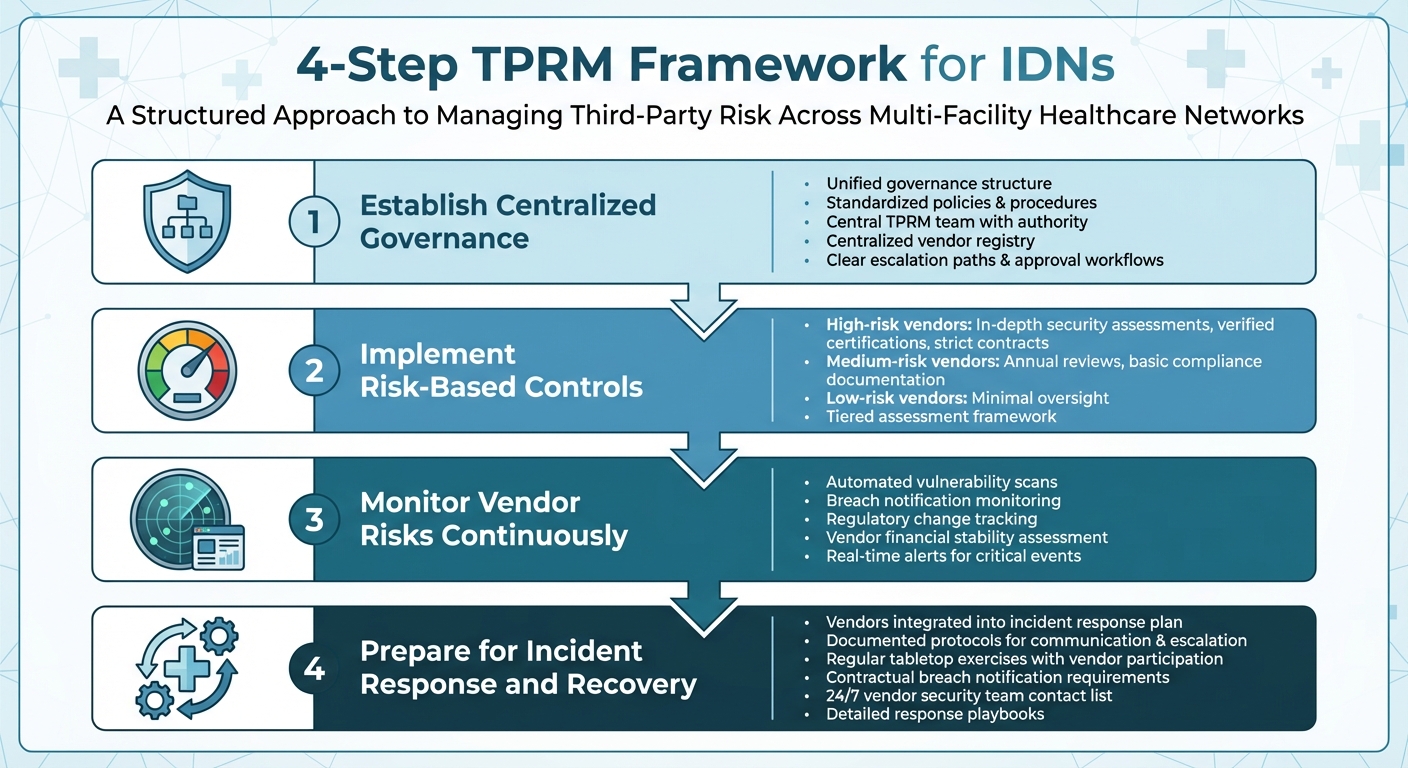
4-Step TPRM Framework for Integrated Delivery Networks
To effectively manage third-party risk across multi-facility Integrated Delivery Networks (IDNs), a structured framework is essential. This approach builds on established governance and risk visibility practices, ensuring patient data protection, regulatory compliance, and operational stability. With third-party cyber risks on the rise, a repeatable process is key to keeping vendor risks under control across multiple healthcare facilities[3].
Step 1: Establish Centralized Governance
Start by creating a unified governance structure to manage vendor risks consistently across all facilities. This means implementing standardized policies, procedures, and tools throughout the network. Assign a central TPRM team with the authority to set standards, approve vendors, and enforce compliance. This team should maintain a centralized vendor registry that tracks crucial details like risk classifications, contract specifics, and compliance statuses for all third-party relationships. The governance model should also include clear escalation paths, approval workflows, and decision-making guidelines. By centralizing oversight, you can ensure consistent, risk-based controls without unnecessary delays.
Step 2: Implement Risk-Based Controls
Develop security controls tailored to the risk level of each vendor. Vendors handling sensitive data like electronic protected health information (ePHI) or delivering critical services will need in-depth security assessments, verified certifications, and strict contractual terms. Medium-risk vendors might require annual reviews and basic compliance documentation, while low-risk vendors can be managed with minimal oversight. A tiered assessment framework can help streamline this process by routing vendors through the appropriate evaluation steps based on their risk level, data access, and service importance.
Step 3: Monitor Vendor Risks Continuously
Managing vendor risk isn’t a "set it and forget it" task - it requires constant vigilance. Use continuous monitoring tools to track vendor security postures, compliance statuses, and emerging threats. This might include automated vulnerability scans, monitoring breach notifications, staying updated on regulatory changes, and assessing vendor financial stability. Set up alerts for critical events like data breaches or the loss of key certifications to ensure a quick response. With breaches becoming more frequent and impactful[1], continuous monitoring provides the real-time insights needed to act swiftly and decisively.
Step 4: Prepare for Incident Response and Recovery
Ensure vendors are fully integrated into your organization’s incident response plan. Extend the centralized governance model to include coordinated responses across the network. High-risk vendors should have documented protocols for communication, escalation, containment, and recovery. Regular tabletop exercises and drills - where vendors actively participate - can help test these procedures and reveal any weaknesses. Include contractual terms requiring vendors to notify you of breaches, assist with forensic investigations, and support remediation efforts. Keep an up-to-date contact list of vendor security teams to ensure key decision-makers are reachable 24/7 in emergencies. Whether facing ransomware or data exposure incidents, having detailed response playbooks ensures everyone knows their role when every second matters.
sbb-itb-535baee
Using Censinet RiskOps™ for IDN-Scale TPRM
Managing vendor risk across Integrated Delivery Networks (IDNs) requires both adaptability and efficiency. Censinet RiskOps™ offers a centralized platform that simplifies the complex task of handling third-party risk at scale while meeting regulatory demands. By integrating third-party risk assessments, continuous monitoring, and collaborative risk management into a single dashboard, it provides risk teams with a clear, comprehensive view of their entire vendor ecosystem. Here's how the platform delivers on its promise.
Key Features of Censinet RiskOps™
The platform removes the hassle of manual processes through automated workflows, making risk management more efficient. Real-time dashboards offer instant insights into vendor risk profiles, compliance statuses, and emerging threats across all facilities. With Censinet AI™, the assessment process becomes lightning fast - vendors can complete security questionnaires in seconds. The AI also summarizes vendor evidence, organizes documentation, captures integration details, and even manages fourth-party risks. This blend of automation and human oversight not only speeds up evaluations but also ensures accuracy and control. Additionally, key findings and tasks are centralized and assigned to the appropriate stakeholders, such as AI governance committees, ensuring each issue is addressed by the right team at the right time.
Scalable Solutions for IDNs
Censinet RiskOps™ is designed to grow alongside your organization. Whether you prefer to manage risk internally, adopt a hybrid model combining the platform with managed services, or fully outsource cyber risk management, the platform adapts to meet your needs. This scalability is vital for IDNs managing hundreds - or even thousands - of vendor relationships across hospitals, clinics, and care facilities. Thanks to its AI-powered tools, risk teams can handle a higher volume of assessments without needing to expand their workforce, tackling the increasing challenge of third-party breaches head-on.
Boosting Efficiency and Ensuring Compliance
The platform doesn’t just handle scale - it also enhances compliance and operational efficiency. It provides a unified approach to meeting healthcare regulations like HIPAA, HITECH, and state-specific data protection laws. By centralizing policies, assessments, and documentation, Censinet RiskOps™ eliminates the fragmentation that often leads to compliance gaps in multi-facility organizations. Risk teams can quickly produce audit-ready reports, monitor vendor compliance certifications, and uphold consistent security standards across all locations. This centralized approach not only reduces compliance gaps but also shortens response times - critical in a landscape where breaches impacting over 300,000 individuals can cost nearly $10 million on average[4].
Conclusion
Effectively managing vendor risk across Integrated Delivery Networks (IDNs) demands more than good intentions - it requires a structured approach with centralized governance, continual oversight, and the right tools to handle the complexity of large-scale operations. With the increasing reliance on extensive vendor networks and the rising frequency of breaches, the stakes have never been higher. A disjointed strategy simply isn’t enough to address the growing threat of vendor-related attacks.
Centralized governance ensures consistent security practices across all facilities. By implementing unified policies and standardized risk assessments during vendor onboarding, IDNs can maintain a strong and uniform security posture across the entire network. This is crucial for safeguarding electronic Protected Health Information (ePHI) and ensuring every location adheres to the same high standards. Additionally, this approach enables a coordinated and efficient response when vendors face cybersecurity incidents or experience downtime, minimizing potential disruptions to operations[9].
Continuous monitoring connects initial risk evaluations to ongoing management. In multi-vendor environments, risk levels can shift quickly, and without regular oversight, small vulnerabilities can escalate into major issues. Real-time monitoring helps detect weaknesses and compliance lapses early, reducing the likelihood of costly breaches and operational failures. Given the financial and reputational damage associated with data breaches, this proactive approach is essential[10].
Technology ties these elements together, playing a critical role in streamlining governance and monitoring. For example, Censinet RiskOps™ offers a comprehensive solution tailored to healthcare’s specific challenges. This platform integrates centralized governance and continuous monitoring into a single system, powered by AI to handle a high volume of assessments efficiently - without requiring additional staff. It also simplifies compliance with centralized documentation and audit-ready reporting. Whether an IDN manages risk internally, through a hybrid model, or via fully outsourced cyber risk management, the platform adapts to operational needs, helping eliminate gaps and strengthen defenses.
FAQs
How does centralized governance help manage vendor risks in multi-facility IDNs?
Centralized governance plays a key role in simplifying vendor risk management within Integrated Delivery Networks (IDNs). By establishing consistent oversight and uniform policies across all facilities, this method ensures risks are identified and addressed more effectively. It also eliminates redundancies and ensures that every vendor adheres to the same compliance and security standards.
When risk management efforts are consolidated, IDNs gain the ability to monitor vendor performance in real time. This enables quicker responses to potential issues while maintaining compliance with regulatory requirements. The result? Smoother operations and a more reliable risk management system.
What are the main advantages of using Censinet RiskOps™ for managing third-party risks in healthcare?
Censinet RiskOps™ streamlines the often complex tasks of vendor onboarding, risk assessments, and continuous monitoring, helping healthcare organizations efficiently manage third-party risks across various facilities. By automating essential workflows, it cuts down on errors, strengthens compliance efforts, and offers a clear view of vendor-related risks.
This platform allows healthcare providers to standardize their vendor management processes, safeguard sensitive data, and stay aligned with regulatory requirements. At the same time, it boosts operational efficiency and reduces the likelihood of disruptions.
Why is continuous monitoring important for managing vendor compliance and security?
Continuous monitoring plays a key role in helping healthcare organizations stay on top of vendor security and compliance in real time. By keeping a constant watch on vendor activities, organizations can spot risks, catch unusual behavior early, and address potential threats before they grow into bigger problems.
In healthcare, where protecting sensitive patient information and meeting strict regulatory standards are non-negotiable, continuous monitoring ensures vendors consistently align with compliance requirements and maintain strong data security practices. This forward-thinking strategy not only reduces risks but also helps streamline operations across various facilities.


